- 20 Dec 2024
- 5 読む分
- 印刷する
- PDF
Configure User Access and IdP User Settings
- 更新日 20 Dec 2024
- 5 読む分
- 印刷する
- PDF
Keycard plugin provides capability to configure settings with which you can control users' access to devices where users can be Identity Providers or otherwise. This article explains the settings.
- In Keycard configuration window, navigate to Keycard Settings on the left panel.
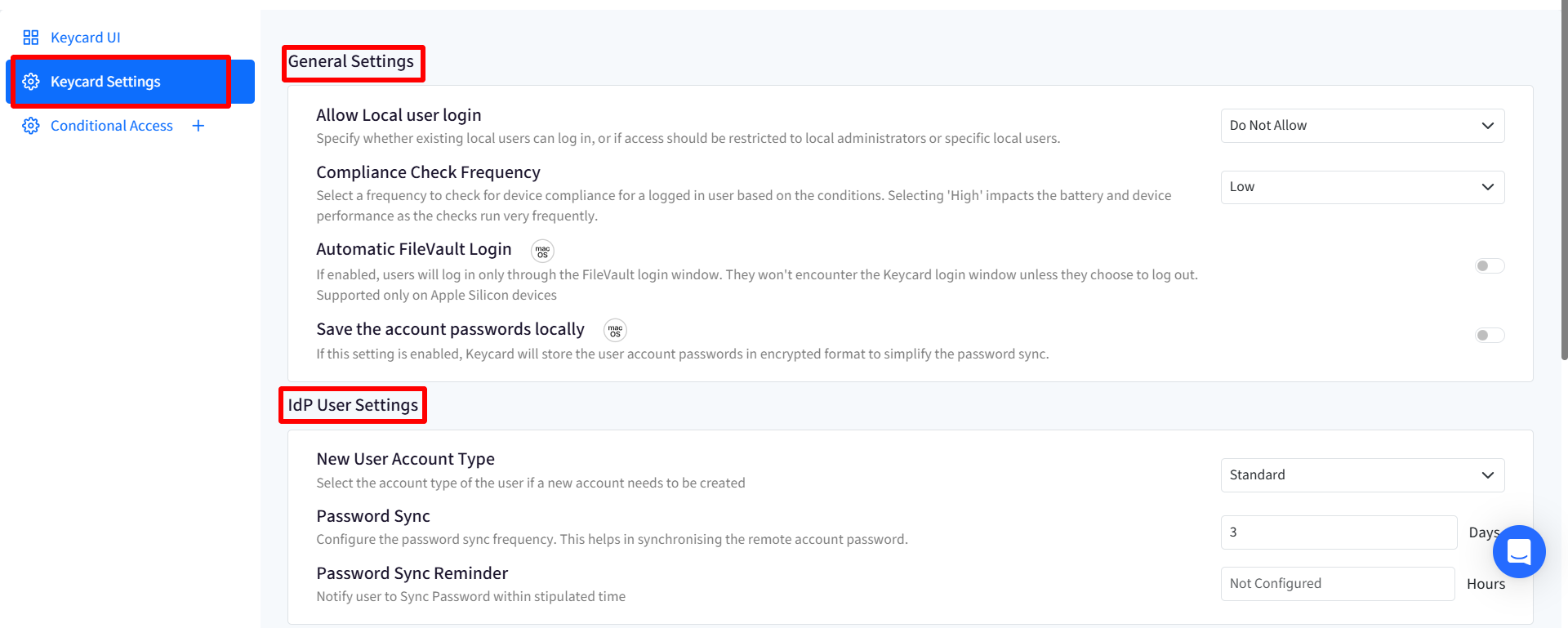
General Settings
- Allow Local User Login: Select an option to specify which Local users will display on the lock screen whether existing local users can log in, or if access should be restricted to local administrators or specific local users. Choose one from the following options in drop-down:

- Do not allow: No local users will be displayed on lock screen. This option will be visible if you are an IdP user.
- Enrolled User: Only the enrolled user will be displayed on the lock screen.
- All Accounts (default): All the user accounts will be displayed on the lock screen.
- Administrator Accounts: The Administrator type of users will be displayed on lock screen.
- Specify User Accounts: Specify the user accounts which will be displayed on lock screen. On selecting this option, a grid will be displayed where you need to enter Local user short names which have been previously configured, from the Device details > User Accounts section on Scalefusion Dashboard. You can search for a particular user which will populate list of users created. To add more than one user, click on New User link. If users are not configured (do not exist in UAM section), they can be configured from this section. Custom properties are also supported for configuring local users.

- Compliance Check Frequency: Select a frequency to check whether the device is compliant with the conditions specified under Conditional Access for logged in user accounts. The frequency can be selected from one of the following:
- High: The compliance check is performed every 5 minutes. Selecting 'High' impacts the battery and device performance as the checks run very frequently.
- Medium: The compliance check is performed every 30 minutes.
- Low: The compliance check is performed every 60 minutes.
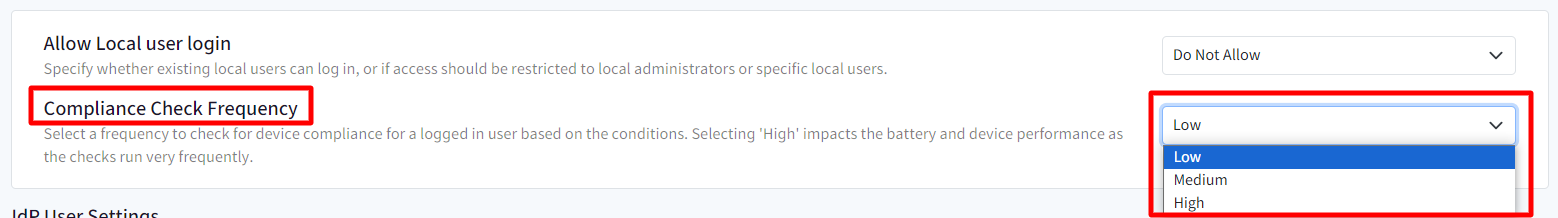
How User settings work on device
Taking an example, if you have allowed local user login for All accounts, and pushed the configuration, then on the device you will get a list of all the users existing on Scalefusion Dashboard. Select one and enter password to login to the machine.
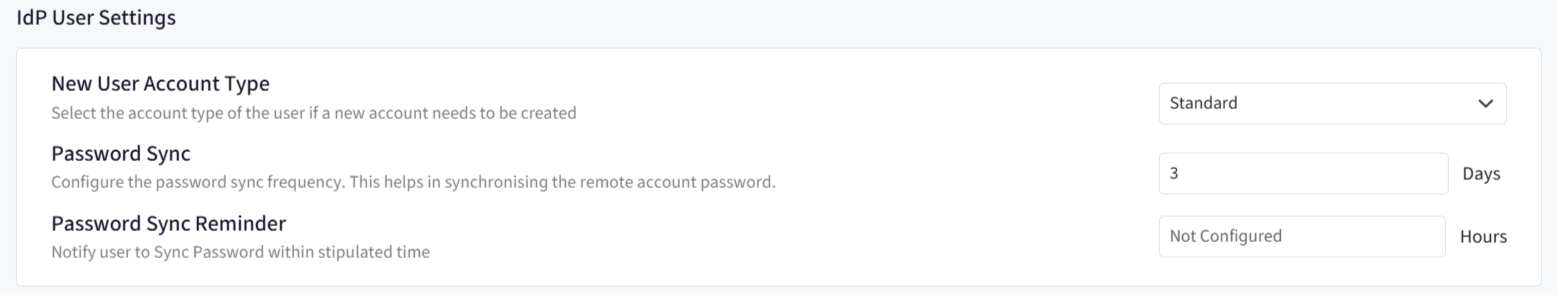
IdP User Settings
These settings are configurable if one of the following conditions are met:
- The account with which you have logged in on Scalefusion Dashboard, is an IdP account (Google Workspace / Microsoft Entra/ OneIdP / Okta / PingOne / OnPrem AD) For OnPrem AD, the OPC setup should be done on Scalefusion Dashboard
- You have created a Directory in OneIdP (with custom and/or default domain)
- Also, the users should be existing under User Enrollment section on Scalefusion Dashboard.
- For identity providers other than oneidp, following settings should be enabled on Scalefusion Dashboard:
- Under User Enrollment > Enrollment & sync settings, the setting Enforce users to sign in using <Identity Provider name> should be enabled
- If User group settings are configured and admin wants to override global enrollment settings, the setting Override Global settings should be enabled with Enforce users to sign in using <Identity Provider name> selected.
Here are the settings:
- New User Account Type: For a new user account created on the device, you can select the new user's account type whether it will be Standard or Administrator. The user should be existing in the User Enrollment section on Scalefusion Dashboard.
- Password Sync: Configure the frequency for synchronizing remote account password. It may happen that IT admin sets/resets the password for an IdP user account, remotely. This password has to be synced with the device and you can select the frequency (in days) at which synchronizing with the device takes place. By default frequency is set to 3 days. It can be selected anywhere between 1 to 30 days.
- Password Sync Reminder: This will notify user to complete sync password activity. Specify a time limit (in hours) and user will be notified to sync password within that timeframe. Reminder time can be set anywhere from 0 to 72 hours. Also, the users will not get logged off to perform the online login, the reminder window is shown to them to complete login.
 If Password policy is set by admin, the remote account password should adhere to the Password policy rules.If the IdP password does not match the password policies configured then the user is alerted to change their IdP password.
If Password policy is set by admin, the remote account password should adhere to the Password policy rules.If the IdP password does not match the password policies configured then the user is alerted to change their IdP password.
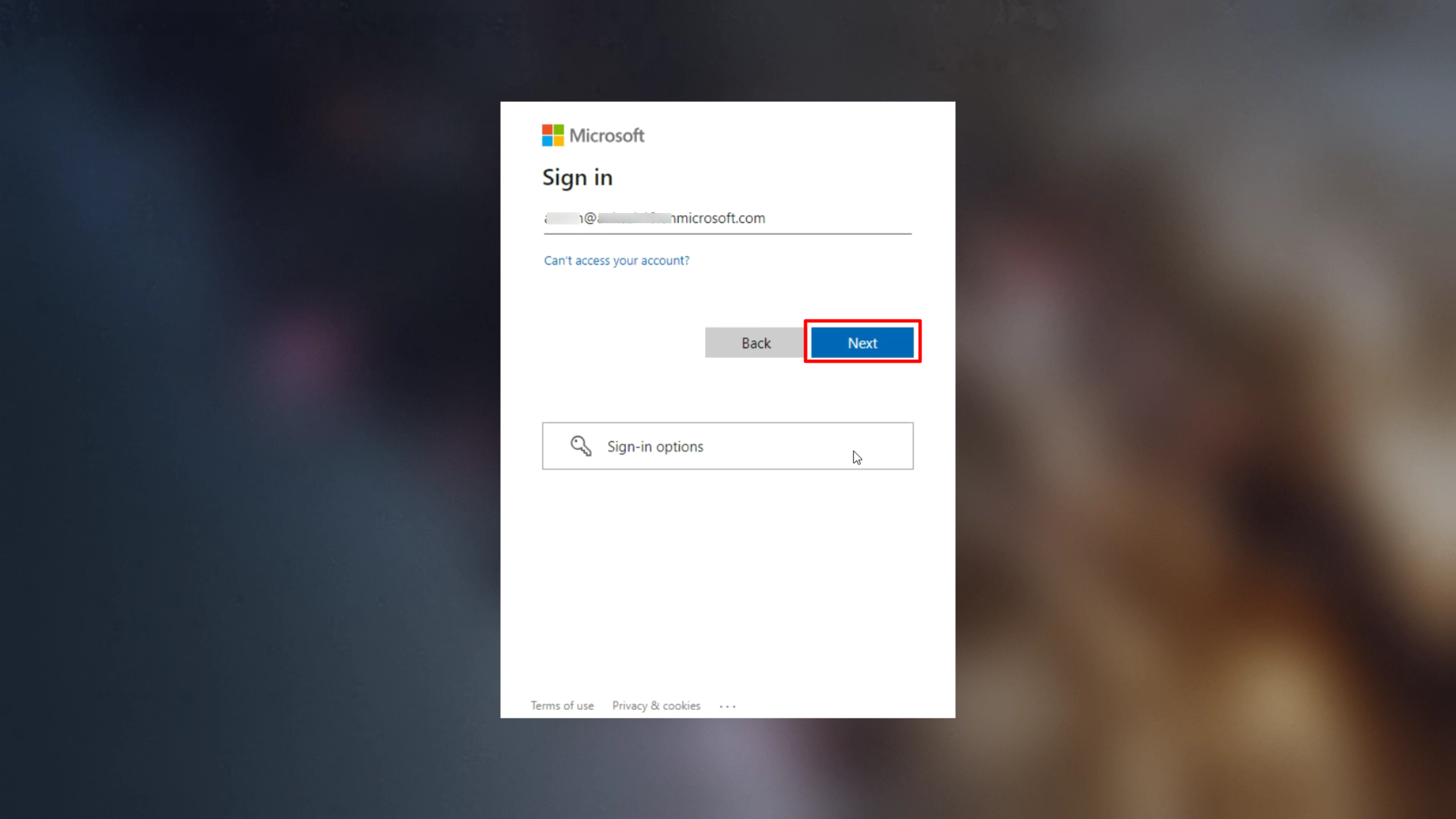
How IdP user settings work on the device
When you push Keycard configuration on the device with IdP user settings configured, an additional link Add work account is created on the device, on the login screen. Click on it and enter your account credentials to authenticate.
- Taking an example of a domain configured in O365 account, click on Add work account and enter your email address on the login screen.

- The domain being configured in O365 account, the next screen will be from Microsoft. Enter your credentials (email address and password) and follow the steps to authenticate.
- Once authenticated, a new user account will be created on the device with the user type (Standard or Administrator), as selected in the New User Account type in IdP User Settings, with which you can login on the device next time. The user will also be added in Device details > User accounts section on Dashboard.
- If a local user with the same username already exists on the device, then it will get linked to the existing user present on the device. Hence, it is up to the discretion of IT admins whether to have a new user created on the device or not. If they want a new user to be created then the username in User Enrollment section should be different from the users already existing on the device.
- Username can be of maximum 20 characters. If it is longer, then it will be truncated till the 20th character. Also, if there are similar usernames then for the user who signs in next, after 18th character the username will automatically trim with 00, 01, 02 and so on appended to it. The full username will be used as the display name on the login screen.
Domain Settings
- Enforce Domain Sign-in on Windows Devices: Allows users to sign in to the windows machine directly with their domain credentials. In this case, a new user account will not get created in User Account Management section or in User Management on the dashboard. Please note that once domain sign in has been enforced, only domain users or local users can sign in to the machine.
- To sign in with local users, end users will have to use the special convention of .\localaccountname
- Other users like Directory users cannot sign in to the machine if they DON’T exist (matching username) in the domain
- Join the device to On-Prem AD: Enabling this setting joins the windows device with a local domain once Keycard configuration is pushed, giving access to their Active Directory. As a result, the users belonging to the domain, can directly login to the device with their domain credentials. Enter the Active Directory domain name, admin username and password with which you want to join the Windows device.











