- 26 Feb 2025
- 9 読む分
- 印刷する
- PDF
Windows OS Update Management
- 更新日 26 Feb 2025
- 9 読む分
- 印刷する
- PDF
One of the critical pieces of managing Windows 10 devices is to manage the Windows OS updates. It is important for organisations to define a policy that either automates or controls the various updates that Windows offers like the OS updates, feature updates and security patches.
Scalefusion lets the IT Admins configure the OS update policy on the managed Windows 10 devices so that they can ensure that the rollouts are controlled. Furthermore you can control which components to auto update and selectively updates others.
If you have configured updates that require your approval then, Scalefusion also offers to check updates at a device or a device group level and apply pending updates.
This document walks you through the various policies on offer around OS updates.
Configuring Windows OS Update Policy
IT Admins can configure a Windows OS update policy for the managed devices by creating a Device Profile and applying to the devices. We suggest you create a Test profile and apply them to a set of test devices to verify the behavior before you make the changes to your main device profile applied to production devices.
The policies related to OS updates are provided in Windows Device Profile. Start by creating a Windows Device Profile or Edit an existing one. Navigate to Device Profiles & Policies > Device Profiles and edit an existing profile or create a new Windows profile.
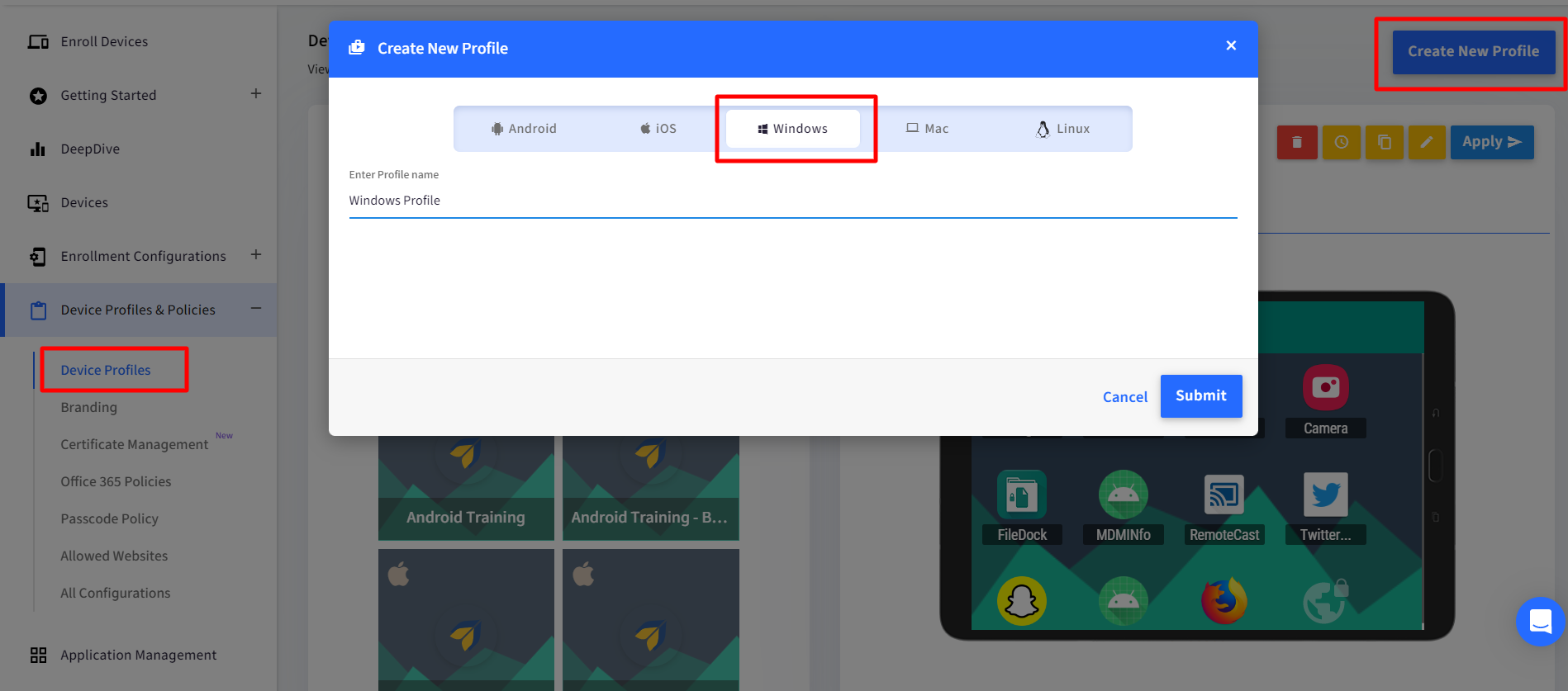
In the Device Profile, navigate to Settings > Windows Updates > Windows MDM Based Settings section to start defining the OS update policy.
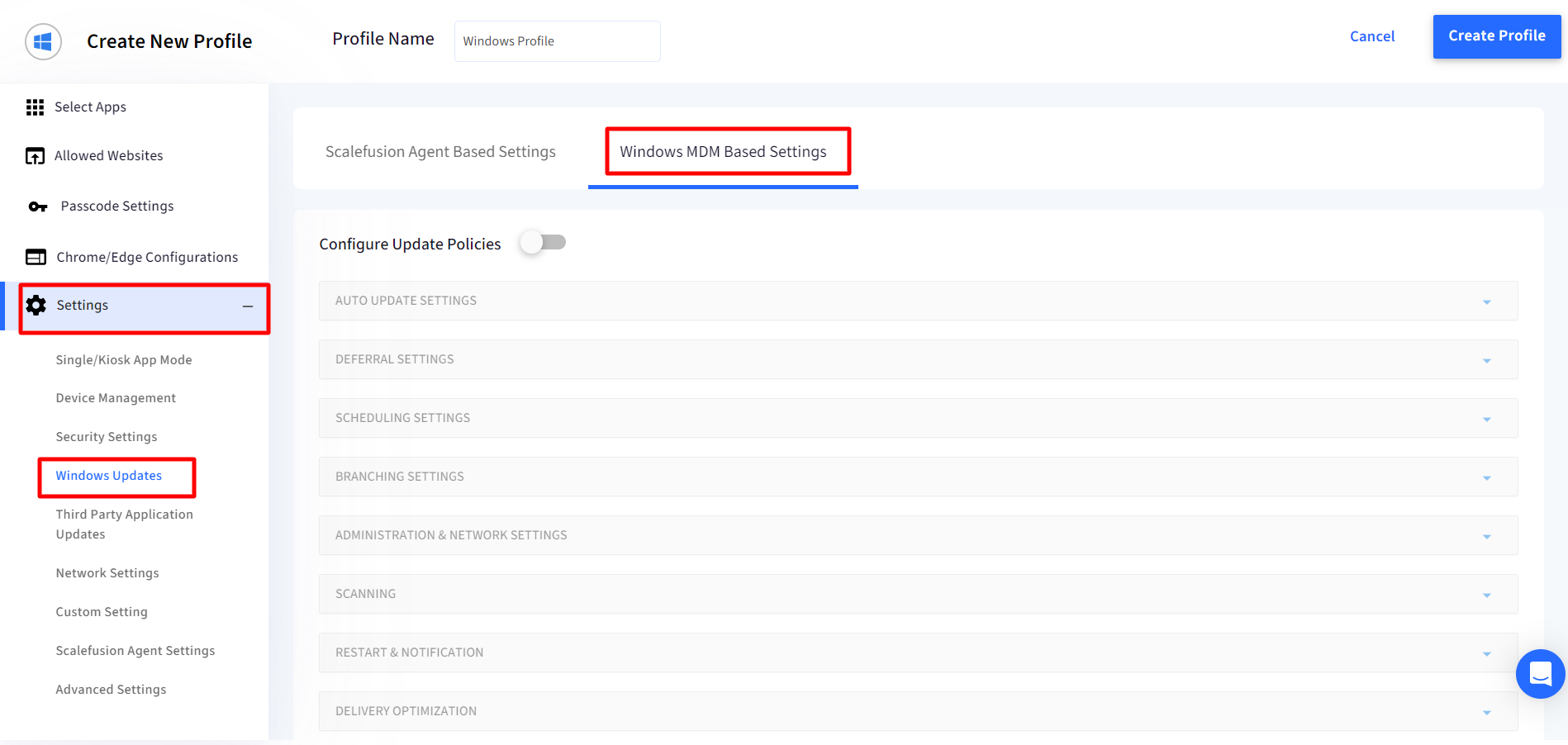
To configure the Windows Update policies for all the devices to which this profile is applied, enable Configure Windows Policies. Once you enable this you can configure the various settings by clicking on the section and expanding it.
Auto Update Settings: This section helps you control the automatic updates behaviour.
Setting
Description
Active Hours Start
Configure a start time for the active hours that prevents the device from rebooting. Works in combination with end time.
Active Hours End
Configure an end time for the active hours that prevents the device from rebooting. Works in combination with the start time.
Active Hours Max Range
The max range for the active hours during which the device is not rebooted capped at 18 hours
Auto Update
Configure automatic update behaviour by selecting one of the options below,
Notify the user before downloading the update
Auto install the update and then notify the user to schedule a device restart
Auto install and restart
Auto install and restart at a specified time
Auto install and restart without end-user control
Turn off automatic updates
Automatic Maintainance Wake Up
Update Notification Level
Control the Notification behaviour for updates by selecting one of the options below,
Use default Windows Update notifications
Turn off all, excluding restart warnings
Turn off all, including restart warnings
Fill Empty Cell URLs
Deferral Settings: Choose how you would like to defer the OS updates by configuring these settings,

Setting
Description
Defers Feature Updates
Defers Feature Updates for the specified number of days.
Pause Feature Updates
Allows IT Admins to pause Feature Updates for up to 60 days.
Configure Deadline for Feature Updates
Allows IT admins to specify the number of days before feature updates are installed automatically. Updates and restarts will occur regardless of active hours.
Defers Quality Updates
Defers Quality Updates for the specified number of days.
Pause Quality Updates
Allows IT Admins to pause Quality Updates up to 35 days.
Configure Deadline for Quality Updates
Allows IT admins to specify the number of days before quality updates are installed automatically. Updates and restarts will occur regardless of active hours.
Configure Deadline for Grace Period
Add grace period to the deadlines for quality and feature updates before the device restarts automatically.
Configure Deadline for No Auto Reboot
If enabled then devices will not automatically restart outside of active hours until the deadline for feature and/or quality updates are reached, even if applicable updates are already installed and pending a restart.
Feature Update Uninstall Period
Enable IT admin to configure feature update uninstall period.
Scheduling Settings: Configure a schedule for OS updates to be installed,

Setting
Description
Schedule Install Day
Configure if you want to install updates everyday or a specific day.
Schedule Install Week
Configure if you want to install updates every week or a specific week of the month.
Schedule Install Time
Enables the IT admin to schedule the time of the update installation.
Branching Settings: Configure the settings that are under development but applicable on Windows Insider preview builds.

The options are,
Setting
Description
Update Branch
Configure this policy to specify the branch from which a device receives its updates. Following are the options to select from:
Semi-annual Channel (Targeted): Organizations will receive updates twice a year, with new features and capabilities that have been tested and validated by Microsoft.
Windows Insider build - Fast: This is the most active and frequently updated level, providing users with access to the latest features and improvements
Windows Insider build - Slow: The builds released in this channel are more stable and have undergone additional testing compared to the "fast" level thereby being more reliable for daily use.
Release Windows Insider Build
Manage Preview Builds
Configure this policy to control the updates you should receive prior to the update being released globally, from the following:
Disable preview builds
Disable preview builds once the next release is public
Enable preview builds
Microsoft App Updates
Allow/Disallow scanning of Microsoft app updates
WSUS Server URL
Provide WSUS Server URL to fetch updates offered from Windows Server Update Service (WSUS)
Allow Update Service
Specify whether the device could use Microsoft Update, Windows Server Update Services (WSUS), or Microsoft Store. Enabling this policy will disable the device's ability to retrieve information from public services like Windows Update and the Microsoft Store.
Allow Non Microsoft Signed Updates
This feature allows IT administrators to control whether Automatic Updates will accept updates signed by sources other than Microsoft.
Alternate Intranet server for Updates
Specify an alternate intranet server to host updates from Microsoft Update. This update service can then be used to automatically update computers on your network. Specify a server on your network which will function as an internal update service.
Exclude Drivers Update
Windows Update includes updates that have a Driver classification. Enabling this setting will exclude Windows Update (WU) drivers during Quality updates.
Administration & Network Settings: In this section configure the updates that should be automated and the ones that should be blocked.

Setting
Description
Require Update Approval
Enable this to configure which updates should be automatically applied and which would require IT Admins approval.
Once this policy is applied to a device, it cannot be reverted and the IT Admin has to apply the pending updates from Scalefusion Dashboard or locally on the device.
From the list, select the components that will be automatically updated. Any item that is not checked will not be updated automatically and the IT Admin would have to install them from Scalefusion Dashboard or locally on the device.
Application
Connectors
Critical Updates
Definition Updates
Developer Kits
Feature Packs
Guidance
Security Updates
Service Packs
Tools
Update Rollups
General
Disable UI/UX to Pause Windows Update
When this policy is enabled, the user cannot access the "Pause updates" feature.
Disable UI/UX to Scan Windows Update
When this policy is enabled, the user cannot access the Windows Update scan, download, and install features.
Allow Auto Update over Metered Network
Allow updates to be downloaded over a metered network connection.
Scanning: In this section configure the scan frequency for updates.

Settings
Description
Detection Frequency
Specifies the scan frequency from every 1 - 22 hours. Default is 22 hours.
Disable Dual Scan
Do not allow update deferral policies to cause scans against Windows Update. With the policy enabled, those scans are prevented, and the deferral policies work as expected.
Restart and Notification: Configure the device restart and notification settings in this section.

Settings | Description |
Engaged Restart Deadline (Quality Updates) | Specify the deadline in days before automatically scheduling and executing a pending restart outside of active hours for Quality Updates. |
Engaged Restart Deadline (Feature Updates) | Specify the deadline in days before automatically scheduling and executing a pending restart outside of active hours for Feature Updates. |
Engaged Restart Snooze Schedule (Quality Updates) | Specify the number of days a user can snooze Engaged restart reminder notifications for Quality Updates. |
Engaged Restart Snooze Schedule (Feature Updates) | Specify the number of days a user can snooze Engaged restart reminder notifications for Feature Updates. |
Engaged Restart Transition Schedule (Quality Updates) | Specify the timing before transitioning from Auto restarts scheduled outside of active hours to Engaged restart for Quality Updates in days. |
Engaged Restart Transition Schedule (Feature Updates) | Specify the timing before transitioning from Auto restarts scheduled outside of active hours to Engaged restart for Feature Updates in days. |
Auto Restart Deadline Period (Quality Updates) | Specifies the deadline in days before automatically executing a scheduled restart outside of active hours for Quality Updates. |
Auto Restart Deadline Period (Feature Updates) | Specifies the deadline in days before automatically executing a scheduled restart outside of active hours for Feature Updates |
Schedule Imminent Restart Warning | Specify the period for auto-restart imminent warning notifications in minutes. |
Schedule Restart Warning | Specify the period for auto-restart warning reminder notifications in hours. |
Auto Restart Notification Schedule | Specify the period for auto-restart reminder notifications in minutes. |
Auto Restart Required Notification Dismissal | Specify the method by which the auto-restart required notification is dismissed. |
Disable Auto Restart Notification | Disable auto-restart notifications for update installations |
Set Cart Restart | Skip all restart checks to ensure the reboot will happen at Scheduled Install Time for devices in Cart. |
Managing OS Updates at Group or Device Level
Based on your OS update policy there might be some updates that you can manage at a device level. Only the items that were not selected under the Require Update Approval setting in the Administration & Network settings section can be controlled at a device level. Scalefusion can query for only these items and the list of updates gets updated at a device level.
Here we see how we can check and initiate updates at a Group and device level.
Please note that only the updates that Require Admin approval as per OS update policy will be shown here.
Viewing & Initiating update at Device Group Level
Navigate to the Device Group section and click on the group where you want to check for updates.
Navigate to Devices tab, click on Actions drop-down and click on View Updates in front of Windows 10 & above,
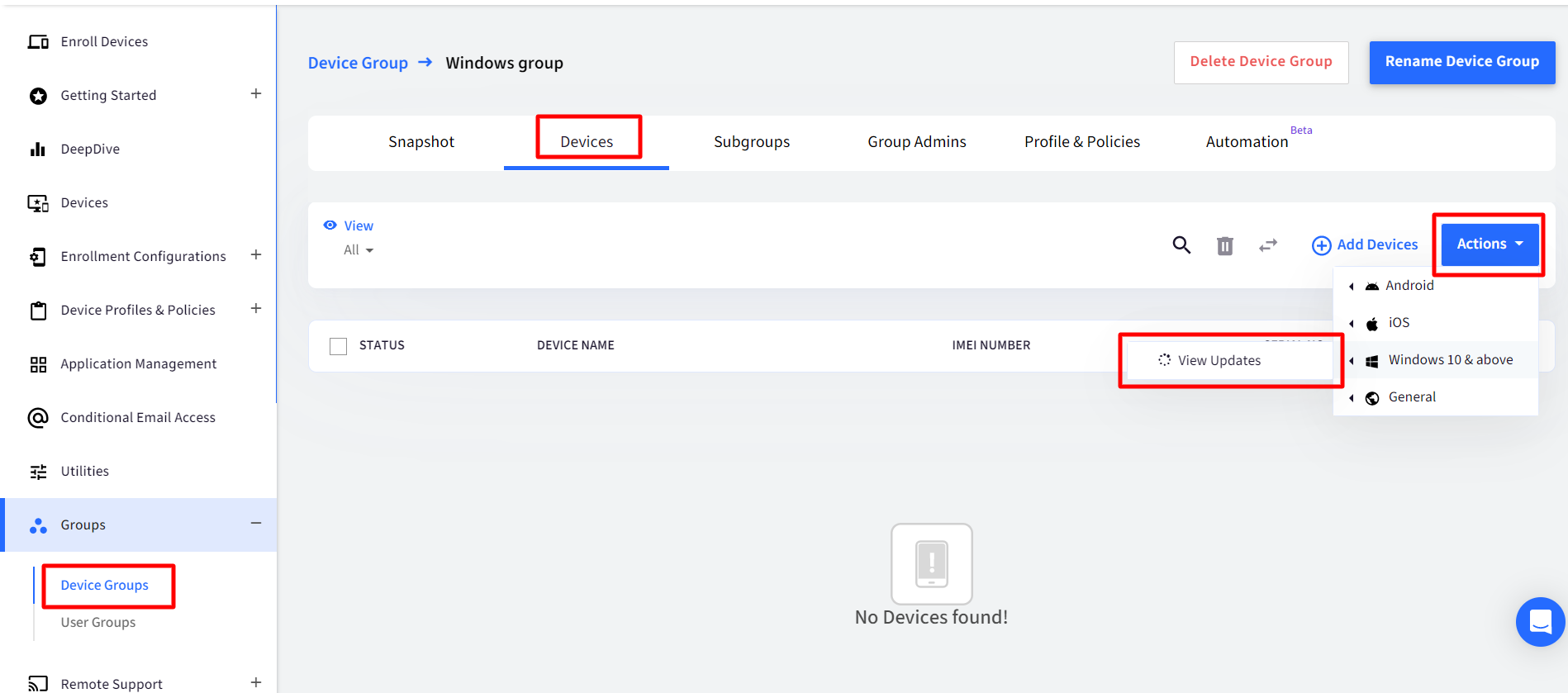
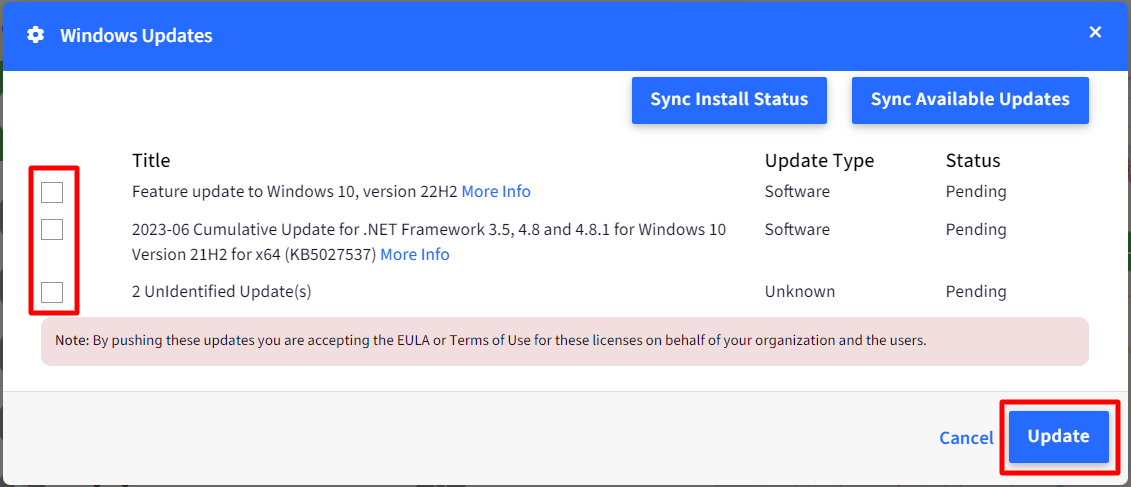
If any of the devices have updates available then you would see the screen below,
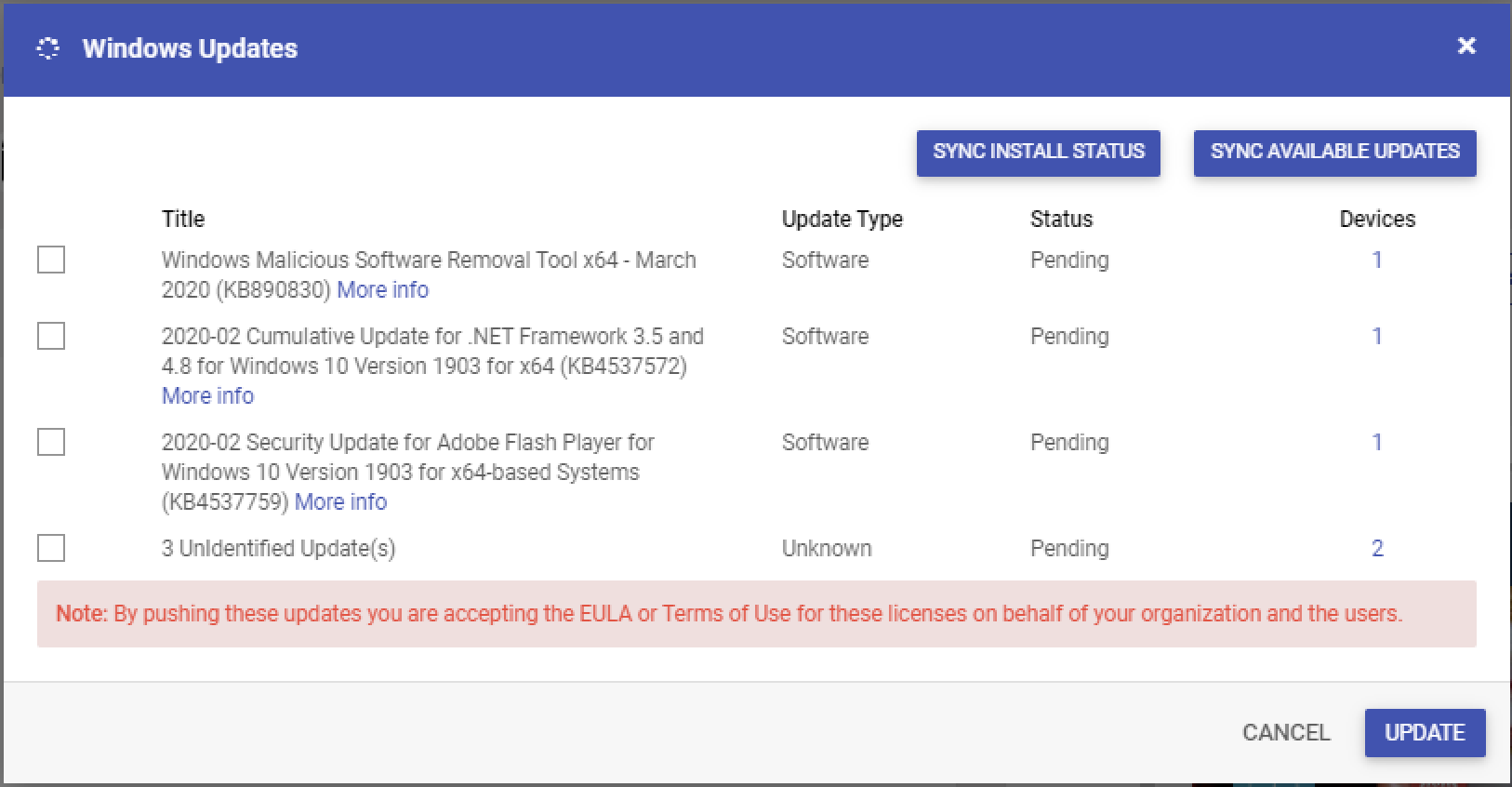
Title: The name of the update as returned by the OS. If no name is returned then it is displayed as an Unidentified Update
Update Type: The type of the update
Status: The current status of the update which is either, Pending, Approved or Installed
Devices: The number of devices in this group where this is available. Clicking on the count of devices shows you the devices where it is available.
Additional Options
Sync Install Status: Sends a query to all devices to retrieve the install status. Please close and reopen the dialog for the latest status to be displayed.
Sync Available Updates: Sends a query to all devices to retrieve the available updates. Please close and reopen the dialog for the latest results to be displayed.
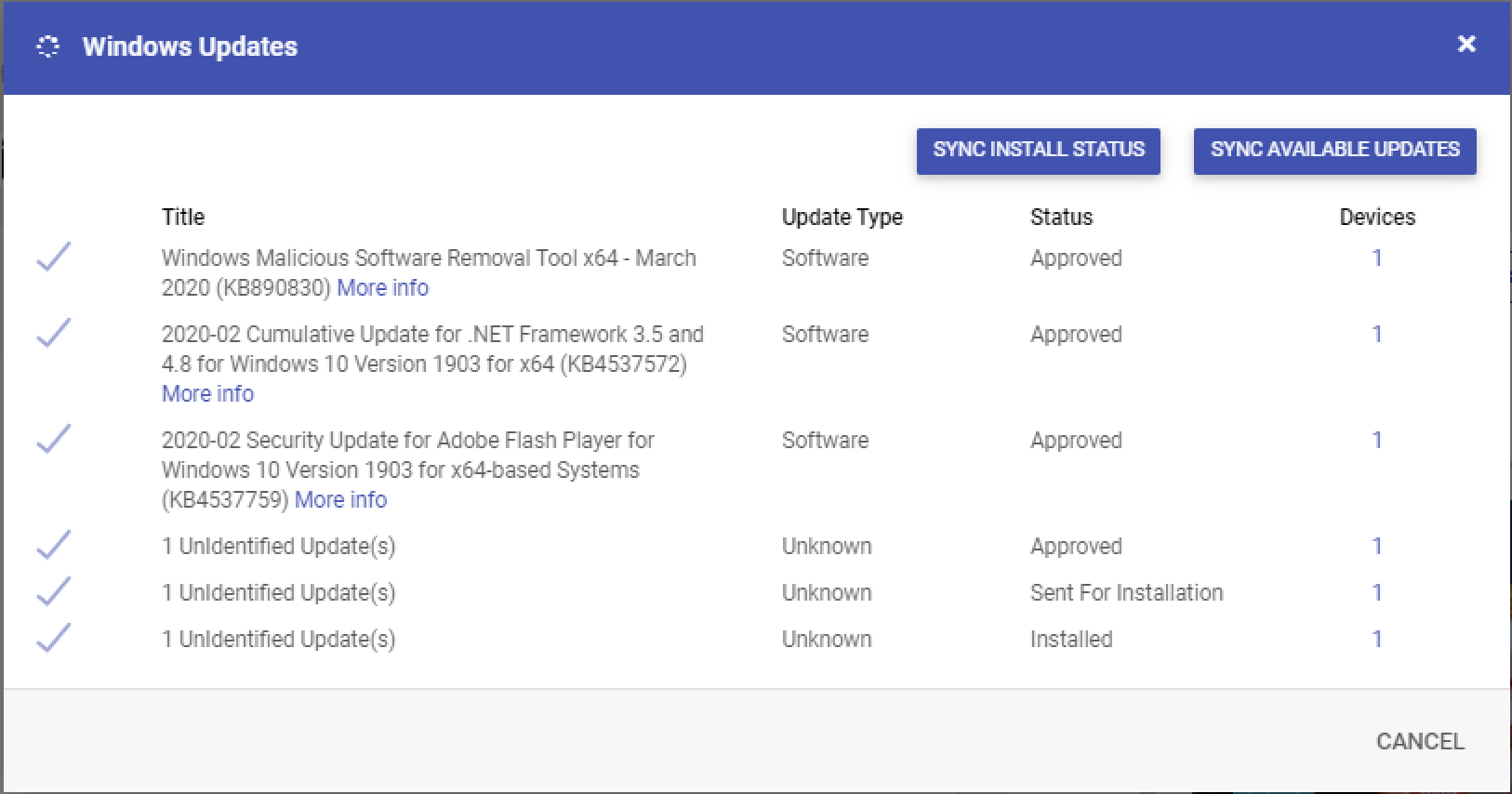
Select the updates that you want to rollout and click on UPDATEto start the updates on the device. Once you have pushed the updates the status will change to Approved.
By clicking on UPDATE you are accepting the EULA agreement. Due to some technical issues with the MDM protocol the content of the EULA
Viewing & Initiating update at Device Level
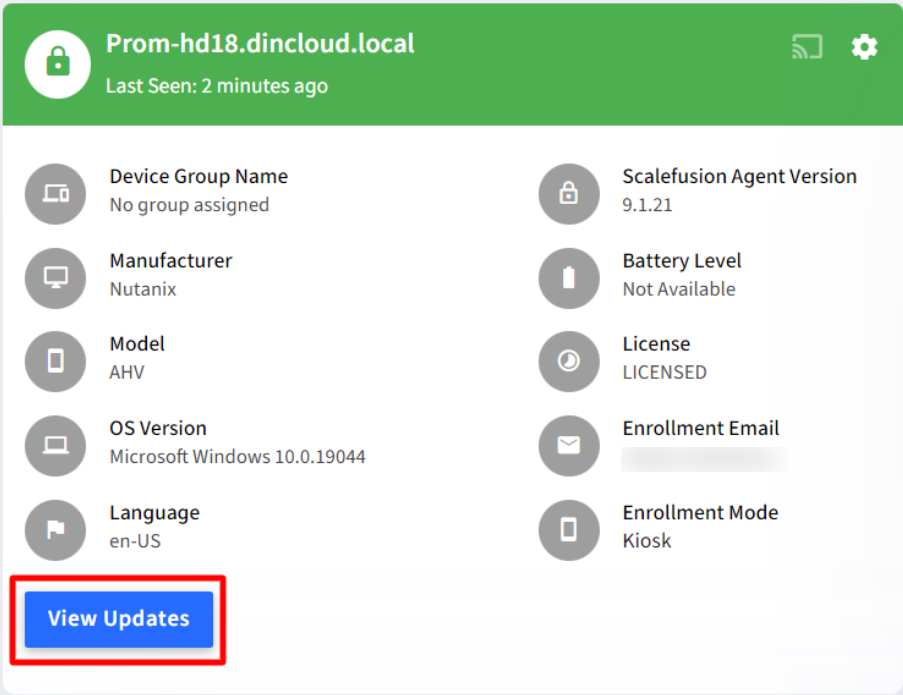
Navigate to the Devices section and click on the Windows 10 devices for which you want to view the available updates.
Once in the Device details view, click on the View Updates button to view the updates.
Select the updates that you want to install on this particular device and click on Update
By clicking on UPDATE you are accepting the EULA agreement. Due to some technical issues with the MDM protocol the content of the EULA
















