- 23 Sep 2025
- 1 Minute to read
- Print
- PDF
SSO General Settings
- Updated on 23 Sep 2025
- 1 Minute to read
- Print
- PDF
Introduction
Setting up Single Sign-On (SSO) can vary depending on the protocol, but there are several core settings that remain consistent across both SAML and OIDC configurations. In this article, we’ll explore the common foundational elements of SSO setups, helping you streamline integration regardless of the protocol you choose.
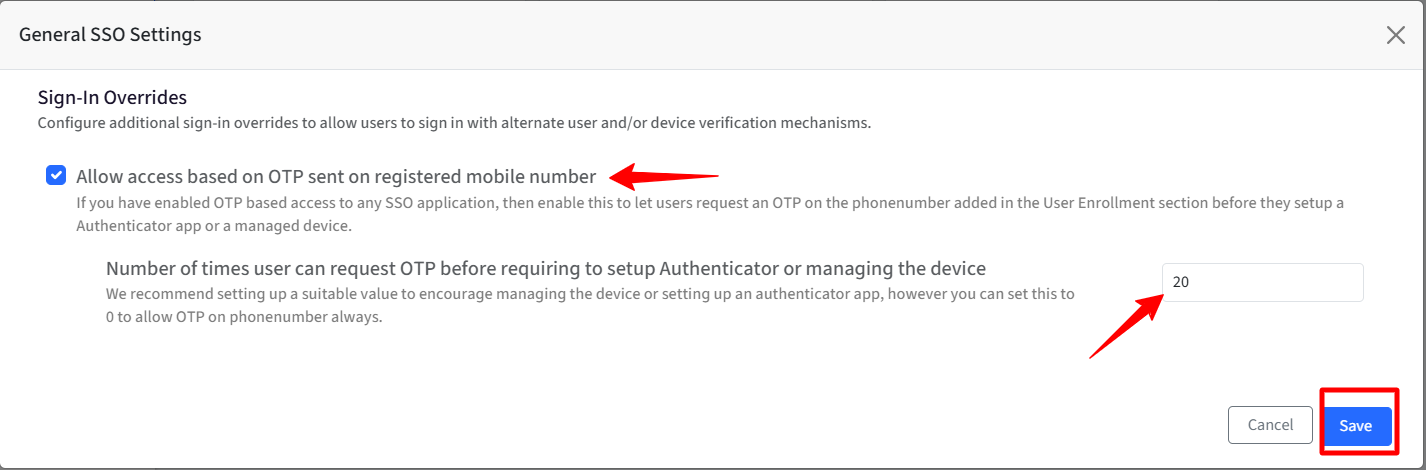
Sign-In Overrides during SSO experience
Configure additional sign-in overrides to allow users to sign in with alternate user and/or device verification mechanisms.
Allow access based on OTP sent on registered mobile number
If OTP-based access is enabled for any SSO application, activate this setting to allow users to receive an OTP on the phone number specified in the User Enrollment section before setting up an authenticator app or enrolling a managed device.
Prerequisites
Phone number is added for the users in the User Enrollment section.
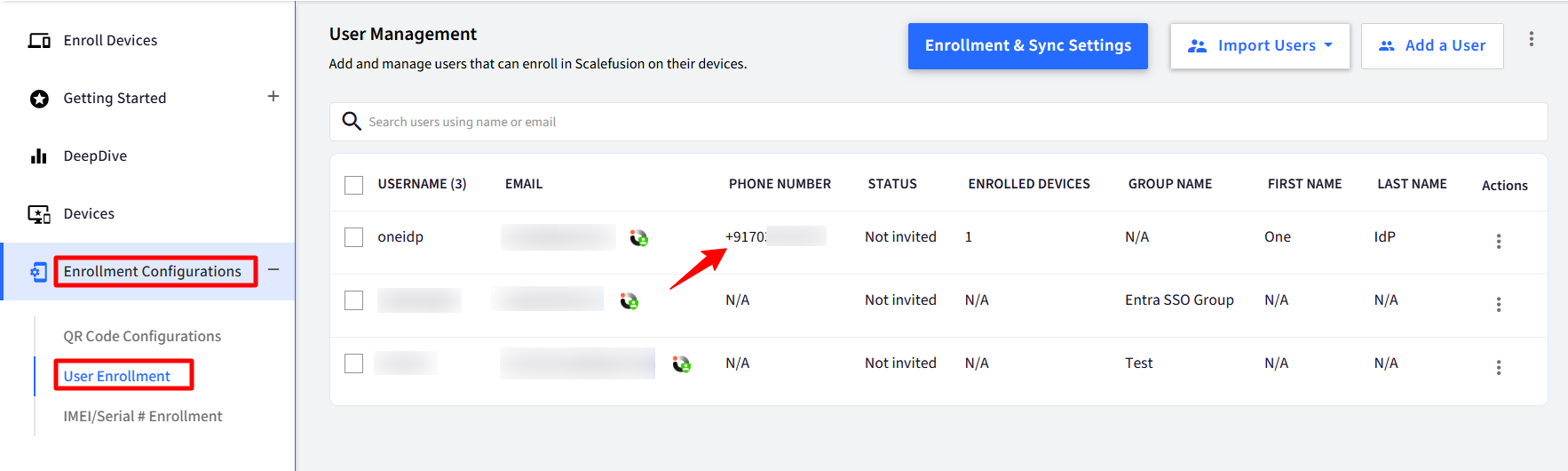
In the Directory settings, navigate to the relevant domain settings and enable “MFA using a third-party authenticator app” under the Multi-factor Authentication section.
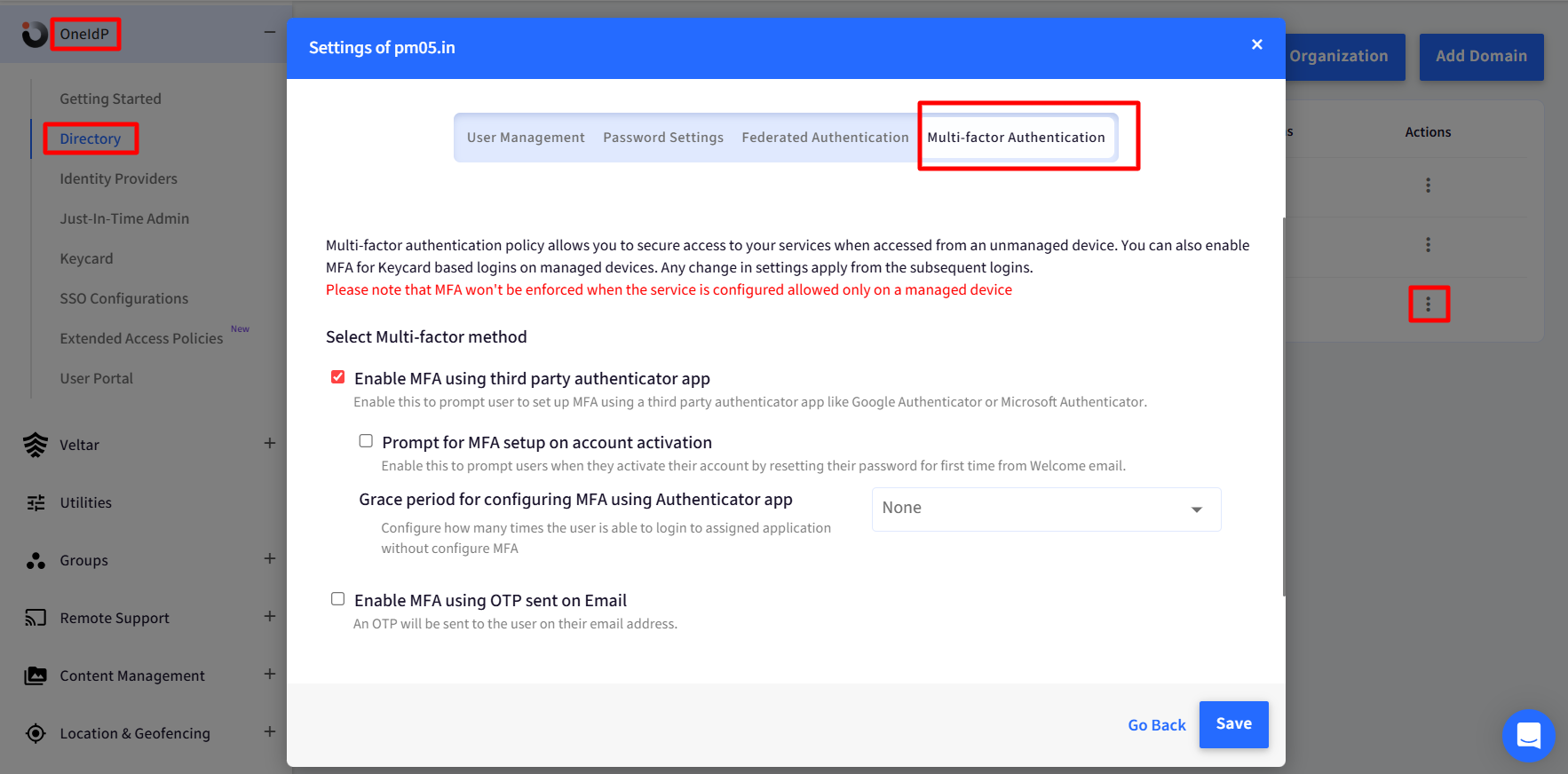
The SMS service provider details—Twilio, in this case—must be configured under Utilities > Global Settings > General Settings > SMS Service Provider Settings.
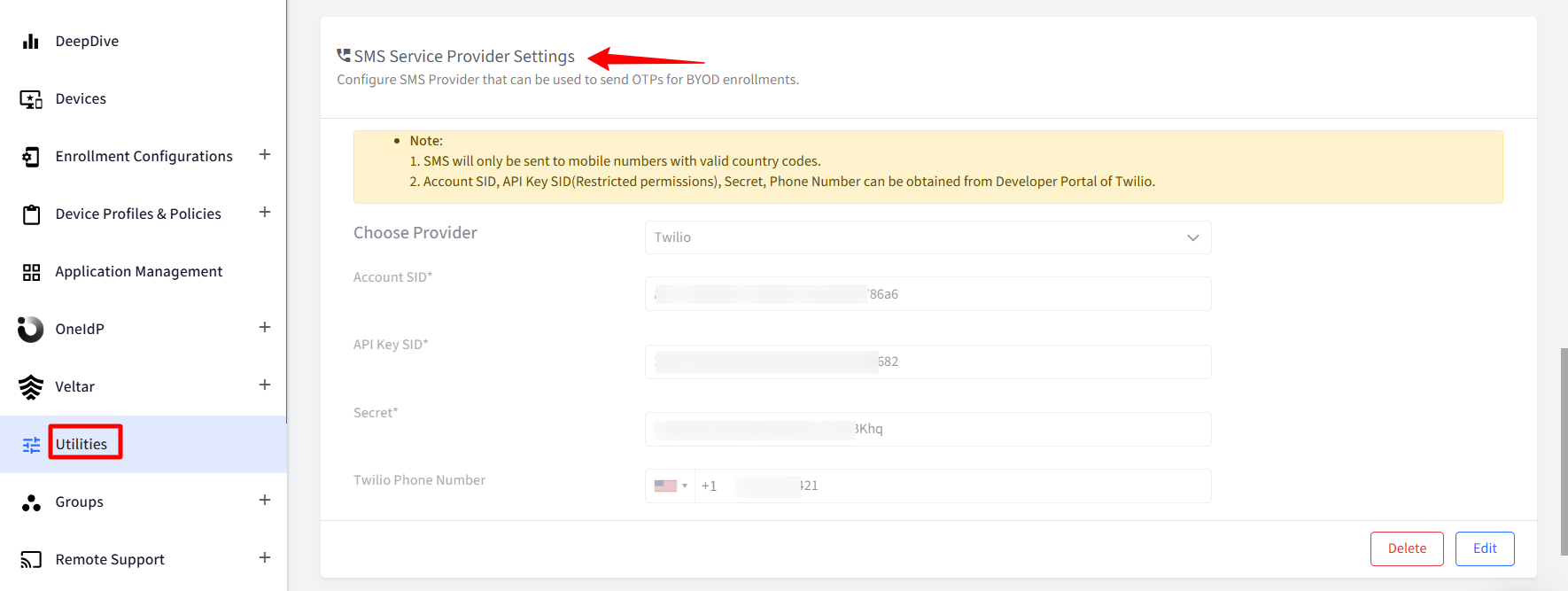
Please ensure that “Allow users to access by setting up MFA using third party authenticator app or OTP sent on email.” option is selected in the concerned SSO Configuration, under Conditional Access Settings.
Settings
Navigate to OneIdP > SSO Configurations > click General Settings.
Select the option “Allow access based on OTP sent on registered mobile number” under Sign-In Overrides during SSO experience.
Select “Number of times user can request OTP before requiring to setup Authenticator or managing the device” to set a value of how many times a user can request for an OTP. You can set the value between 0 and 20.
Click Save.
Note:
If the user exceeds the allowed number of OTP requests, they will be prompted to set up a third-party authenticator instead.
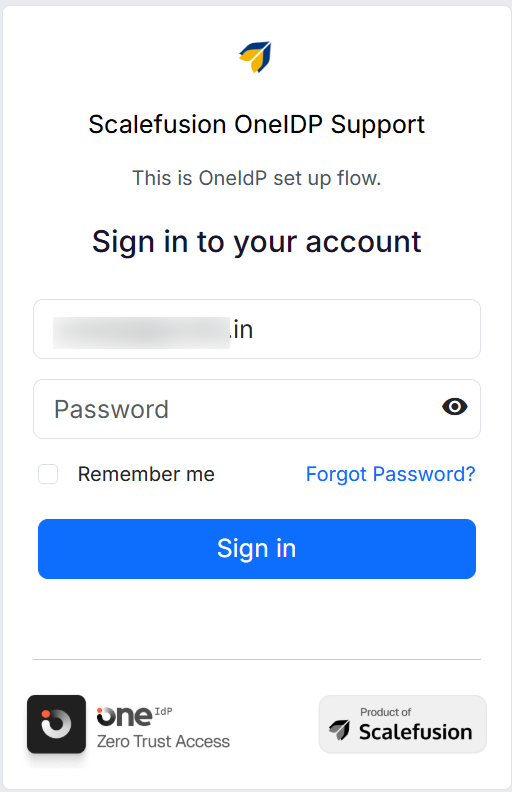
User Experience
When a user attempts to access an application or service from an unmanaged device, they will be redirected to the OneIdP login screen, where they must enter their email ID and password.
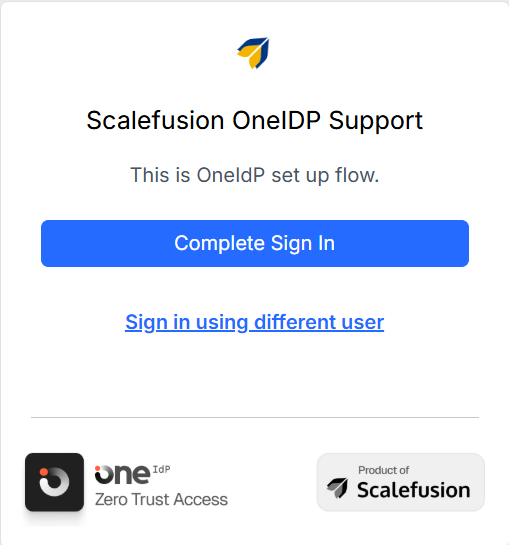
They will see the following screen. Click Complete Sign in.
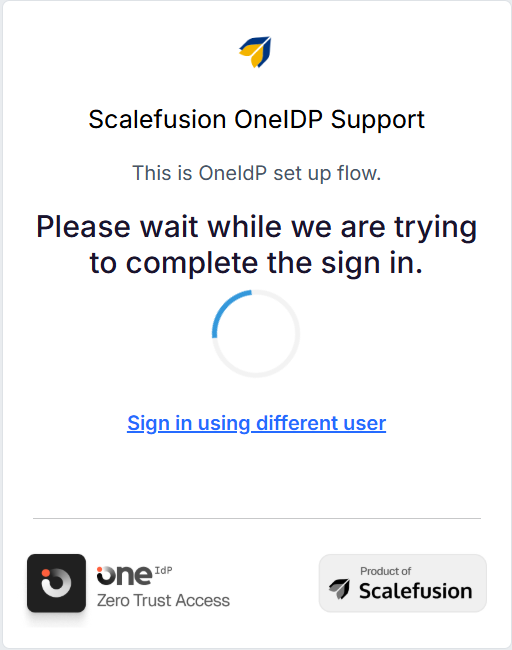
Scalefusion will perform a compliance check, after which users will be presented with the following screen.
Click Send SMS on Phone Number.
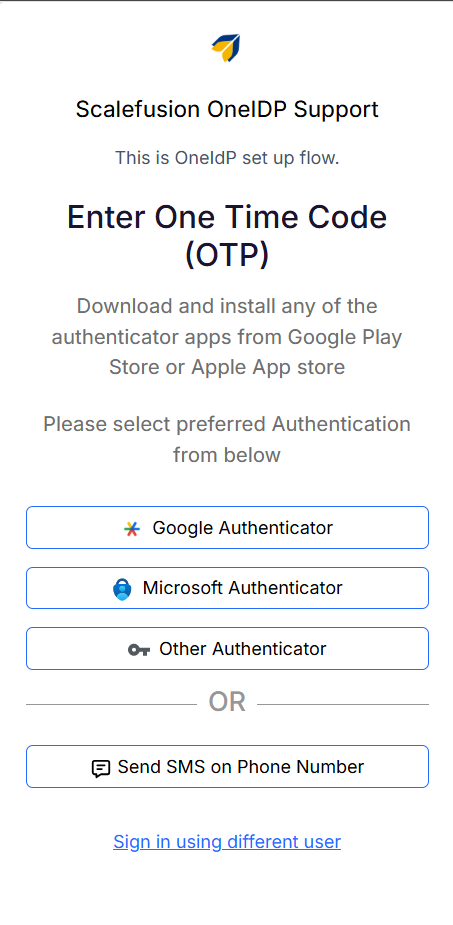
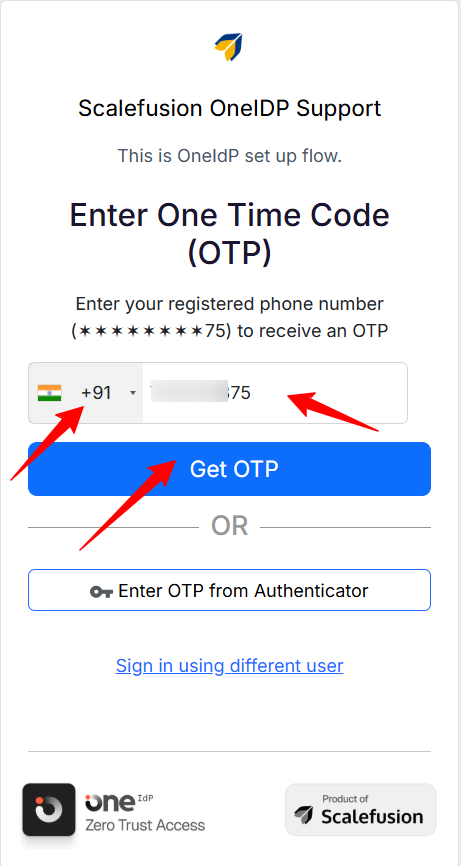
The user must enter the correct registered phone number along with the appropriate country code to receive the OTP.
At this step, the user must enter the OTP received on their registered phone number.
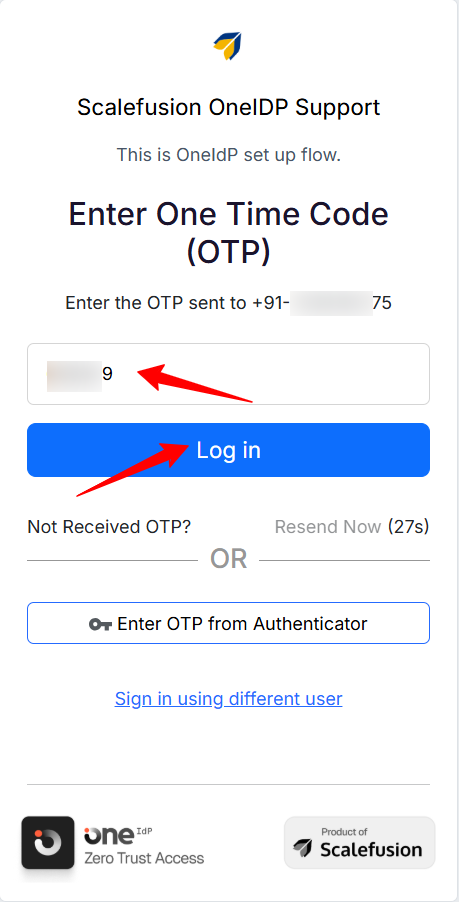
Once done, they will be able to log in.


