- 10 Feb 2025
- 3 読む分
- 印刷する
- PDF
Configuring Google LDAP as Identity Provider
- 更新日 10 Feb 2025
- 3 読む分
- 印刷する
- PDF
Google LDAP (Lightweight Directory Access Protocol) is a service offered by Google that allows organizations to use their Google Workspace (formerly G Suite) directory as an LDAP server. This enables external applications or systems to authenticate and interact with Google Workspace user data, such as email addresses, group memberships, and other directory information, using the standard LDAP protocol.
This article provides a step-by-step guide to configuring Google LDAP as the Identity Provider for all the services you use.
Prerequisites
Google Workspace Business Plus or Enterprise Plus license.
Please make sure you have created the SSO configuration for the service you want to access and set Google LDAP as its Identity Provider.
Also, make sure that the user(s) is present in the Google Workspace portal and the respective service’s portal that you are trying to access.
The same user(s) must be present in Scalefusion and the SSO configuration of the respective service is applied to it.
Step 1: Configuring Google LDAP as an Identity Provider on Scalefusion dashboard
Navigate to OneIdP > Identity Provider.
Click on the New Provider button.
Select G Secure LDAP and click on Next.

Provide a name to this configuration for easy identification.
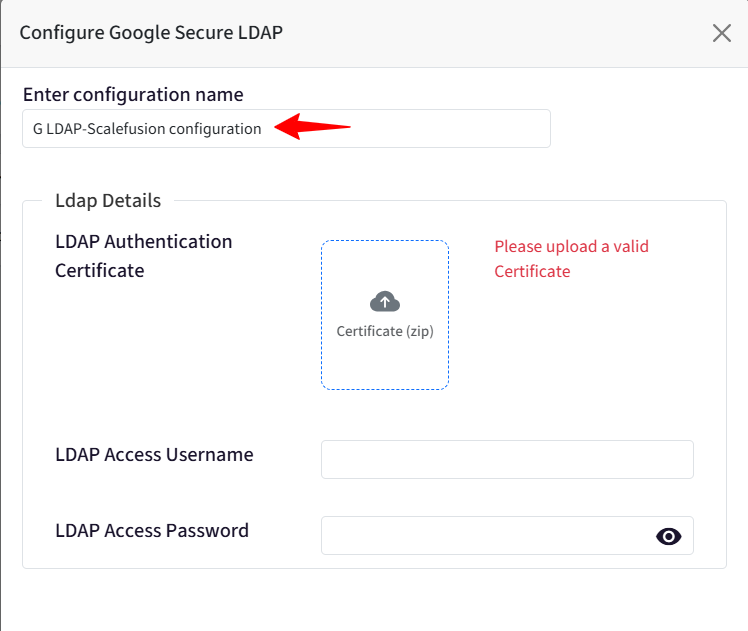
LDAP details will be generated on the Google Workspace Admin Console, as shown in Step 2.
Step 2: Google LDAP Setup in Google Workspace Admin Console
Sign into your Google Workspace Admin Console.
Navigate to Apps > LDAP and click on Add Client.
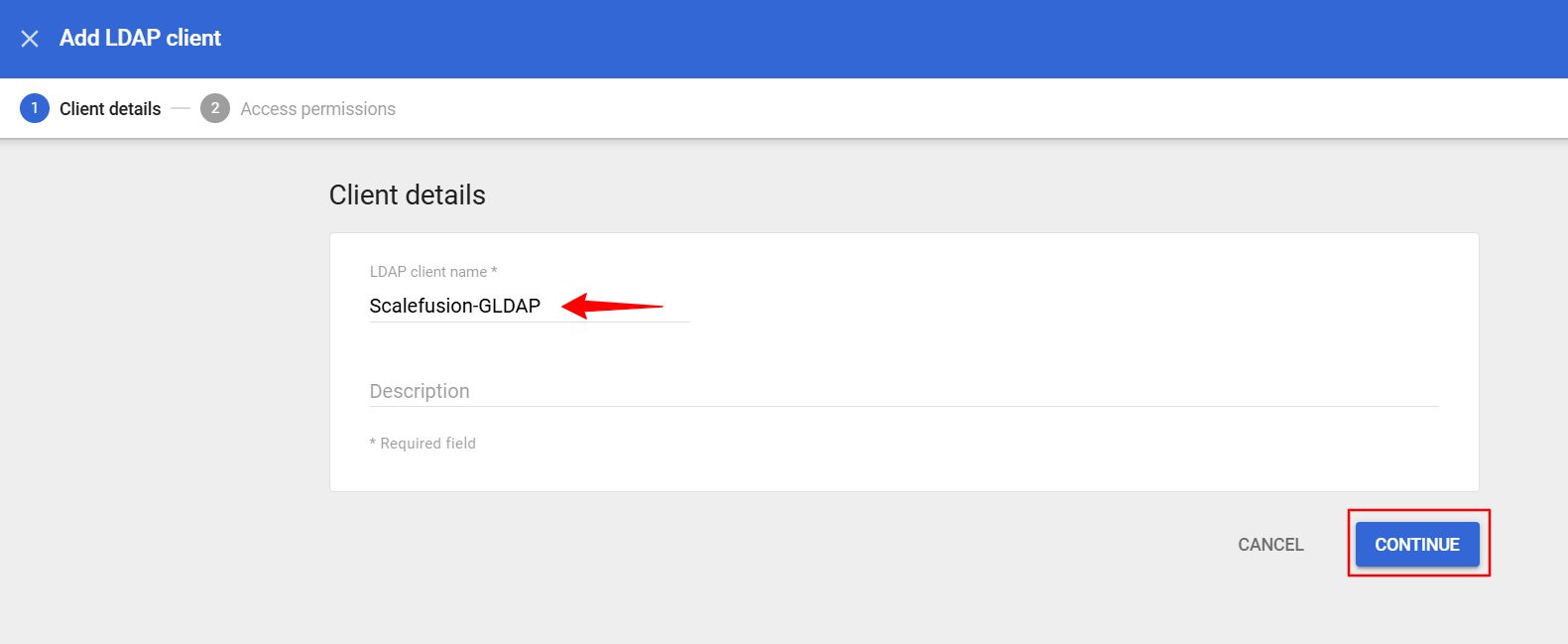
Enter a name to it for easy identification and click on Continue.
In the Access Permission page, please select the options under Verify user credentials and Read user information.
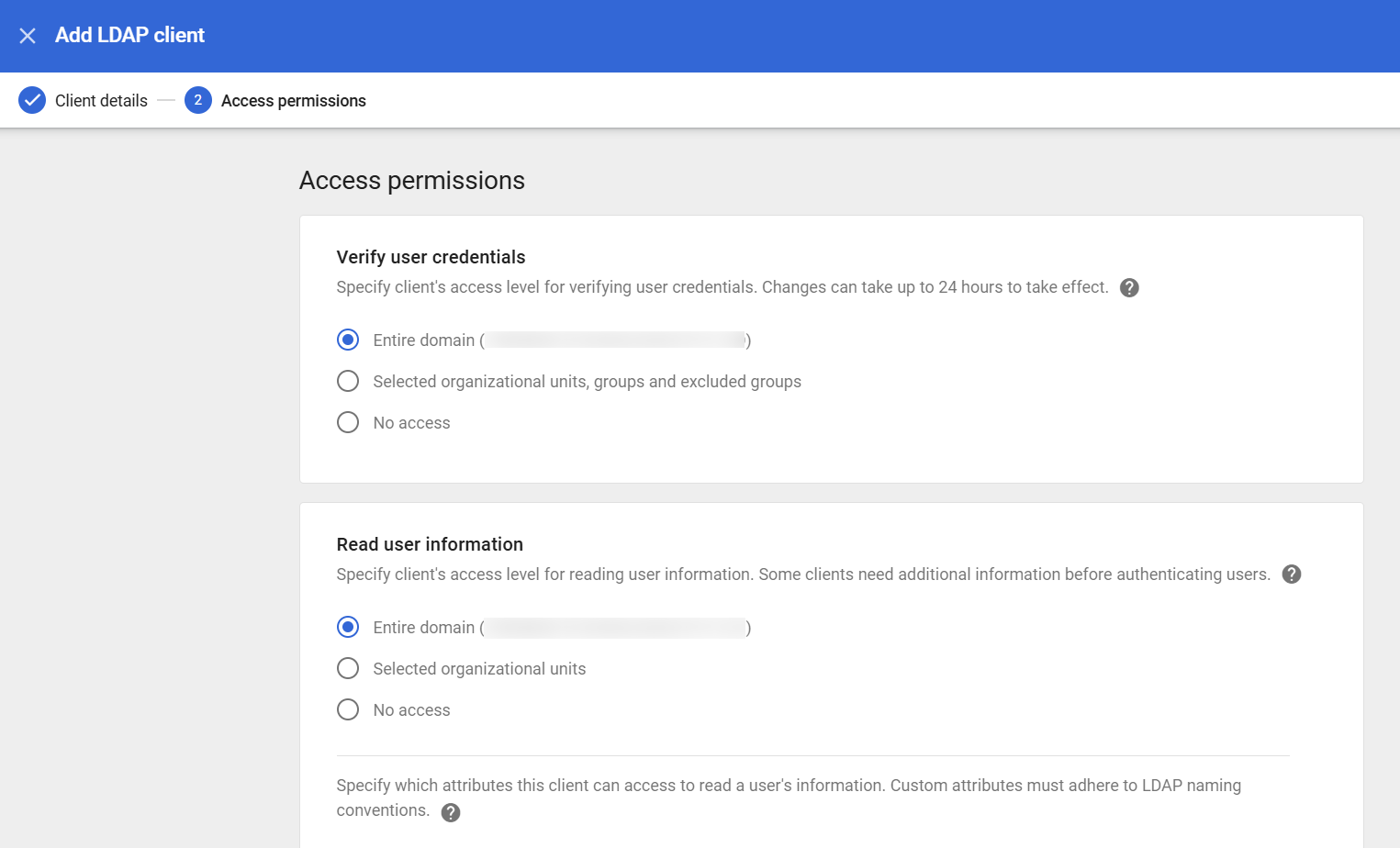
Select the Entire domain if you want the settings to apply to all the users in your organization.
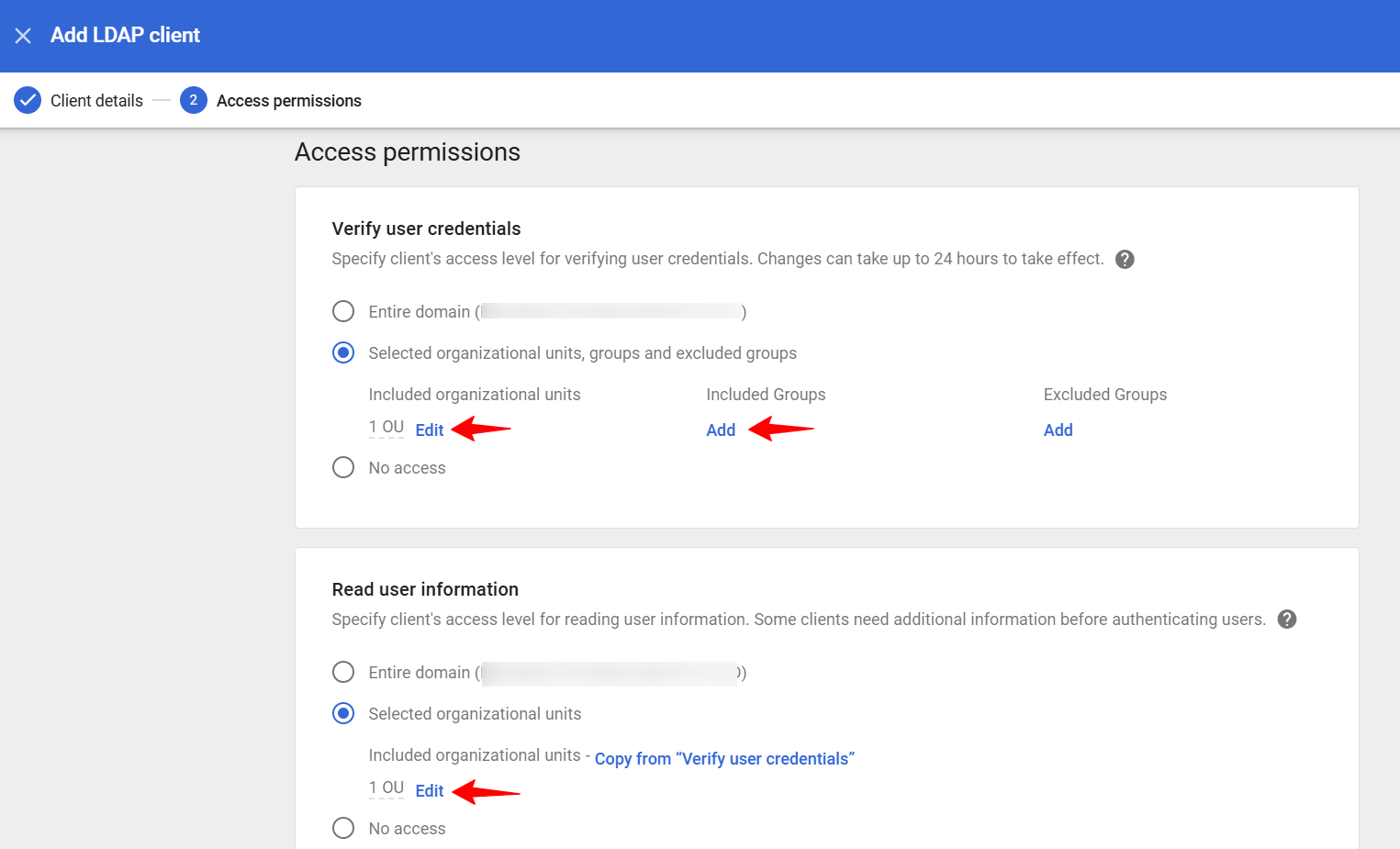
Choose “Selected organizational units, groups and excluded groups” if you want the settings to apply to selected users. Please make sure you select the correct Organizational Unit (OU)and Included Groups.
For “Read user information” if you select “Selected organizational units” then please make sure you select the same OU as “Selected organizational units, groups and excluded groups”.
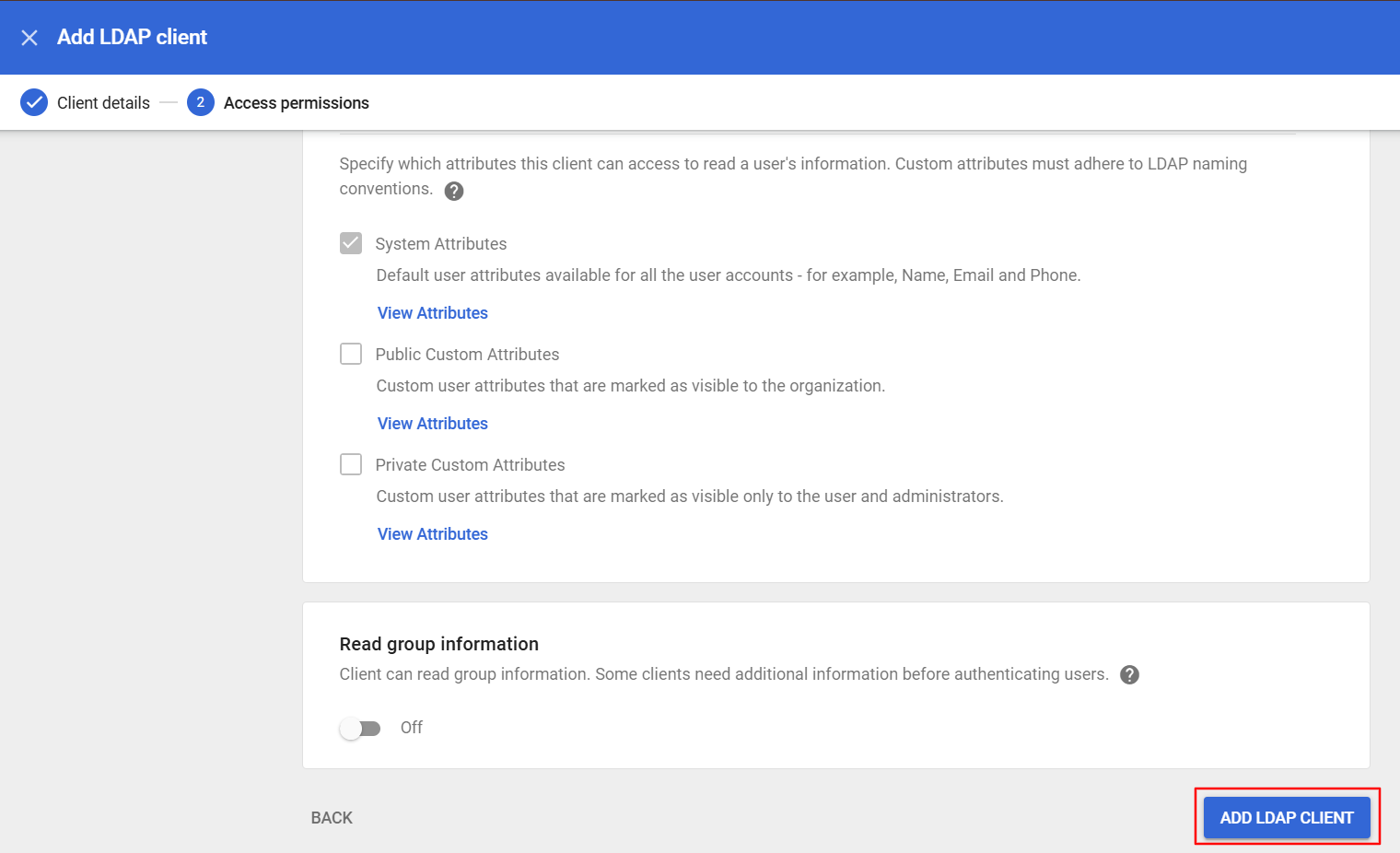
Once you have made your selection click on Add LDAP Client button.
This will generate a certificate, please download it and save it. Click on Continue to Client Details.
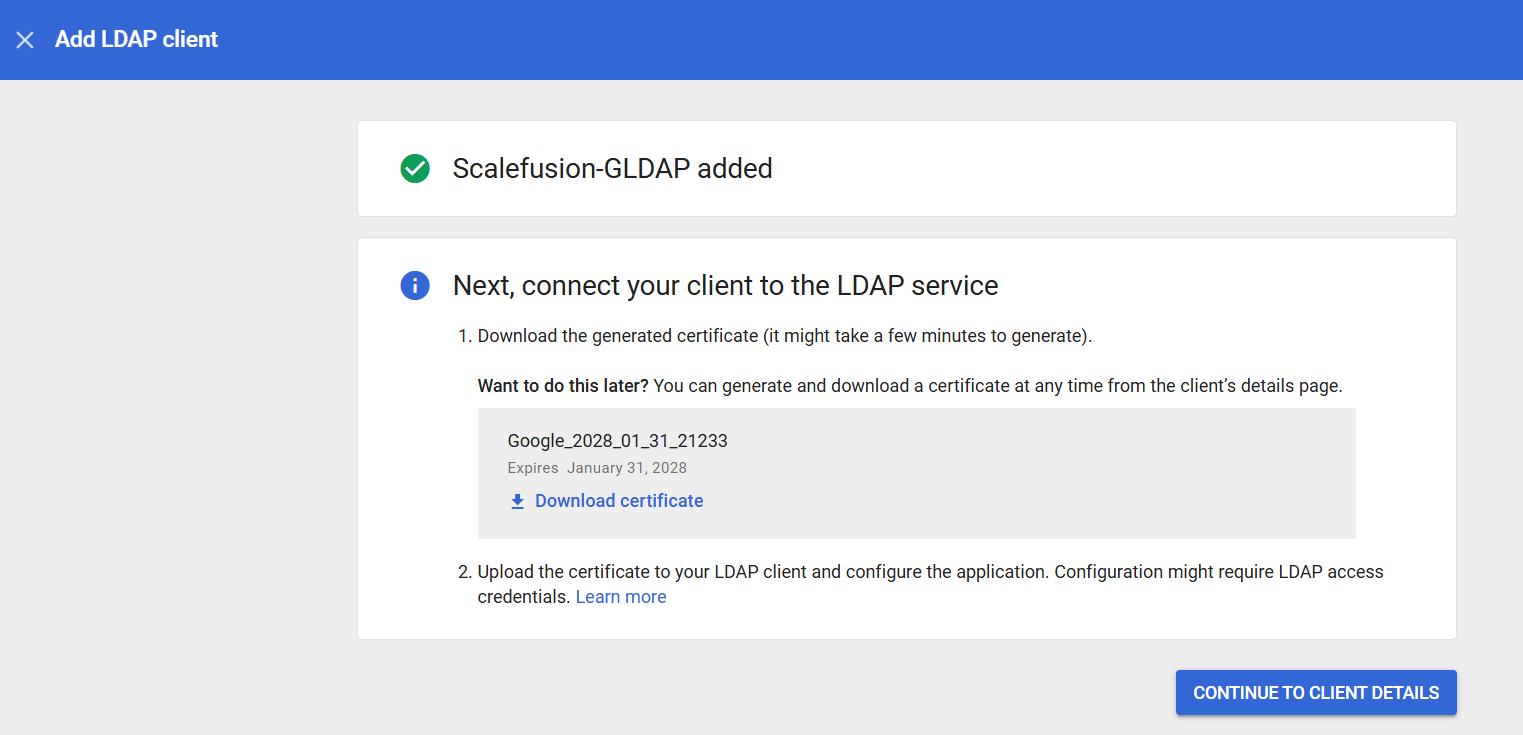
On this page click on Service Status and turn it On.
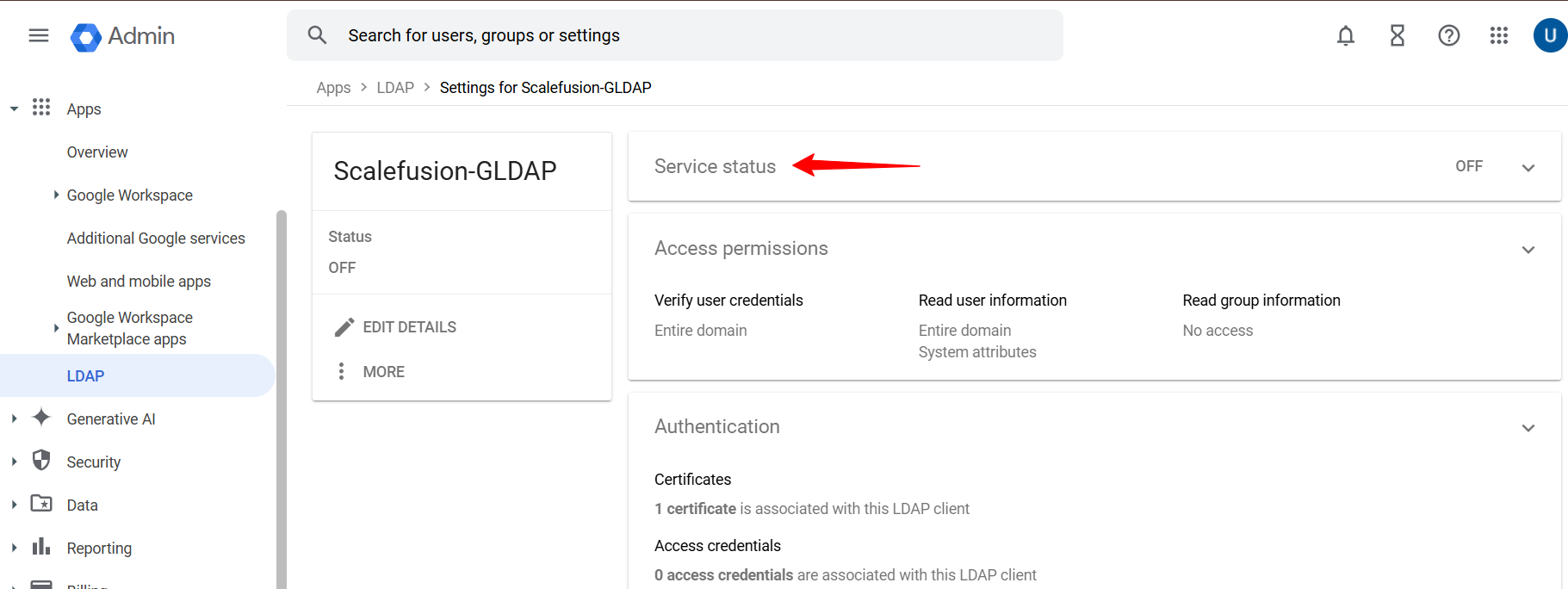
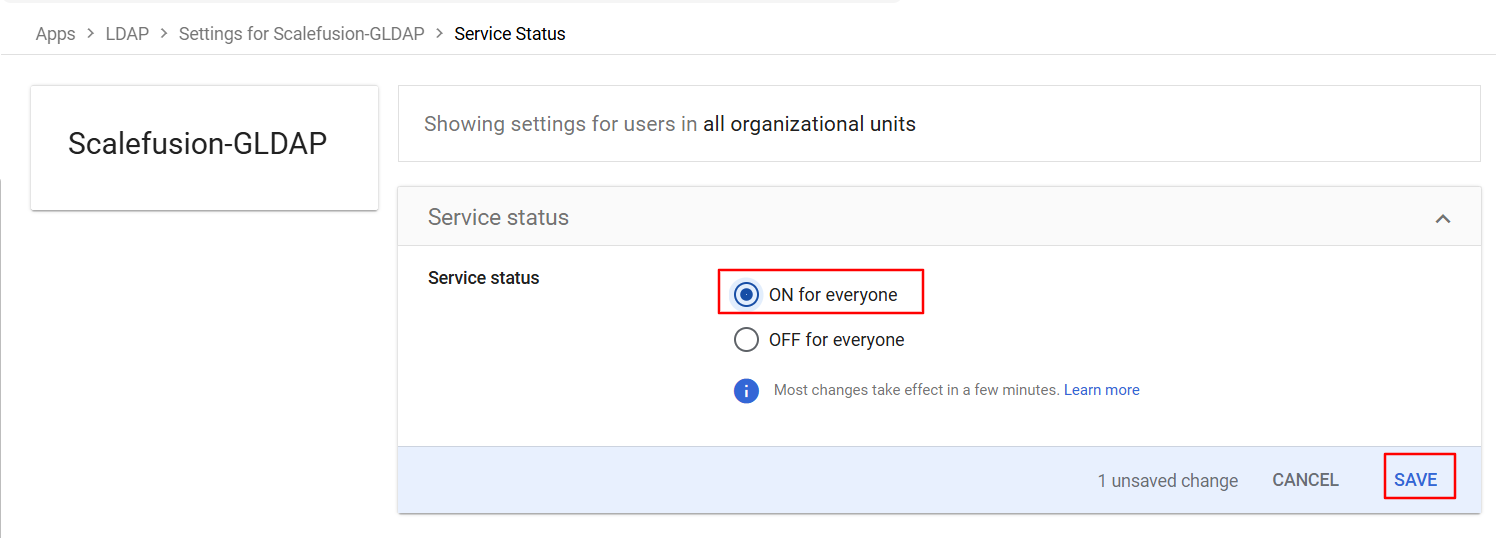
Come back to the previous page and click on Certificates in the Authentication tab.
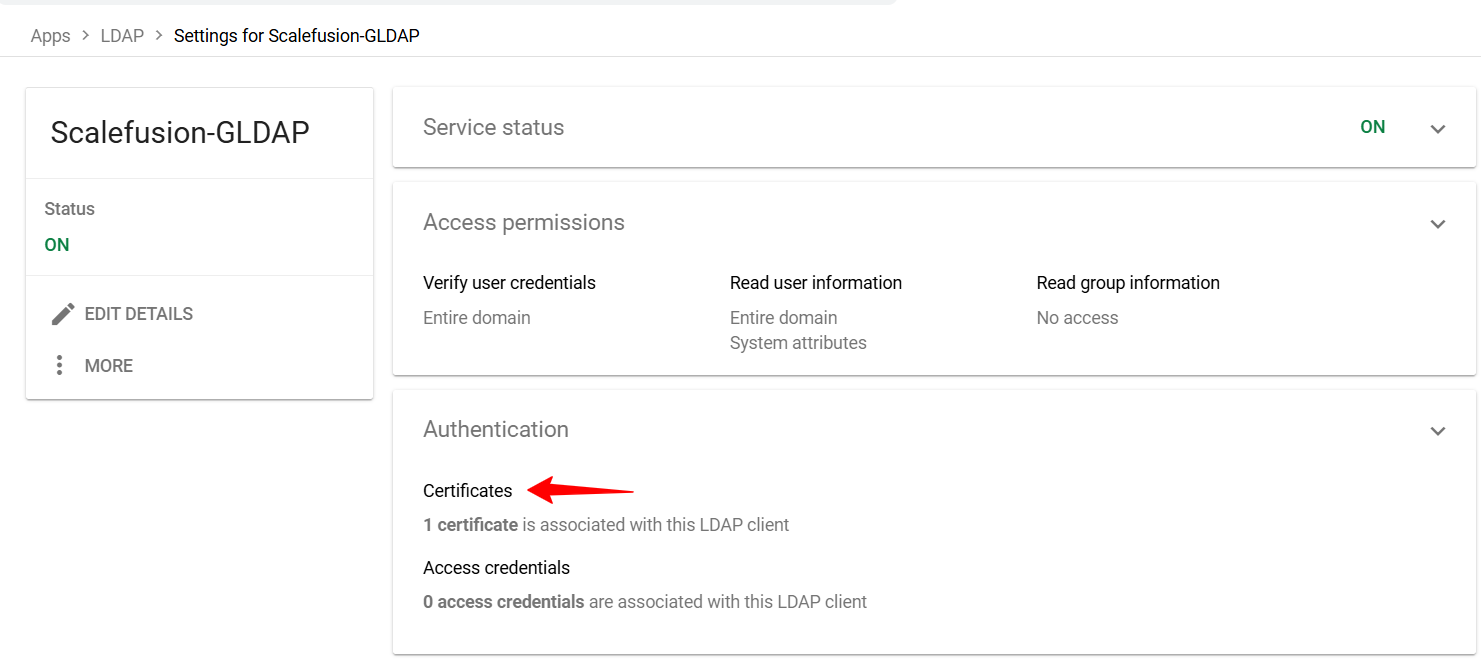
Here click on Generate New Credentials.
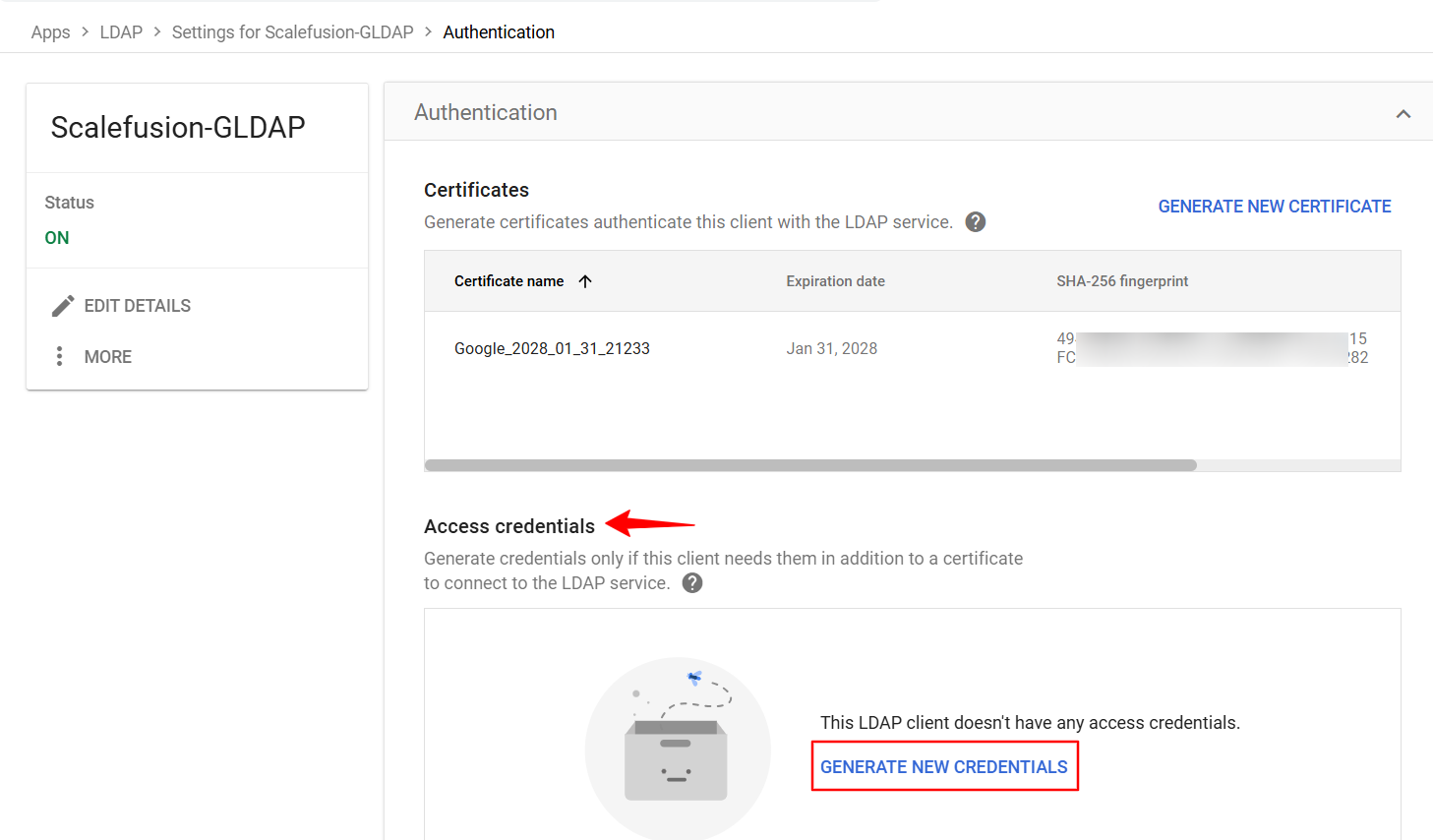
In the new pop-up window, copy and save the User name and password. These will have to be added to the Scalefusion dashboard (as shown in Step 3).

Step 3: Adding Google LDAP setup details to the Scalefusion dashboard
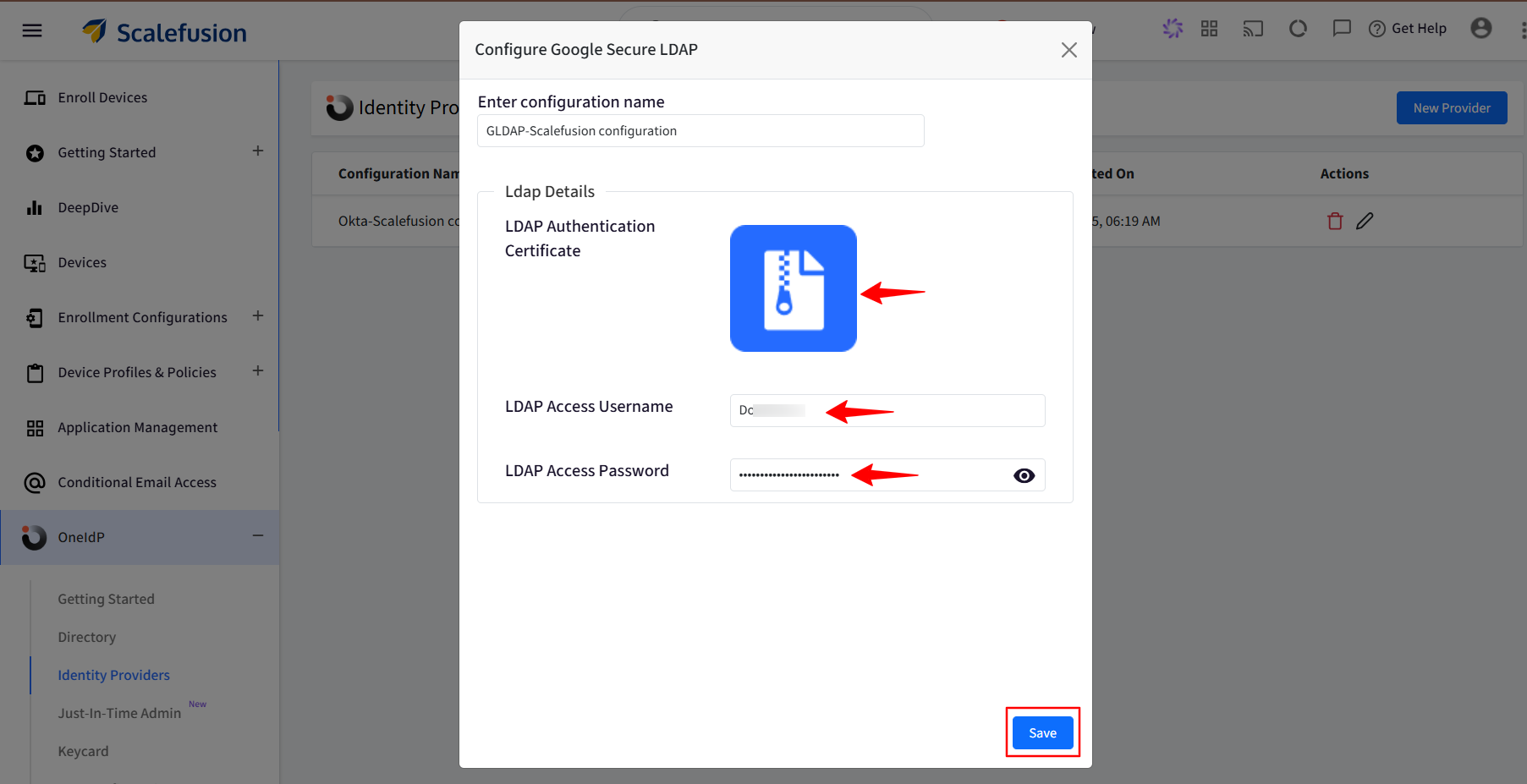
On the Scalefusion dashboard, upload the certificate that you downloaded in Step 2.
Next, add the Username and password that you saved as shown in Step 2.
Click on Save.
Step 4: Associating Google LDAP Identity Provider with a Directory
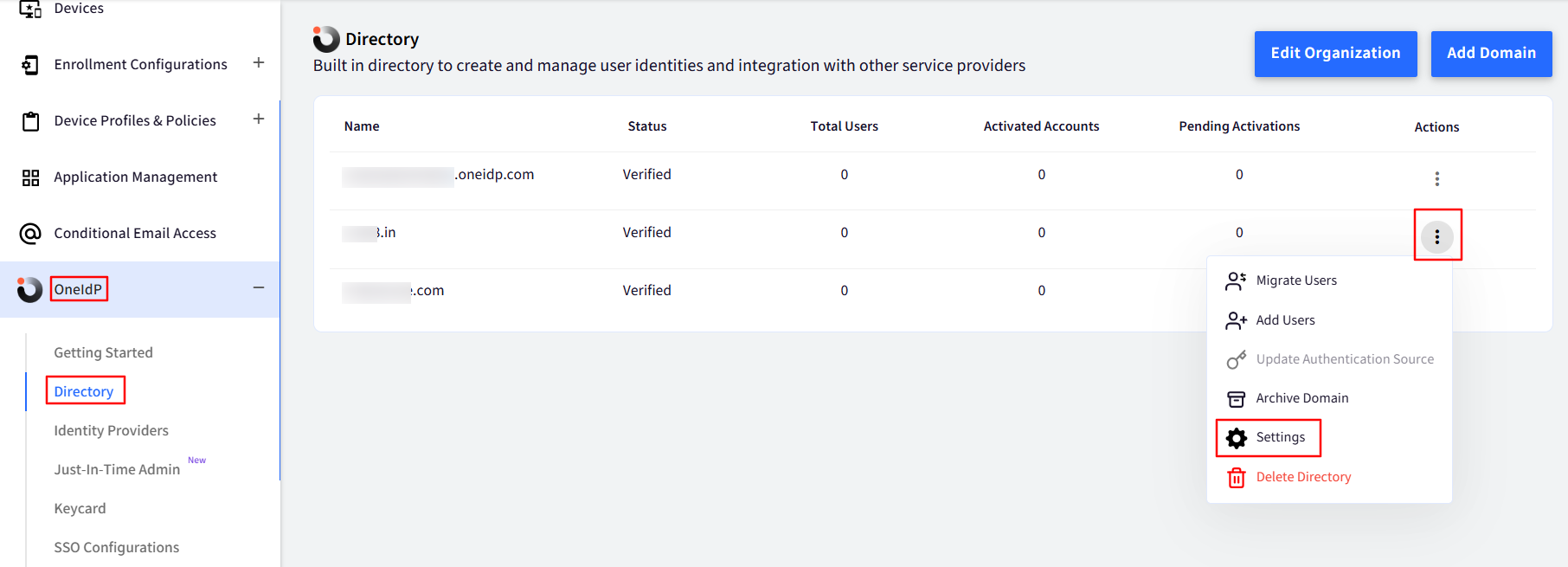
Navigate to OneIdP > Directory.
Click on the 3-dots under Actions for the concerned Domain.
Click on Settings.
Go to the Federated Authentication tab and toggle on the button for Google LDAP as an Authentication source.
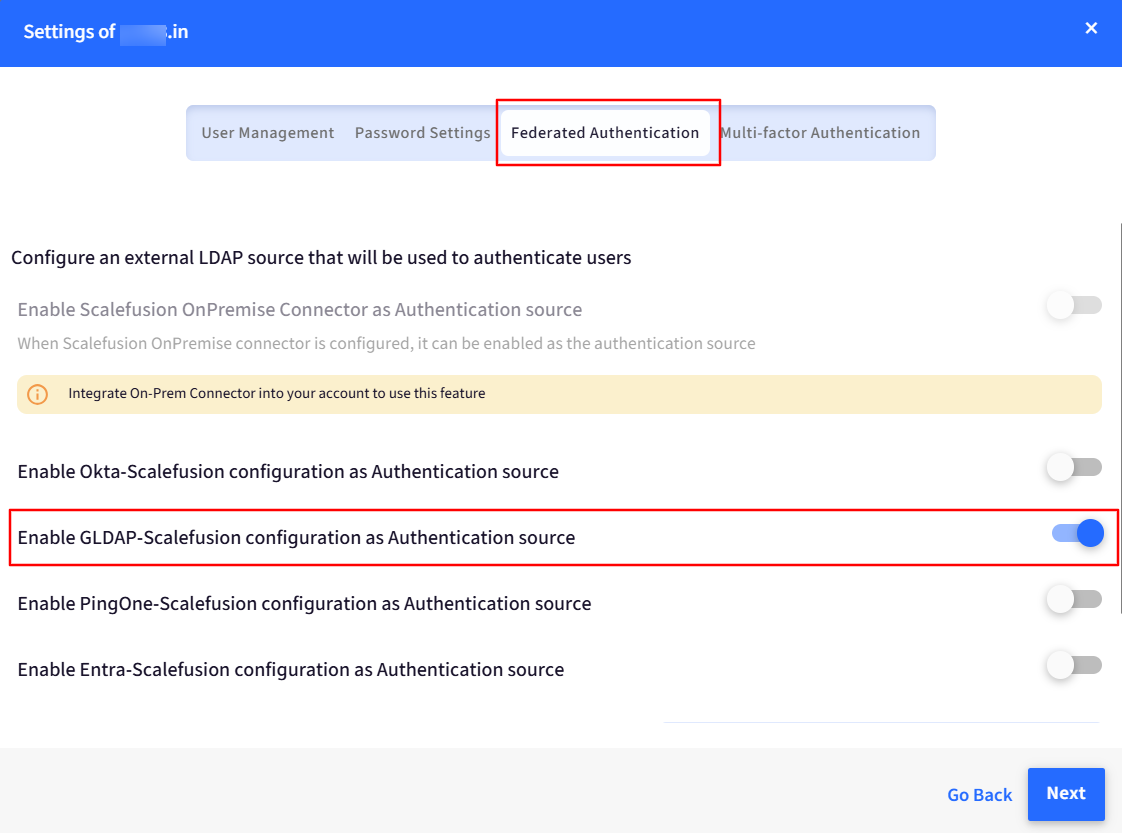
You can also “Set default authentication source”.
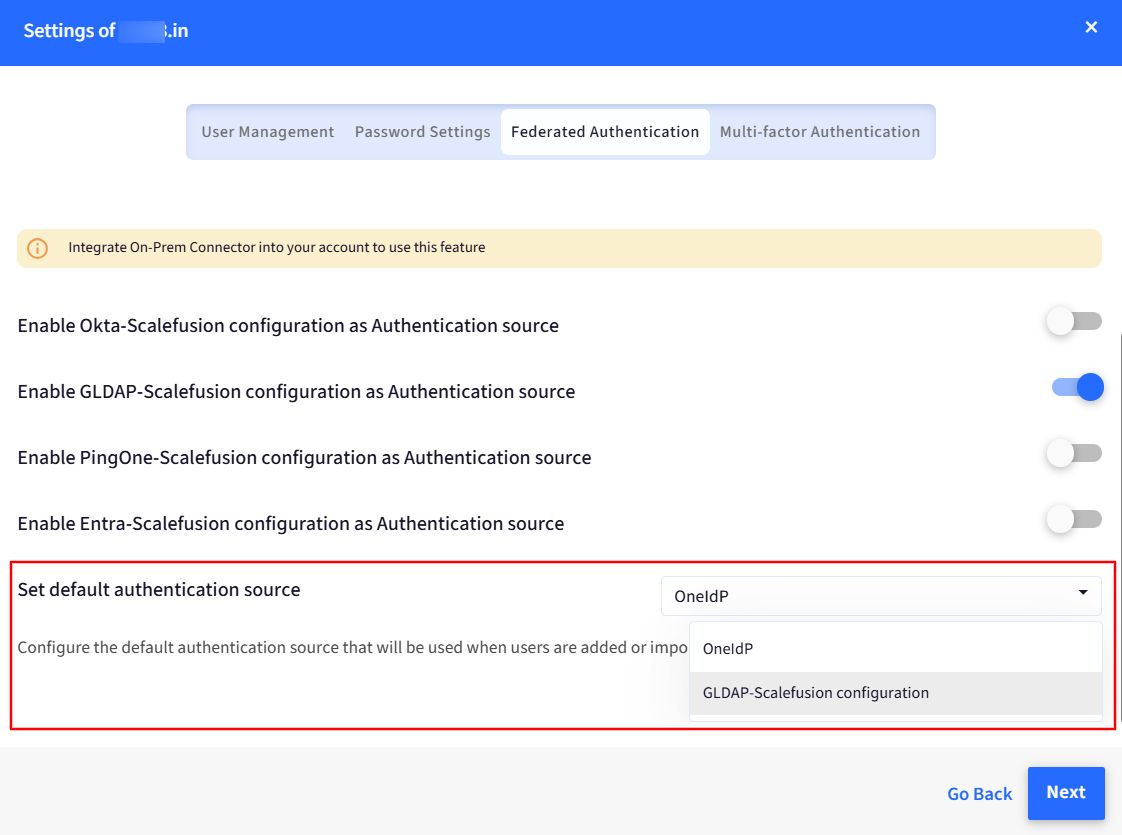
On setting a default authentication source, whenever you add any new user in the Scalefusion dashboard and migrate it to OneIdP, the default Authenticator would be Google LDAP.
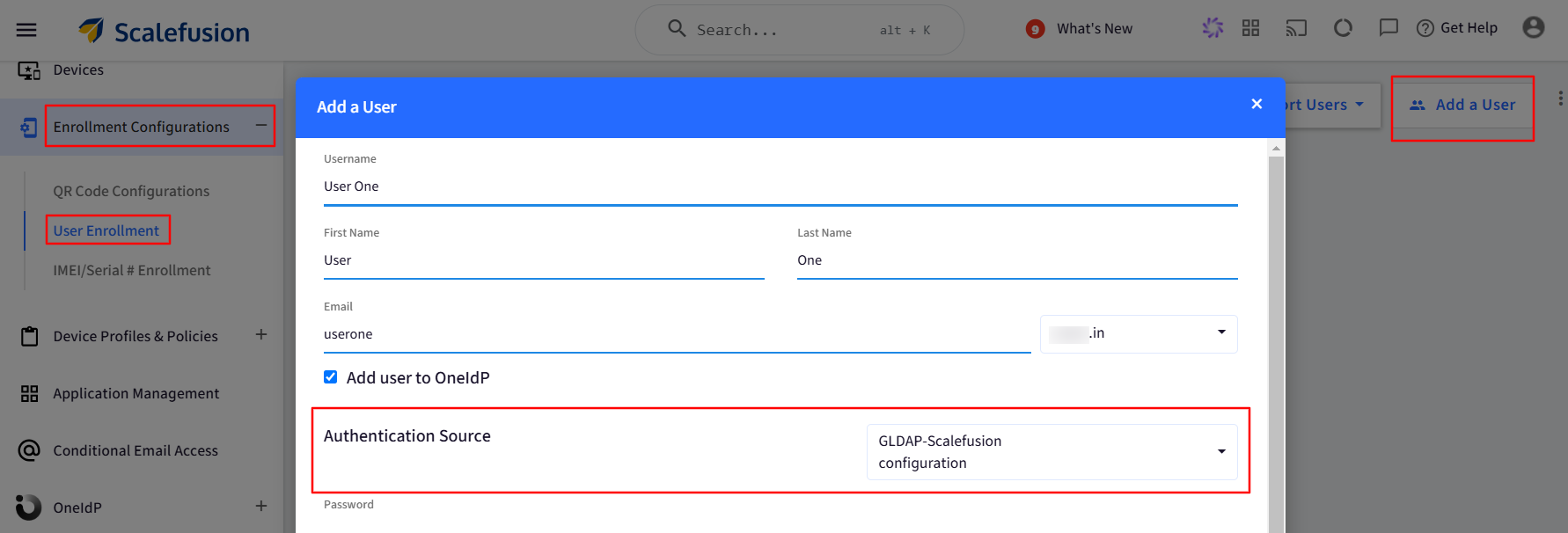
Click on Next and Save.
For existing users that are present in the Scalefusion dashboard, you can change the default authentication source by going to 3-dots under Actions > Update Authentication Source.
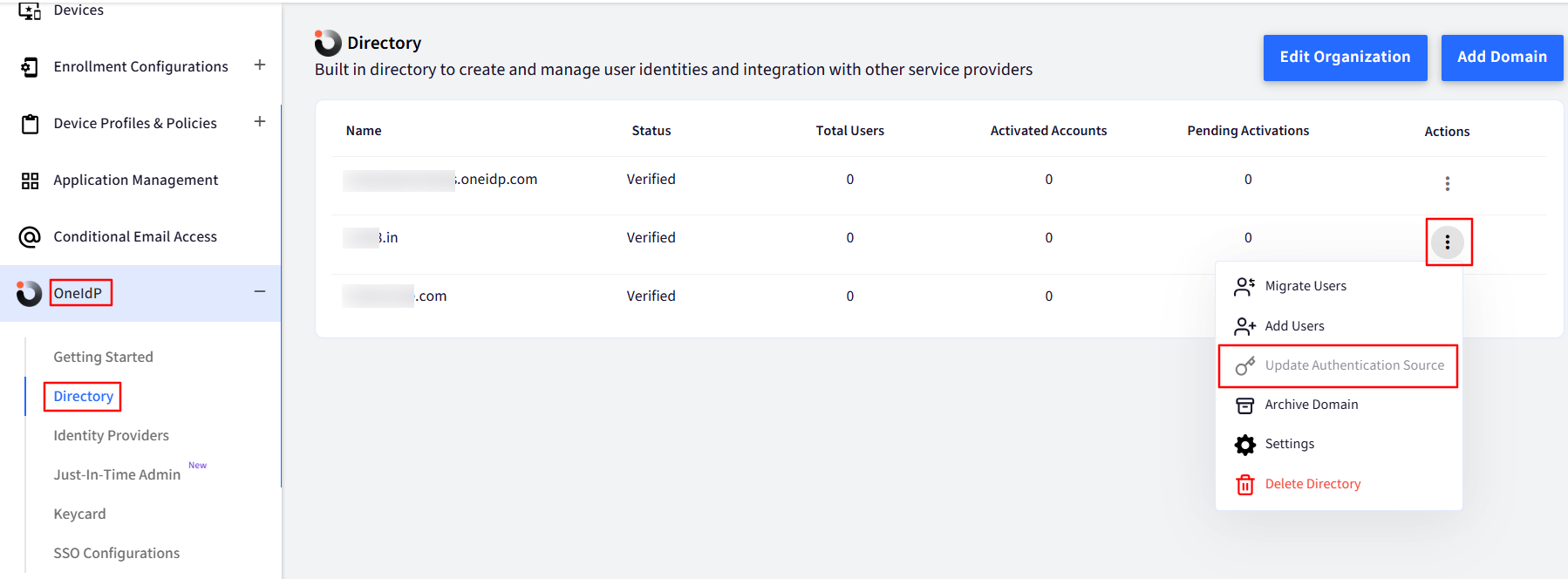
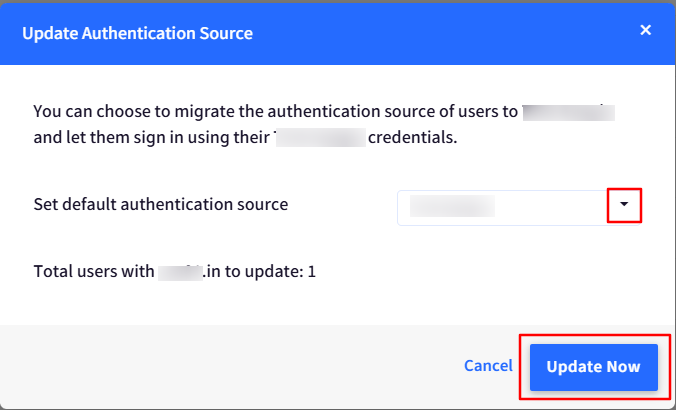
Select Google LDAP from the drop-down list for “Set Authentication Source” and click on Update Now.
User Login Flow
When Google LDAP is configured as the identity provider, and a user attempts to access the service, they will be redirected to the OneIdP login page after entering their email in Google’s sign-in page. There, the user will need to provide their email and password. Once authenticated, the user will gain access to the service.























