- 06 May 2025
- 3 Minutes to read
- Print
- PDF
Securing Outlook/M365 in iOS/iPadOS
- Updated on 06 May 2025
- 3 Minutes to read
- Print
- PDF
Introduction
Scalefusion’s OneIdP helps organizations secure access to Microsoft 365 applications like Email, OneDrive, and other applications by allowing them to be accessed only on Scalefusion-managed devices. On iOS and iPadOS devices, though OneIdP has the required checks to allow access from a managed device, due to the behavior of iOS/iPadOS applications, OneIdP cannot detect if the app itself is managed or not. Because of this behavior, the end users may access corporate data from a managed device but from an unmanaged application.
This document outlines the steps that an IT Administrator can take to ensure that this platform limitation can be safely prevented.
Step 1: Restrict OAuth App access to selected Permissions
OAuth applications are third-party applications that use Microsoft Graph OAuth APIs to access Email and other functionality. By default, an end user can use any Email app to sign in to their corporate email and grant the required permissions. Examples of such applications are iOS/iPadOS Native Email app, Edison Email app, and others.
Since all these OAuth applications use Web-based modern authentication, during Sign-in, users are redirected to OneIdP for authentication. Since there is no standard way to detect which app has triggered the authentication, OneIdP just checks for the device management state, and if the device is managed, then it allows access. This allows end users to access Email from unapproved applications.
IT Administrators can prevent this by classifying the permissions that an end user can give to a 3rd party application by following the steps below:
Log in to the Entra ID portal (https://portal.azure.com) with Admin credentials.
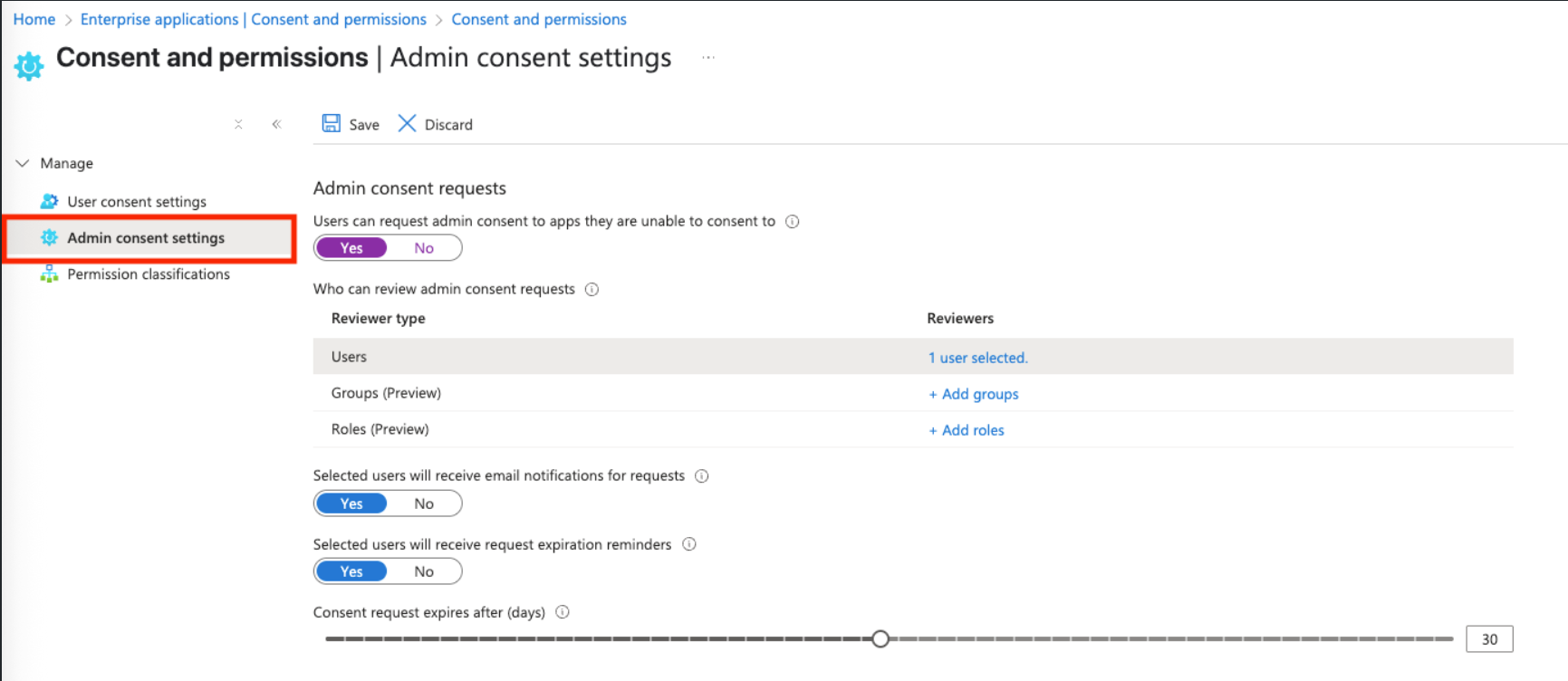
Navigate to Enterprise Applications > Security > Consent and Permissions.
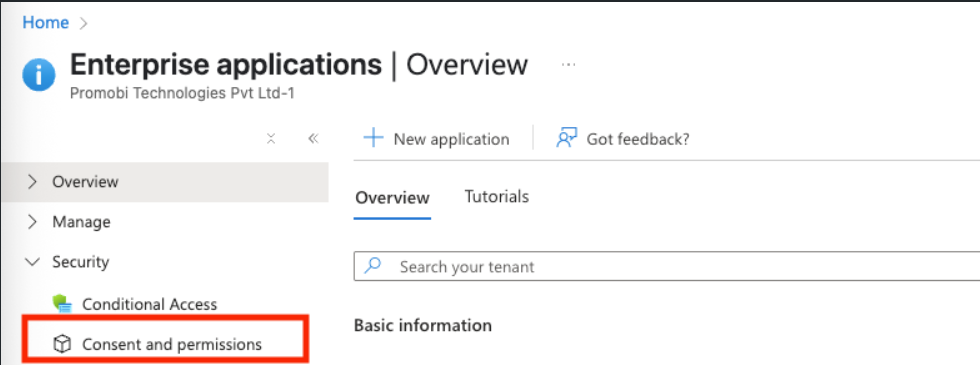
Click on Permission Classifications.
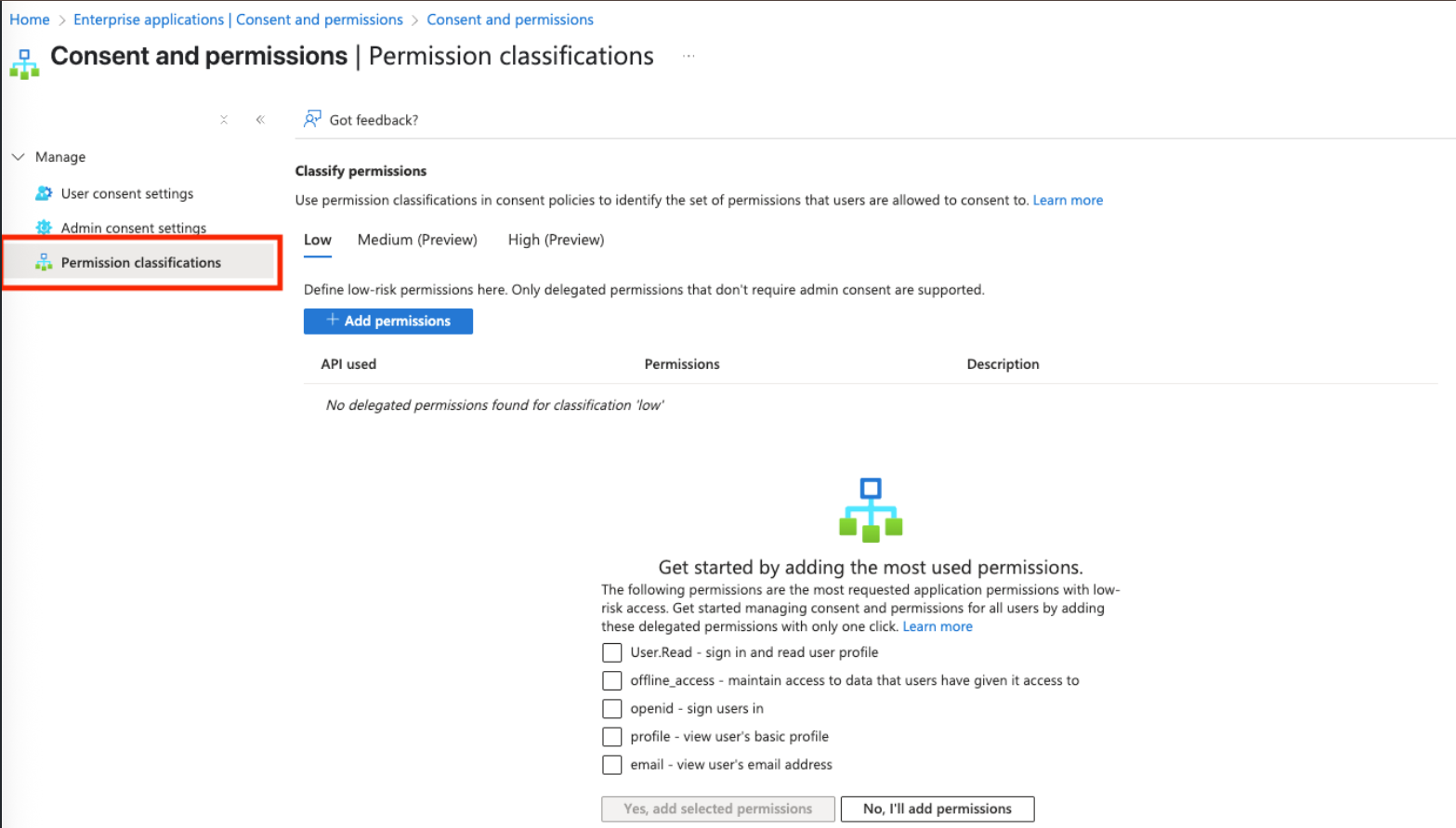
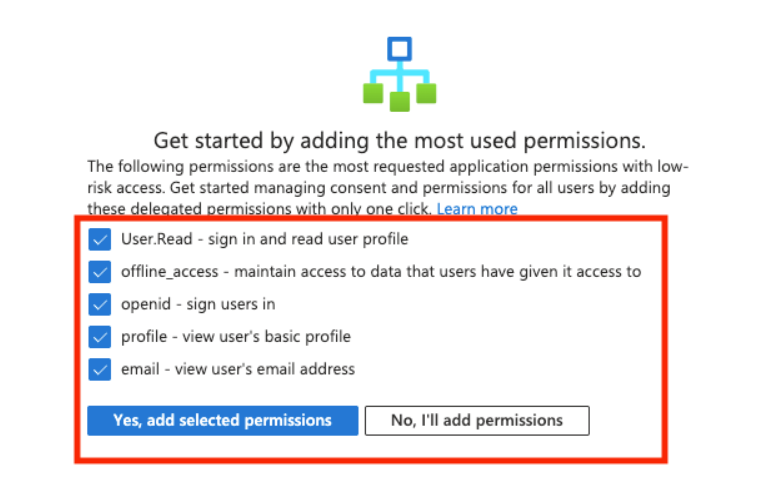
Select all permissions displayed under the most used permissions and click Yes, add selected permissions.
If you don’t see this section, click on + Add Permissions and all the permissions under the Microsoft Graph section.
Most applications that you use in your organization should be covered by adding the most used permissions; however, if your organization uses applications that require more permissions to be granted by end users, then click on + Add Permissions and select the other permissions.
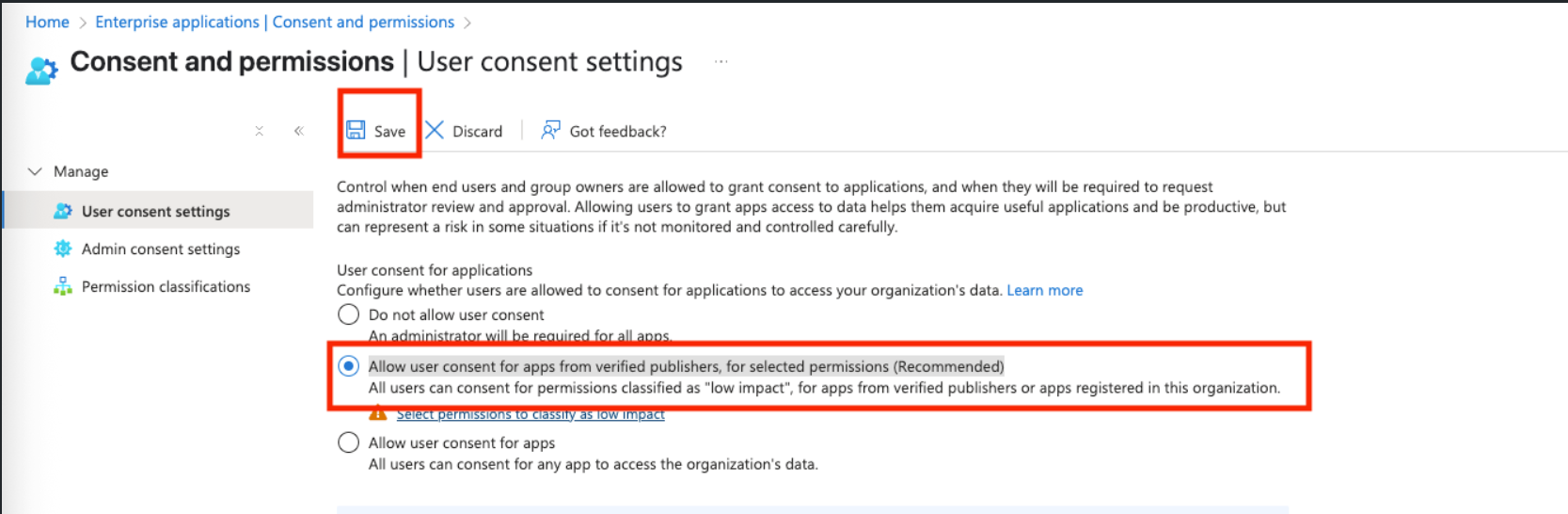
Now navigate to User consent settings and select Allow user consent for apps from verified publishers, for selected permissions (Recommended), and click on Save.
Additionally, you can configure Admin consent settings and allow users to request permissions to use applications that require more permissions than what you have allowed.
Note:
We recommend reviewing all the existing 3rd party native and web applications that are using Microsoft Graph APIs and add all such permissions to the list.
Step 2: [Optional] Allowing iOS/iPadOS Mail app for corporate Email
Since in Step 1, we have limited the permissions that an OAuth app can be granted by end users, it will prevent end users from accessing corporate email from the native Email app as well.
However, if you want to allow your users to access corporate Email via iOS/iPadOS native email app, then you would have to perform the following steps:
From the Scalefusion console, configure Exchange settings and publish to the Device Profiles. This ensures that the native Mail app treats this as a managed configuration and the MDM-based policies are automatically applied.
Post this, you can either wait for a user to request access to the native Mail app (based on the Consent settings that you configured in Step 1), or the recommended way would be to:
Sign in to the Mail app using an admin's credentials and grant access to the app.
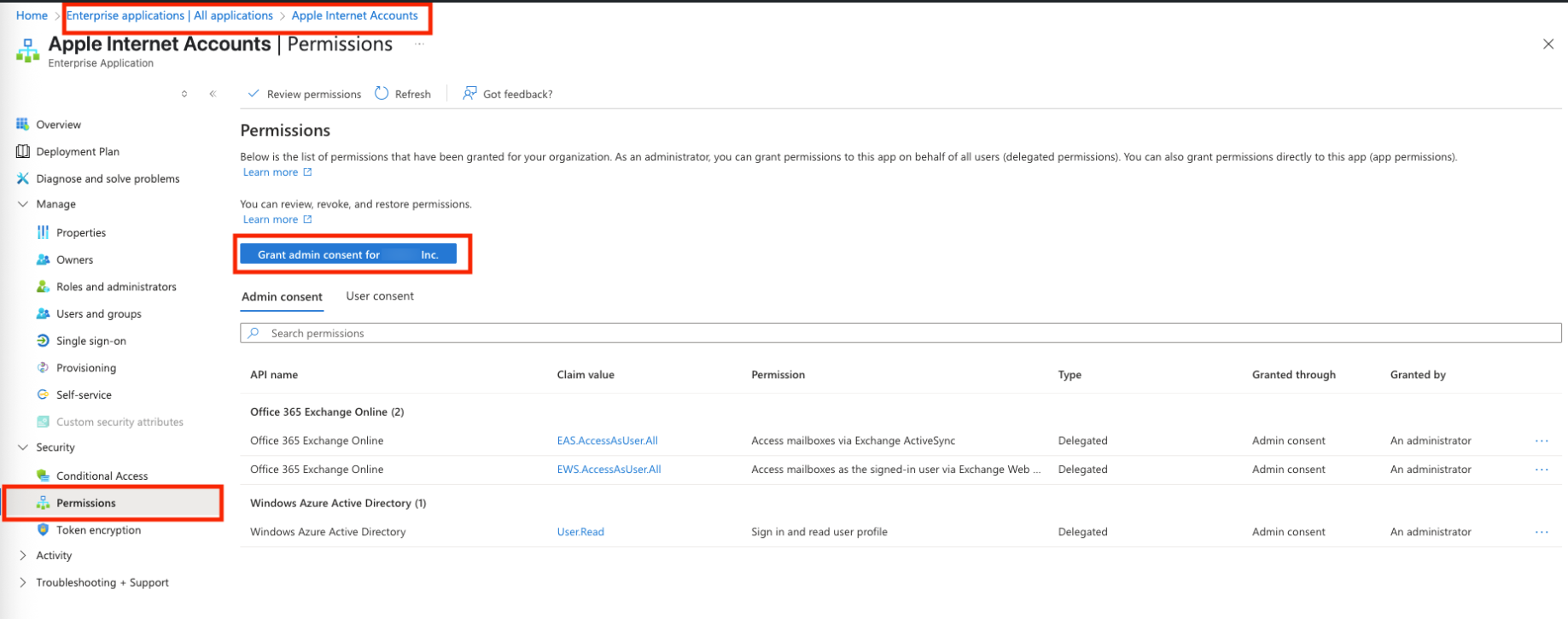
Once you have signed in, the Mail app will be added to your Enterprise Applications in the Entra portal and listed as Apple Internet Accounts. To grant access to all users at an org-level:
Log in to the Entra portal.
Navigate to Enterprise Applications and click on Apple Internet Accounts.
Expand the Security tab and click on Permissions.
Click on Grant admin consent for %org_name%
Note:
Please note that these steps can be followed to provide access to any third party applications that are approved in your organization.
Step 3: Manage Outlook and other Microsoft 365 applications
Now that you have made sure that only approved applications can access Email in your organization, please go ahead and configure OneIdP SSO for Microsoft 365 and publish Outlook and other Microsoft 365 applications along with app configurations as described in our help document here.








