- 21 Feb 2024
- 3 読む分
- 印刷する
- PDF
Silently Enable BitLocker on Windows devices.
- 更新日 21 Feb 2024
- 3 読む分
- 印刷する
- PDF
The following PowerShell script helps IT Admins to silently encrypt their managed Windows 10 and above devices with BitLocker.
Create a file on your desktop, for example, silently_enable_bitlocker.ps1 and open it in a text editor like notepad++
# set parameters for bitlocker $bitlockerPassword = "Passwordtounlocksystem"; $bitlockerMountDrive = "driveletter:"; # registry hive for bitlocker $RegistryPath = 'HKLM:\SOFTWARE\Policies\Microsoft\FVE' # set array of hashtable of key value pair $eveDataCollection = @( @{ Name = "EnableBDEWithNoTPM"; Value = '1';} @{ Name = "UseAdvancedStartup"; Value = '1';} @{ Name = "UseTPM"; Value = '2';} @{ Name = "UseTPMKey"; Value = '2';} @{ Name = "UseTPMKeyPIN"; Value = '2';} @{ Name = "UseTPMPIN"; Value = '2';} ) # Remove the key if it does exist If (Test-Path $RegistryPath) { Remove-Item -Path $RegistryPath -Force | Out-Null } # Create the key if it does not exist New-Item -Path $RegistryPath -Force | Out-Null # Now set the value in registry foreach ($eveDataItem in $eveDataCollection) { New-ItemProperty -Path $RegistryPath -Name $eveDataItem.Name -Value $eveDataItem.Value -PropertyType DWORD -Force } # force to update group policy Invoke-Command -ScriptBlock {GPUpdate /Force} # Convert the password to SecureString $SecureString = ConvertTo-SecureString "$bitlockerPassword" -AsPlainText -Force; # invoke command to add recovery password and enable the bitlocker Add-BitLockerKeyProtector -MountPoint $bitlockerMountDrive -RecoveryPasswordProtector | Out-Null Enable-BitLocker -MountPoint $bitlockerMountDrive -EncryptionMethod Aes256 -Password $SecureString -PasswordProtector; # reboot the system Invoke-Command -ScriptBlock {shutdown -r -t 2}Copy the contents as shown above to the file or click here to download the file.
In the script, you will need to provide the bitlockerPassword and bitlockerMountDrive that you want to encrypt.
- For example,
$bitlockerPassword = "Pass@659"; $bitlockerMountDrive = "C:";The bitlockerPassword should be alpha numeric and must be minimum 8 characters.
Please mention the Drive that you would like to encrypt, for example, C: or D: or any other removeable media drives.
Please note you can only encrypt a single Drive at a time using this script.
Once the first Drive is encrypted, you can then change the bitlockerMountDrive to a different Drive in the script to encrypt it and push to the device. Different scripts are required to push to encrypt 2 or more drives.
The script will force update some GPO setting and Registry required to enforce BitLocker silently.
BitLocker encryption will start silently once GPO setting update is successful.
Machine will restart in 3 secs or as per the time specified in the script. This time can be defined in the script. For example,
Invoke-Command -ScriptBlock {shutdown -r -t 3}After restart, machine will ask to enter BitLocker Password. End user will need to enter BitLocker Password as provided by the Admin.
After entering the BitLocker password, device will boot up and it will continue encrypting the whole disk that is mentioned in the script.
Current encryption process encrypts whole disk and not the Used Space.
Once Encryption is completed, Recovery key will be updated on the Scalefusion dashboard.
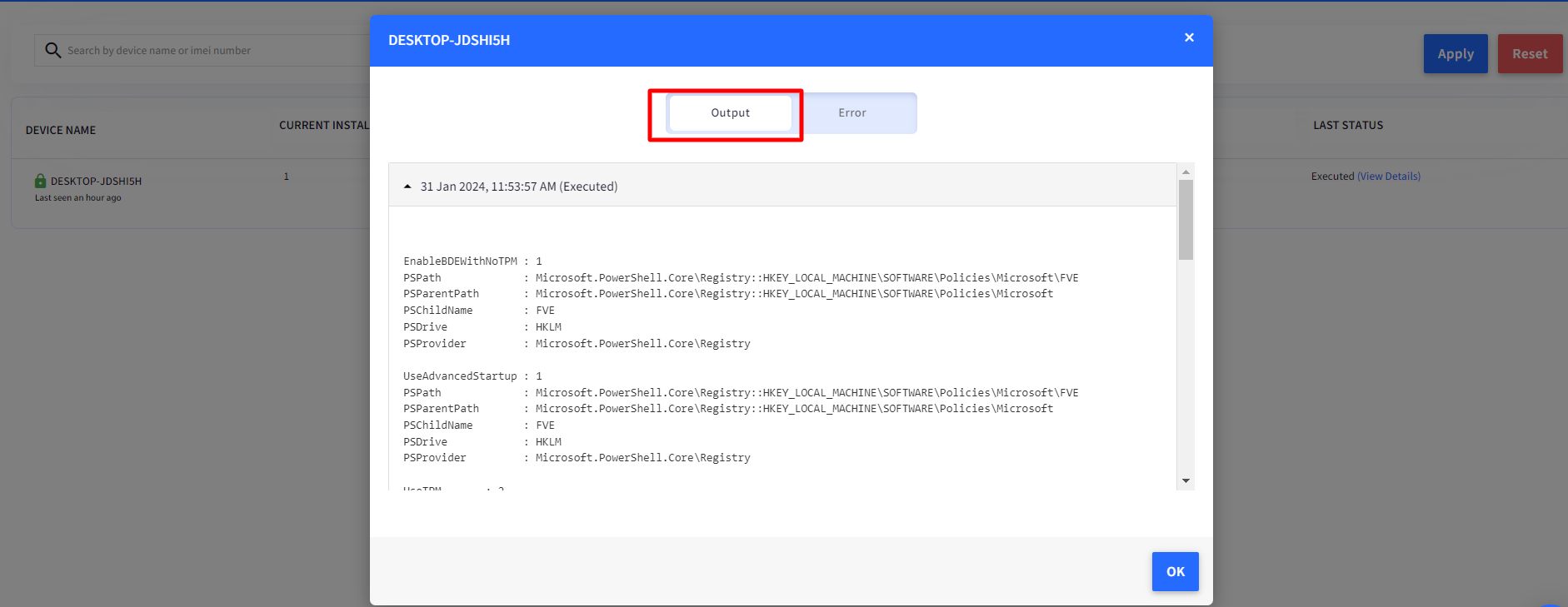
Once the script is successfully executed, you will be able to see the Output of the changes made to the GPO setting and Registry in the View Status report on the Scalefusion dashboard.
Click on the PowerShell script and click on the View Status.
Executed means that the script has successfully run on the device. Click on View Output to see the details.
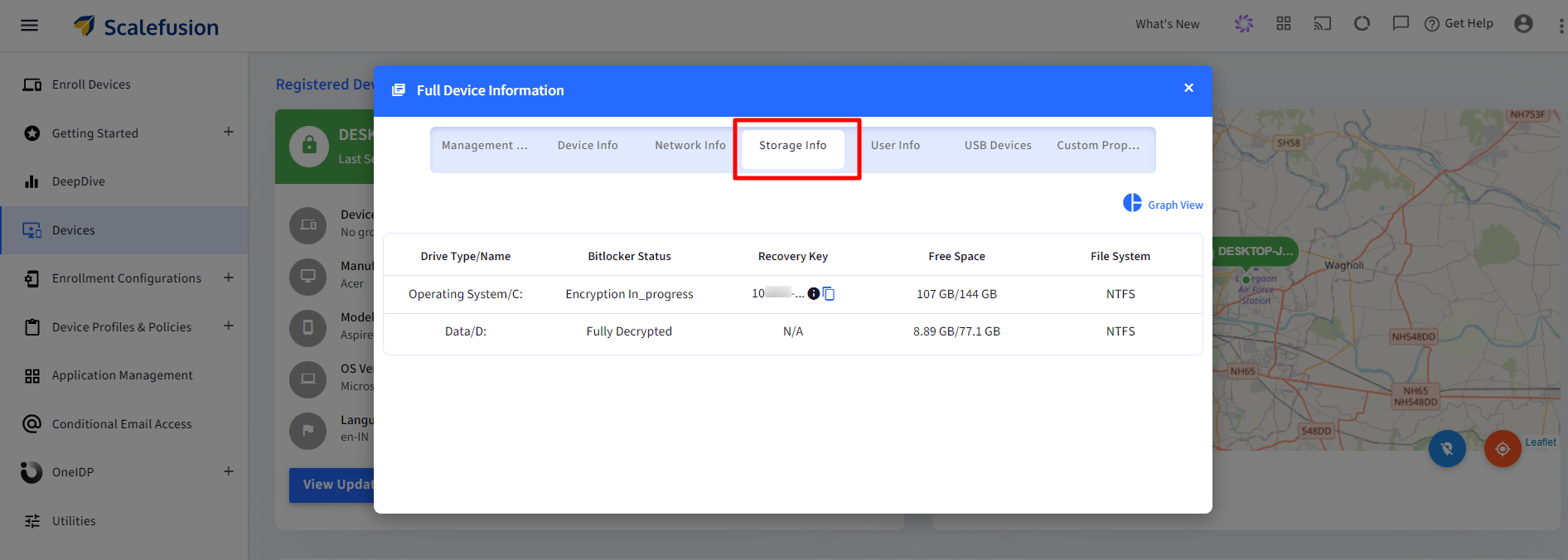
You will be able to see the Recovery Key in the Full Device Information > Storage Info.
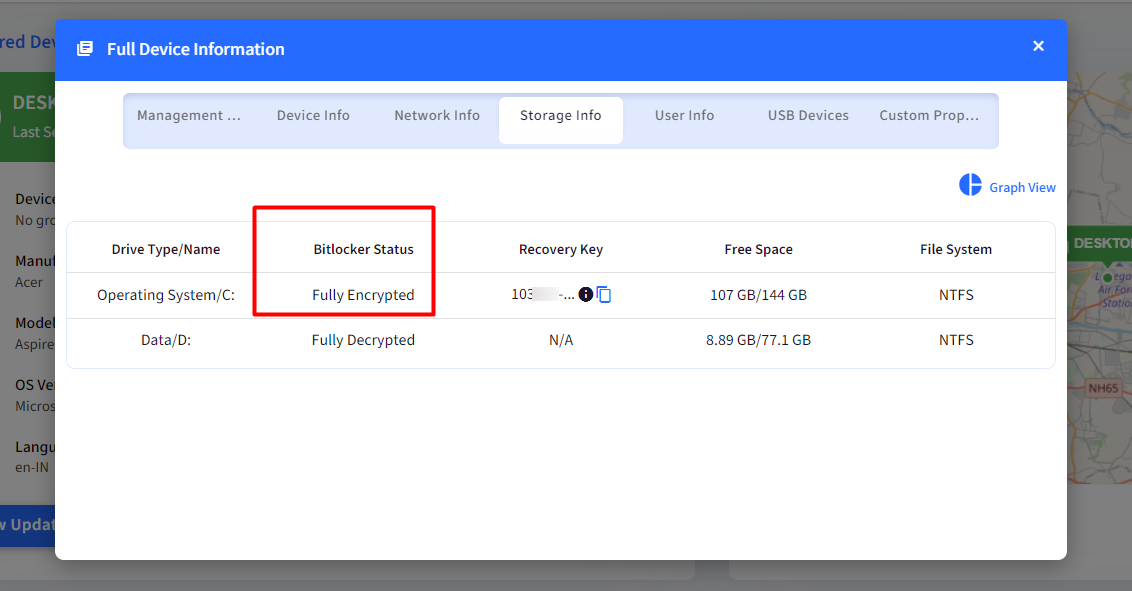
Your Please note that if you are using the script to silently encrypt the device then do not enable the BitLocker settings in the Device Profile.
Note:To use this PowerShell scripts, the latest Scalefusion MDM Agent Application must be installed on the device(s). Please follow our guide to publish and install the Scalefusion MDM Agent Application.
Notes:
The scripts and their contents are sourced from various albeit authenticated Microsoft sources and forums.
Please validate the scripts on a test machine before deploying them on all your managed devices.
Scalefusion has tested these scripts, however, Scalefusion will not be responsible for any loss of data or system malfunction that may arise due to the incorrect usage of these scripts.



