When managing employee-owned devices, it becomes imperative to make sure that the device adheres to compliance standards such as device integrity, security and compatibility. Managing Employee-owned devices becomes even more challenging because of the wide variety of Android devices available. Allowing access to Work Apps on a compromised device is a high-security risk and can lead to critical information loss and/or theft.
To mitigate such risks, Scalefusion uses Google Play Protect API to check device compliance. The Google Play Protect API helps Scalefusion assess the security and compatibility of Android devices.
Google Play Protect examines software and hardware information on the device where the Work Apps are being used. The service then attempts to find this same profile within a list of device models that have passed Android compatibility testing. The API also uses this software and hardware information to help you assess the basic integrity of the device. This attestation helps Scalefusion to determine whether or not the particular device has been tampered with or otherwise modified.
Using Scalefusion's Device Profile for Personal (BYOD) devices, you can choose the Google Play Protect compliance levels and the compliance actions that need to be taken in the event of a violation. Follow the steps below to setup Google Play Protect checks,
- Navigate to Device Profiles & Policies > Device Profiles.
- Create or Edit the Personal(BYOD) profile where you want to set the Compliance levels.
- Navigate to the Restrictions > Device Management > Compliance section.
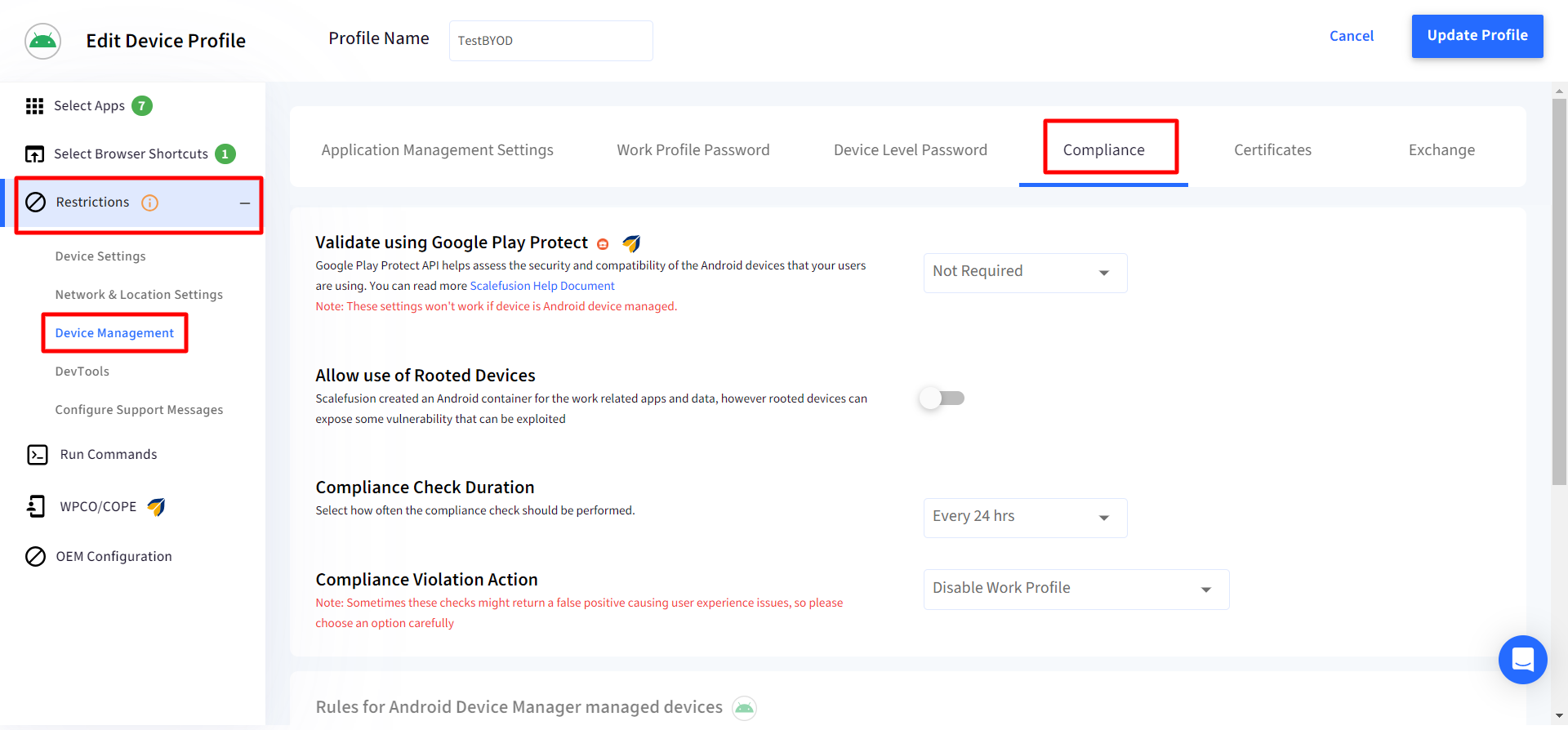
- Here you can enable the use of Google Play Protect API and the action to be taken in case there is a compliance violation,
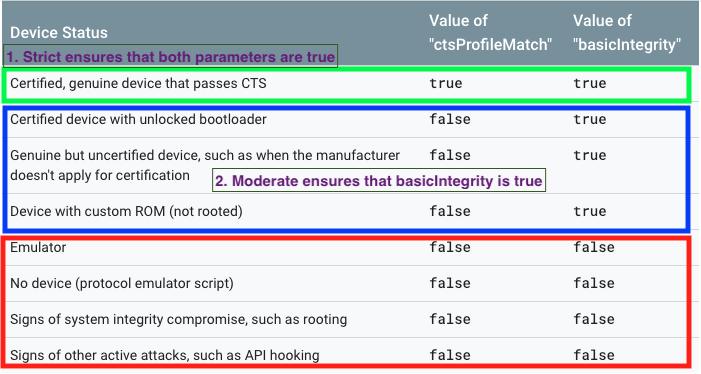
- Validate using Google Play Protect: You can choose between a Strict or a Moderate level for validations. Scalefusion uses the ctsProfileMatch and basicIntegrity flags to make sure that the device is compliant. A Strict check would mean both the values should be true, and a Moderate check would mean at least the basic integrity is true. The reference image (taken from Google's document) with additional notes shows the various possibilities.Devices should be EMM Managed
- Compliance Check Duration: Select the duration and how often the compliance check has to be performed. The following are the options to choose from:
- Every 24 hours
- Every 48 hours
- Weekly Once
- Compliance Violation Action: Once you have selected a validation level, you can choose between the following options on what action should be taken.
- No Action: No restrictions will be applied to work apps, but results will be captured for future reference.
- Disable Work Profile: Use this option to disable the work apps but keep their data if a violation is detected later.
- Remove Work Profile: Use this option to completely remove the work apps and their data if a violation is detected later.Sometimes these checks or APIs may return a false positive, so please choose a violation action accordingly.
- Validate using Google Play Protect: You can choose between a Strict or a Moderate level for validations. Scalefusion uses the ctsProfileMatch and basicIntegrity flags to make sure that the device is compliant. A Strict check would mean both the values should be true, and a Moderate check would mean at least the basic integrity is true. The reference image (taken from Google's document) with additional notes shows the various possibilities.
Rules for Android Device Manager Managed Devices
From this section, you can configure compliance actions for devices managed by Android Device Manager. They are as follows:
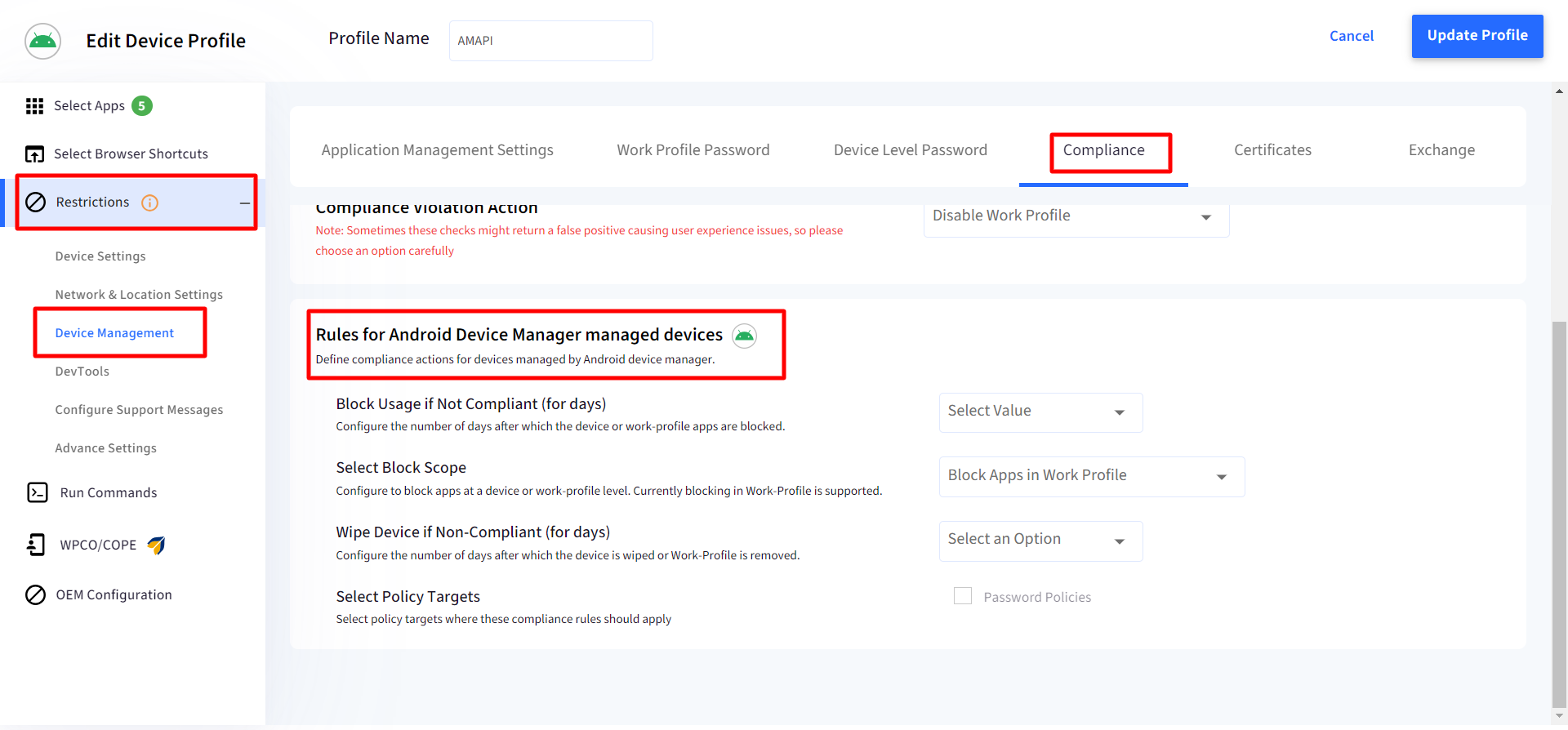
- Block Usage if Not Compliant (for days): Configure the number of days after which the device or work-profile apps will get blocked.
- Select Block Scope: Select whether to block the apps in the work profile or device profile. Currently, blocking in Work-Profile is supported.
- Wipe Device if Non-Compliant (for days): Configure the number of days after which Work-Profile is removed from the device. This will be enabled only if Block Usage is enabled and adds an additional 1 day to what you have configured for blocking usage of apps.
- Select Policy Targets: Select the Policies on which these compliance rules will be applied. Currently, they can be applied to Password Policies.