- 03 Jul 2025
- 8 Minutes to read
- Print
- PDF
SSO with 1Password for Business
- Updated on 03 Jul 2025
- 8 Minutes to read
- Print
- PDF
Introduction
1Password is a secure password manager that helps you store, manage, and autofill your passwords, login details, and other sensitive information in one place. It not only improves security but also makes logging into websites, apps, and services faster and more convenient.
With Scalefusion SSO configuration, you can easily integrate 1Password using OIDC/OAuth 2.0 standards. This allows users to securely sign in to 1Password using their existing corporate credentials, streamlining access, reducing password fatigue, and enhancing overall IT security and user experience.
Prerequsite
The devices should be enrolled with Scalefusion as BYOD or UAE, or Shared COD.
The Custom Domain for which you are authorising should be verified through OneIdP.
Users belonging to a custom domain should be imported/added to the Scalefusion Dashboard and migrated to OneIdP.
IT Admins should have access to the 1Password admin console.
Create SSO Configuration for 1Password
Navigate to OneIdP > SSO Configurations on the Scalefusion dashboard.
Click on the New SSO configuration button.
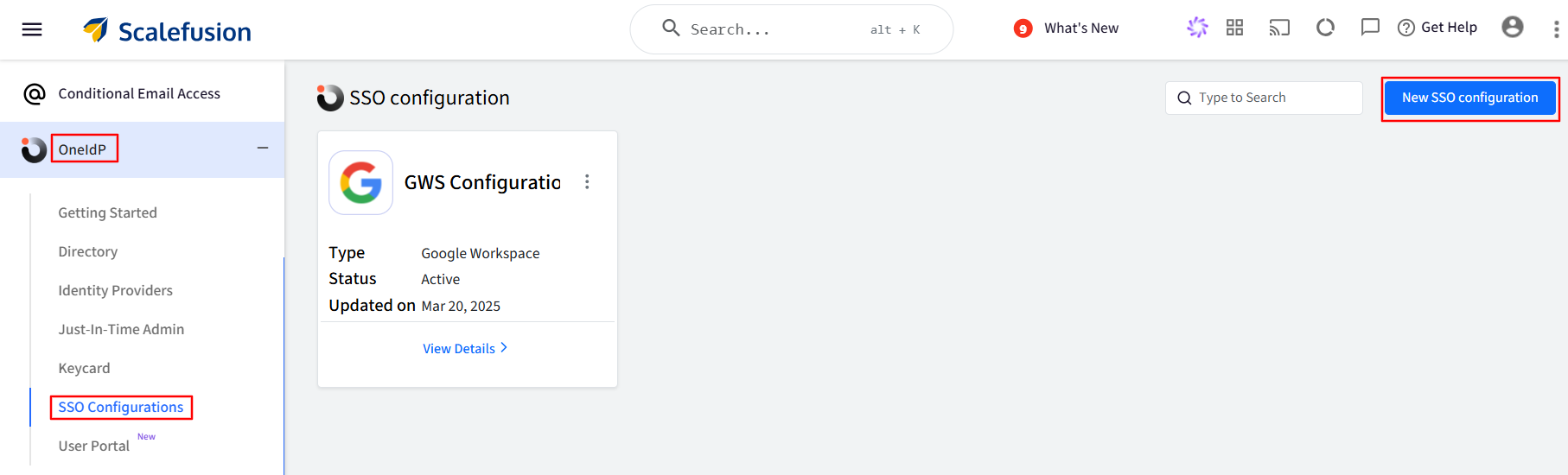
From the shown list, click on Configure for 1Password to open the configuration wizard.
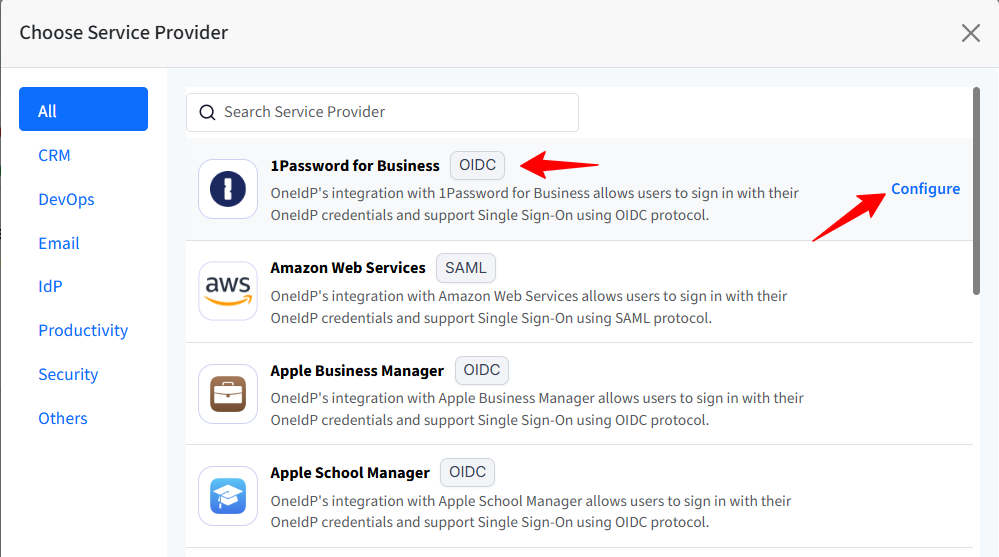
Navigate to each tab and enter the required details. You can navigate to the next tab only after you have entered complete details in the current section.
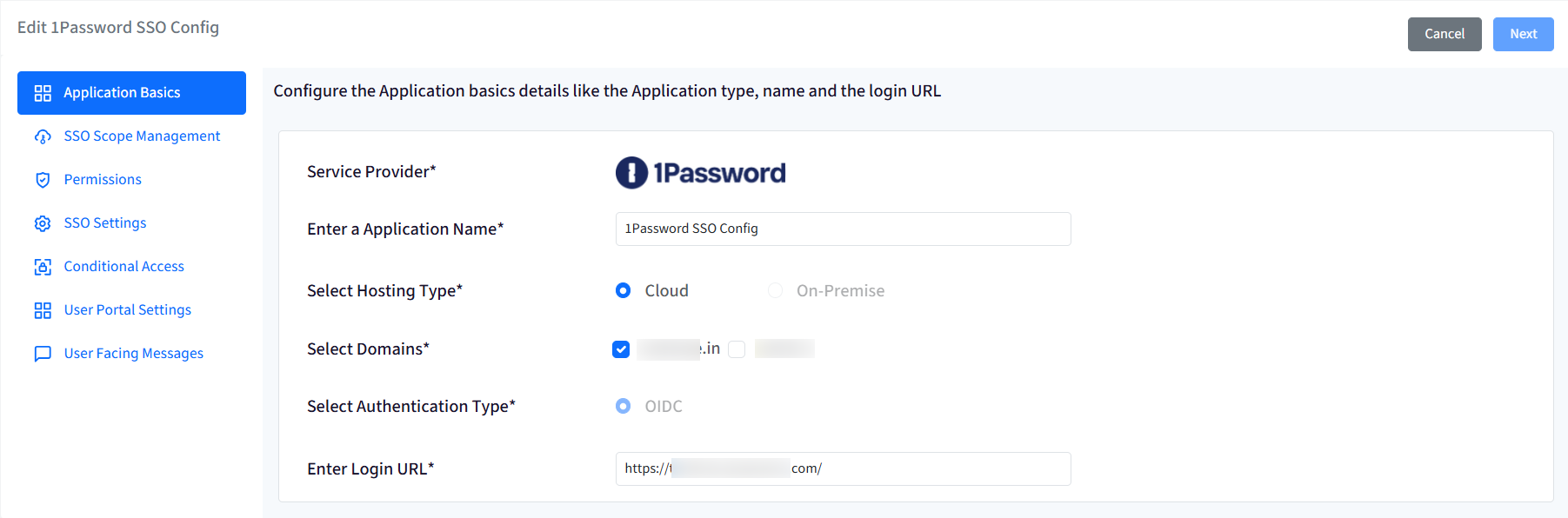
Application Basics
Enter Application Name: Enter a name for your App, which will be an identifier for your configuration. The name must be at least 5 characters long. The maximum allowed length is 128 characters.
Select Hosting Type: This will be pre-selected as Cloud.
Select Domains: All the custom domains you have configured and verified using OneIdP will be listed here. Select the domain(s) on which you want SSO to be enabled. You can select more than one domain.
Select Authentication Type: This will be pre-selected as OIDC.
Enter Login URL: Provide the URL that you use to sign in to that service.
Once you have entered all details, click Next.
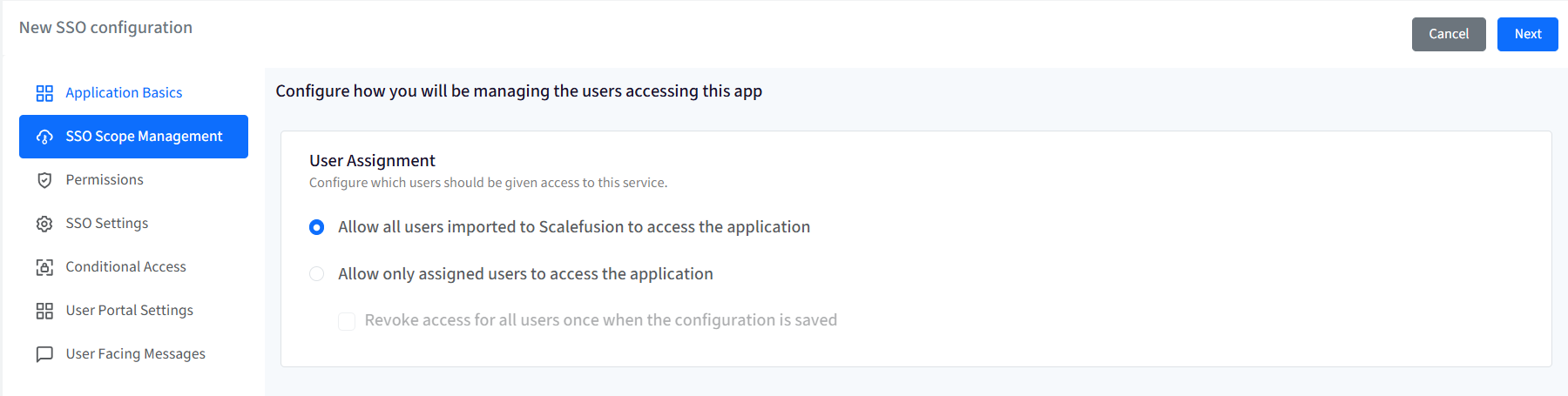
SSO Scope Management
With SSO scope management, you can configure the procedure for managing the users who will be accessing this application.
User assignment
SSO Configuration would allow only assigned users to access the app. Choose one from the following options:
Allow all users imported to Scalefusion to access the application: All users (belonging to the domain) imported to Scalefusion and migrated to OneIdP will be allowed to access the application.
Allow only assigned users to access the application: Only the user(s) whom you have assigned the SSO configuration will be allowed to access the application. With this option, after the SSO configuration is created, you need to manually select and assign the users.
Revoke access for all users once when the configuration is saved: If this is checked, the access is revoked from the users who are currently assigned the configuration. As a result, it will invalidate all user sessions and log out users from their current running session.
Permissions
Scalefusion does not require any additional permissions to manage SSO for this application. Click Next to continue.
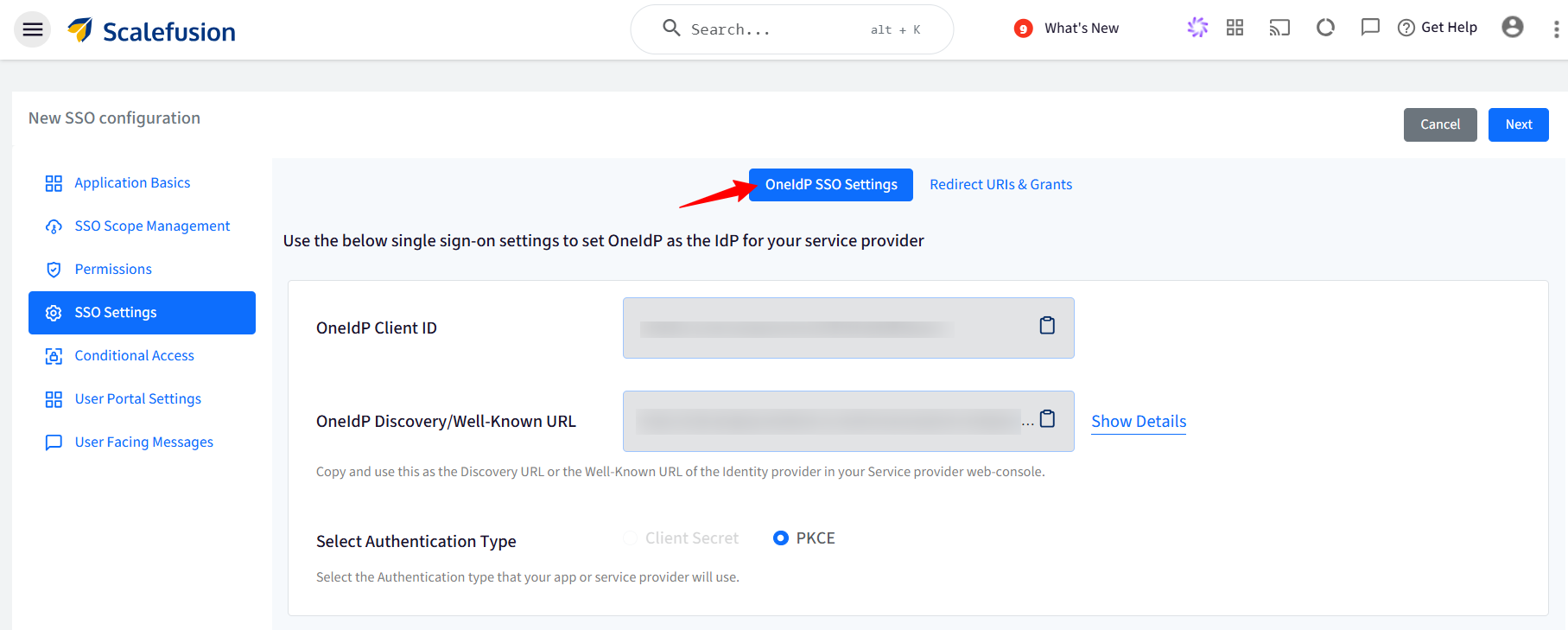
SSO Settings
This section provides the SSO settings to set OneIdP as the Identity Provider for 1Password. You will have to add these in 1Password admin portal.
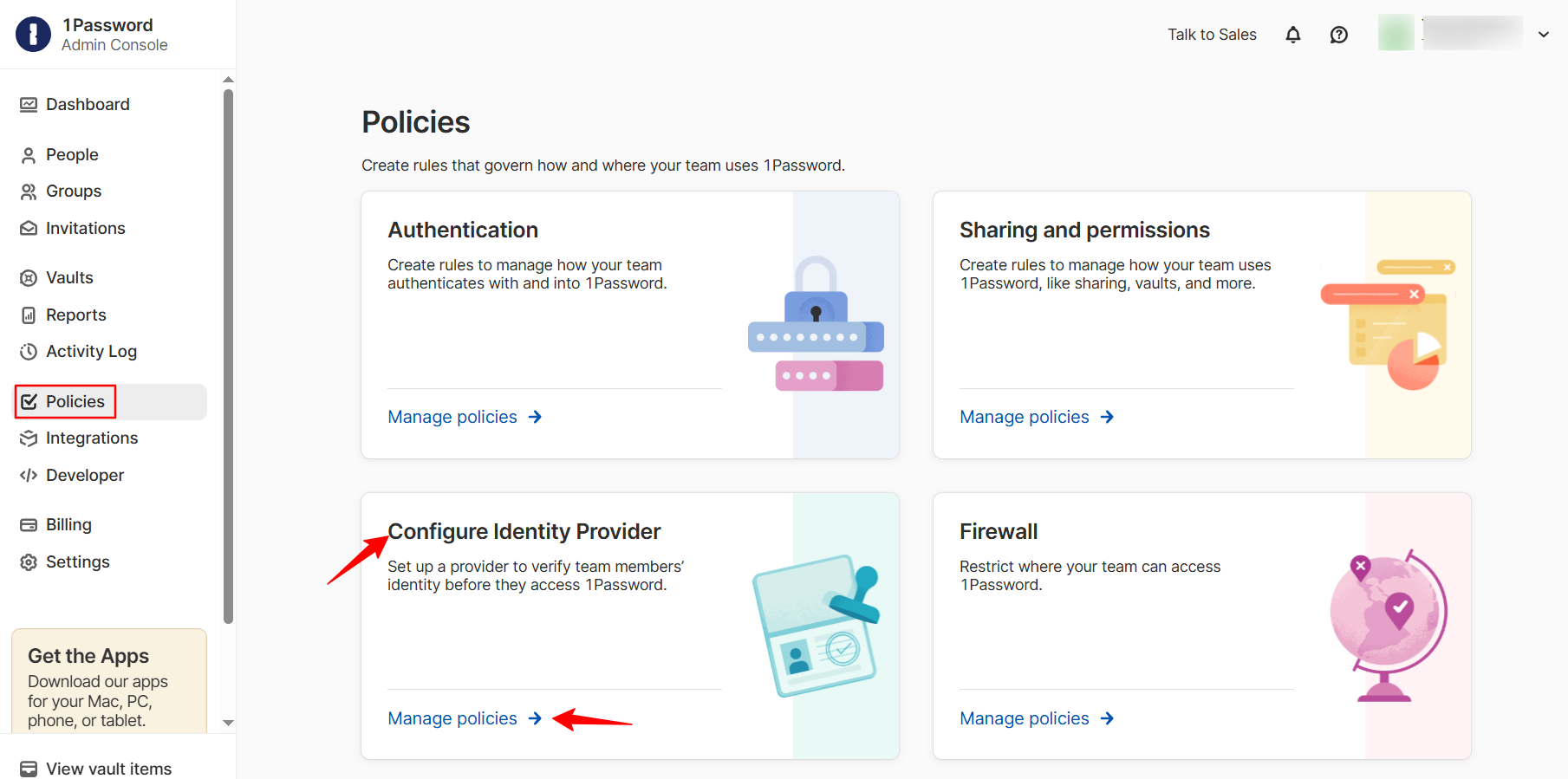
Navigate to your 1Password Admin Portal and log in.
Go to Policies > Configure Identity Provider > click on Manage Policies.
In the Choose your identity provider section, click Others.
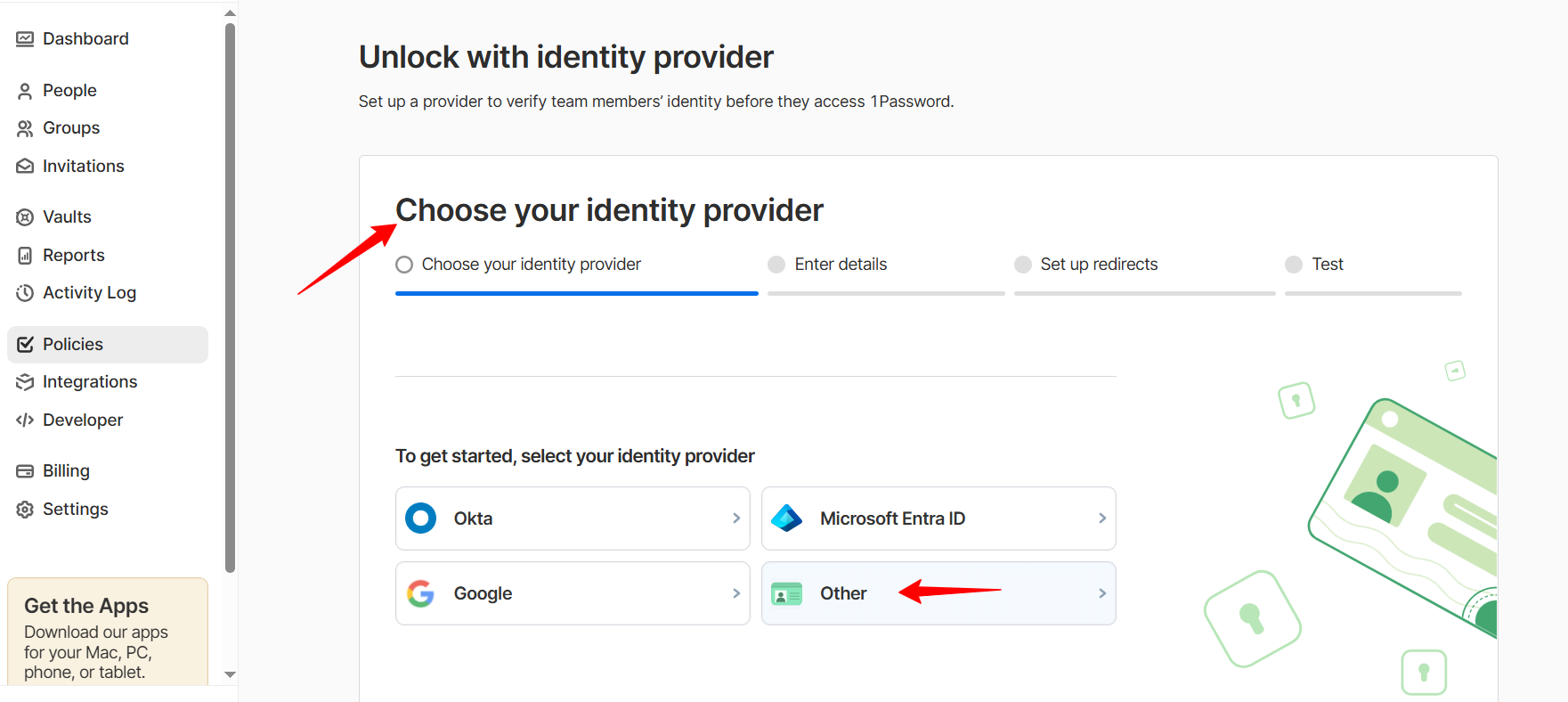
Scroll down and click on Next.
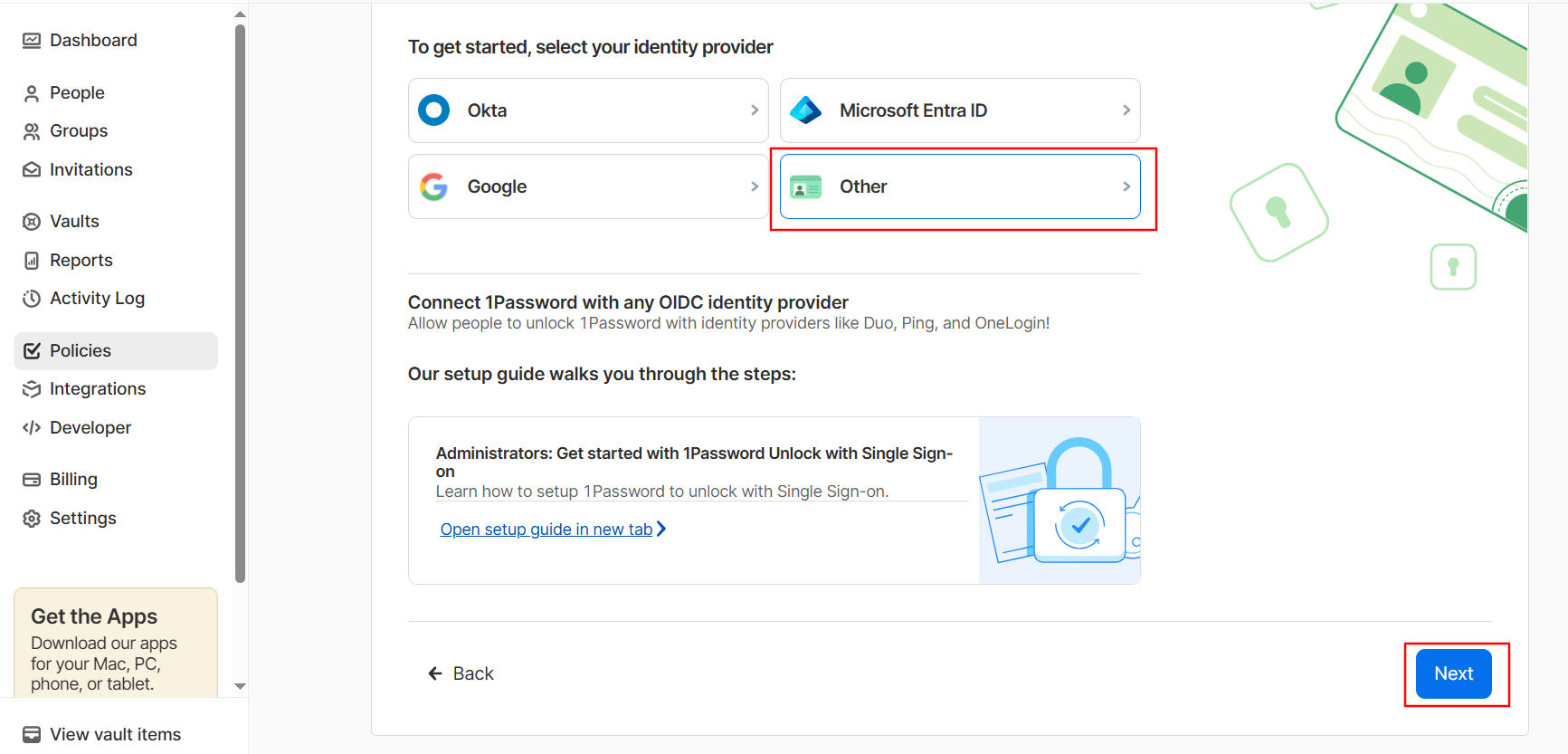
In the Enter details section:
Select Others in What is the name of your Identity Provider? field.
Provide a unique name for it.
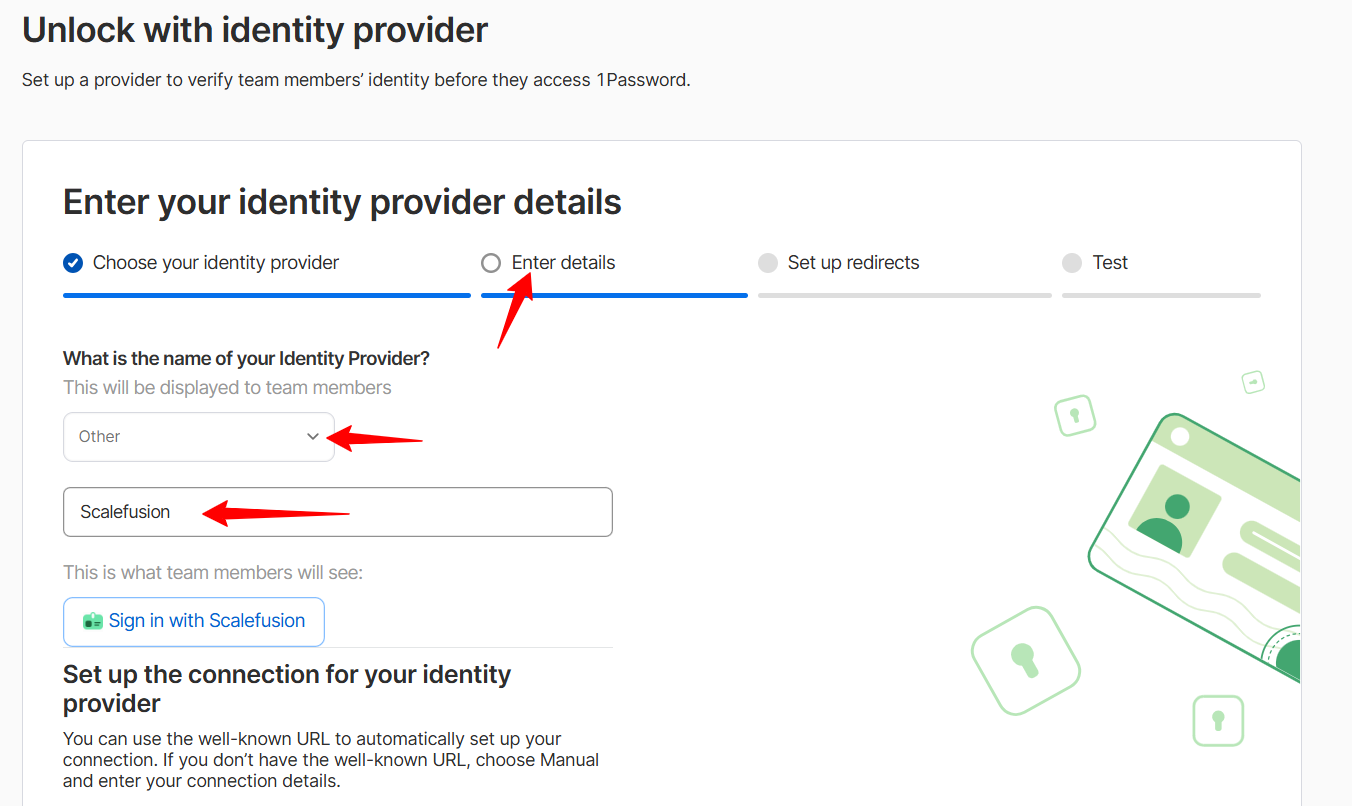
Keep Set up the connection for your identity provider as Automatic.
Paste the OneIdP Client ID from the Scalefusion dashboard in Client ID field.
Paste the OneIdP Discovery/Well-Known URL from the Sclaefusion dashboard in Well-Known URL filed.
Click on Next.
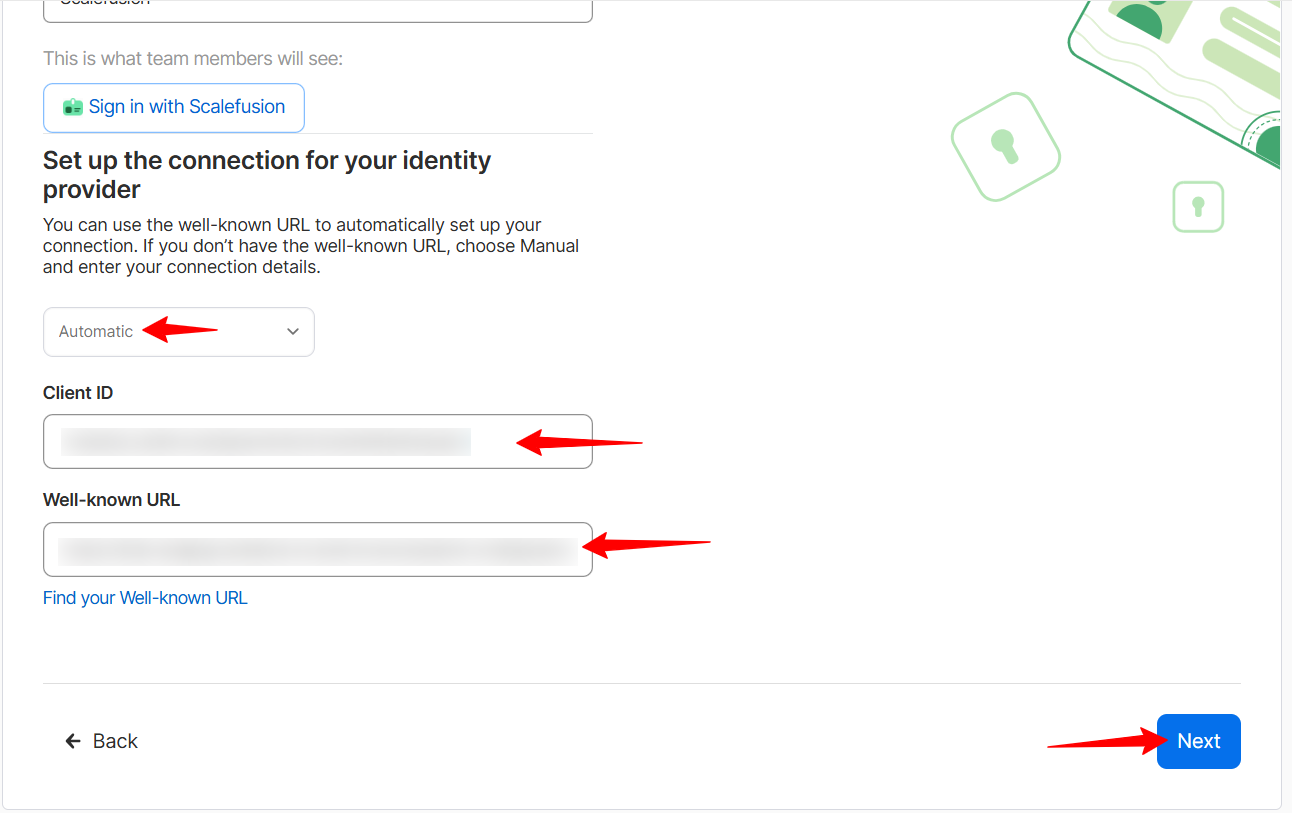
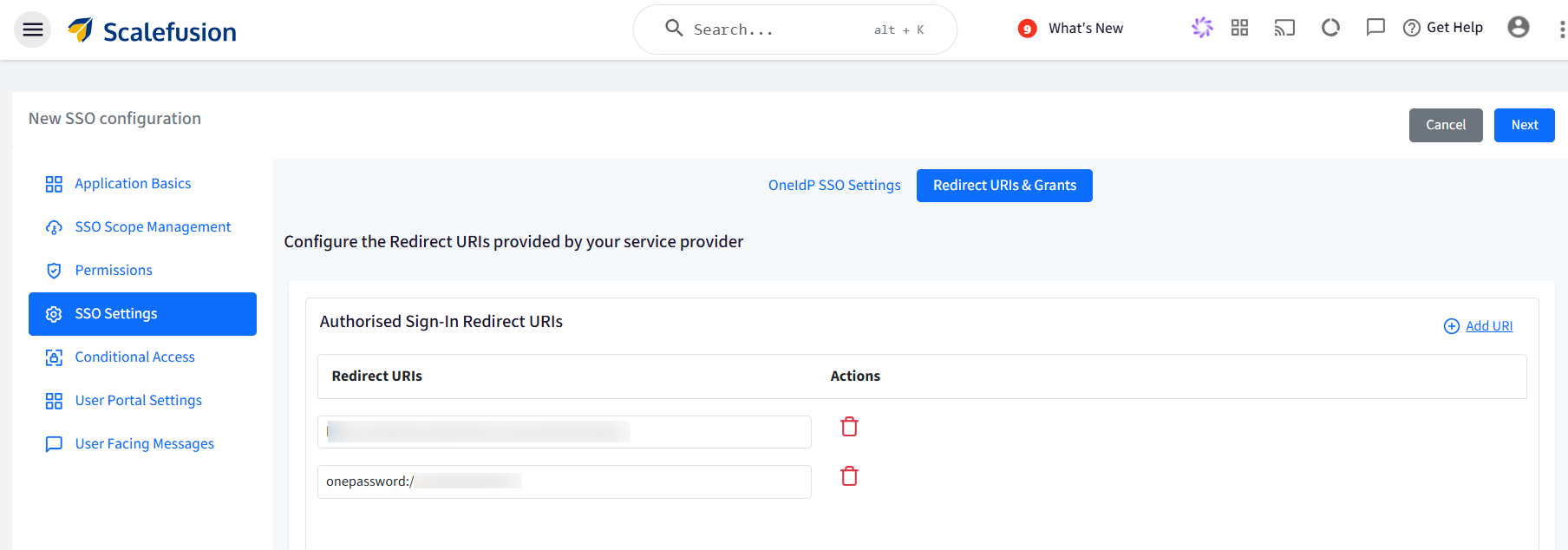
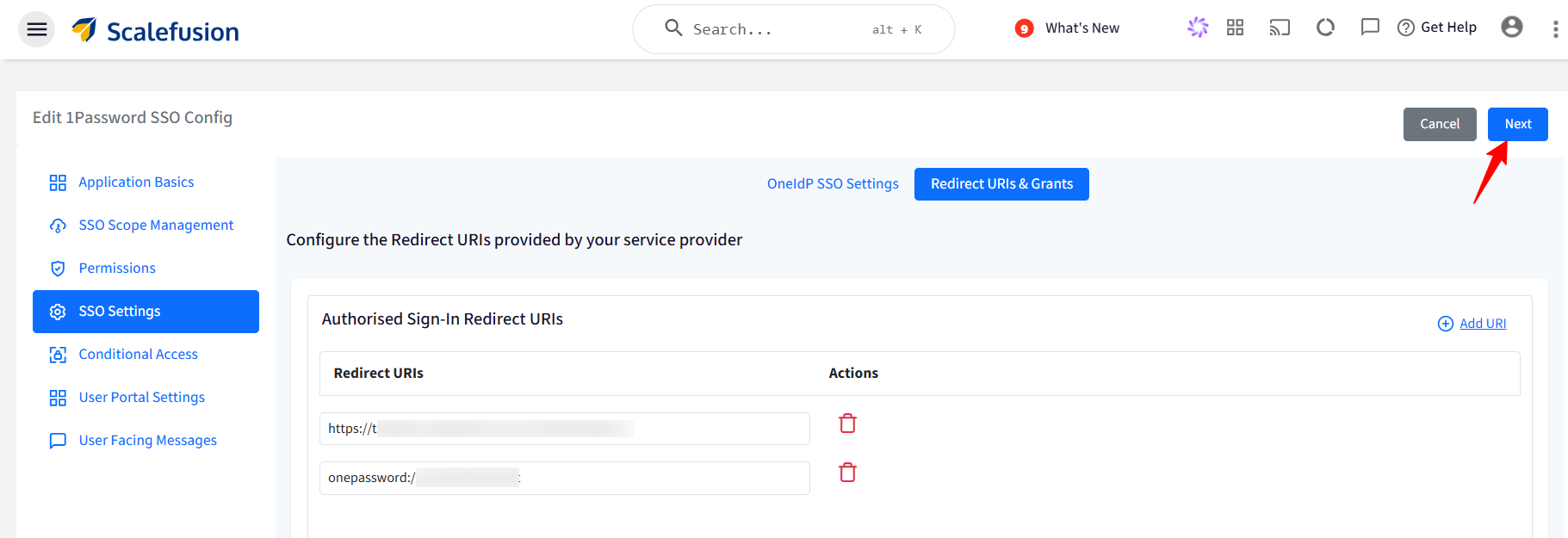
Copy the Redirect URLs and add them to the Redirect URLs & Grant section on the Scalefusion dashboard. Once done, click on Next.
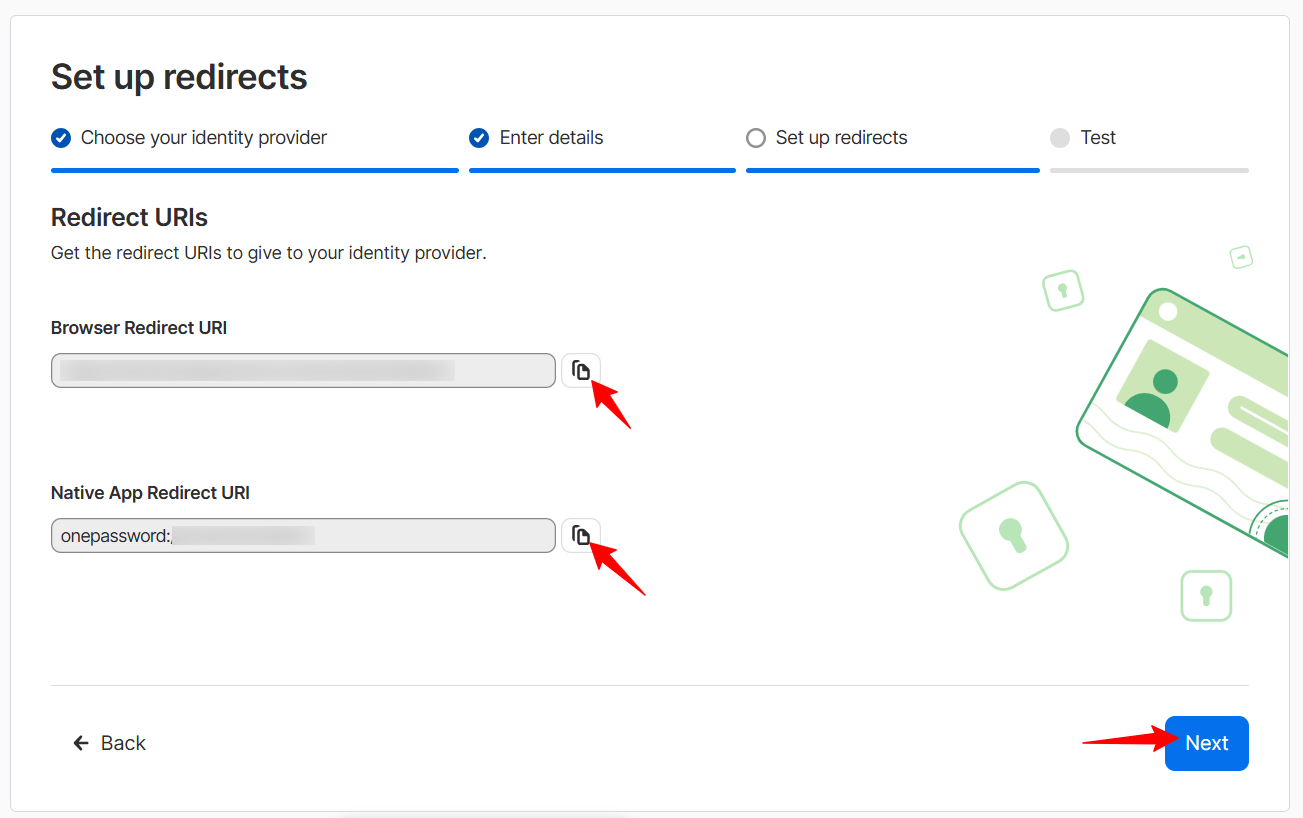
Sign-Out URL: You can add the back channel log out URL here, if it is supported.
Grant type: Select the grant types that should be provided in response. By default, Authorization Code is selected. You can also select Refresh Token.
Access Token: You can set the Token expiry from 5 to 120 minutes and the Grace Period for Token from 0 to 5 minutes.
Click on Next in the 1Password portal to go to the last section.
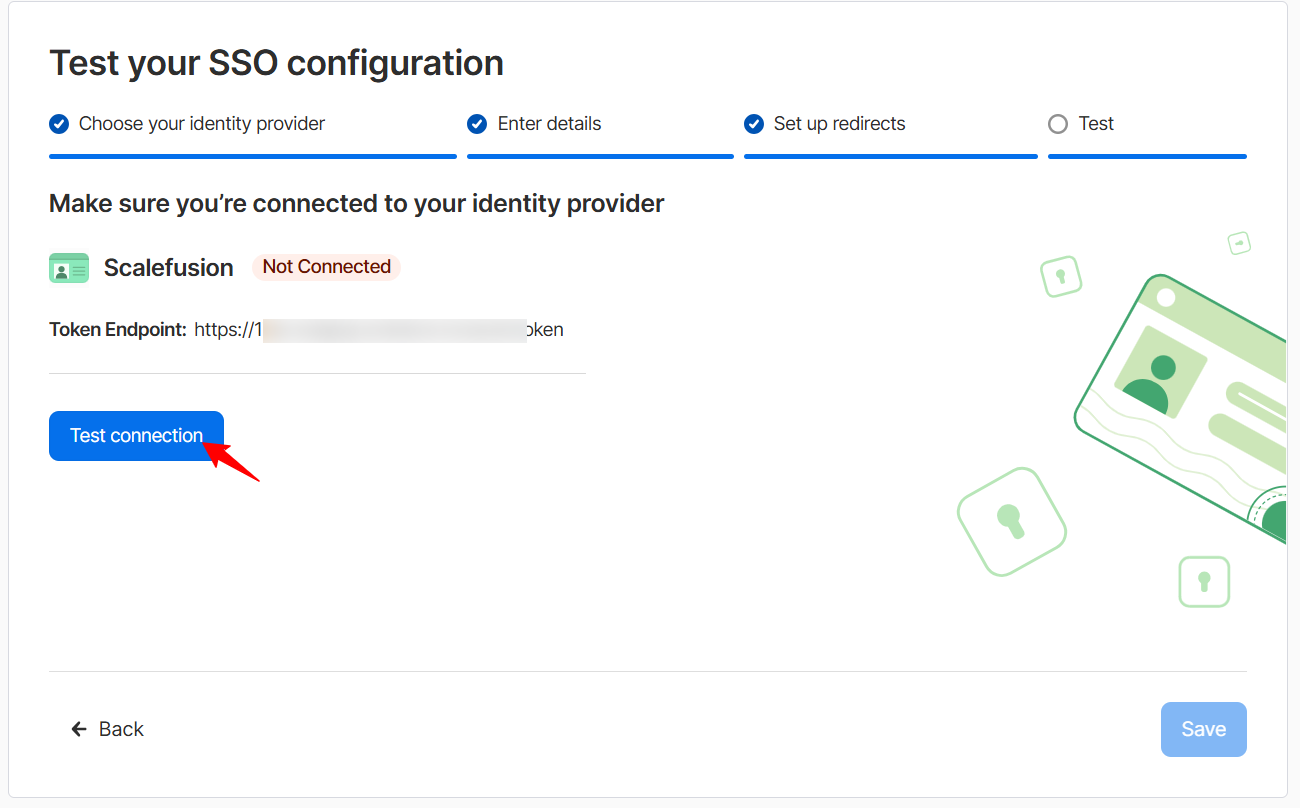
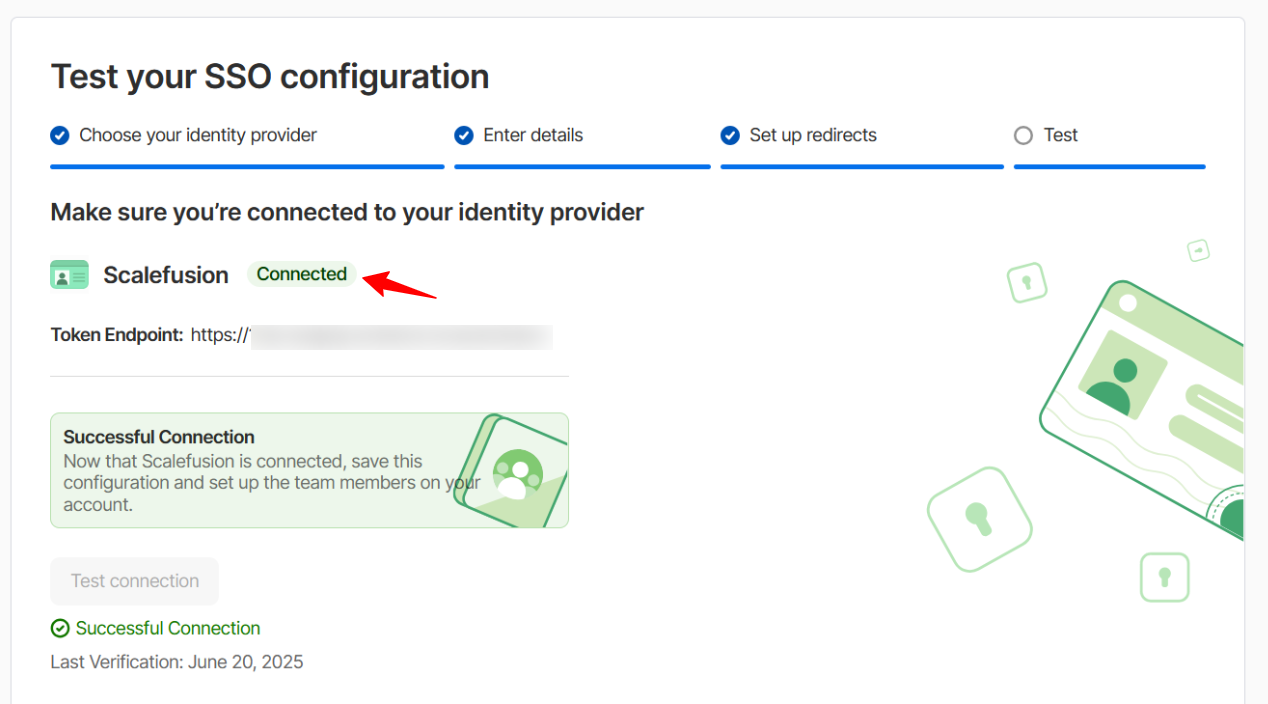
In this section, click the Test Connection button to make sure you are connected to Scalefusion.
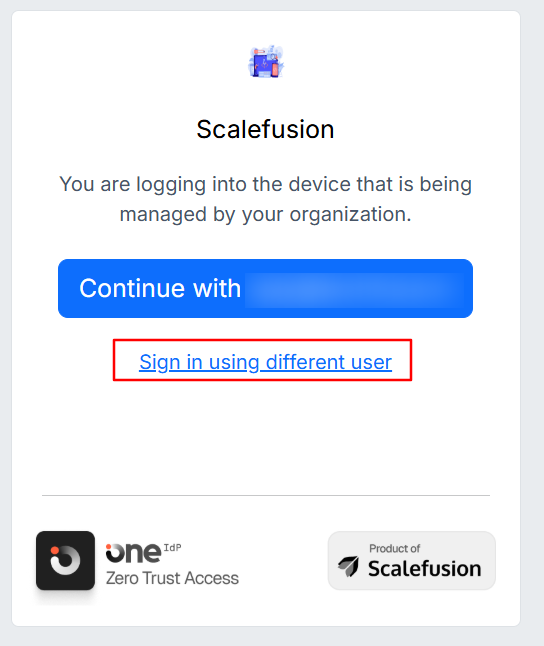
You will see a OneIdP Authentication screen. Click on Sign in using a different user and enter the email ID and password of the user who is an Admin of the 1Password portal.
You will see the screen below where you have to accept the permissions by clicking Continue.
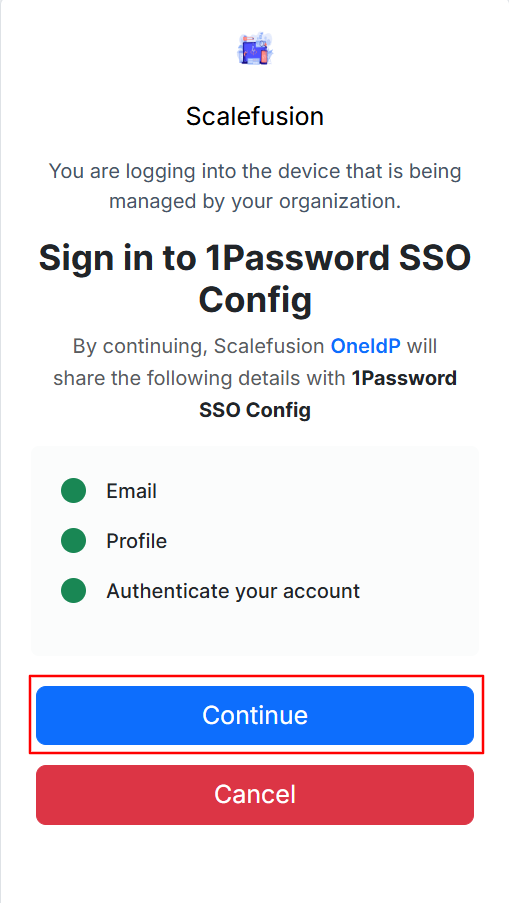
You will be redirected to the 1Password portal, and it will show Test connection as successful. Click Save to save this configuration.
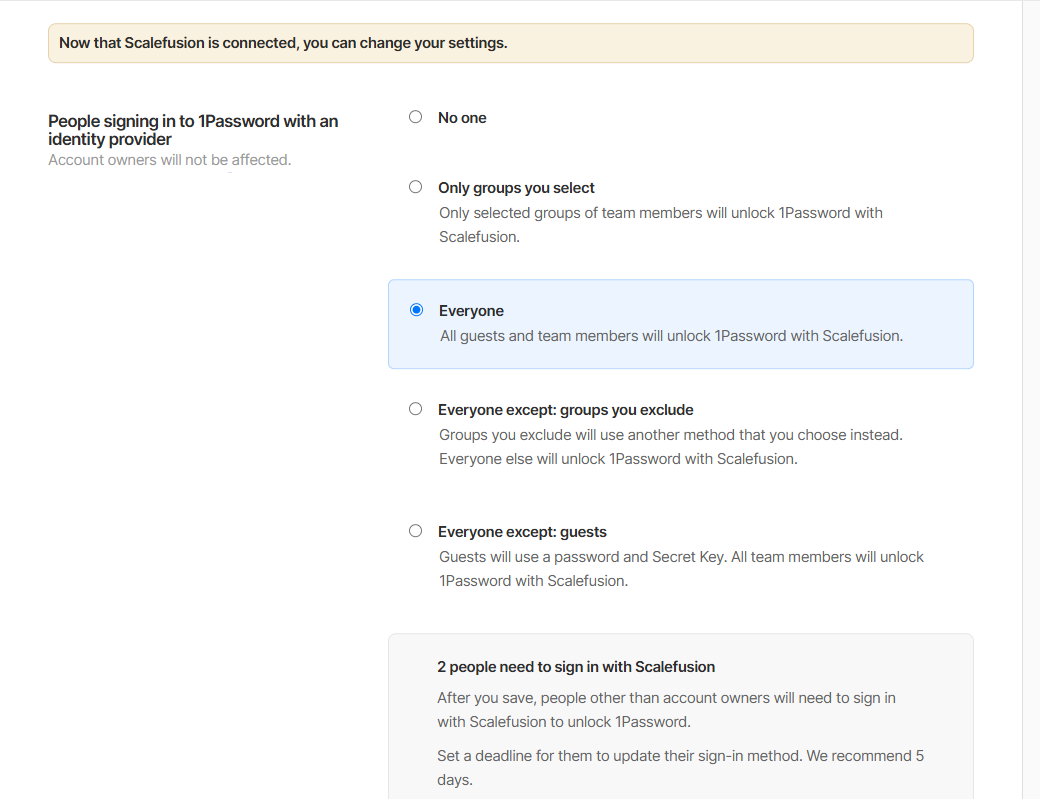
You can later set up the settings of who can sign in to 1Password with Scalefusion as the Identity Provider.
This also completes the SSO Settings on the Scalefusion dashboard. Click on Next to save the settings on the Scalefusion dashboard.
Conditional Access
From this section, you can define the additional conditions on the basis of which users will be allowed/disallowed from accessing the application on the device.
Conditional Access Settings
Device Policy
For Android, iOS/iPad OS, Windows & macOS, Linux: Choose one from the following two conditions:
Only if the device is managed by Scalefusion: The application will be accessible only on devices managed (enrolled) by Scalefusion.
If the device is managed by Scalefusion or an OTP using the Scalefusion Authenticator app from a managed device: The application is accessible if any of the following conditions is met:
Device is managed by Scalefusion: If device is managed you will not be asked to enter OTP for authentication, or
If device is unmanaged, OTP is required for authentication: OTP can be taken from the Scalefusion Authenticator app installed on a Scalefusion-managed device.
Allow users to access by setting up MFA using third-party authenticator app or OTP sent on email:
Device is managed by Scalefusion: If device is managed user will not be asked to enter OTP for authentication.
If device is unmanaged, OTP is required for authentication. OTP can be taken from any 3rd party authenticator app or an OTP received via email, based on the MFA settings in Directory Settings.
Note: The left side panel is for configuring Device Policy on Android & iOS/iPad OS and right side is for Windows & macOS and Linux below them. Hence, you can configure separate device policies based on platform.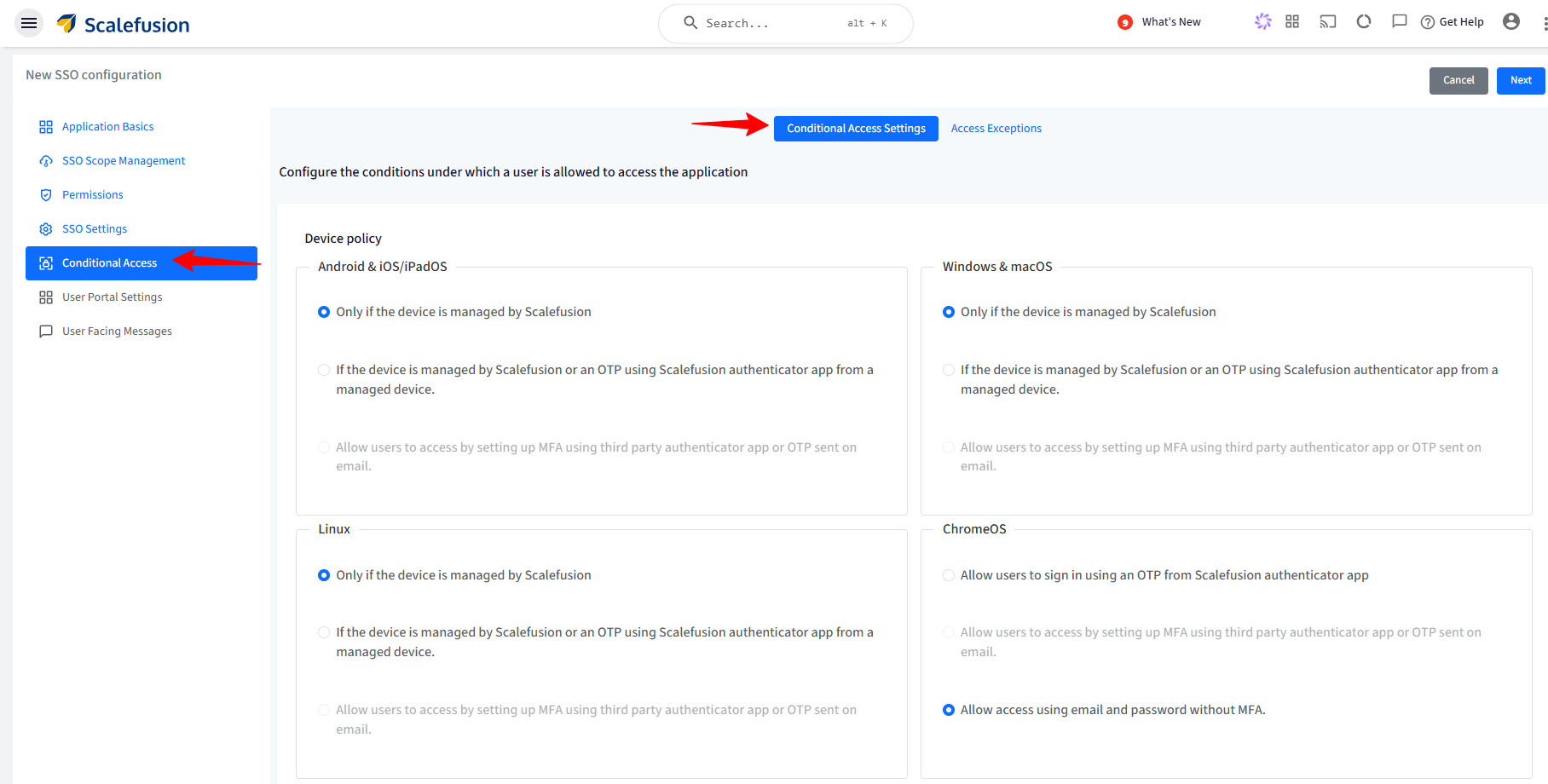
For ChromeOS: Choose one from the following two conditions:
Allow users to sign in using an OTP from Scalefusion authenticator app: OTP can be taken from Authenticator app installed on a Scalefusion managed device.
Allow users to access by setting up MFA using third party authenticator app or OTP sent on email: OTP is required for authentication. OTP can be taken from any 3rd party authenticator app or an OTP received via email, based on the MFA settings in Directory Settings.
Note:
This option will be enabled if MFA is enabled in Directory Settings.
Allow access using email and password without MFA: Authorization check will not happen, and users can login directly with their email and password.
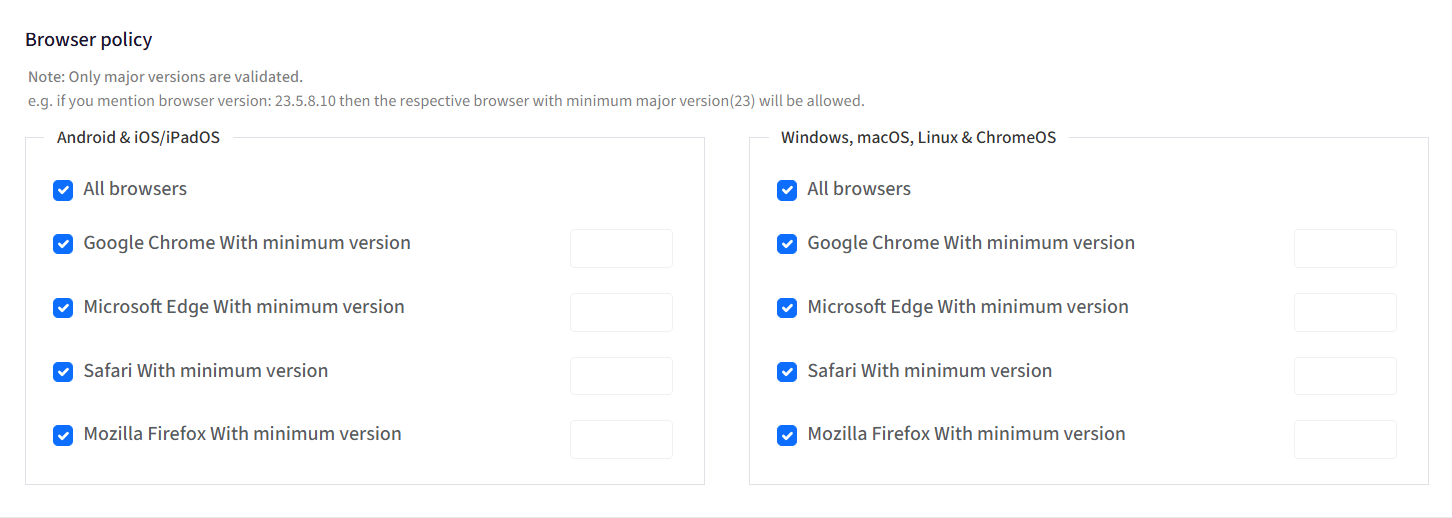
Browser Policy
From here, you can select one or more browsers and specify minimum versions on which you want to allow the access to the application.
The following are the options:
All Browsers
Google Chrome with minimum version
Microsoft Edge with minimum version
Safari with minimum version
Mozilla Firefox with minimum version
By default, all browsers are allowed.
Only major versions are validated. E.g., if you mention browser version: 23.5.8.10, then the respective browser with minimum major version (23) will be allowed.
Access Exceptions
From this section, you can configure the exceptions where the users are allowed to access the applications even if the conditions are not met. The following are the exceptions that can be configured:
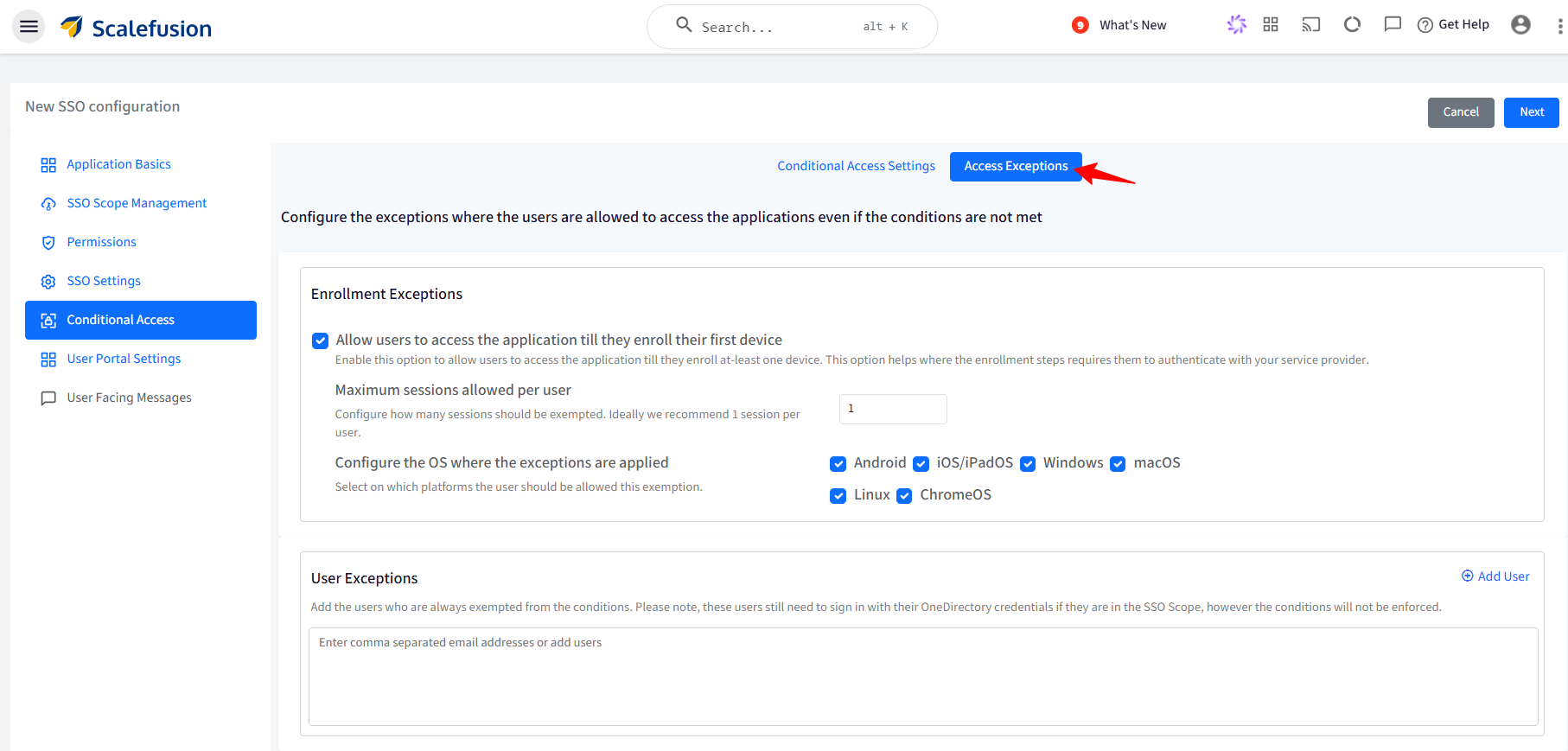
Enrollment Exceptions:
Allow users to access the application till they enroll their first device: Allows users to access the application till they enroll at least one device. This option is helpful in conditions where the enrollment steps require them to authenticate with the service provider. With this, you can also configure the following:
Maximum sessions allowed per user: Set the maximum number of simultaneous sessions a user can have when logging into an application across devices. If a user is already logged into the app on one device, they won’t be able to log in to the same app on another device. It can range from 1 to 3. Ideally, 1 session per user is recommended.
Configure the OS where the exceptions are applied: Select the platform(s) on which this exemption would be allowed to users.
User Exceptions: Here, you can add the users who are always exempted from the conditions and will never be asked to manage their devices. Enter comma-separated email addresses of users, or click on Add Users on the right, and in the new window, select the users who should be exempted.
Note:
These users still need to sign in with their OneDirectory credentials if they fall under the SSO Scope, however the conditions will not be enforced.
User Portal Settings
IdP-initiated SSO is particularly useful in scenarios where users access applications through a unified dashboard or portal displaying all available apps. Since OAuth (and OIDC) does not natively support IdP-initiated SSO, we handle this by displaying application shortcuts based on the configured SSO settings. When a user clicks on an app, they are redirected to the appropriate login URL to initiate the standard authentication flow.
To know more about the User Portal, please refer to our guide here.
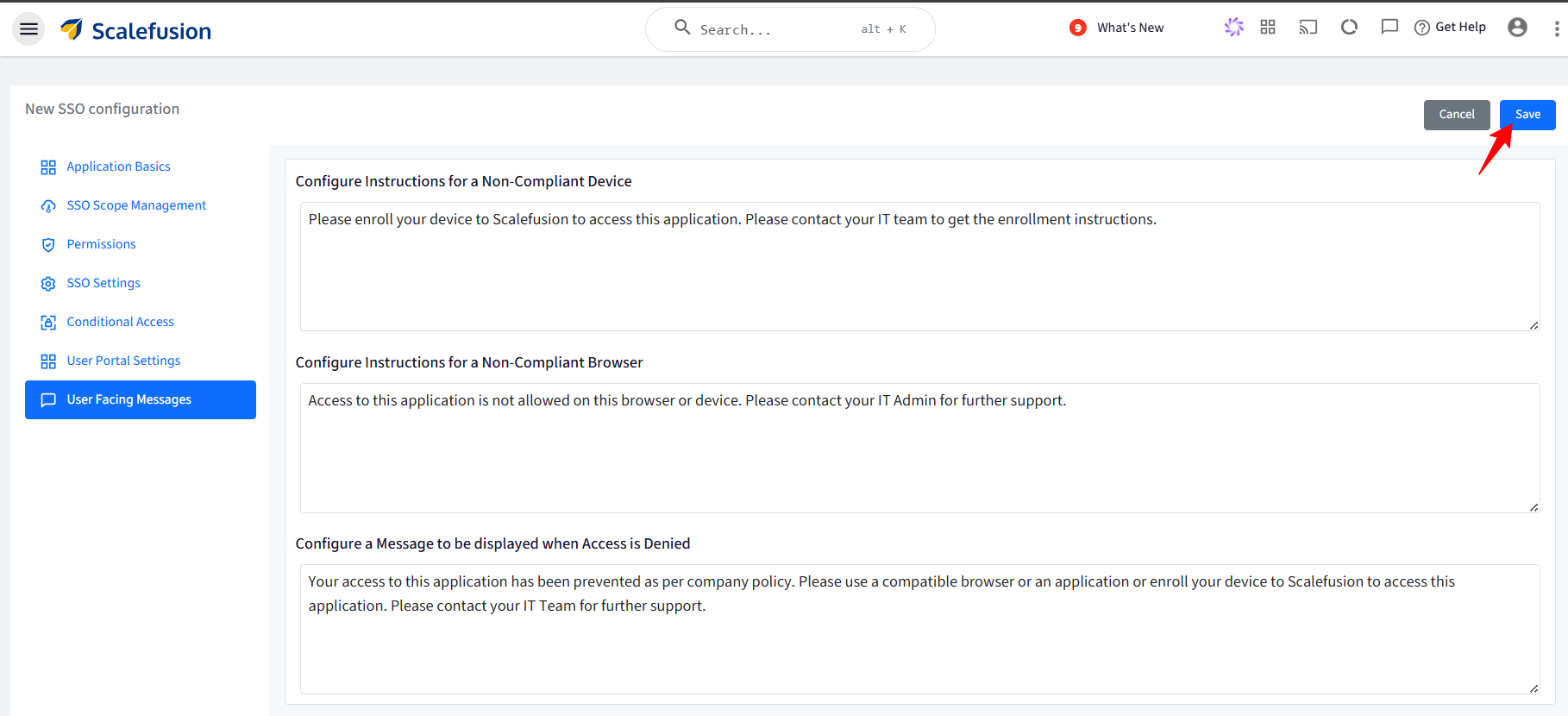
User Facing Messages
User-facing messages help admins configure messages that end users may be shown when they are unable to access the application if any of the compliance conditions are not met. You can configure messages under the following:
Configure Instructions for a Non-Compliant Device: This message is shown when the device is not compliant and needs to be enrolled in Scalefusion.
Configure Instructions for a Non-Compliant Browser: Shown when the browser is not compliant as per the configurations.
Configure a Message to be displayed when Access is Denied: Any other cases where access to the application is denied.
There are some pre-configured messages displayed on the Dashboard which you can edit as per your requirement.
After configuring user-facing messages, click on Save.
The SSO configuration is created and listed on the SSO Configuration page as a separate card with the name you have defined. You can create multiple SSO configurations in the same manner.
User Experience
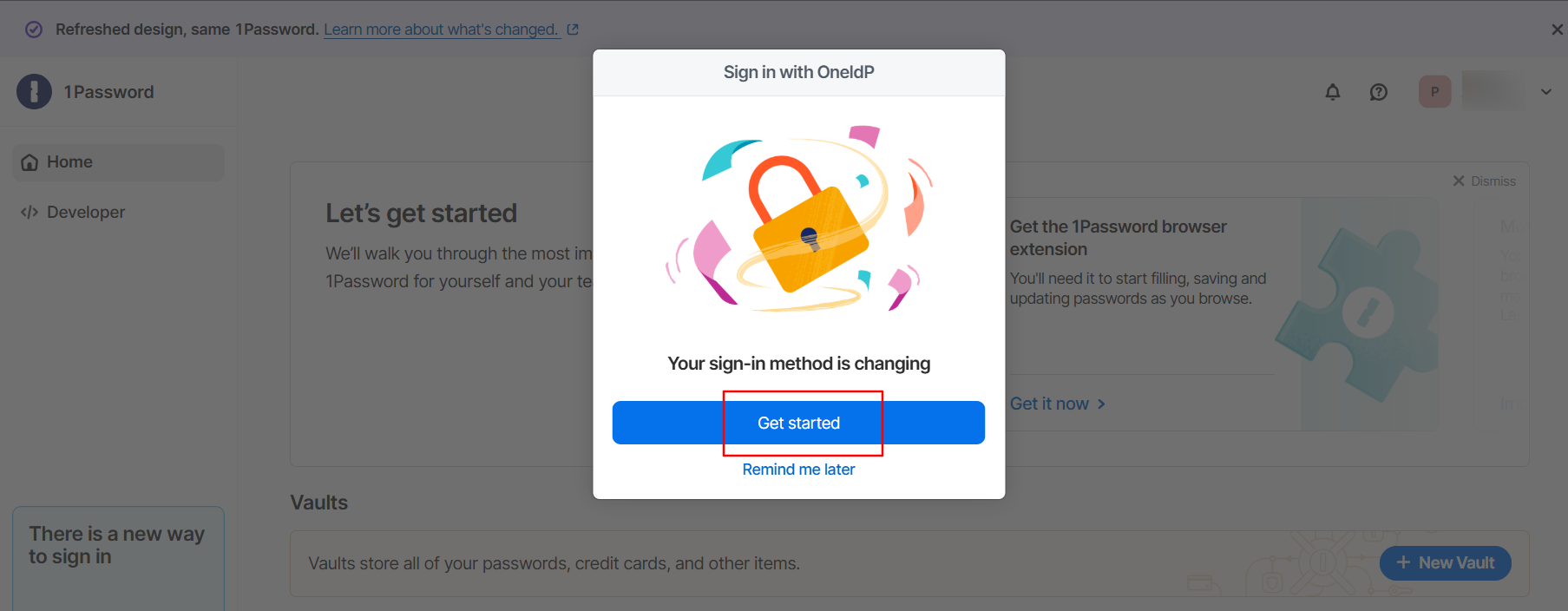
Depending on the settings configured under 'People signing in to 1Password with an identity provider' in the 1Password portal, where you specify the users this policy applies to, those users will be required to change their sign-in method.
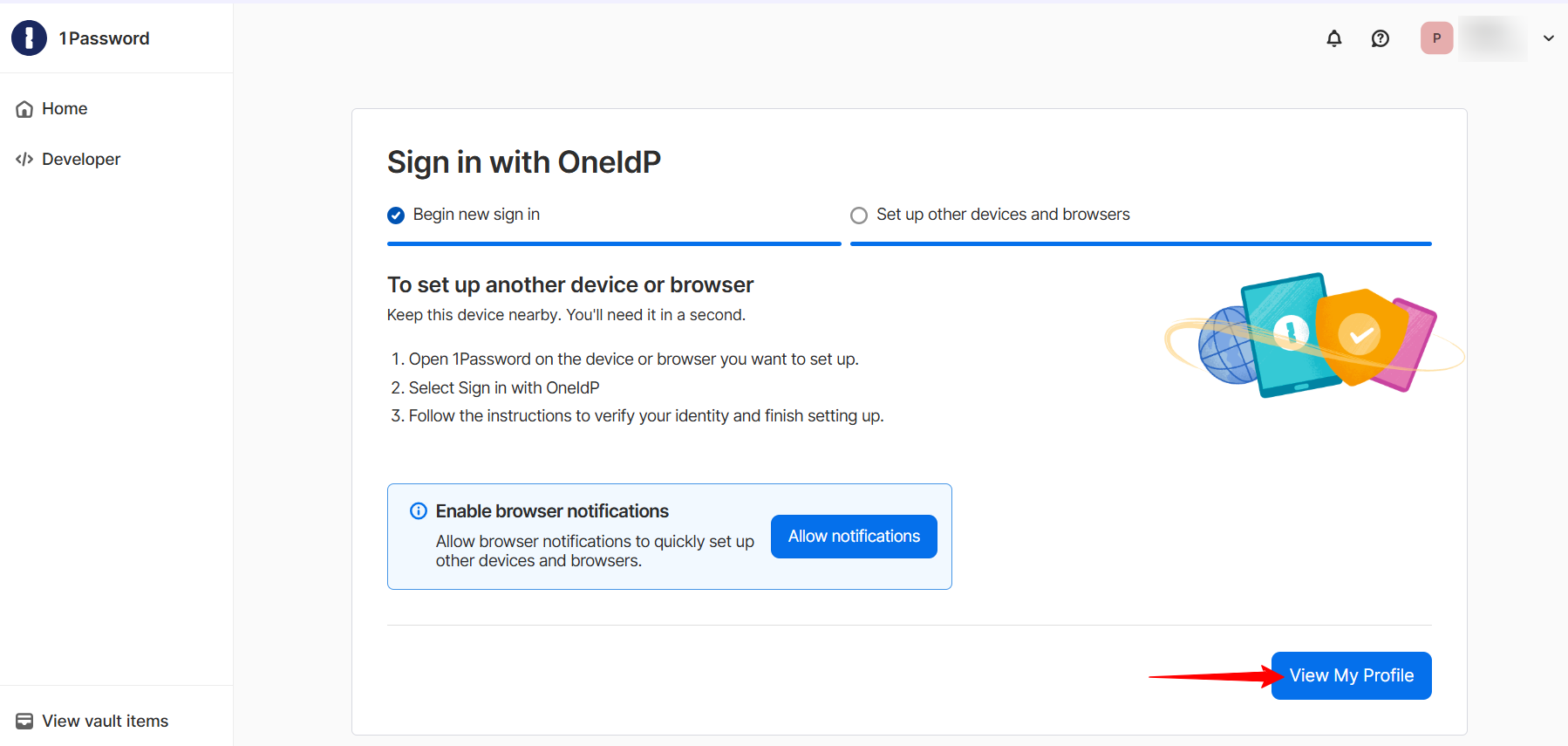
When a user logs into their 1Password account, they will encounter the following message. Click Get started.
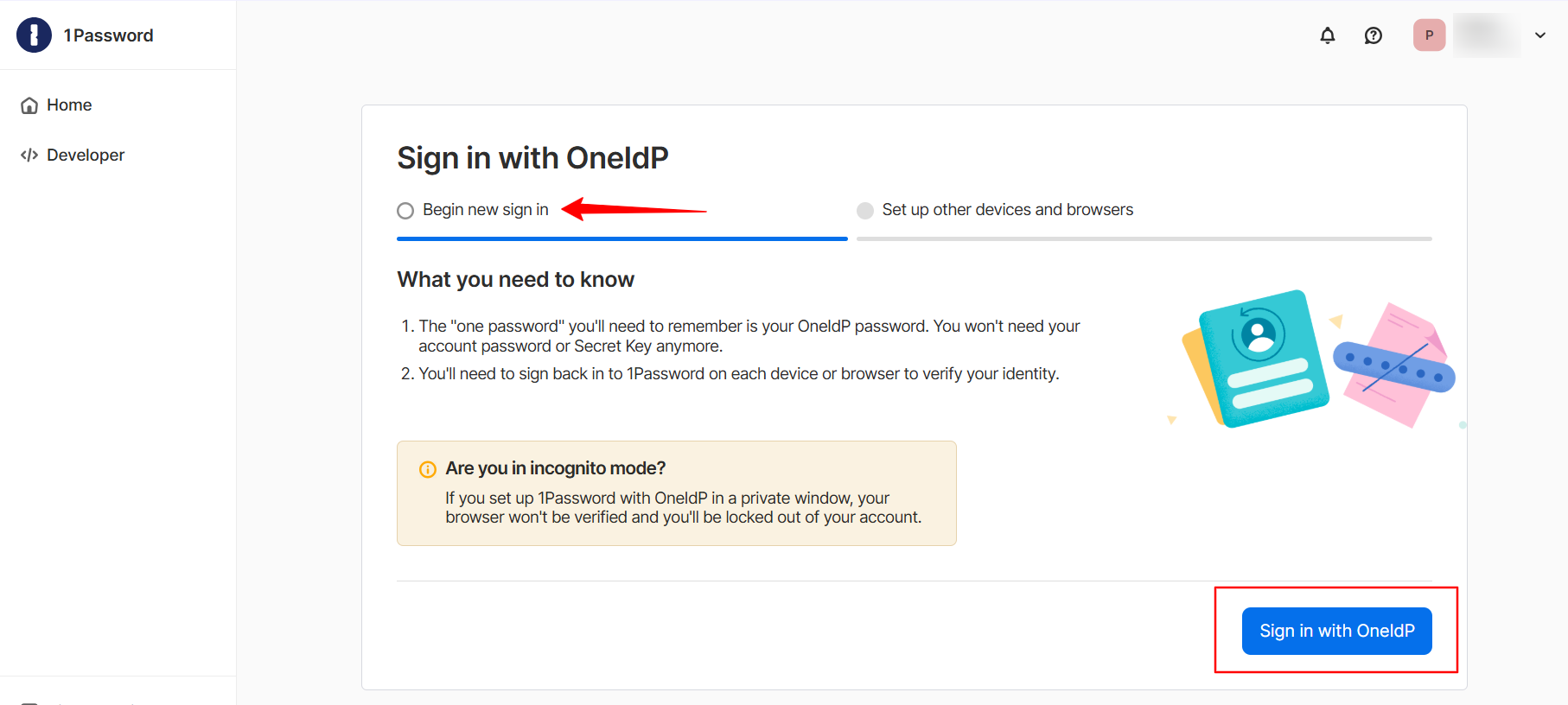
On the next page, click Sign in with OneIdP.
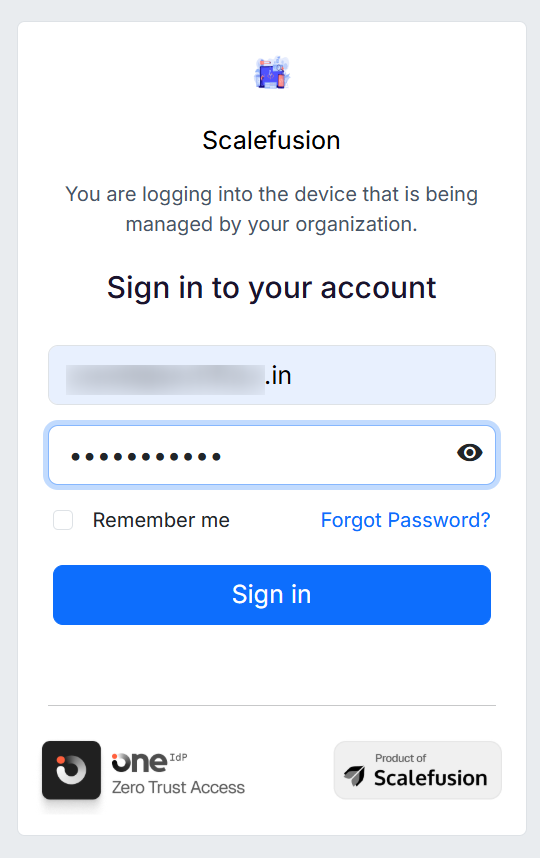
The user will be redirected to OneIdP screen, where they will have to enter their email ID and password.
The user will have to click Continue to grant the requested permissions.
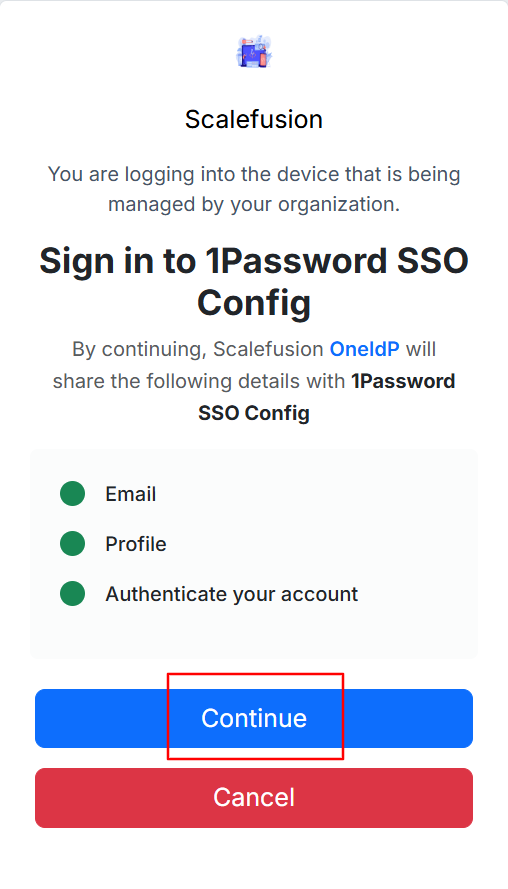
Once this is done, the user can view their profile and access their 1Password account.