- 22 Sep 2025
- 3 Minutes to read
- Print
- PDF
Access Logs
- Updated on 22 Sep 2025
- 3 Minutes to read
- Print
- PDF
In a Zero Trust security model, visibility into access activity is as critical as the access control itself. Access Logs in Scalefusion’s OneIdP provide a granular and unified view of every sign-in attempt and service access event whether or not Extended Access Policies (XAP) are enforced. Access Logs capture extended attributes like device posture, policy evaluation results, IP address, geolocation, and application compliance. This information empowers IT and security teams to troubleshoot access issues, validate policy enforcement, monitor suspicious behavior, and support regulatory compliance all from a centralized and intuitive dashboard.
To access,
On Scalefusion Dashboard, navigate to OneIdP > Extended Access Policies > Access Logs
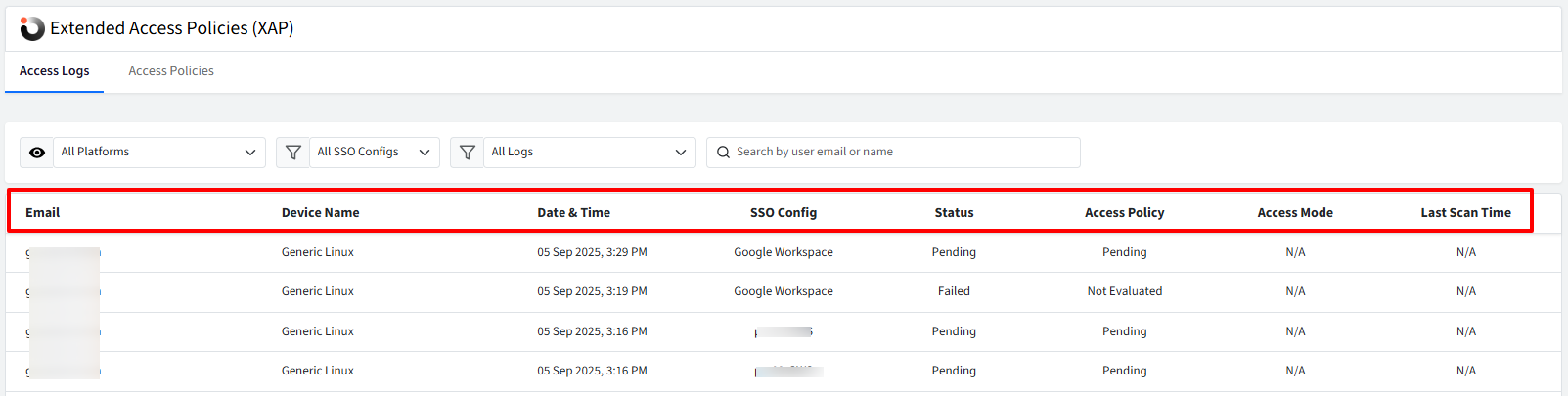
Log Entry Fields
Each access log entry provides detailed information across the following fields:
Email: The user’s email address used during the sign-in attempt.
Device Name: Name of the device from which the sign-in attempt was made.
Date & Time: Timestamp of the access attempt (displayed in your preferred time zone).
SSO Config: The SSO configuration that was accessed.
Status: Indicates the outcome of the access attempt based on XAP and SSO policy evaluation:
Pending – Sign-in was not completed (e.g., session timeout or incomplete auth flow).
Failed – Sign-in blocked due to failed XAP or SSO access policies.
Passed – All access policies (XAP and SSO) were met successfully.
Access Policy: Represents the result of SSO-level conditional access evaluation:
Not Evaluated: This status is displayed when XAP policy is Failed due to which Access policy will not be evaluated.
Passed: All SSO configuration policies passed.
Pending: Evaluation is still in progress.
Failed: Policy conditions were not met.
Note: XAP policies are evaluated first, followed by SSO-level policies such as browser policy and device management status (managed/unmanaged).
Access Mode: Specifies how the user accessed the service:
Scalefusion: Accessed via a managed device.
OneIdP Credentials: Used the Scalefusion Authenticator app on a managed device.
User Portal: Accessed via the Scalefusion user portal.
Other Authenticator App: Used a third-party authenticator or OTP (based on MFA settings in Directory Settings).
Last Scan Time: Timestamp of the most recent scan performed on the device.
In the Access Logs, we display entries for Keycard Login and Enrollment. For these events, the SSO configuration will appear as N/A.
Displaying Access Details
Clicking on a log entry opens a side card view with detailed information related to the access attempt. This information is grouped under the following sections:
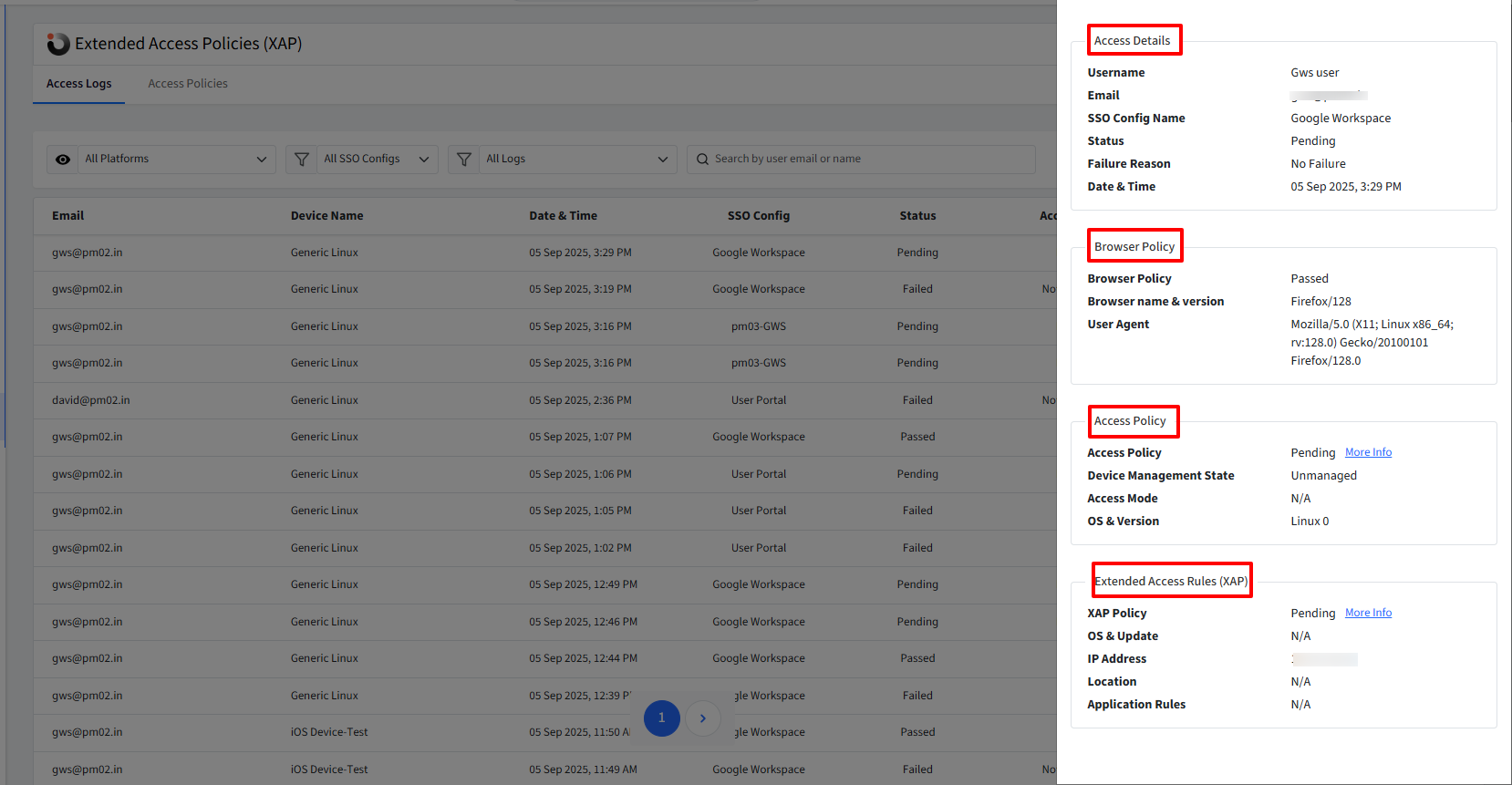
Access Details
Basic information about the access attempt:
Username – Name of the user attempting sign-in.
Email – User’s email address.
SSO Config Name – The SSO configuration used.
Date & Time – Timestamp of the access attempt.
Status – Overall access result:
Passed – Sign-in was successful.
Failed – Sign-in was blocked.
Pending – Sign-in attempt not completed.
Failure Reason – Reason for failure, if applicable (e.g., failed browser policy, access policy, or XAP rule).
Browser Policy
Details of the browser policy evaluation:
Browser Policy – Pass or Fail.
Browser Name & Version – The browser used for sign-in.
User Agent – Complete user-agent string of the browser.
Access Policy (SSO Configuration Policy Evaluation)
Shows results of policies applied within the SSO configuration:
Access Policy – Pass, Fail, Pending, or Not Evaluated. More Info reveals:
Status – Final policy evaluation result.
Access Policy – Policy type (e.g., Managed, Unmanaged, MFA, etc.).
Device Management State – Managed, Unmanaged, or Not Evaluated.
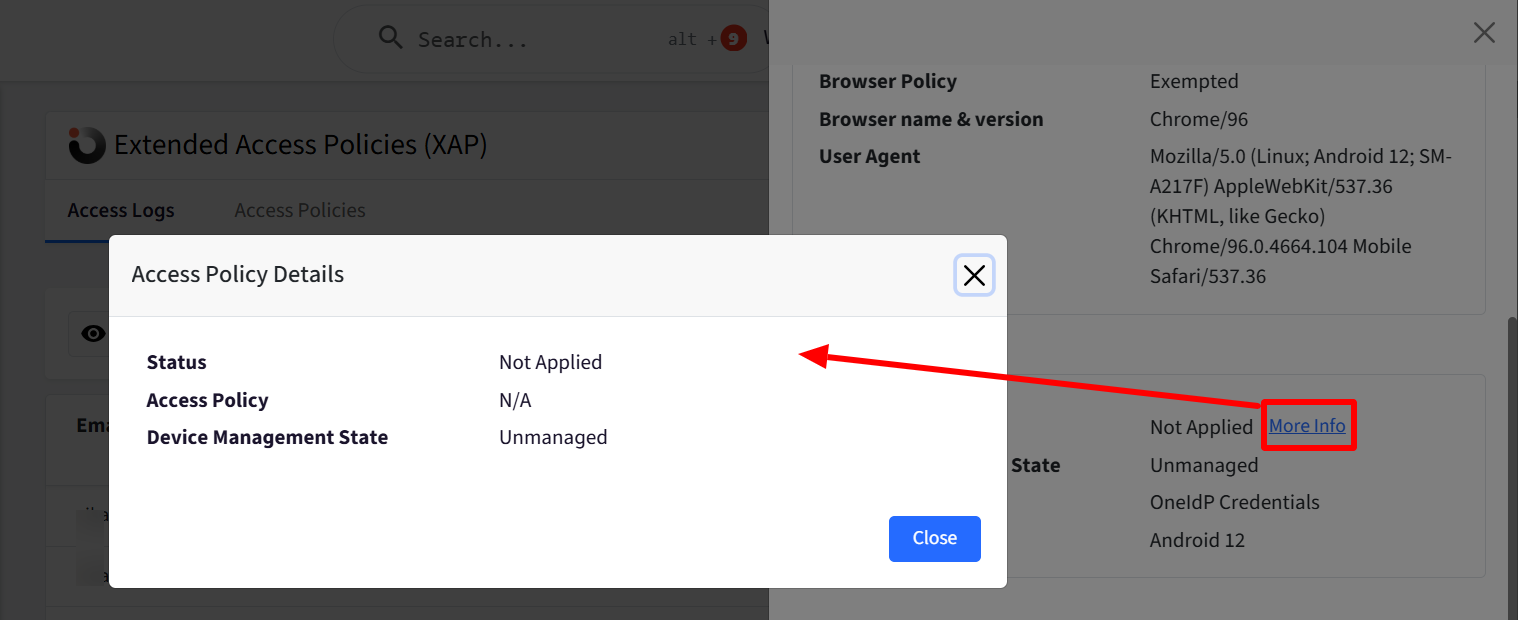
Access Mode – How access was attempted:
Scalefusion – From a managed device.
OneIdP Credentials – Using the Scalefusion Authenticator app.
User Portal – Via Scalefusion’s user portal.
Other Authenticator App – Third-party apps or OTP (based on MFA settings).
OS & Version – Operating system and version used during sign-in.
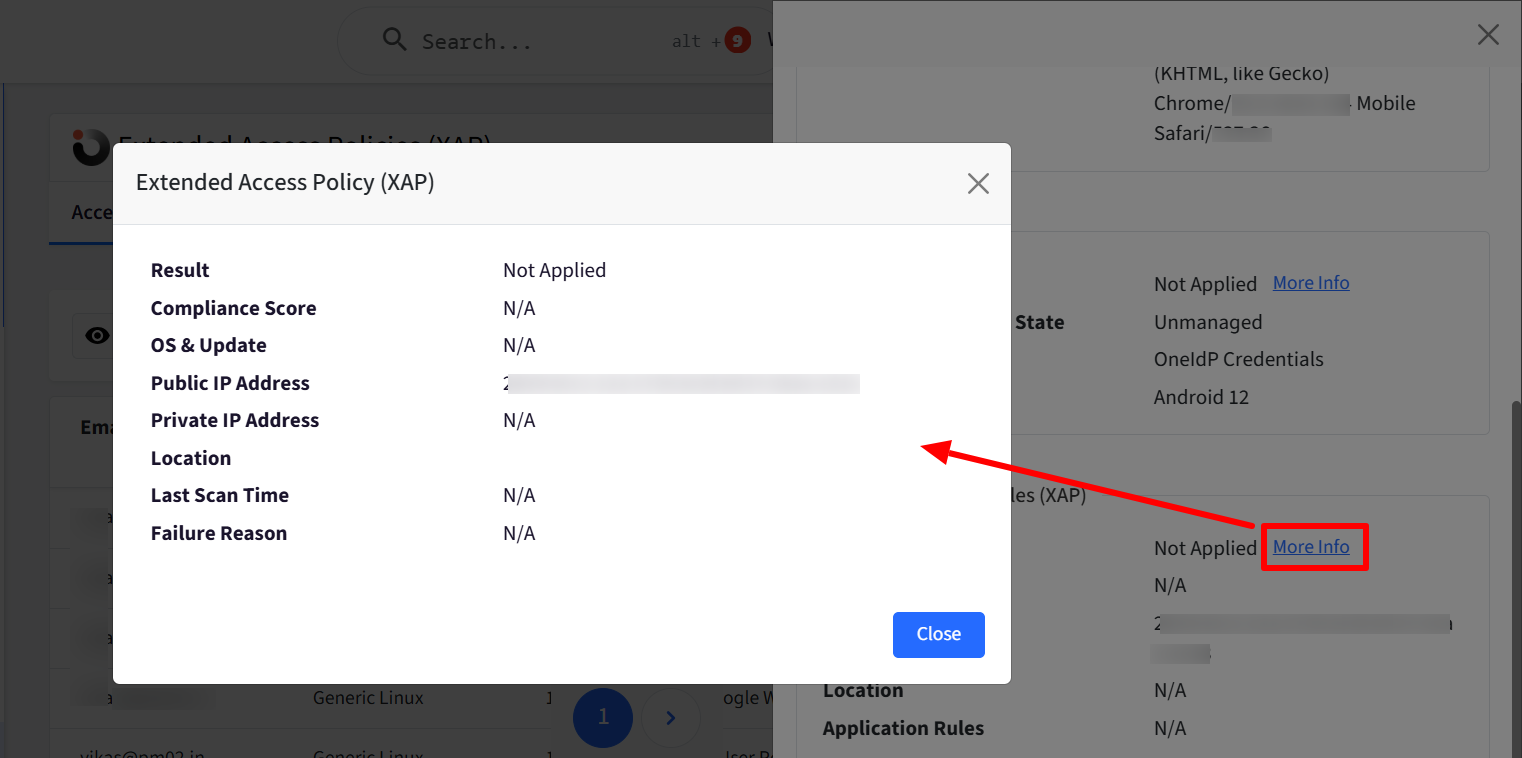
Extended Access Rules (XAP Policy Evaluation)
This section presents the evaluation of Extended Access Policies:
XAP Policy – Pass, Fail, Not Applied, or Not Evaluated. More Info provides additional insights:
Result – Final outcome of XAP evaluation.
Compliance Score – Last reported score from Veltar Compliance.
OS & Updates – OS update and patch status (Pass or Fail).
Public IP Address – Last known public IP of the device.
Private IP Address – Private/local IP of the device.
Location – GeoCode (latitude & longitude) of the access attempt.
Application Rules – Status of required application checks (Pass, Fail, or N/A).
Last Scan Time – Timestamp of the last compliance scan.
Failure Reason – If failed, reason will be specified here.
Additional Features
Filters
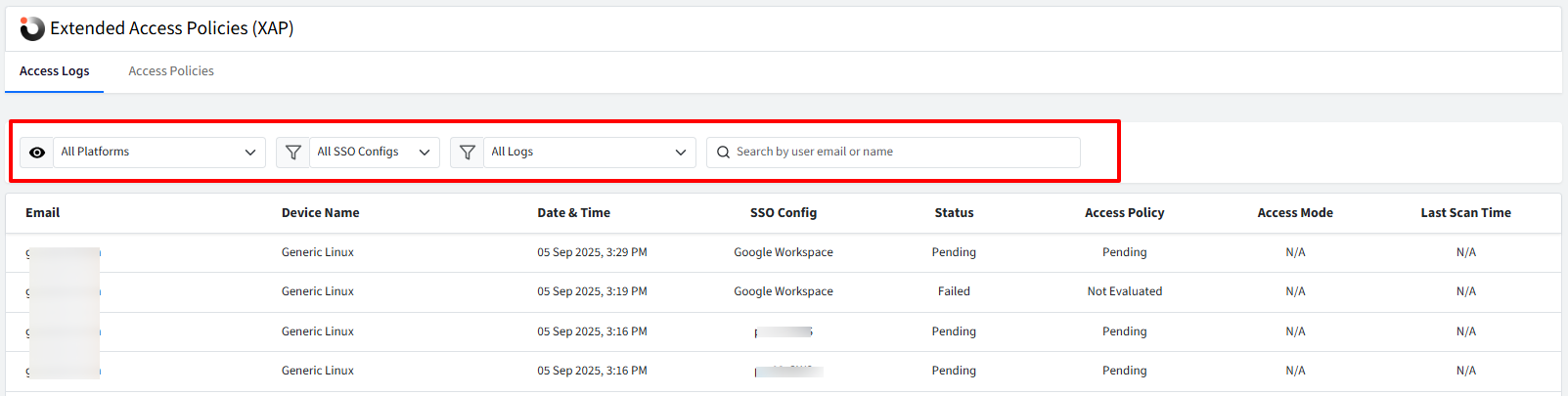
You can filter access logs based on various criteria. You can filter them by:
All Platforms
Android
iOS/iPadOS
macOS
Windows
Linux
ChromeOS
All SSO Configs: Displays all the SSO Configs. You can choose a specific configuration
All Logs (as per status)
Pending
Passed
Failed
Search Bar
Search by user email or name