- 25 Sep 2023
- 10 Minutes to read
- Print
- PDF
Intune Application Protection Policies
- Updated on 25 Sep 2023
- 10 Minutes to read
- Print
- PDF
Microsoft Intune® App Protection Policies or Data Loss prevention policies help you secure corporate data across Microsoft Office 365® apps and applications that support Intune SDK on Android & iOS devices.
Scalefusion integration with Microsoft Graph API lets IT Admins manage these policies directly from Scalefusion Dashboard, thereby removing the need to manage two consoles when using Scalefusion.
This document helps you understand how to give Scalefusion the required permissions to manage Intune protection policies and describes the various policies supported by Scalefusion.
Before you Begin
- To use Microsoft Intune® Endpoint Protection Policies, you would require one of the following licenses,
- Microsoft 365 E5
- Microsoft 365 E3
- Enterprise Mobility + Security E5
- Enterprise Mobility + Security E3
- Microsoft 365 Business Premium
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 Government G5
- Microsoft 365 Government G3
- You would need access to an Admin account that can grant Scalefusion the required permissions to create, update, & sync the policies.
- Data Loss Policies created from Scalefusion currently target only the following applications,
- Microsoft Outlook
- Microsoft OneNote
- Microsoft Excel
- Microsoft Powerpoint
- Microsoft Word
Step 1: Authorize Scalefusion to Configure Data Loss Protection Policies
The first step is to authorize Scalefusion to manage the policies on behalf of your organization. Follow the steps below to complete this part,
- To do so, you would need to Sign In to Scalefusion with an Office 365 account that has Admin privileges. If you are using a Scalefusion account, then please migrate to using Office 365 based access.
- Click on Device Profile & Policies and click on Office 365 Policies.
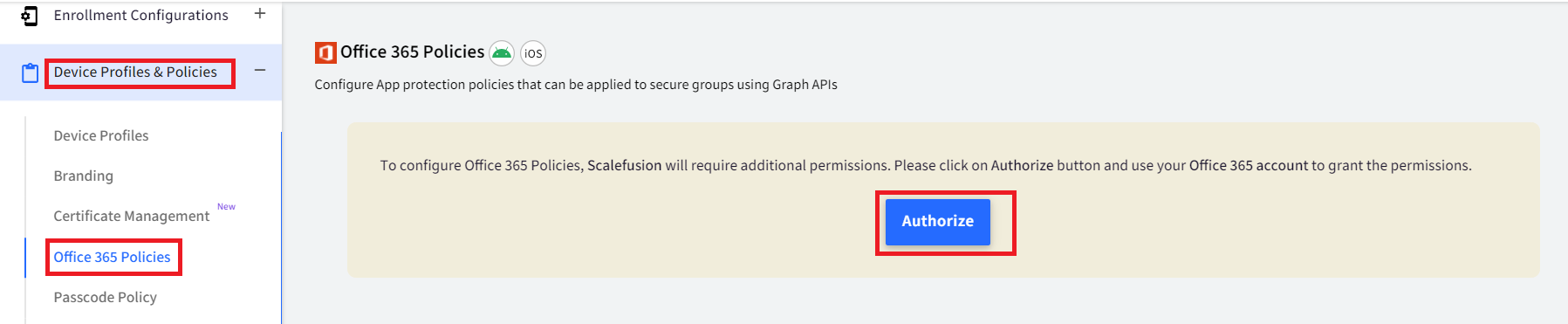
- Click AUTHORIZE in this screen and grant Scalefusion the required permissions when prompted,

- Once authorized, this section becomes the single pane of control to view & manage your Data Loss prevention policies. This screen displays all the policies currently created and other related information.
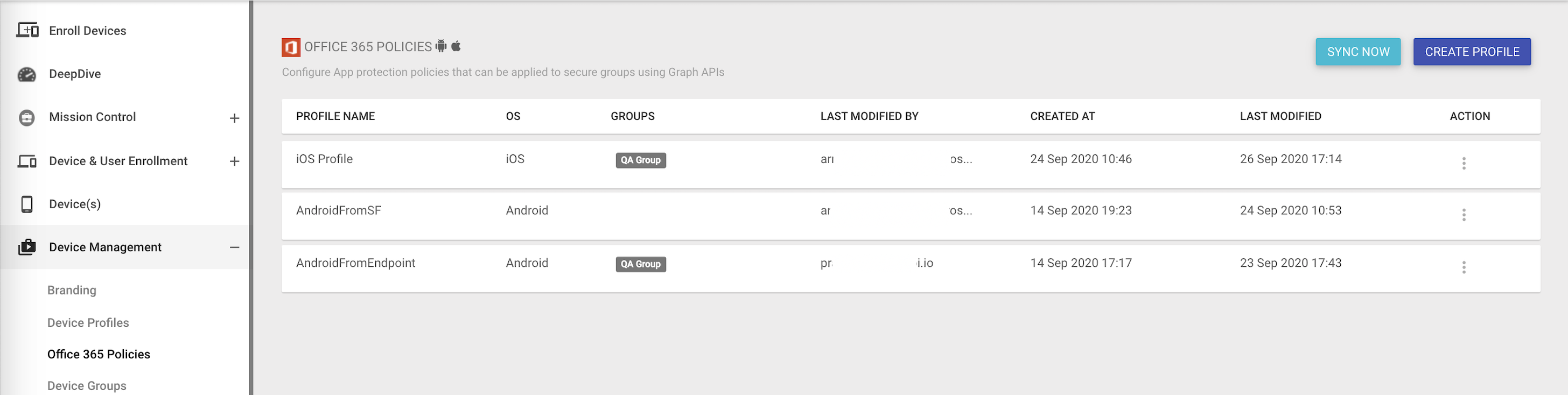
- Profile Listing View
- Profile Name: The display name of the profile/policy for your reference.
- OS: The OS that this policy is applicable to between Android & iOS.
- GROUPS: The security groups this policy is currently active on. Note that there can be multiple policies applied to the same group.
- Last Modified By: The email ID of the admin that modified this policy last.
- Created At: The date and time when this policy was first created.
- Last Modified: The date and time when this policy was last modified.
- Actions: Provides you options to Publish, Unpublish, Edit or Delete this profile.
- SYNC NOW: Allows you to sync the current policies and update the state from Microsoft Endpoint Manager.
- CREATE PROFILE: Use this option to create a profile from Scalefusion Dashboard.
- Profile Listing View
Step 2: Prepare for end-user experience on Android & iOS devices.
- On Android devices, the end users need to Sign In to Intune Company Portal app before using Microsoft Office 365 applications. So make sure that you publish the Intune Company Portal application using Scalefusion's Play for Work integration

- On iOS devices, when the user authenticates to Microsoft Office 365 applications, the system displays a popup stating that your organization manages the application. There are no additional steps in the configuration.
Step 3: Create Data Loss Prevention Profiles
Using the Scalefusion Dashboard, IT Admins can create Data Loss Prevention Policies for Android & iOS devices. For both the platforms, the application where this policy will be applied are,
- Microsoft Outlook
- Microsoft OneNote
- Microsoft Excel
- Microsoft Powerpoint
- Microsoft Word
To create a new Data Loss Prevention policy, follow the steps below,
- Navigate to Device Management > Office 365 Profiles and click CREATE PROFILE
- Provide a Name and choose the OS/Platform that this policy should target. Click SUBMIT to open the profile creation wizard.
- Data Storage & Share Settings: Use this section to define how data is stored and shared between applications. In the table below, managed applications refer to applications managed by this policy unless otherwise specified.
Data Storage & Share Settings Description Prevent Corporate Data Backup to OS-specific services Enable this to prevent users from backing up data from their managed applications to OS-specific services like iCloud or Android backup services. Data Transfer to Other Apps Configure data transfer policy for managed applications. The options are,
Allow All: Transfer data to Any App
Restricted: Transfer data to Managed Apps only
- Block All: Blocks All Data Transfer
Disallow Save As or Block storing copies of Corporate data Prevent users from saving copies of corporate data. This option can be controlled only if the data transfer to another app is selected as Restricted: Transfer data to Managed Apps only Configure Storage Locations If you have prevented saving copies of data, you can select an override to configure allowed locations, and the options are,
- OneDrive for Business
- SharePoint
- Local Storage
Receive Data From Other Apps Configure if managed applications can receive data from other apps using the share menu options in other apps. The options are,
- Allow All: Receive data from Any App
- Restricted: Receive data from Managed Apps only
- Block All: Blocks All Data Transfer
Restrict Cut Copy Paste with Other Apps Configure the clipboard settings for the managed applications.
- Any App: Allow to cut, copy, and paste data between their managed applications and any application.
- Apps Managed by Policy: Allow cut, copy, and paste data between managed Microsoft Intune App Protection Policies applications.
- Policy Managed Apps with Paste in: Allow cut and copy data from another app. However, it blocks users from sharing content outwardly unless sharing with a managed app.
- Blocked - Prevents users from cutting, copying, and pasting data between managed applications and all applications.
Force Links in Managed Apps to open in Managed Browser Forces link in managed applications to open in a managed browser like Microsoft Edge. Encrypt Managed App Data Encrypts data pertaining to managed applications when this option is selected. The system encrypts data stored anywhere, including external storage drives and SIM cards. Disable Printing From Managed Apps Prevents printing documents and data from managed applications. Disable Contact Syncing to the Native Contact book Prevents managed applications from saving contacts to the native address book by hiding the Sync Contacts option. - Access Settings: Use this section to define the access rules for your managed applications.
Access Settings Description Require PIN for Access Requires users to enter a PIN to access managed applications. Users create the PIN during the initial setup of the application. Once enabled, you can configure the following sub-settings, Select PIN Type Choose between Numeric or Alphanumeric & Symbols Select Minimum PIN Length Configure a minimum length for the PIN that the user needs to set. Force Reser PIN Duration Enable this to reset the PIN after the selected number of days. Maximum Invalid PIN Attempts Configure the maximum invalid PIN attempts before the managed app access is restricted, and the user is forced to create a new PIN. Disable App PIN even if Device PIN exists Enable this if the PIN shouldn't be used if there is a device-level PIN set. Block Fingerprint/Touch ID access to apps Choose if users are allowed to use Fingerprint instead of PIN on Android 6.0+ devices. Block Simple PIN Prevent users from setting simple patterns for their PINs. Enforce Corporate Credentials For Access Sets the system to validate the access PIN, fingerprint, or credential information when the access session reaches one of the time intervals. - Timeout - The number of minutes the access sessions for managed applications are idle.
- Offline Grace Period - The number of minutes devices with managed applications are offline.
Enforce Access Requirements Configure how often the access requirements should be enforced. The options are, - Idle Timeout Minutes: The user will be asked for a PIN after the device is idle for the selected time.
- Offline Grace Period Minutes: Users will be given a grace period if they are offline before enforcing access requirements.
Wipe Managed App data if Idle for (days) Sets the system to remove managed application data from devices when devices are offline for a set number of days. - Android Settings: Define additional settings for your Android devices. These options are visible only if you are creating/editing an Android profile.
Android Settings Description Block Screen Capture and Android Assistant Enable this to block screenshots of the managed applications and prevent Android Assistant App scanning. Minimum Android OS version Required Enter the required minimum Android OS version number that a user device must have to access the managed app. Enter the required minimum Android OS version number that a user device must have to access the managed app. Minimum Android Patch version Required Enter the minimum Android security patch level that a user device must have to access the managed app. Minimum App version required Enter the required minimum App version number that a user must have to get access to the app. - iOS Settings: Use this section to define settings specific to iOS devices. These options are visible only if you are creating/editing an iOS profile.
iOS Settings Description Block Face ID access to apps (iOS 11+) Enable this to prevent Face ID access to managed applications or disable this to enforce the PIN requirement. Minimum iOS version required Enter the required minimum iOS version number that a user device will have to access the application. Minimum App version required Enter the required minimum app version number that a user device must be having to access the application. Minimum App protection policy SDK version required Enter the minimum Intune Application Protection Policy SDK version that the managed applications should have to get access to the application. - Once you have configured the profile, click on the SAVE button to save the profile.
.png)
Step 4: Managing & Deploying Data Loss Preventions Profiles
Once you have created the DLP policies for Android and/or iOS, you can manage them by choosing to publish, unpublish, edit or delete them.
Scalefusion syncs the state of policies with Microsoft Endpoint Manager every time you open this page, but if you want to force a sync, then you can use the SYNC NOW button.
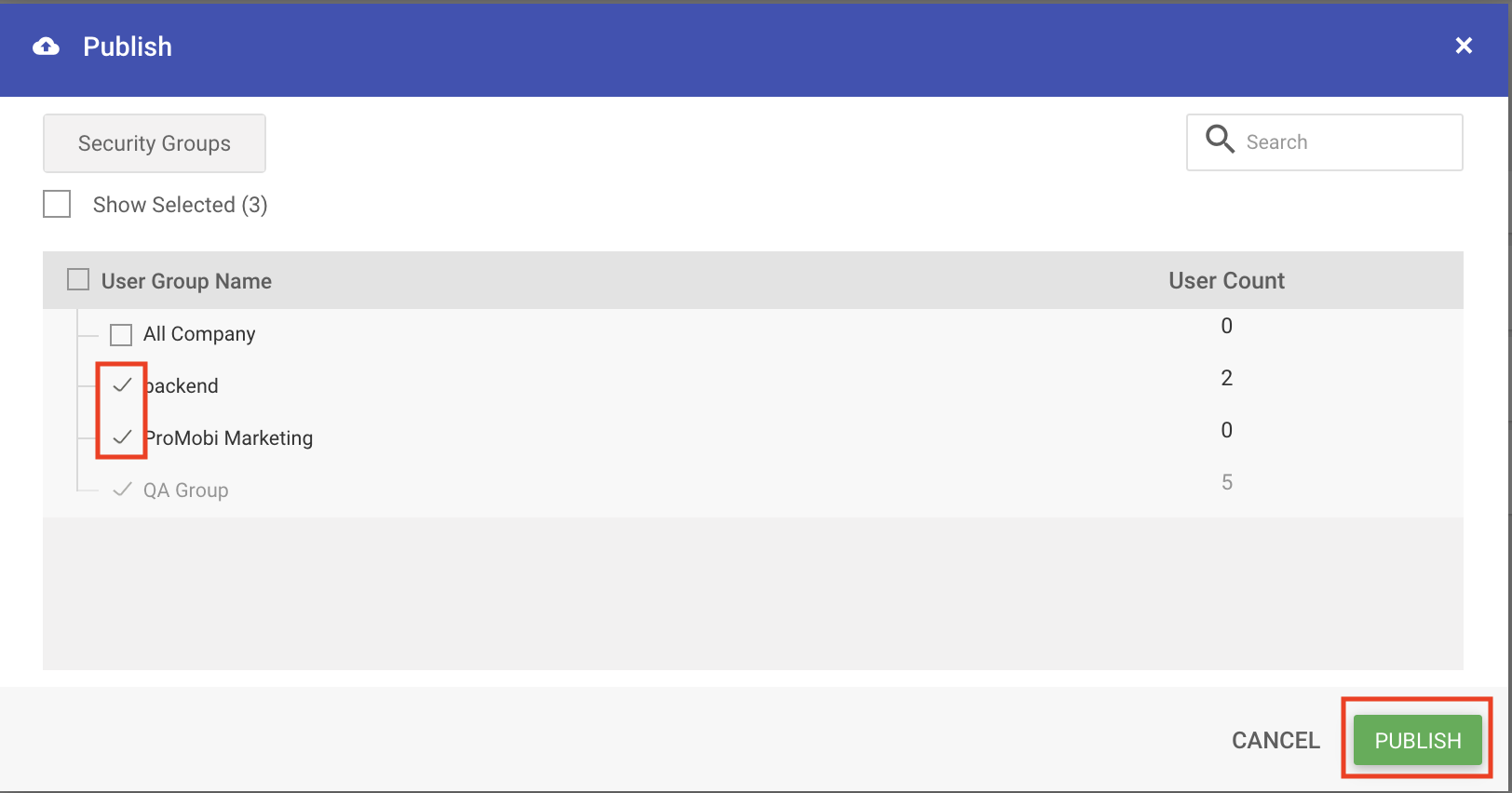
Publish a Profile
Use this option to apply/publish a set of policies to one or multiple security groups in your organization.
- Click on 3 dots in the Actions column and select Publish

- Select the groups where you want to publish this policy and click PUBLISH.
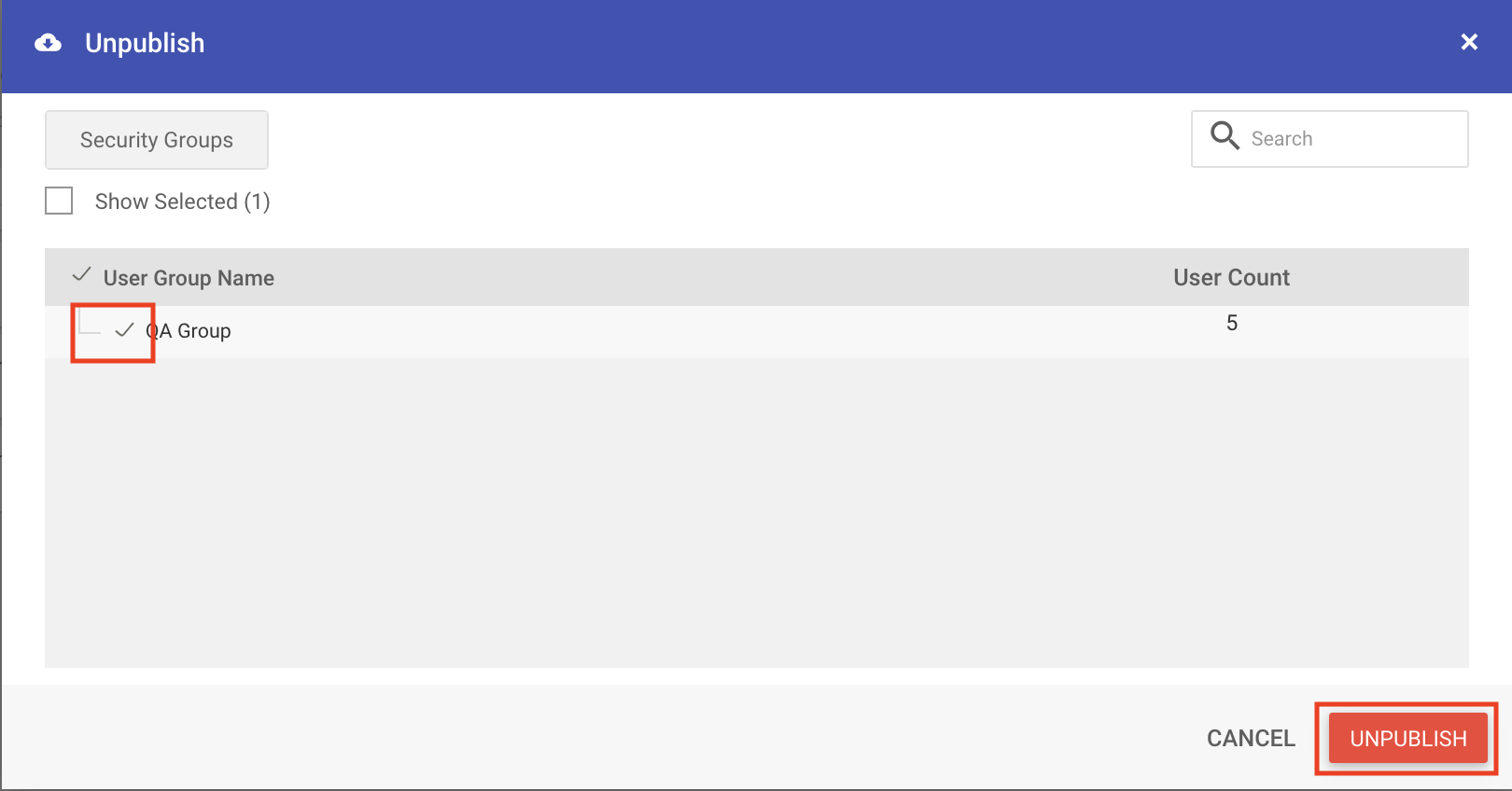
UnPublish a Profile
Use this option to remove the applied policies from one or multiple security groups in your organization.
- Click on 3 dots in the Actions column and select UnPublish

- Select the groups from where you want to remove the policy and click UNPUBLISH.Only the groups where this policy has been published will be listed in the unpublish dialog.
Editing a Policy
Use this option to make changes to an existing policy. Note that any changes to the policy will automatically be applied to the groups where this policy has been applied.
Deleting a Policy
Use this option to delete a profile completely. Note that this action will remove the data loss prevention policies governed by this profile on the devices. To delete a profile, select the Delete option from the actions menu and confirm the action.
Frequently Asked Questions
Question: How much time does it take for the new policies or changes in policies to take effect?
Answer: As per the documentation, users who are already signed in to the apps won't see the changes in the policy for an eight-hour period. On Android, using the Intune Company Portal and syncing the policies makes the policies to be re-synced. On iOS, when the app is restarted or the device reboots, it looks like the policies seem to take effect.
Question: We have applied the policies, and they work on iOS devices but not on Android.
Answer: Make sure that you have published the Intune Company portal app to your Android devices and that the user is signed in to the IDP app using the corporate credentials.
Question: What do we do if a particular policy does not seem to work?
Answer: In the case of Office 365 policies, Scalefusion simply acts as a bridge, helping you easily manage DLP policies from a single Dashboard. Please note that the actual behavior is dependent on the target application, and you would have to reach out to Microsoft Intune/Endpoint Manager support.
Question: We see that Profiles created from Scalefusion are applied to only a select few application targets. However, we would like to add other Intune SDK-supported applications as targets.
Answer: If you have an application that integrates with Intune SDK and supports Data Loss Prevention policies, do get in touch with our support, and we can add support for the target application.


