- 29 Oct 2024
- 6 Minutes to read
- Print
- PDF
I/O Device Access Control
- Updated on 29 Oct 2024
- 6 Minutes to read
- Print
- PDF
I/O Device Access Control is a crucial security measure that empowers administrators to strictly regulate the connection of external devices to managed devices. By controlling which I/O devices can be accessed, you can effectively prevent unauthorized data transfers and protect your organization's sensitive information. This mitigates the risks associated with connecting untrusted devices to your network. At the same time you can exercise precise control over which I/O devices are allowed to access your devices.
By implementing I/O Device Access Control, you can significantly strengthen your organization's security posture and protect your valuable data.
The document explains what configurations you need to do on Scalefusion Dashboard to control accessing I/O devices on managed macOS devices.
Platforms Supported: macOS
External Storage Device Types Supported: PenDrive, Hard Disk Drive, SD Card
Pre-Requisites
Scalefusion MDM Client’s (agent app for macOS) v4.1.1 or above should be installed on device
macOS Device Profile should be created on Scalefusion Dashboard
Your account should have access to I/O Device Access Control feature
Supported OS: OS 10.15 or above
How it Works
Configure Access Policy: Set the default access level for storage devices.
Define Access Rules: Create rules specifying the storage devices to deny or allow based on the chosen criteria.
Enforcement: Scalefusion Veltar will monitor external devices connected and enforce the defined rules.
Logging: Detailed logs are recorded for devices’ access, providing valuable insights into device usage.
Steps
Step 1: Create Configuration
On Scalefusion Dashboard, navigate to Veltar > I/O Device Access Control and click on Create Configuration
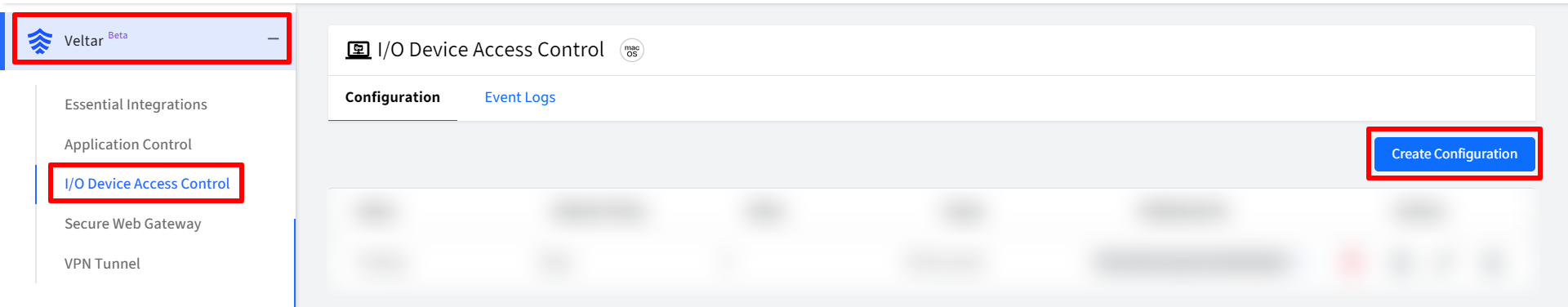
In the new window, enter Configuration Name
On the left you will find the configurable settings under these heads. Navigate to each link:
Access Policy
Settings
Access Restrictions
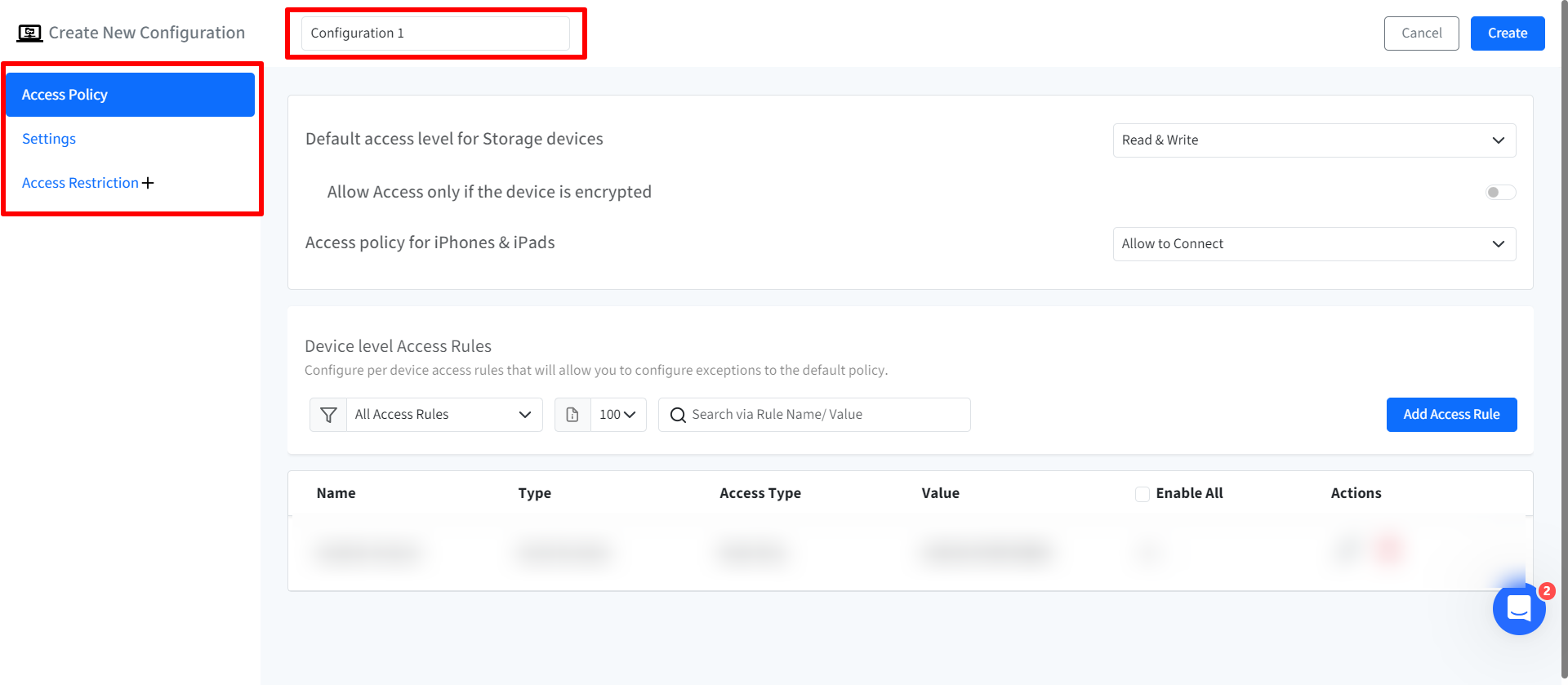
Once you have configured all the above, click on Create button on top right.
The configuration will get created and displayed under Configuration tab with other related details.
Access Policy
From this section, you can define the rules related to storage device access control. By configuring these settings, you can control the access level for storage devices, enforce encryption requirements, and manage connections from iPhones and iPads. Configuration Options:
Default Access Level for Storage Devices: Set the default access level for storage devices.
Read & Write
Read Only
Deny Access
Allow Access Only if the Device is Encrypted: Enables or disables access to storage devices unless they are encrypted. This option is configurable when the default access level is set to Read & Write or Read Only.
Access Policy for iPhones & iPads: Configure the access policy for iPhone and iPad connections to the device by choosing one of the following:
Allow to Connect
Deny Access
Device Level Access Rules: Configure specific rules for individual storage devices which will allow you to define exceptions to the default policy. To do so,
Click on Add Access Rule
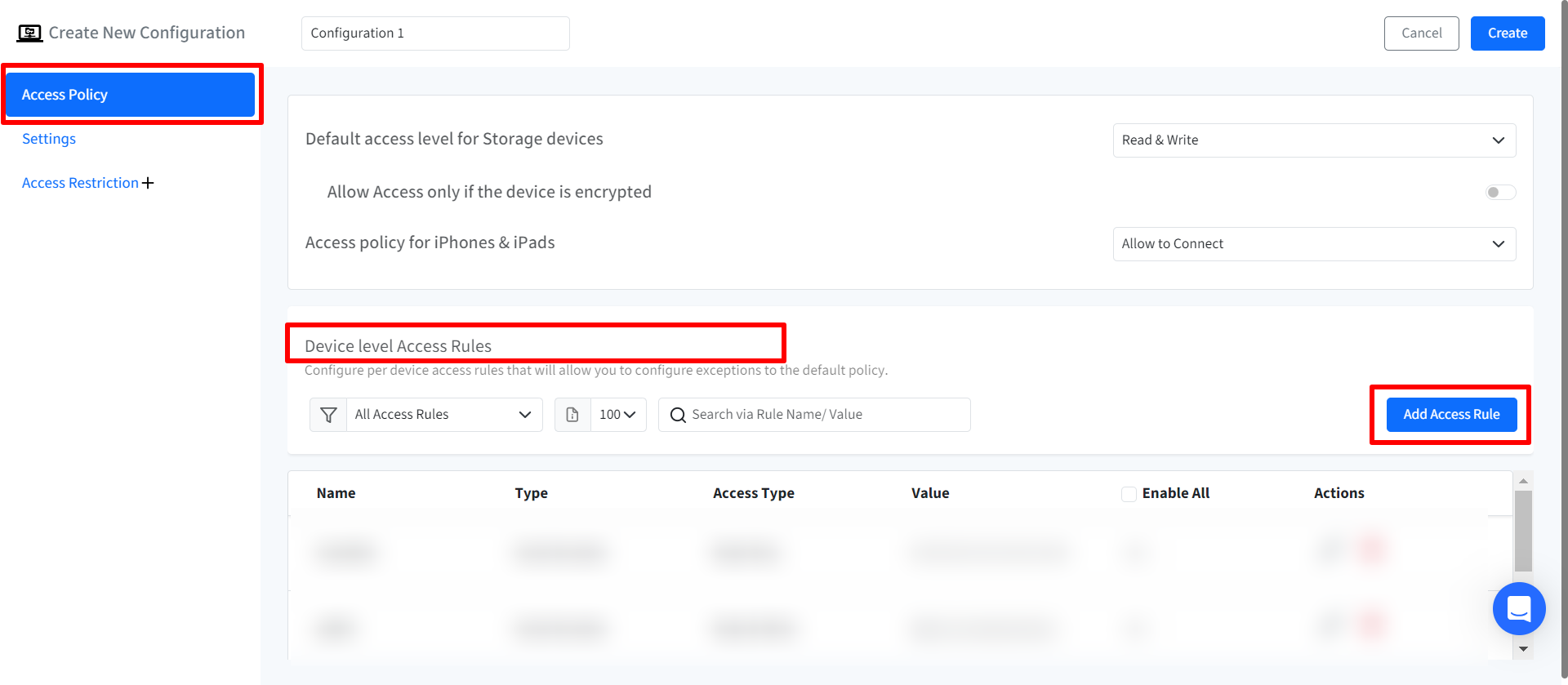
This will open the Add Access Rule wizard. Enter the following details:
Name: Set a unique name for the rule.
Type: Select the rule type which act as unique identifiers for the device. It can be based on any of the following:
Product ID
Vendor ID
Serial Number
Access Type: Configure the access type for the device.
Read & Write
Read Only
Deny Access
Encryption Status: With this, you can allow or deny the access to the storage device only if the device is encrypted.
Value: Enter the value for the selected rule type. For example, if you have selected Product ID as the Type then provide the Product ID of the storage device for which you are creating access rule.
Note: Values can be fetched from the managed device by navigating to Settings > General > About > System Report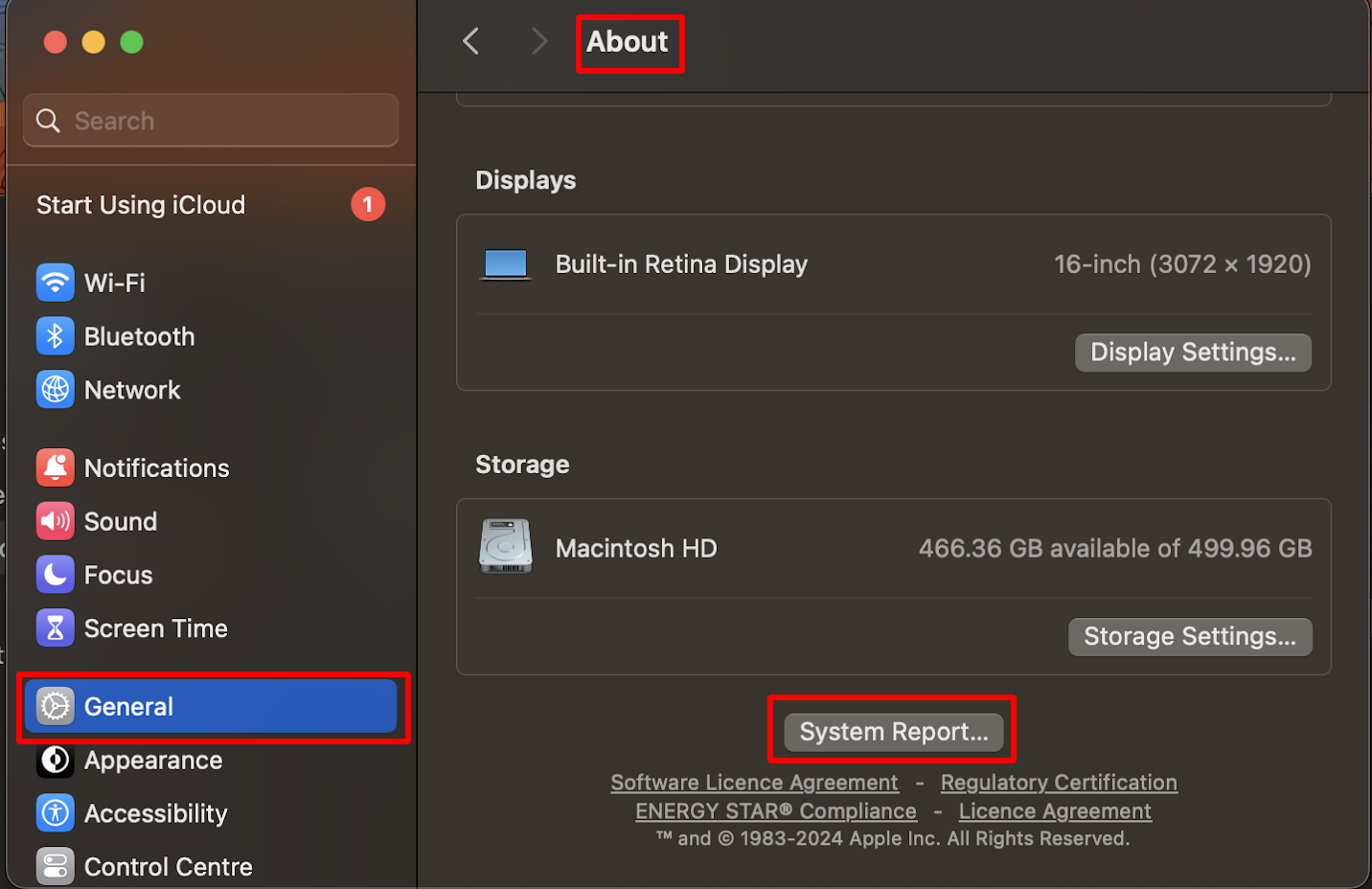
Click Save
The rule will be created and displayed.
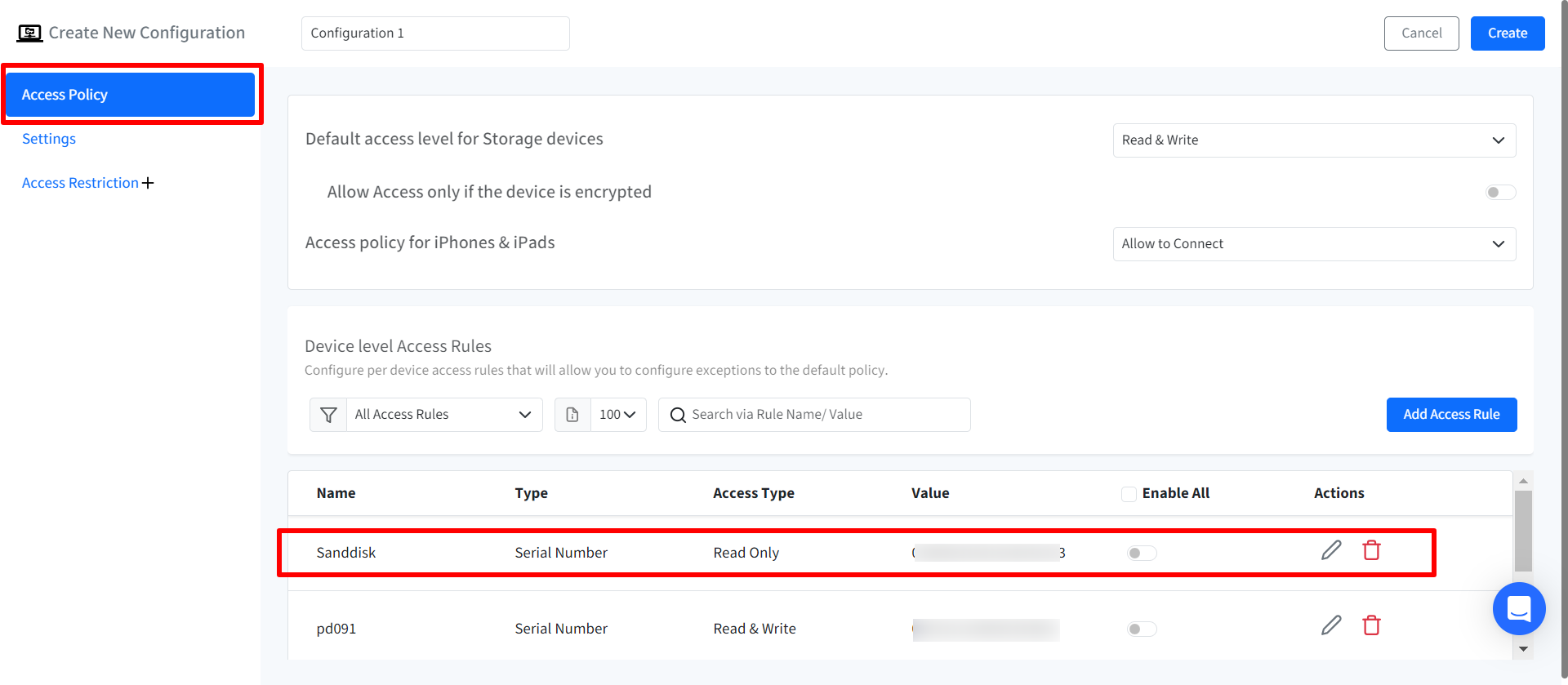
To apply a rule, you need to enable the toggle under Enable All
Settings
Configure I/O Devices’ blocking behavior through these settings:
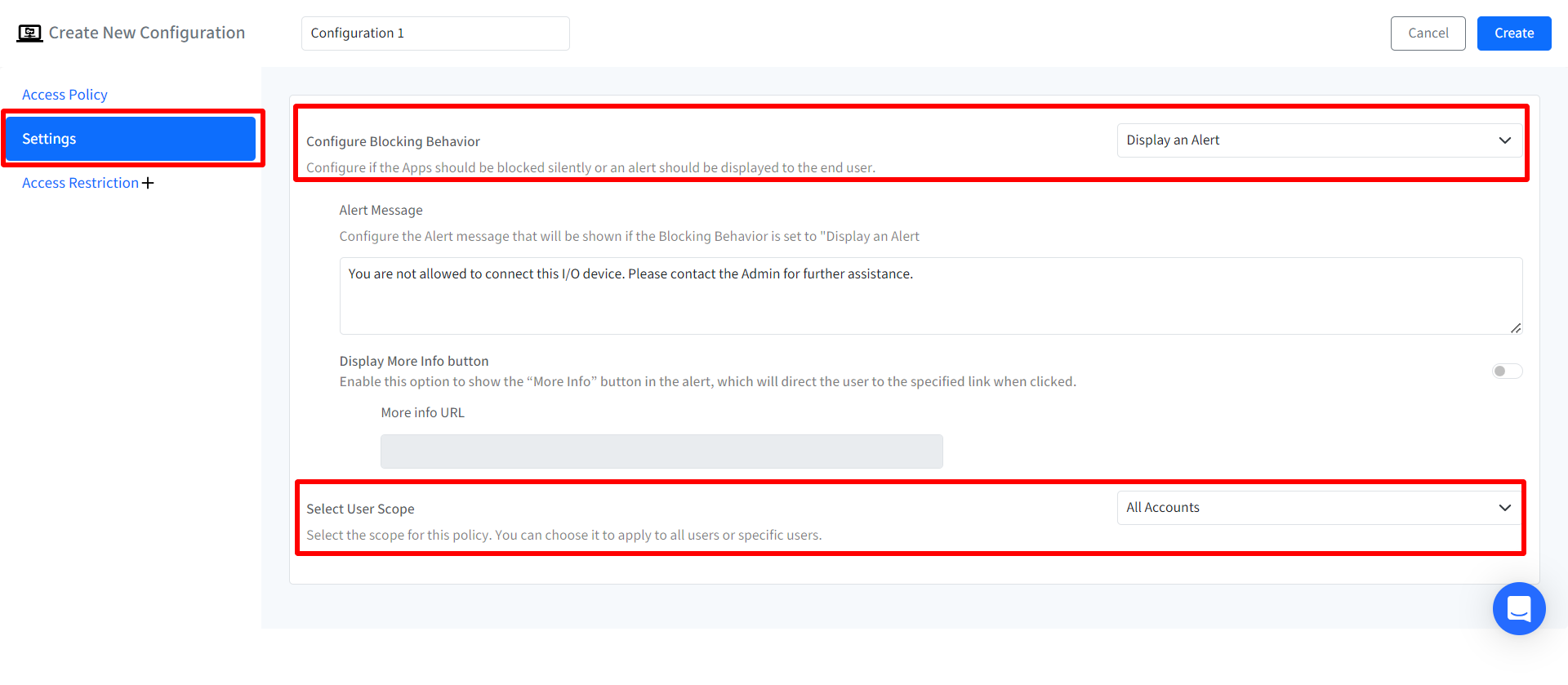
Configure Blocking Behavior: Select whether to block I/O device silently or display an alert to the end user.
Alert Message (Enabled if Blocking Behavior is set to Display an Alert): Configure the alert message that will be shown to the user when a blocked storage device is accessed.
Display More Info Button: Enables or disables the More Info button in the alert. When enabled, clicking the button will direct the user to the specified URL.
More Info URL: Enter the URL that will be displayed when the More Info button is clicked.
The alert message and Display More Info button become configurable only if the blocking behavior is set to Display an alert
Select User Scope: Select the scope for the blocking policy by choosing one of the following:
Enrolled User
All Accounts
Administrator Accounts
Standard Accounts
Specific User Accounts: On selecting this option, a text field will be displayed where you need to enter Local user short names which are present on the device. You can search for a particular user which will populate list of users created. To add more than one user, click on New User link.
Access Restrictions
IT admins can configure specific conditions from the Scalefusion Dashboard which determine the users' ability to access the I/O device. To conditionally access, following parameters can be enforced:
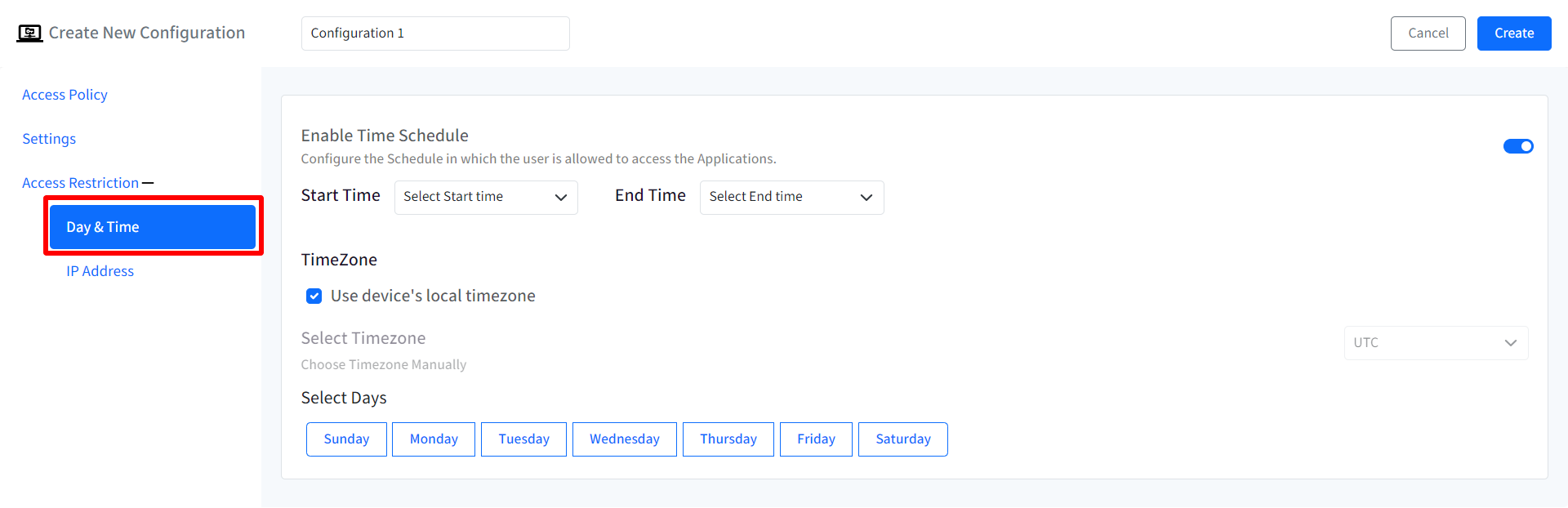
Day & Time: Configure the Time schedule in which user account is allowed to access the I/O device. Select the following:
Start Time & End Time
Timezone: You can either choose to use device's local timezone or select it manually from the drop-down.
Select Days: Select particular day(s) from Sunday to Saturday
IP Address: Enter the IP ranges and the user(s) will be allowed to access the I/O device within those specified ranges. To give range, click on Add Range link. This will add a new row below. Here, select Type from IPv4 and IPv6, give start and End IP address. The IT admins can click on the delete icon under Actions if any particular IP range has to be removed. Click on Add range to configure multiple IP ranges. Note: The IP addresses should be valid.
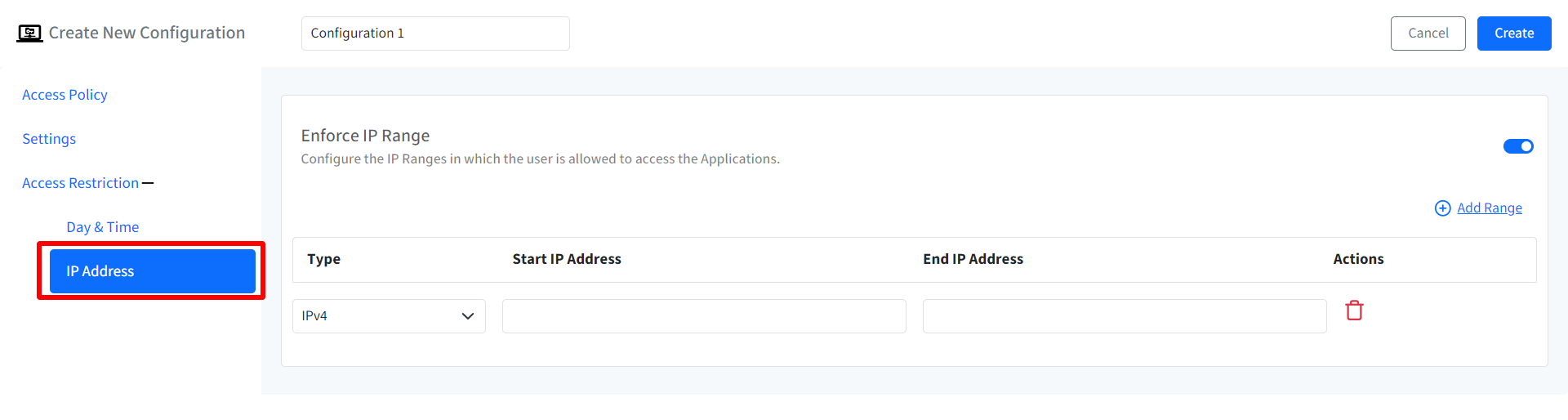
Once you have configured all the above, click on Create button on top right. The configuration will get created and displayed under Configuration tab with other related details.
Step 2: Publish Configuration
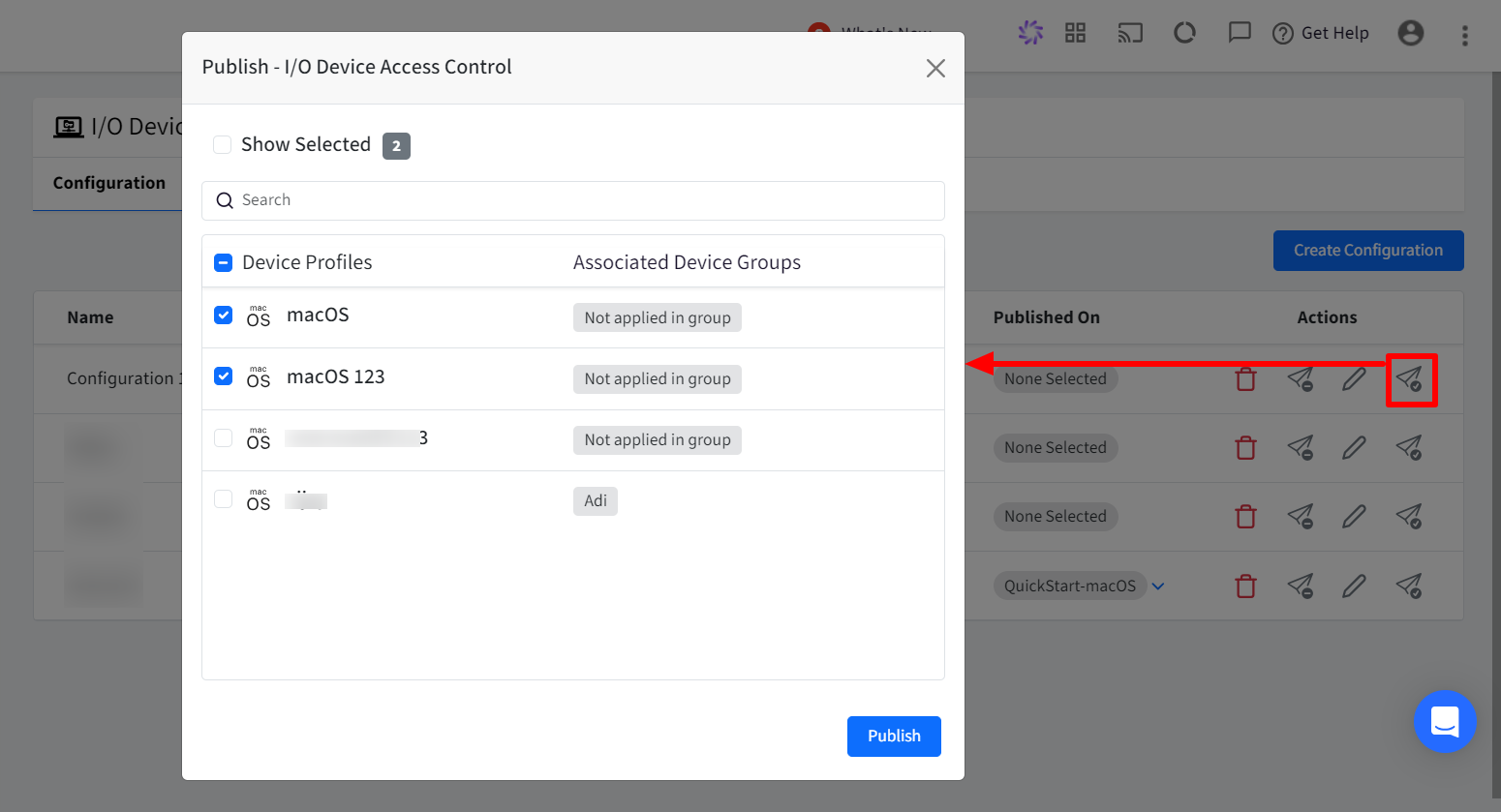
To Publish,
Click on publish icon in front of the configuration
In the new window, select the device profile(s) on which you want to publish the configuration.
Click Publish
User Experience on Device
On publishing the configuration,
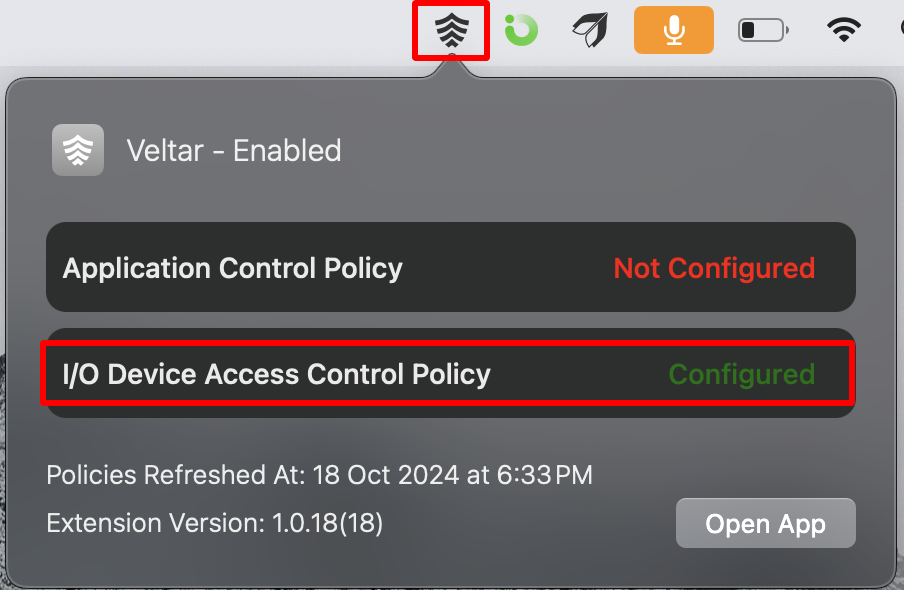
Notice Veltar icon on the top bar. Clicking on it will reflect I/O Device Access Control Policy as Configured
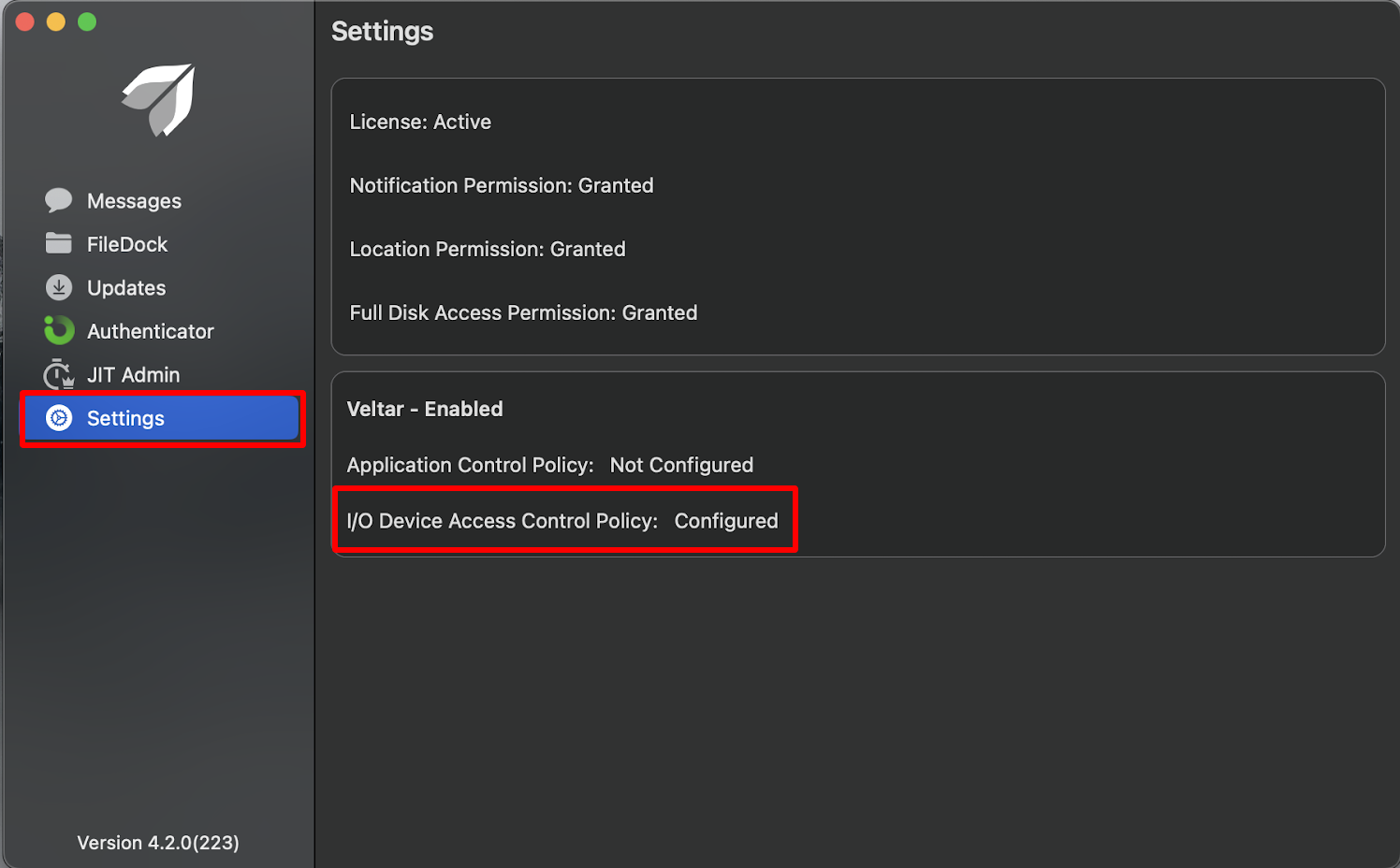
If you open Scalefusion MDM Client, it will reflect I/O Device Access Control Policy as Configured, under Settings
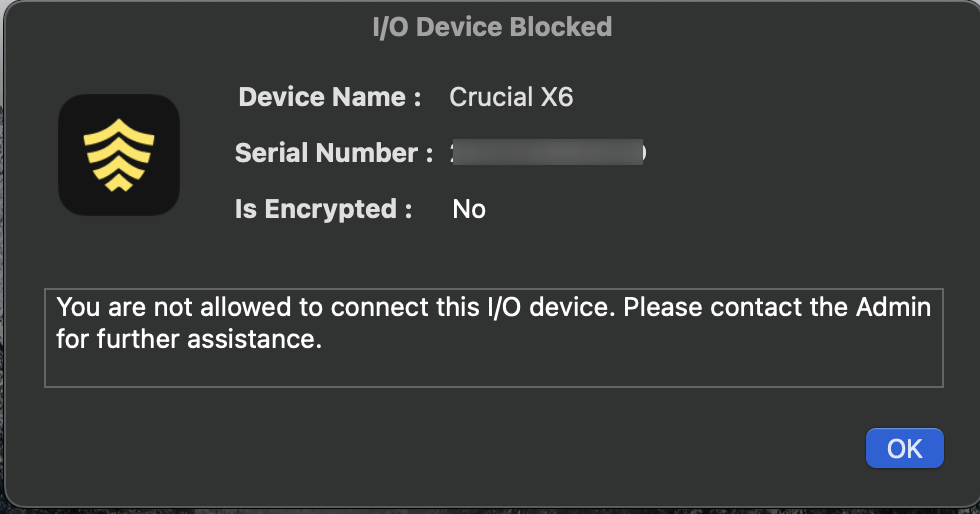
If you try to access an external storage device (for which you have created a rule in the configuration) it will show up the alert message you have configured. Below screenshot is an example when user tries to access Crucial X6, a portable solid-state drive (SSD) which has I/O Device Access Control policy applied to it and the user is denied from using the storage device.
Event Logs
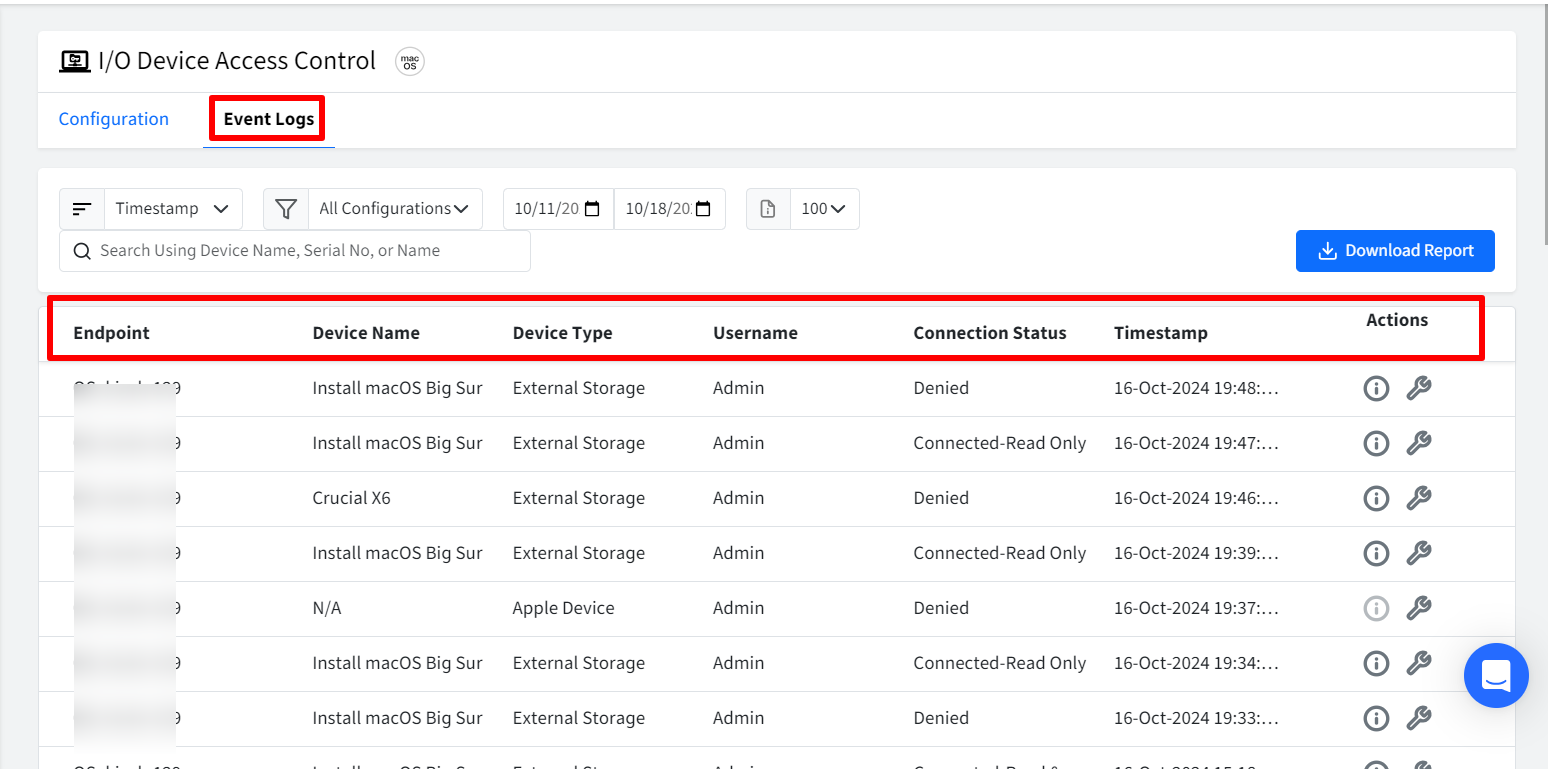
From this section you can get detailed logs which are recorded for I/O device access, providing valuable insights into device usage. Click on Event Logs tab under I/O Device Access Control
Events Info
This section shows detailed information on the events, under following heads
Endpoint: The name assigned to the macOS device.
Device Name: The name of the external storage device.
Device Type: The type of external storage device
Username: The name of the user account that accessed the storage device.
Connection Status: Connected- Read & Write, Connected - Read Only, Denied, Connected
Timestamp: Indicates when the I/O device was accessed by the user.
Actions:
View App Information: Clicking this option displays a pop-up with detailed information about the I/O device. This information helps administrators understand the context of storage device’s access and identify the specific reasons for the blocks:
Name
Product ID
Product Name
Vendor ID
Serial Number
Manufacturer
BSD Name
Bsd Path
Mount Point
File System
Is Encrypted
Is Read Only
Total Size
Available Size
Connection Status
Connection Reason
Edit Configuration: With this, you can update the configuration
Additional Features
Filters
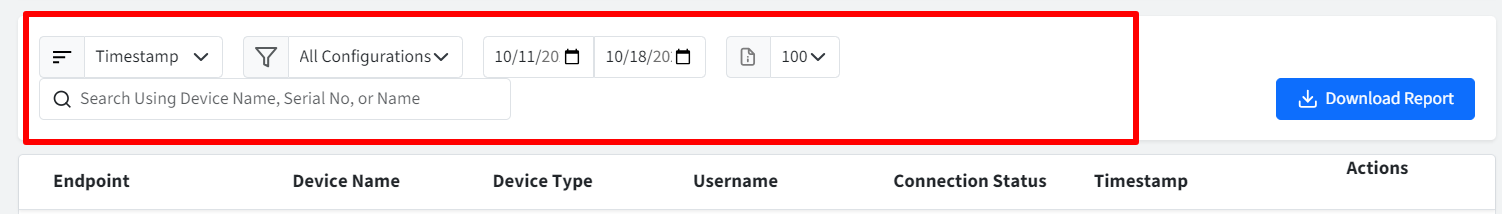
There are filtering options available for viewing activity logs. You can filter them by:
Timestamp:
Timestamp
Device Name
Username
Configurations:
All Configurations
List of available configurations. Choose a specific configuration
Date Picker:
Start Date: It can be from Current Date to 7 days. You cannot select a date more than 30 days in the past.
End Date
Note: Logs older than 30 days get automatically deleted.
Page Size: Select the number of records to be displayed on one page
Search Using Device Name, Serial No, or Name
Download Report
Clicking the button downloads a CSV report containing the filtered activity data. Please note the report can be downloaded for a duration of 7 days at the maximum.

















