What is SCIM?
SCIM (System for Cross-domain Identity Management) is an open standard protocol designed to streamline and automate the exchange of user identity data between identity providers (IdPs) such as Microsoft Entra, Okta, PingOne, or OneLogin and service providers like Scalefusion. SCIM provides a standardized way to:
Create, update, and delete user identities automatically.
Synchronize user attributes (e.g., name, email, phone number, department) across platforms.
Assign users and groups to applications or services in a consistent, secure, and scalable manner.
Scalefusion now supports SCIM (System for Cross-domain Identity Management) v2.0 to streamline user and group management by enabling IT admins to import and synchronize users from popular identity providers like Okta, Microsoft, PingOne, OneLogin, and more. Through the Integrations > SCIM Connectors section, admins can configure SCIM integrations that allow Scalefusion to automatically listen for and apply changes pushed from these external SCIM sources, keeping the user and group database up-to-date in real-time.
Benefits of SCIM
This SCIM integration enhances Scalefusion’s flexibility by allowing organizations to import users from multiple identity sources within a single console. For example, organizations using a combination of Google Workspace (GWS), Okta, and Microsoft can:
Sign in with Google Workspace and import users and groups directly,
Set up SCIM connectors for Okta and Microsoft to synchronize additional users and groups,
Use OneIdP’s identity federation to enable users to log in with their existing credentials without requiring a separate SSO setup.
Similarly, organizations with on-premises Active Directory alongside Microsoft can sync users from these sources and leverage OneIdP for seamless identity federation, simplifying user access management across different environments.
Supported Identity Providers for SCIM Integration
Scalefusion supports SCIM 2.0 integration with the following identity providers:
Okta
Microsoft Entra ID (formerly Azure Active Directory)
PingOne
OneLogin
Any SCIM 2.0-compliant Identity Provider
If your identity provider supports the SCIM 2.0 protocol, it can be configured to work with Scalefusion for automated user provisioning and deprovisioning.
Pre-requisites
Access to Identity Provider’s admin console
Users should either be subscribed to Scalefusion Enterprise 2025 and 2023 Plans or SCIM Integration feature should be enabled for their account
How it Works
Set Up the SCIM Connector in Scalefusion:
Begin by configuring the SCIM connector within the Scalefusion dashboard. This creates the necessary endpoint and authentication details that the Identity Provider will use to communicate with Scalefusion. The detailed steps are mentioned below.Configure SCIM in Your Identity Provider’s Admin Console:
Next, set up the SCIM integration on your Identity Provider’s side (e.g., Okta, Microsoft Entra, PingOne, OneLogin) by entering the Scalefusion SCIM endpoint and authentication tokens. Refer to the specific setup guides for your identity provider (e.g., Okta, PingOne) for detailed configuration instructions.Automated User and Group Provisioning:
Once the SCIM connection is established and activated, user and group information is automatically provisioned and synchronized between the Identity Provider and Scalefusion, ensuring up-to-date access management.
Configure SCIM Connector on Scalefusion Dashboard
On Scalefusion Dashboard, navigate to Integrations > SCIM Connectors
Under SCIM Configurations click on Add New
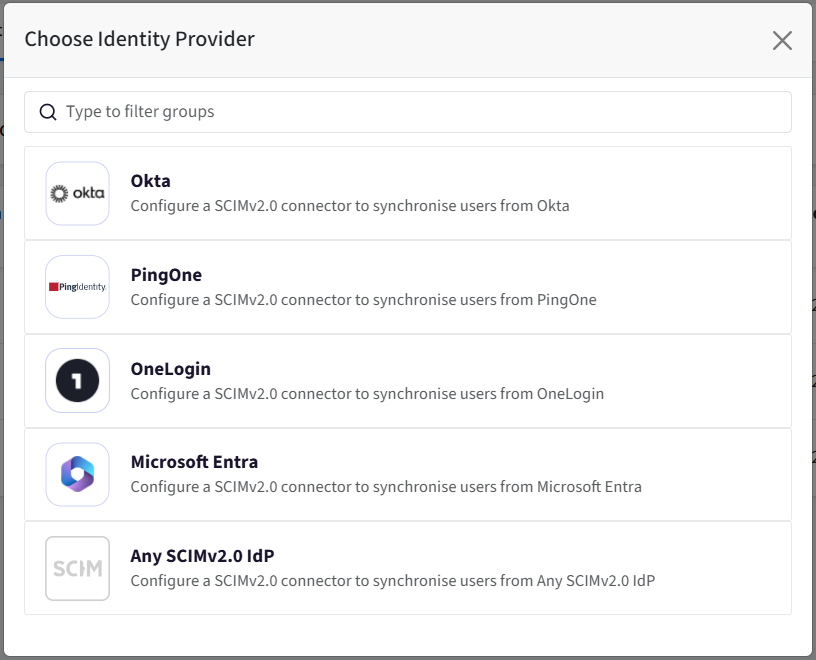
In the dialog box that opens, select the respective Identity Provider
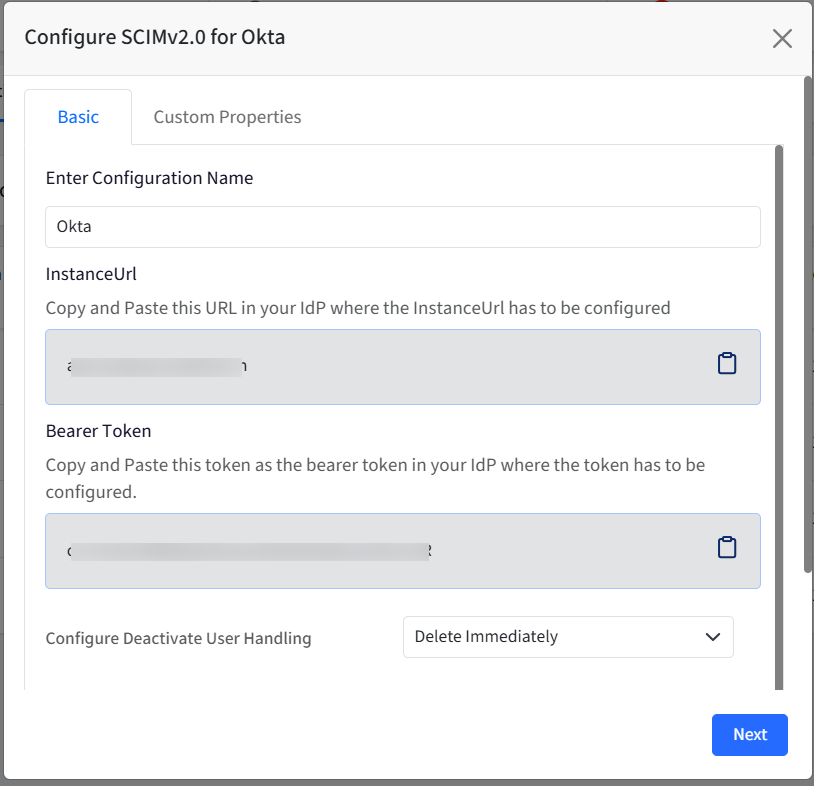
This brings up the following dialog.
Basic: Under this, enter the following details and click Next
Enter Configuration Name
Instance Url: Copy and Paste this URL in Okta where the SCIM API endpoint/URL has to be configured
Bearer Token: Copy and Paste this token as the bearer token in the identity providers’ console where the token has to be configured.
Configure Deactivate User Handling: Choose one of the following that determine how and when users are removed or disabled from the target system:
Delete Immediately: As soon as a user is deprovisioned (e.g., removed from a group or no longer meets assignment rules), the user is permanently deleted right away.
Soft Delete & Delete after 24 hours: The SCIM connector first sends a soft delete request. This deactivates the user but does not delete them yet. After 24 hours, a full DELETE request is sent to permanently remove the user.
Delete Company Owned Devices assigned to the user when user is deleted: When enabled, Scalefusion will automatically delete any company-owned devices assigned to the SCIM user once the user is deleted via SCIM.
Please note that the BYO devices of the users will be deleted when users are deleted.
Note: The screenshots below show configuration for Okta. In similar manner they can be created for other Identity Providers.
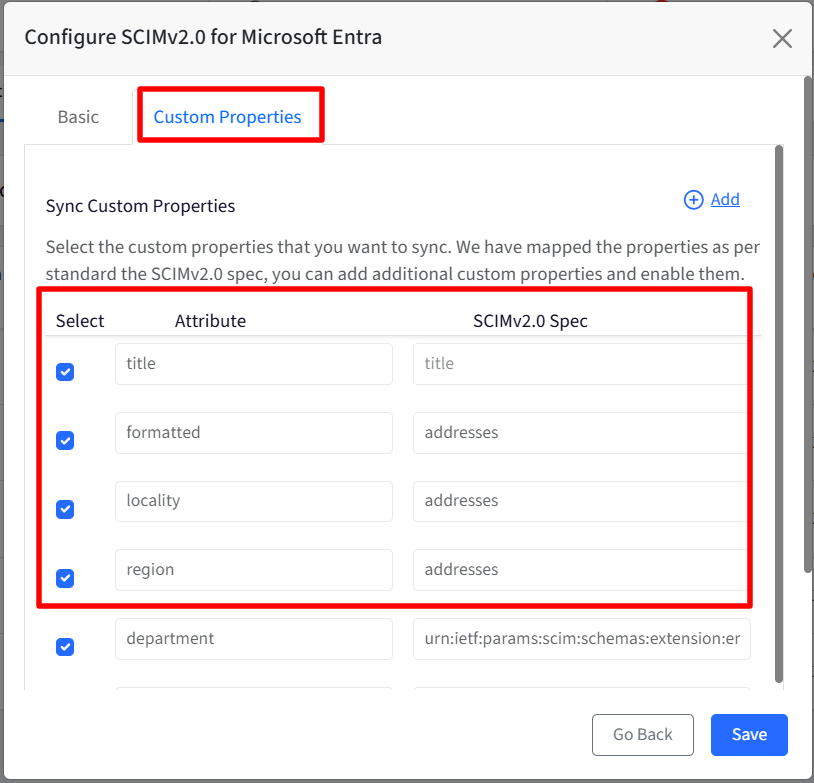
Custom Properties: Use this option to choose which custom user properties should be synchronized with your identity provider. By default, properties are mapped according to the SCIM v2.0 standard. If you have additional custom properties, you can add them here and enable syncing for those properties. This allows you to control exactly which custom data fields are included during synchronization.
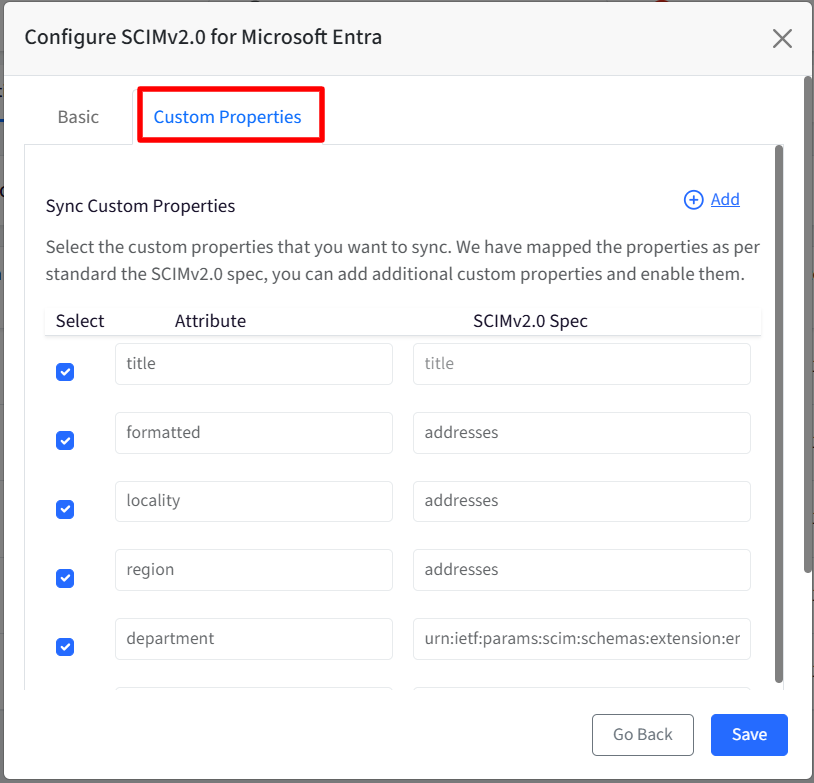
How it works:The system retrieves the latest custom properties and updates the mappings each time the configuration is accessed. Only properties that match the SCIM v2.0 specification or are supported by the selected identity provider (IdP) are displayed; all others are ignored. The properties are listed under following heads:
Attribute: Represents the user attribute from Scalefusion. These are automatically displayed when they match the SCIM v2.0 specification or are supported by the selected IdP.
SCIM v2.0 Spec: This field represents the corresponding SCIM v2.0 specification. The value is automatically populated when a matching SCIM v2.0 specification or supported IdP mapping is found.
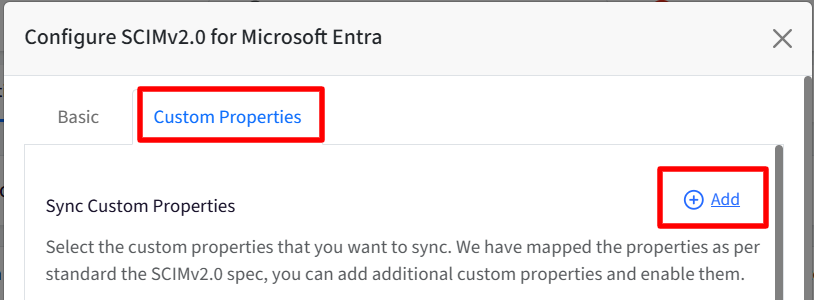
To add a new field, click Add. A new row is added at the bottom of the list.
Define the value using the
$user.prefix. When you type$user., all available user attributes (from Scalefusion Dashboard > User Management) are shown, allowing you to select the required attribute.Note: The selected user attribute must also exist in the identity provider’s portal.
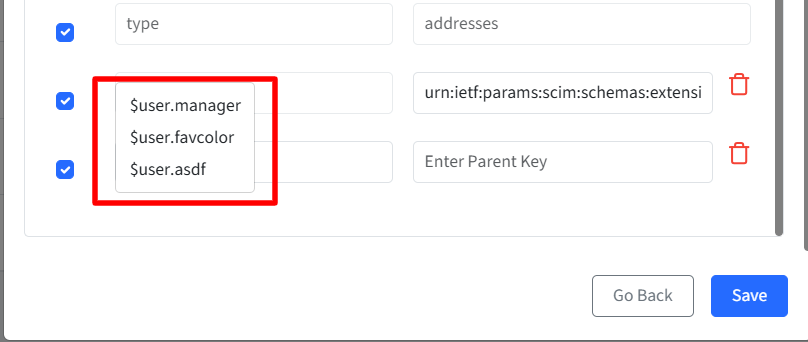
After selecting the attribute, enter the corresponding parent key as defined in the SCIM v2.0 specification. The parent key is important and can be taken from the Identity Provider’s SCIM payload structure.
For example, a valid parent key format is:
urn:ietf:params:scim:schemas:extension:enterprise:2.0:User
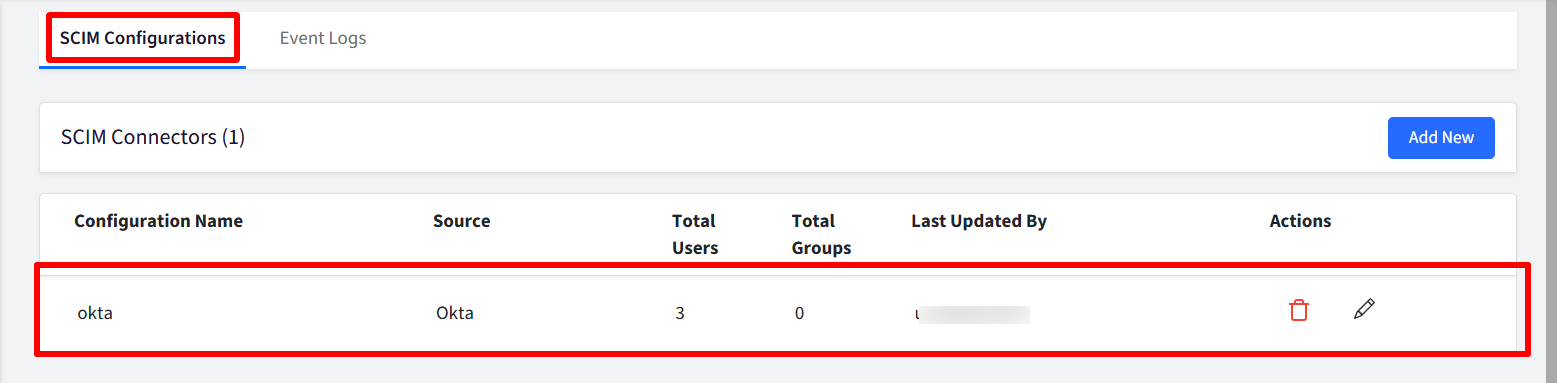
On saving, the configuration will be created and visible on dashboard under SCIM configurations tab.
Note: If Maker/Checker is enabled, the configuration will be sent for approval. User can add comments while sending for approval.