- 10 Feb 2025
- 2 読む分
- 印刷する
- PDF
Configuring PingOne as Identity Provider
- 更新日 10 Feb 2025
- 2 読む分
- 印刷する
- PDF
PingOne is a cloud-based identity and access management (IAM) platform developed by Ping Identity. It provides solutions for managing user identities and securing access to applications and services.
This article provides a step-by-step guide to configuring PingOne as the Identity Provider for all the services you use.
Prerequisites
Please make sure you have created the SSO configuration for the service for which you want to set PingOne as the Identity Provider.
Also, make sure that the user(s) is present in the PingOne portal and the respective service’s portal that you are trying to access.
The same user(s) must be present in Scalefusion, and the SSO configuration of the respective service is applied to it.
Step 1: Configuring PingOne as an Identity Provider on Scalefusion dashboard
Navigate to OneIdP > Identity Providers.
Click on the New Provider button.
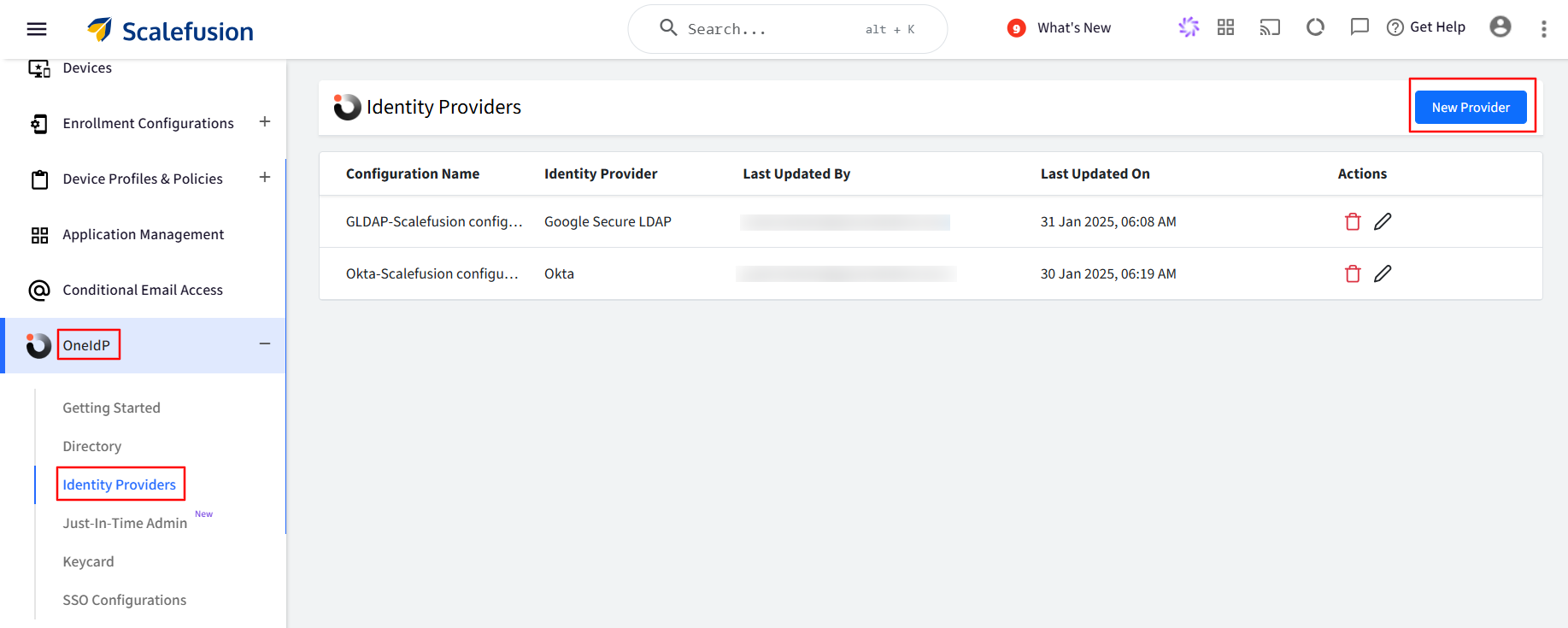
Select PingIdentity and click on Next.

Provide a name to this configuration for easy identification.
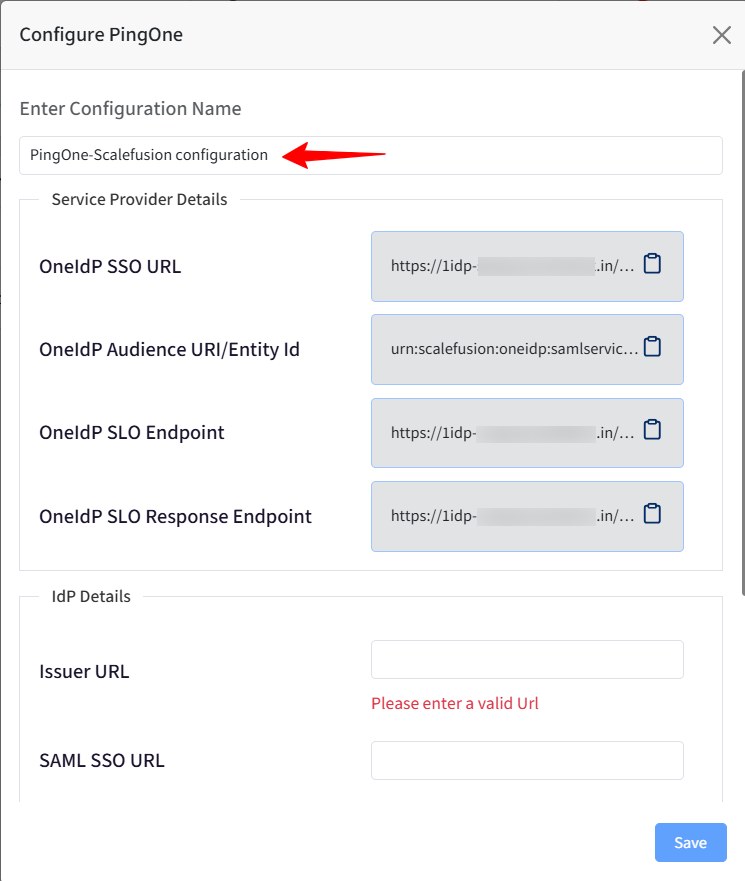
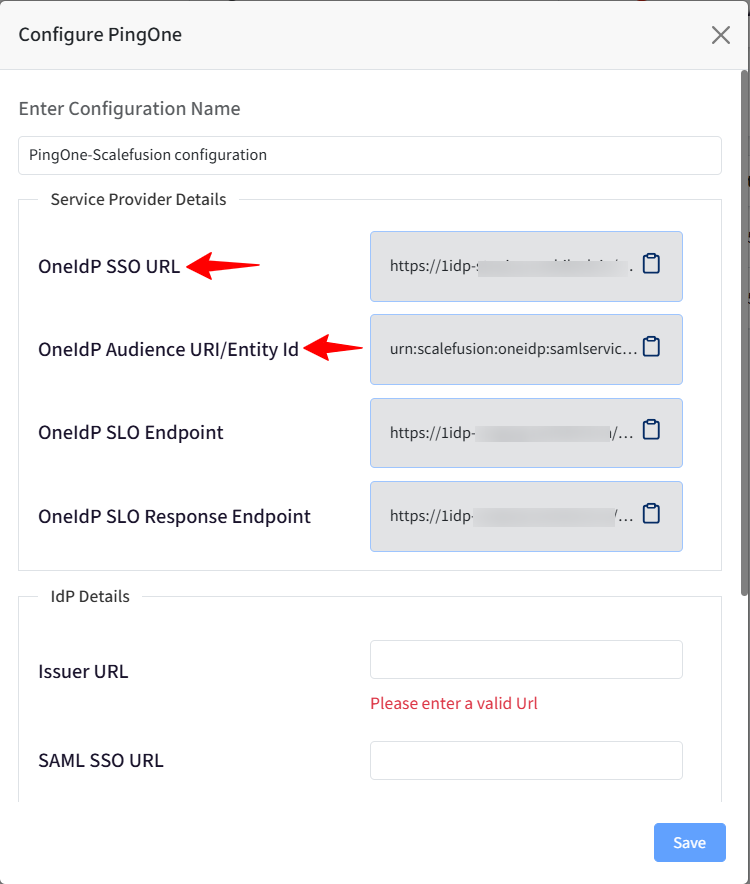
Service Provider Details will be added in the PingOne Admin Console as shown in Step 2.
IdP Details will be generated on the PingOne Admin Console as shown in Step 2.
Step 2: PingOne SAML Setup in PingOne Admin Console
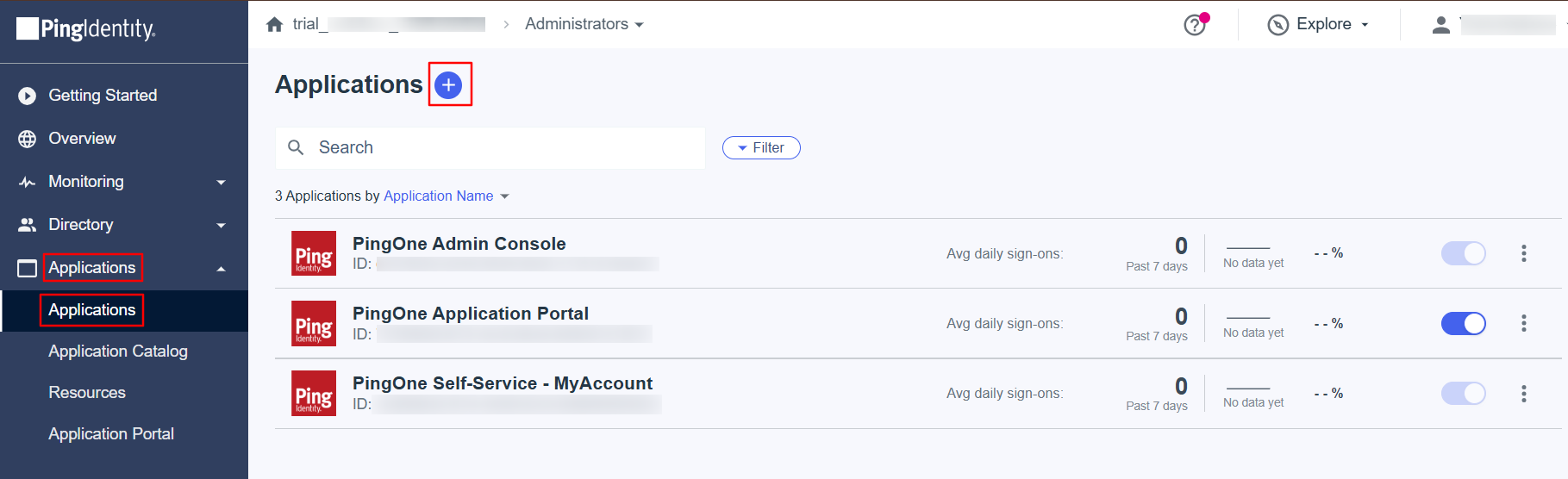
Log into your PingOne Admin console.
Navigate to Applications > Applications.
In this page click on the plus button next to Applications on the top left-hand side.
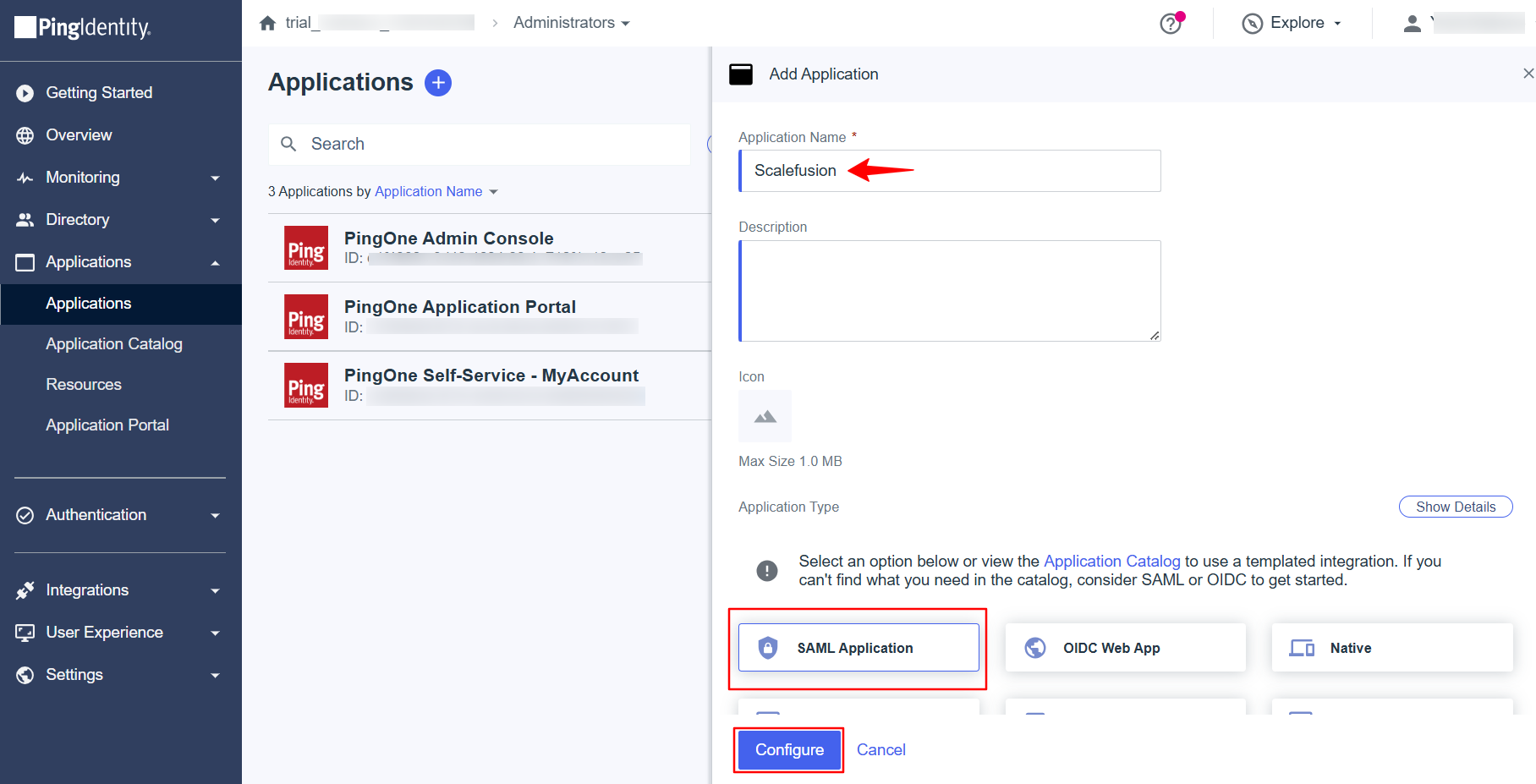
Provide a name to this configuration for easy identification.
Select SAML Application under Application Type and click on the Configure button.
On the next page, select Manually Enter and add the ACS URLs and Entity ID from the Scalefusion dashboard here.
ACS URL will be the OneIdP SSO URL.
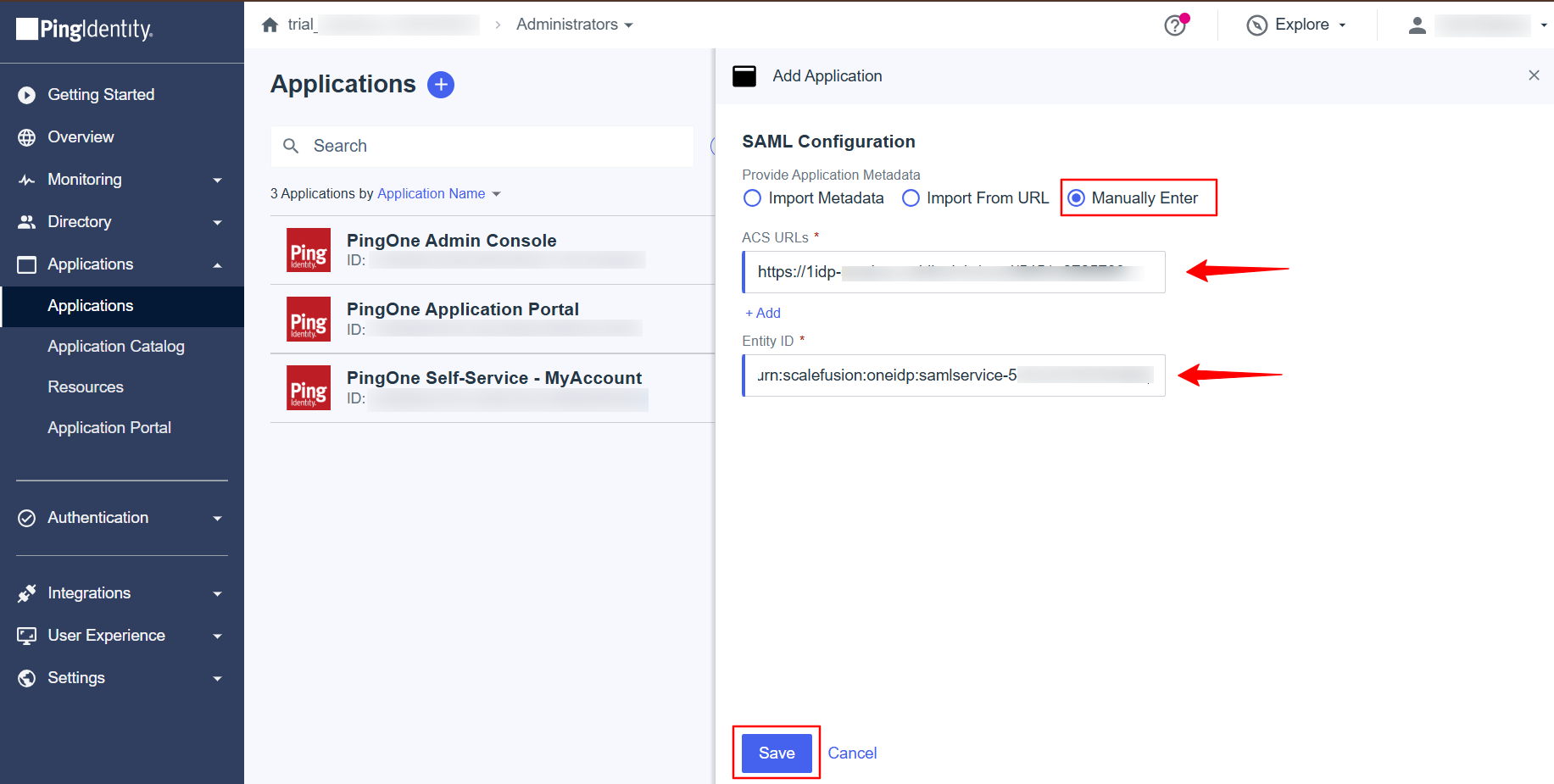
Click on Save.
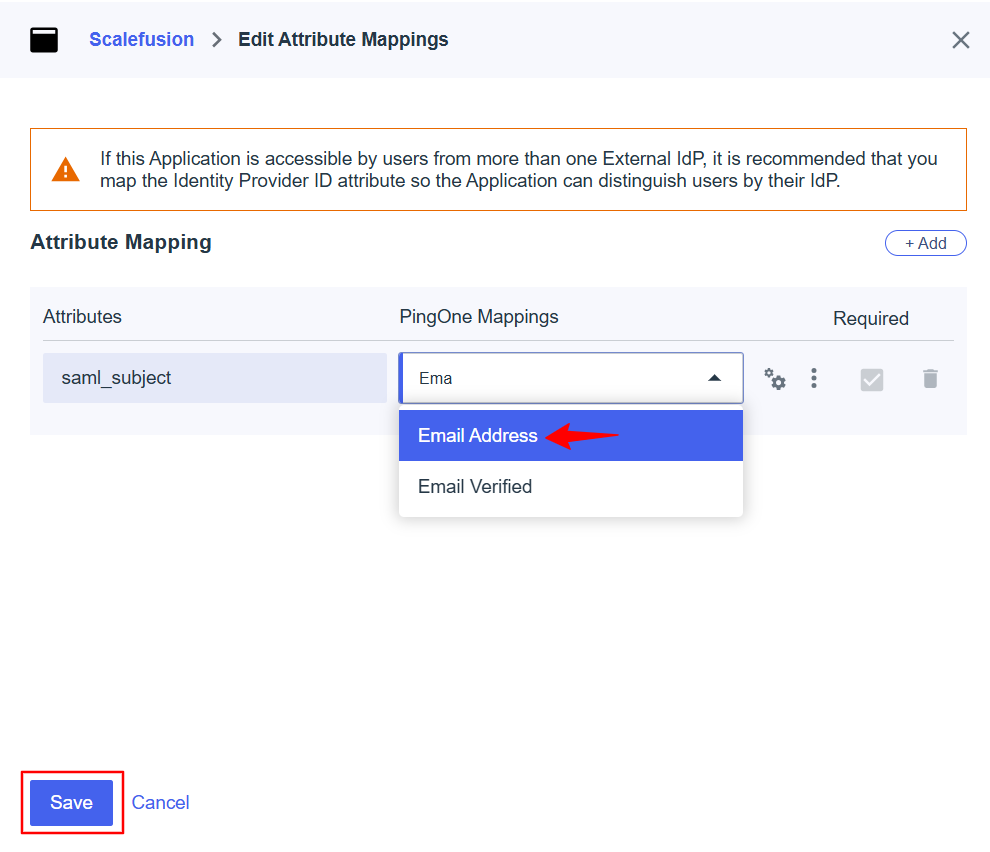
On the next page, go to the Attribute Mappings tab and click the Edit icon.

Change the PingOne Mappings to Email Address and click on Save.
Next, go to the Configuration tab and click on the Edit icon.
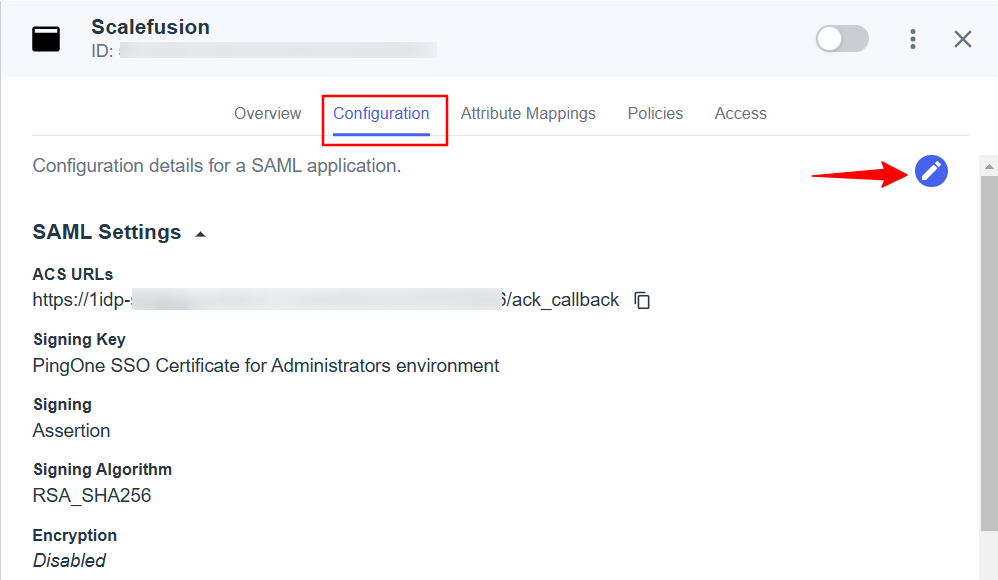
Here change the Sign… to Sign Assertion & Response.
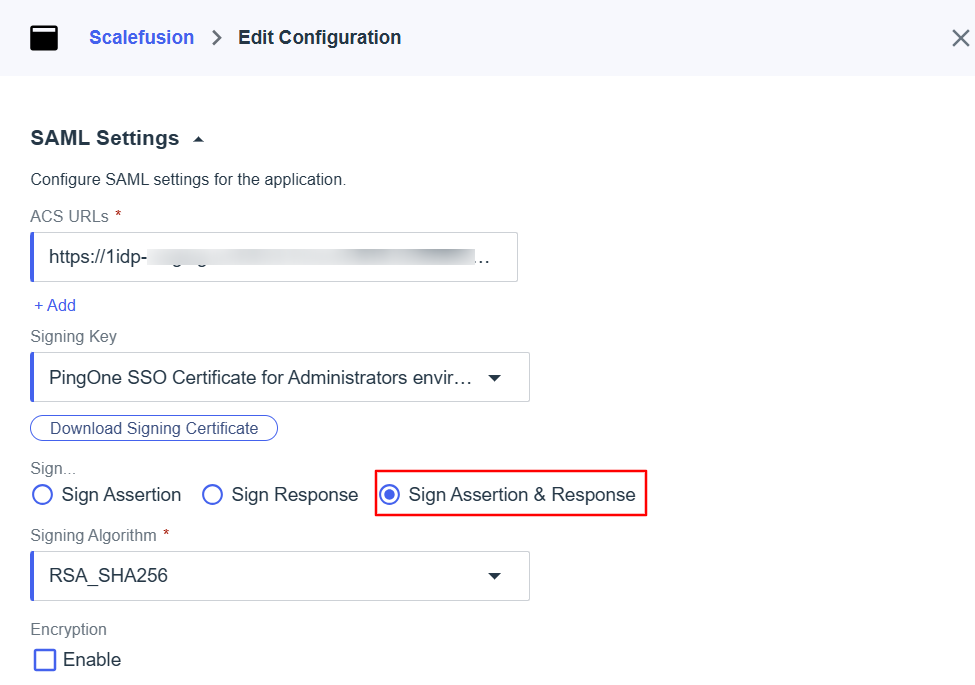
Scroll down a little and add the SLO Endpoint URL from the Scalefusion dashboard here.
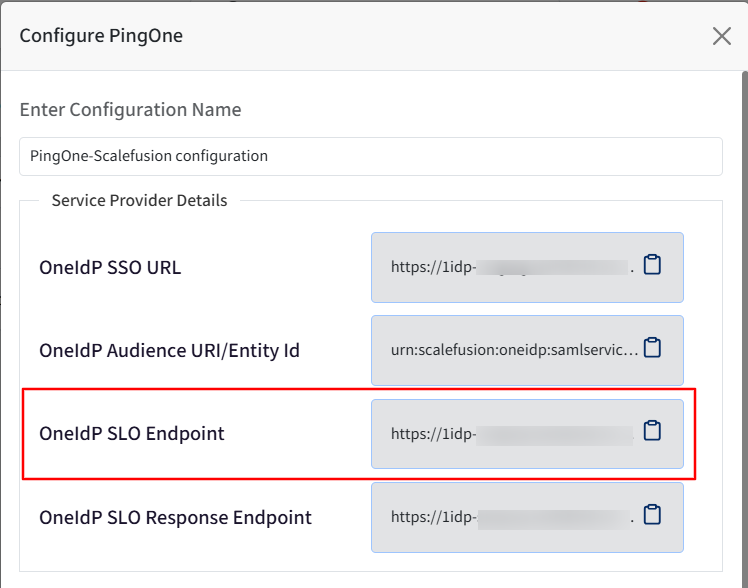
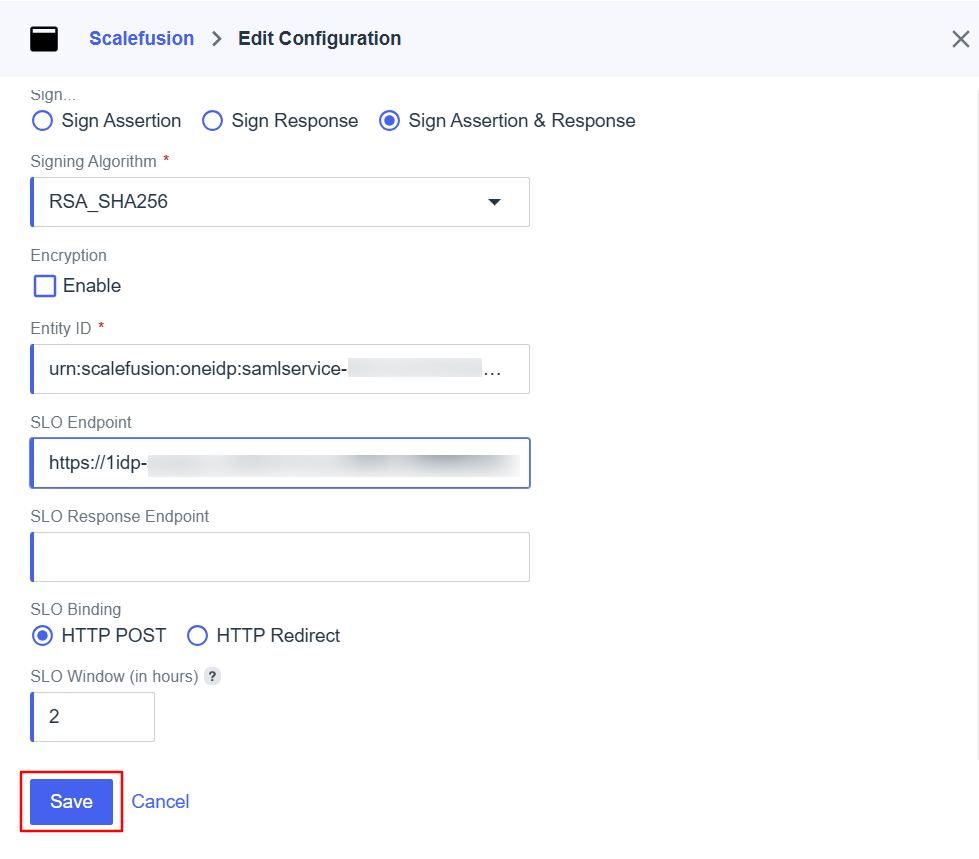
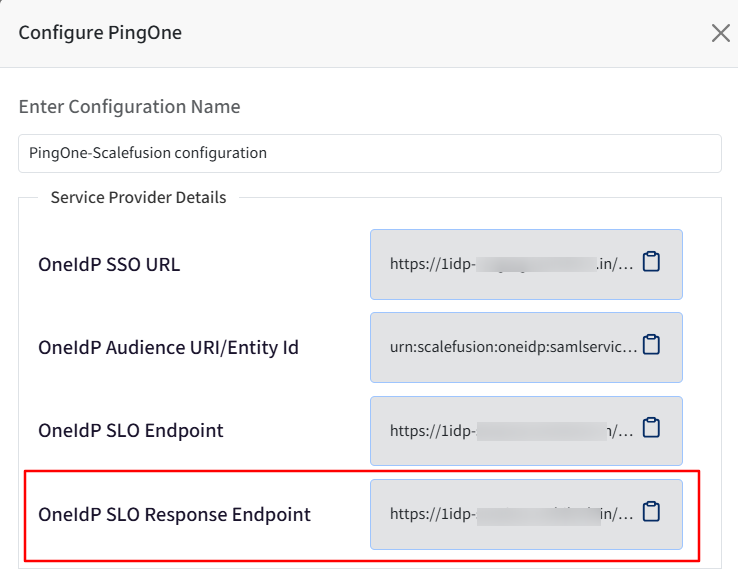
Next, add the OneIdP SLO Response Endpoint URL from the Scalefusion dashboard to the SLO Response Endpoint field.
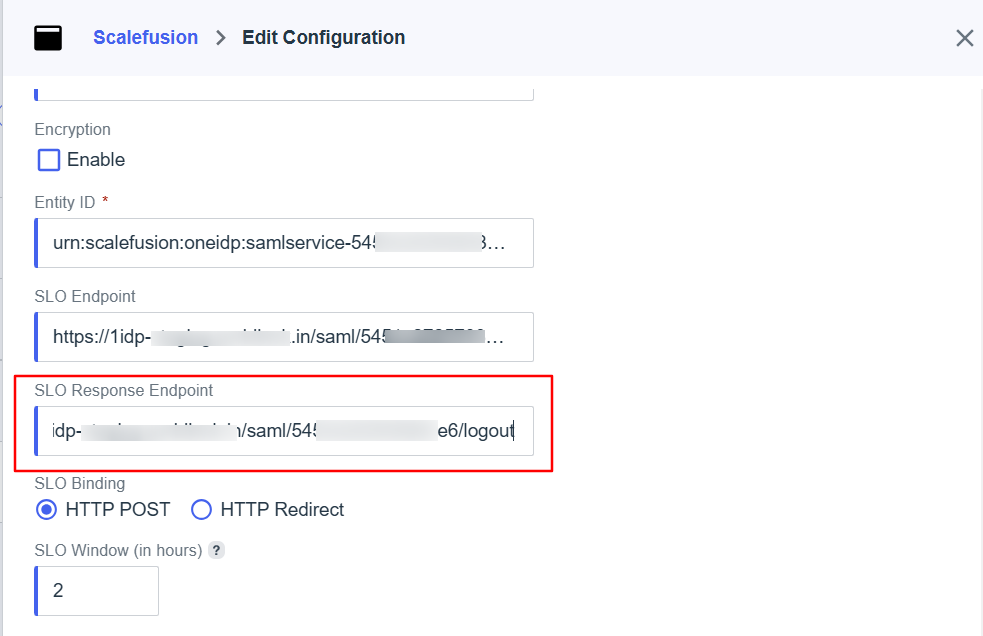
Click on Save.
Next, toggle On the button on the top.
Next, go to the Overview tab and scroll down to Connection Details.
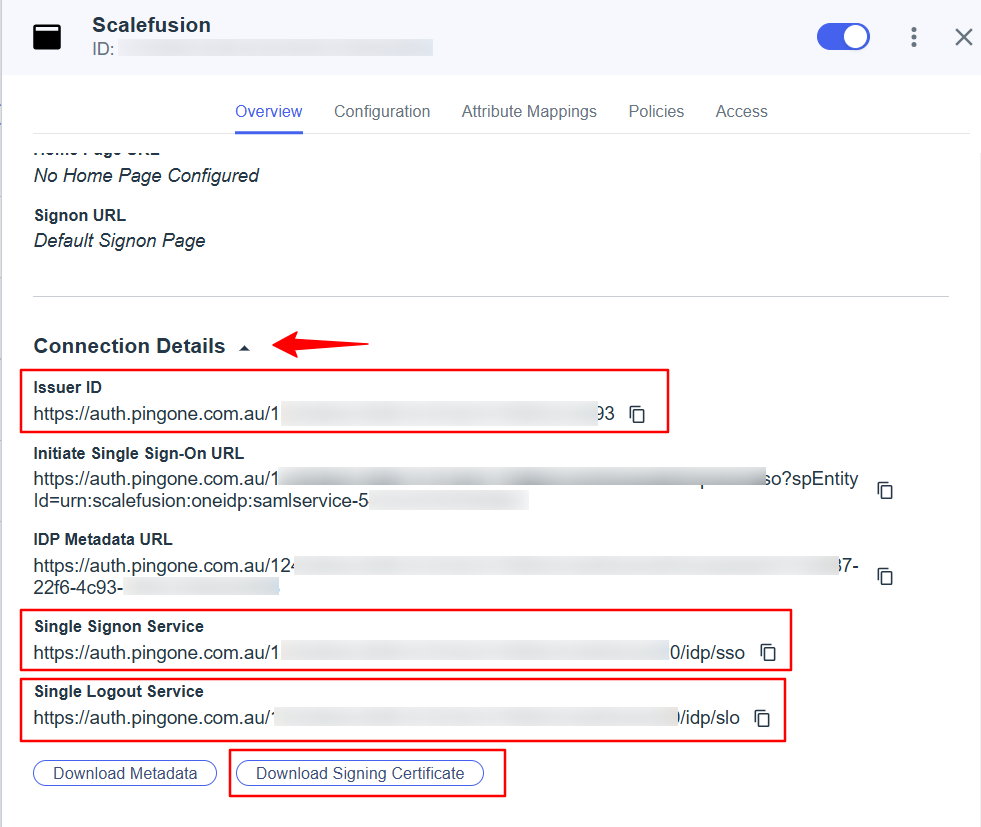
Copy the Issue ID URL, Single Signon Service URL, and Single Signout Service URL and save them, as these will be used on the Scalefusion dashboard.
Download the X509 PEM (.crt) by clicking on the “Signing Certificate” button as this will be uploaded on the Scalefusion dashboard.
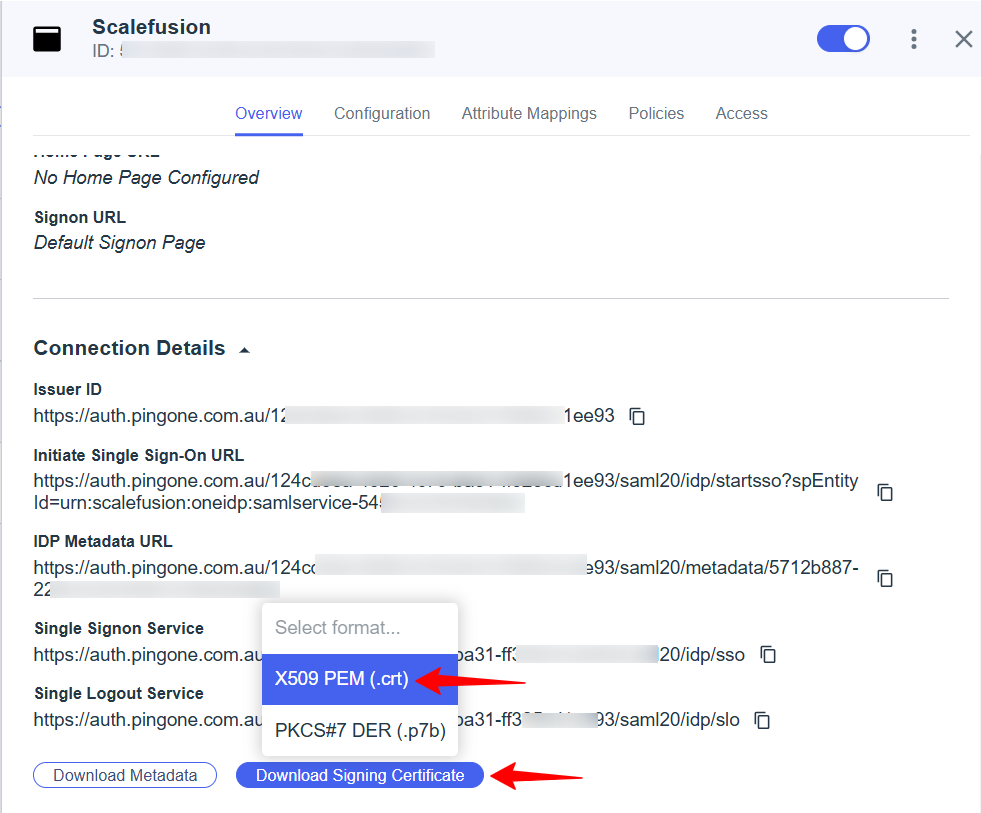
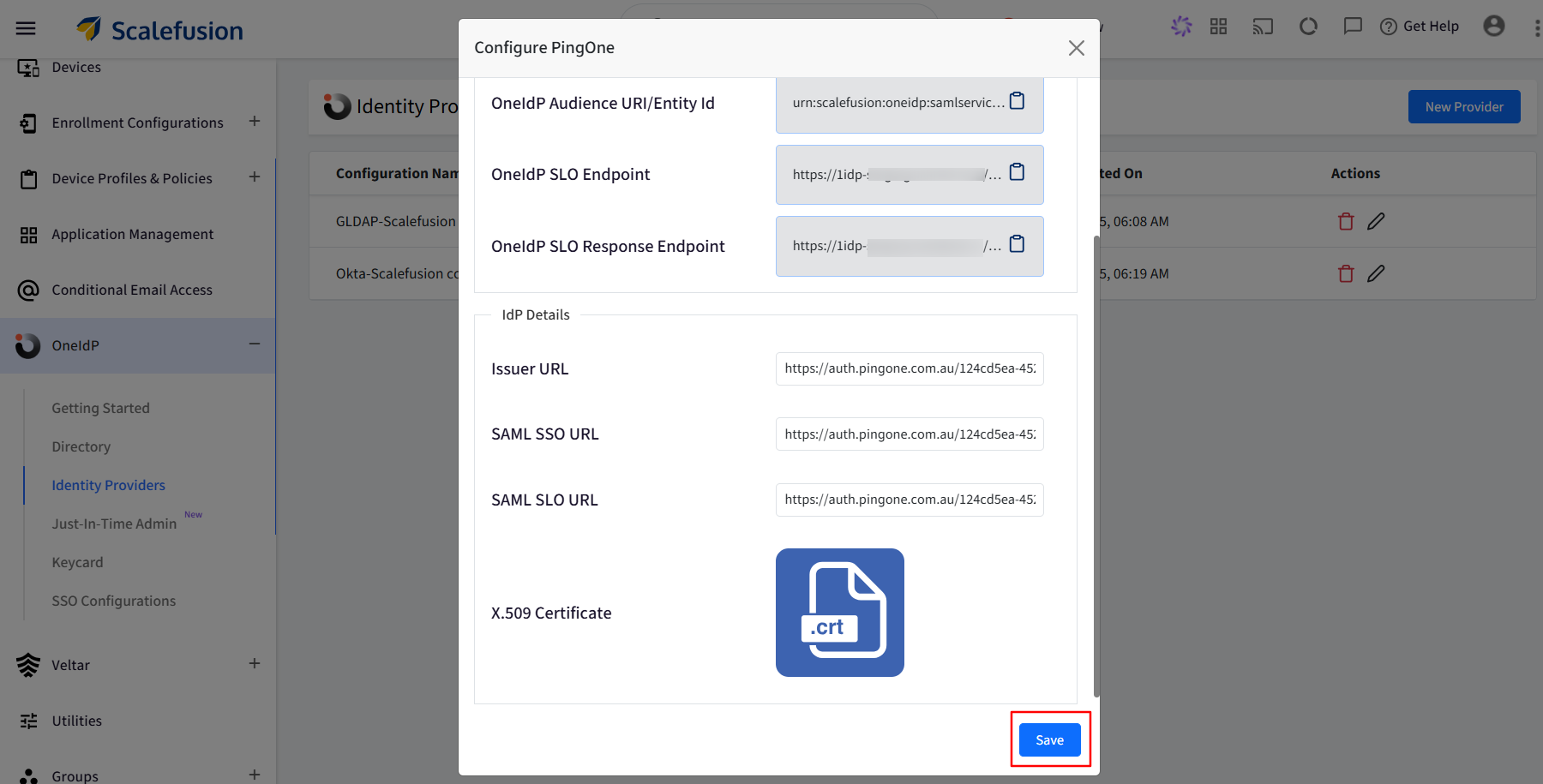
Step 3: Adding PingOne Saml setup details to the Scalefusion dashboard
On the Scalefusion dashboard, enter the saved URLs from Step 2 in the respective fields.
Upload the x509 certificate that you downloaded in Step 2.
Click on Save.
Step 4: Associating PingOne Identity Provider with a Directory
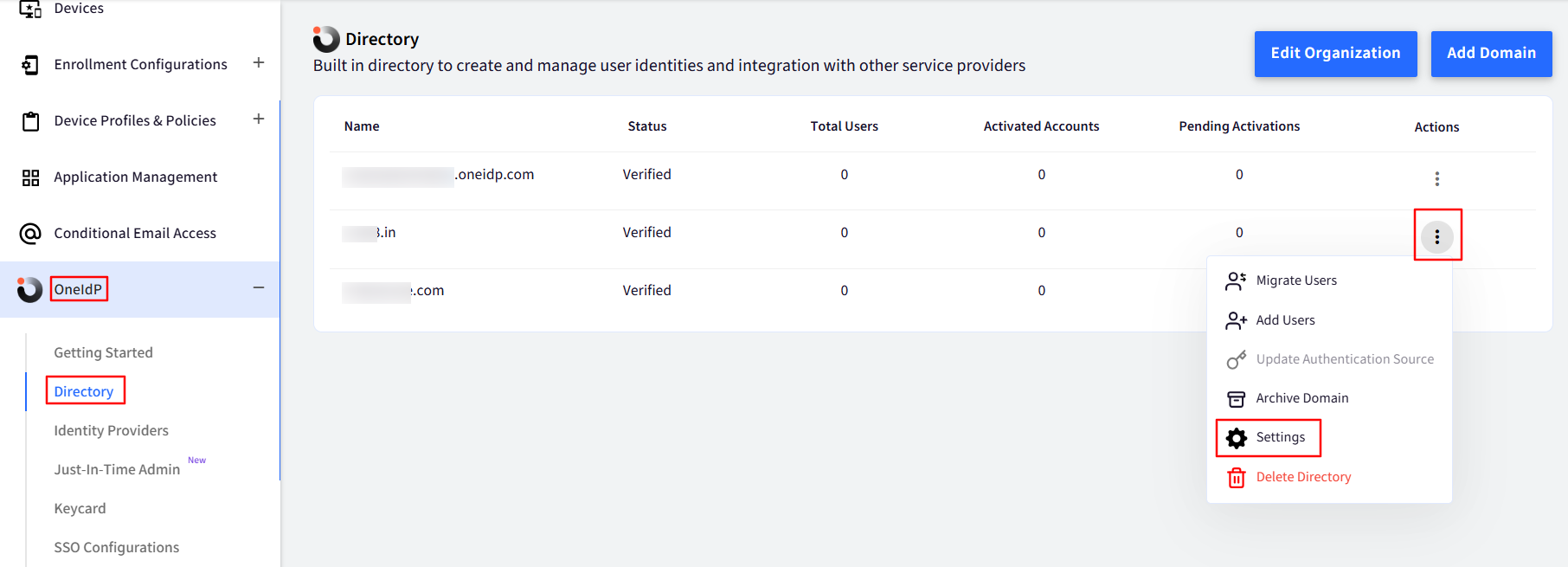
Navigate to OneIdP > Directory.
Click on the 3-dots under Actions for the concerned Domain.
Click on Settings.
Go to the Federated Authentication tab and toggle on the button for PingOne as an Authentication source.
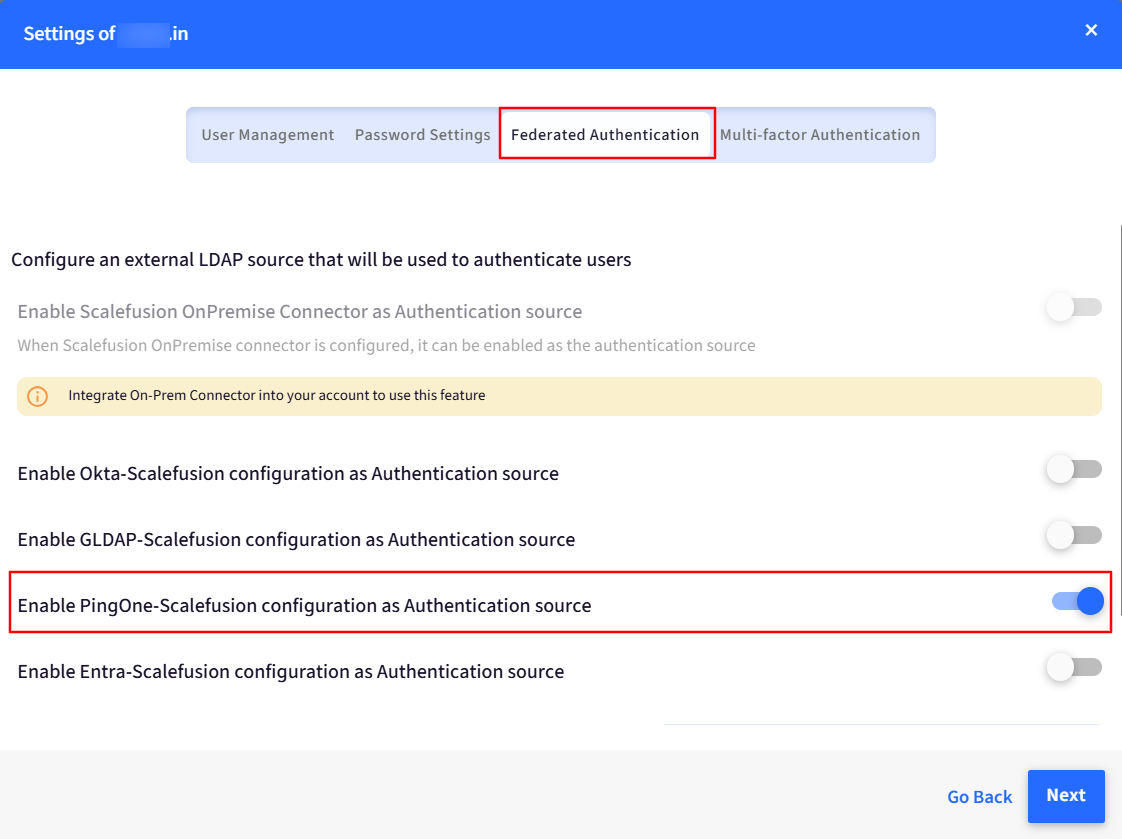
You can also “Set default authentication source”.
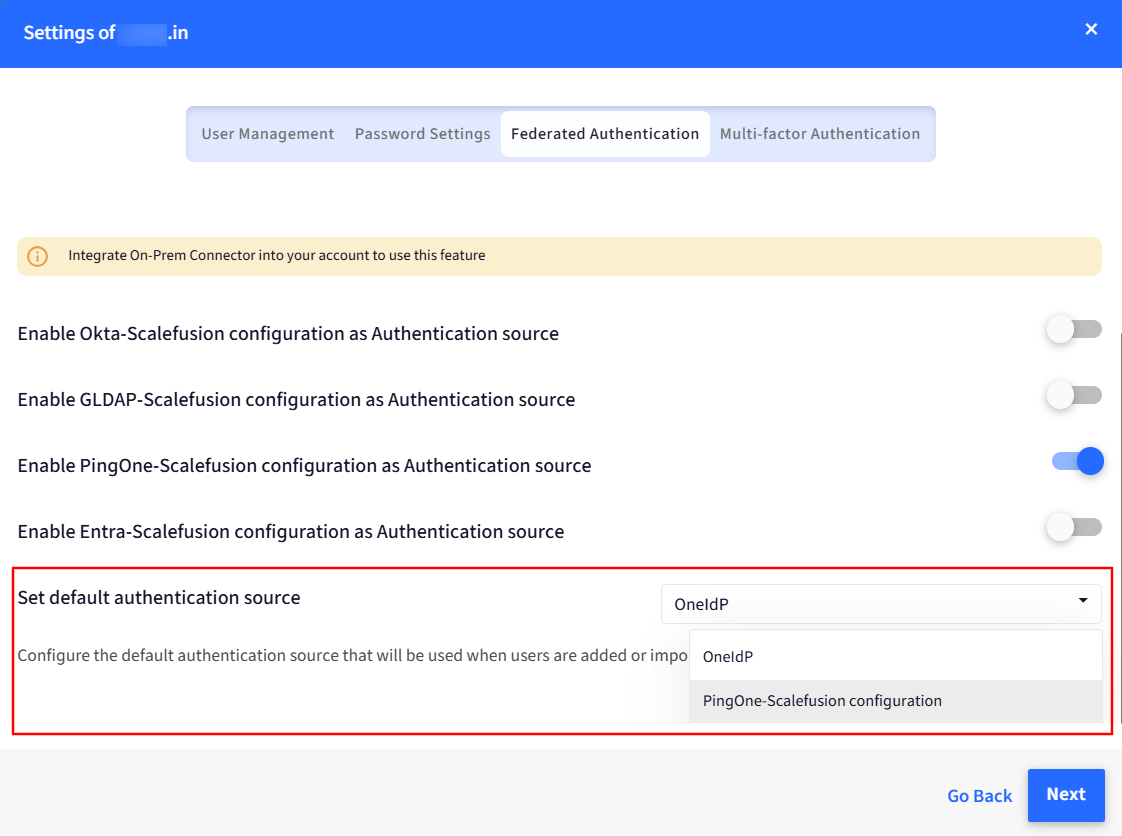
On setting a default authentication source, whenever you add any new user in the Scalefusion dashboard and migrate it to OneIdP, the default Authenticator would be PingOne.
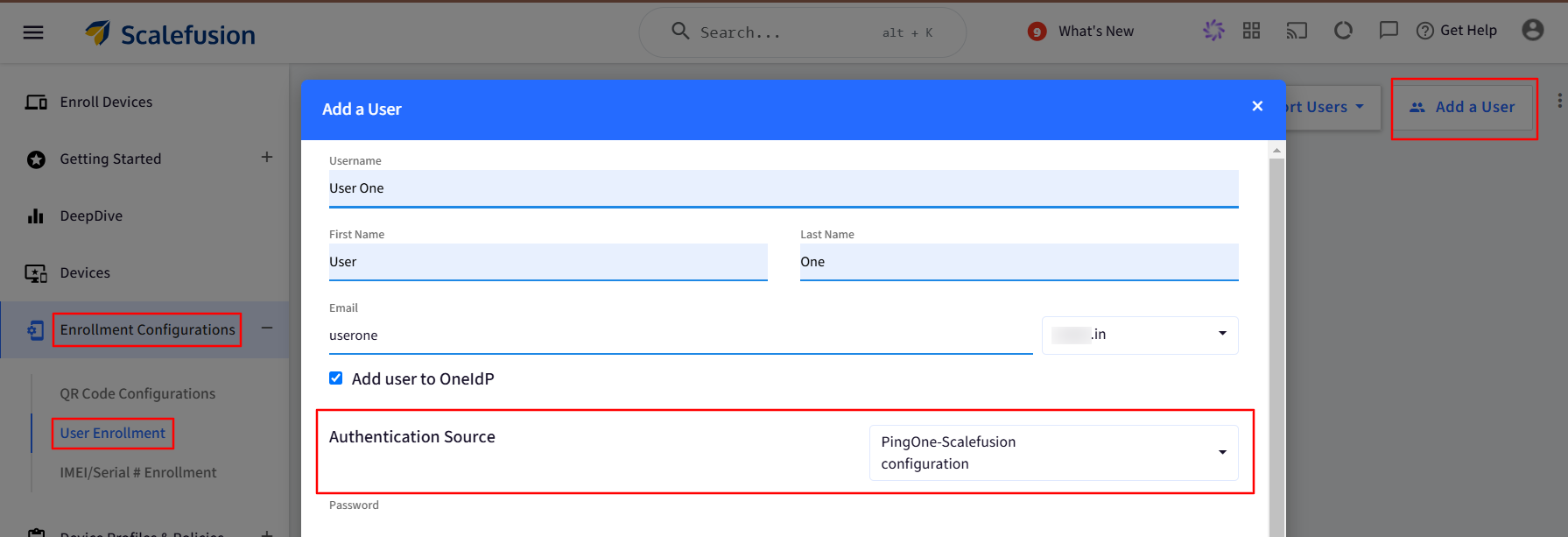
Click on Next and Save.
For existing users that are present in the Scalefusion dashboard, you can change the default authentication source by going to 3-dots under Actions > Update Authentication Source.
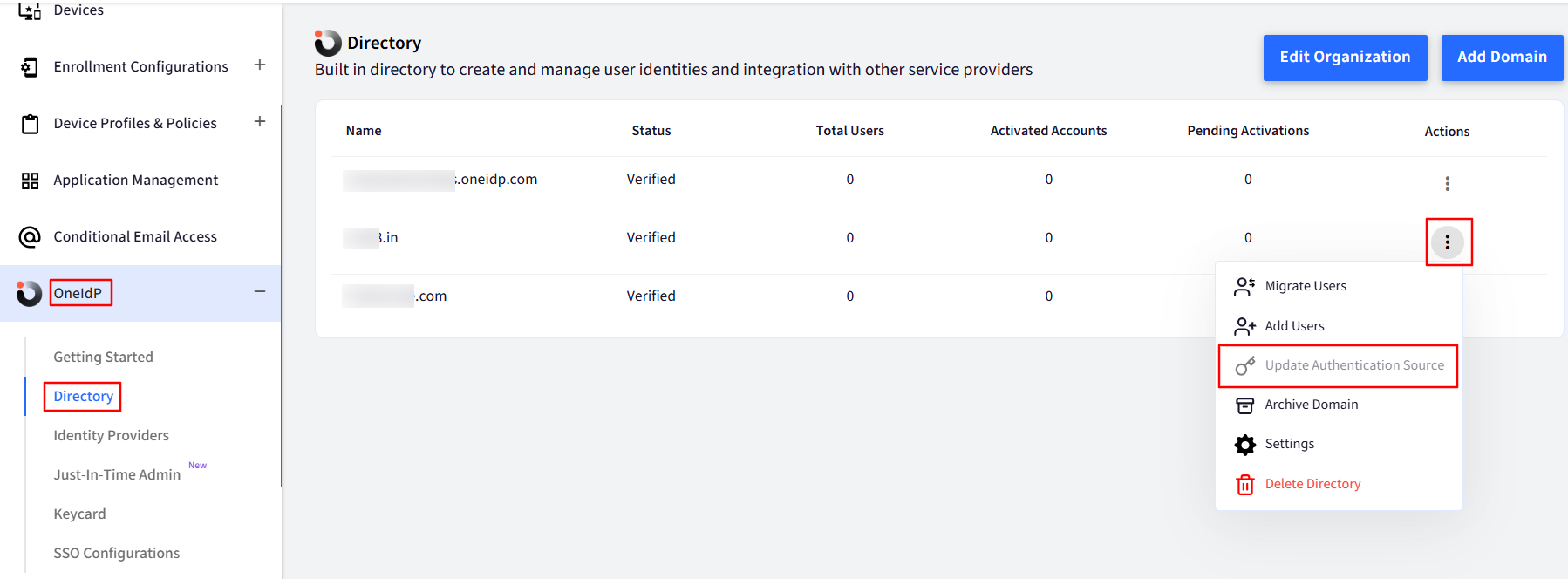
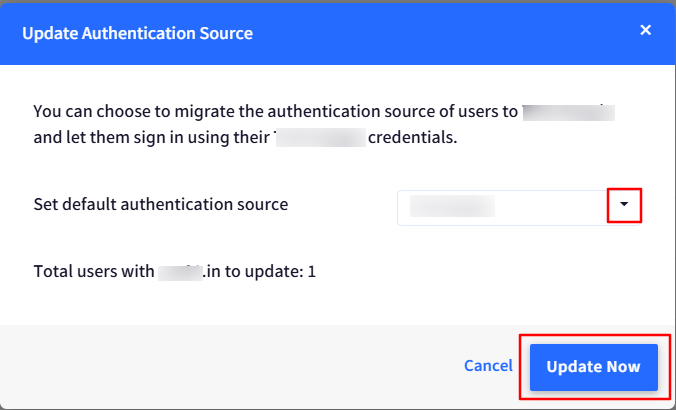
Select PingOne from the drop-down list for “Set Authentication Source” and click on Update Now.
User Login Flow
When the user enters their email on the service login page, they will be redirected to OneIdP. From there, OneIdP will redirect the user to the chosen identity provider (PingOne, in this case) for authentication. Once the identity provider authenticates the user, they will be granted access to the service.



























