- 22 Oct 2024
- 3 Minutes to read
- Print
- PDF
Configure Password Policy for Windows Devices
- Updated on 22 Oct 2024
- 3 Minutes to read
- Print
- PDF
Securing enterprise Windows 10 & above devices is a very important aspect of managing them. A quality password acts as first line of defense in protection against unattended access and stolen/lost devices.
Scalefusion helps you define a password policy, that can be applied to the devices thereby forcing the users to create a password that complies with your organizational policies. In this document, we will walkthrough on how to configure and publish a Password policy.
Before you Begin
- Login into Scalefusion Dashboard
- Have access to one Scalefusion managed Windows 10 & above devices.
Password Policy
Creating a Password Policy
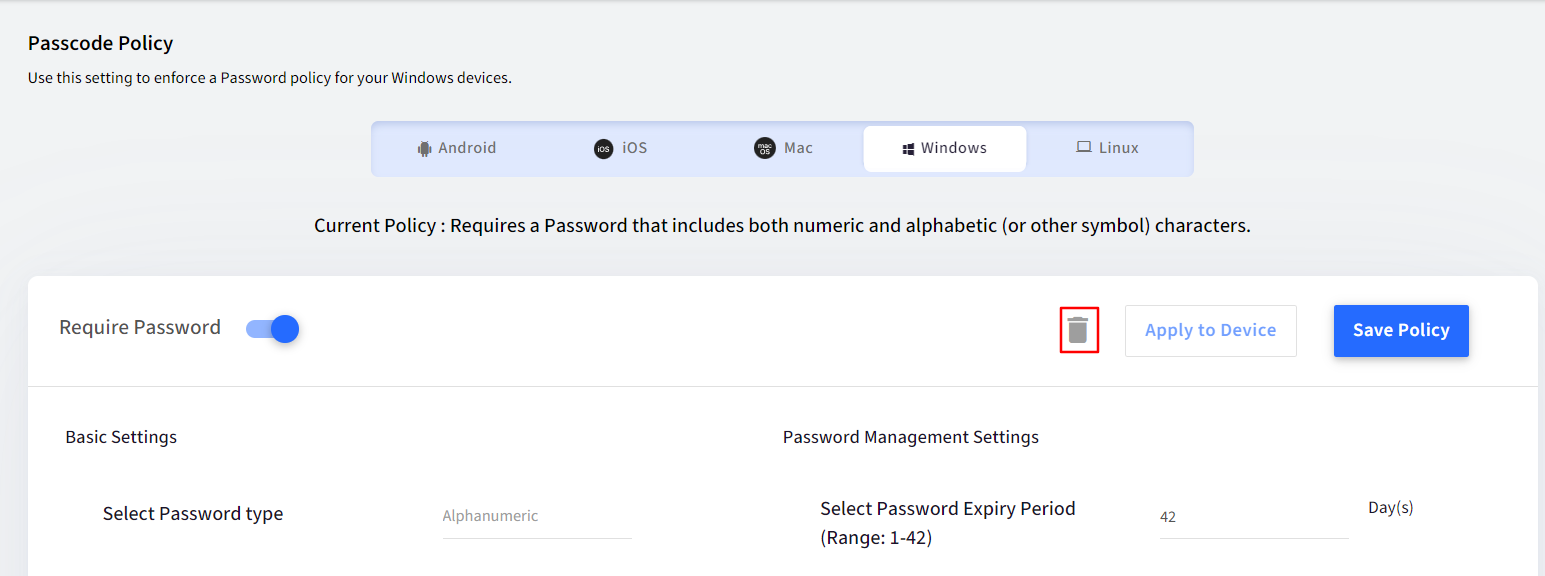
- Navigate to Device Profiles & Policies > Passcode Policy > Windows section.
- Toggle on the Require Password setting.
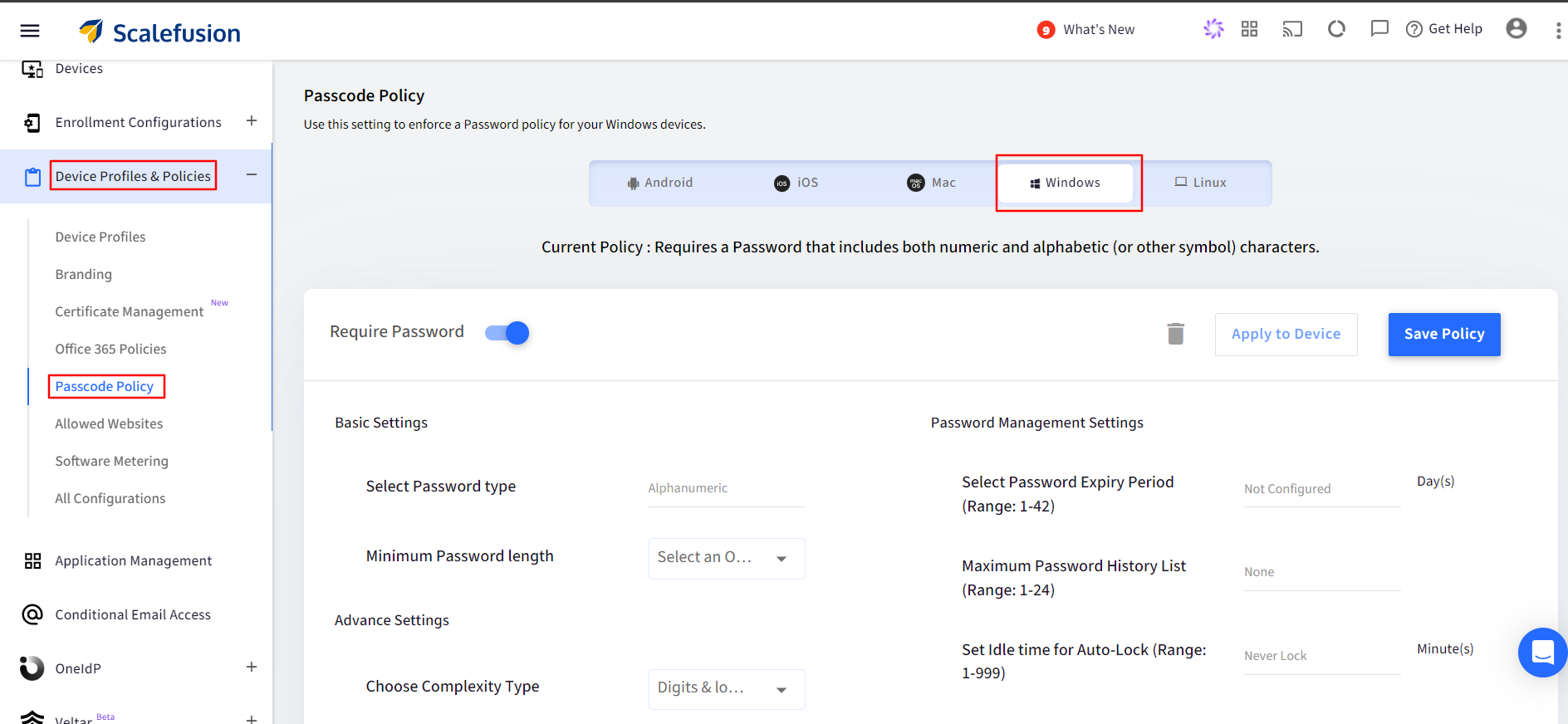
- Following are the options for Password complexity for Windows devices,
Setting
Description
Known Behavior
Require Password
Enable this setting if you want to enforce a password.
Select Password Type
Currently the only type supported is Alphanumeric.
Minimum Password Length
Select a minimum password length that is enforced.
- Accepted values are between 6 to 16
Choose Complexity Type
Select if you want the password to contain Digits or Digits & lower case letter.
Windows Enterprise enforces Digits & lower-case letters in password irrespective of the selection.
Select Password Expiry (in days)
Select an optimal period after which the password should expire, and user is enforced to set a password. You can set it between the range 1-42 days. The default will be Not Configured.
The maximum you can keep the password for is 42 days as Microsoft does not allow to keep same password for more than 42 days.
This field cannot be left blank.
Maximum Password History List
Choose an optimal value on how often user can repeat the passwords once they expire. You can choose between the range 1-42 days. You can set it between the range 1-24. The default will be None.
Set Idle Time for Auto Lock (in minutes)
Select an idle timeout after which the screen is auto locked. You can set it between the range 1-999 minutes. The default will be Never Lock.
Configure max attempts to enforce BitLocker recovery mode/Restart
Select an optimal value after which the device will either enter into BitLocker recovery mode or will start. You can set is between the range 4-999. The default will be Never.
- If the device BitLocker encrypted and user(s) enter wrong password multiple times, after the max set value, the device will boot into BitLocker recovery screen.
- If the device is not BitLocker encrypted and user(s) enter wrong password multiple times, after the max set value, the device will boot into the login screen.
- Once you have configured the desired policy, click Save Policy. 
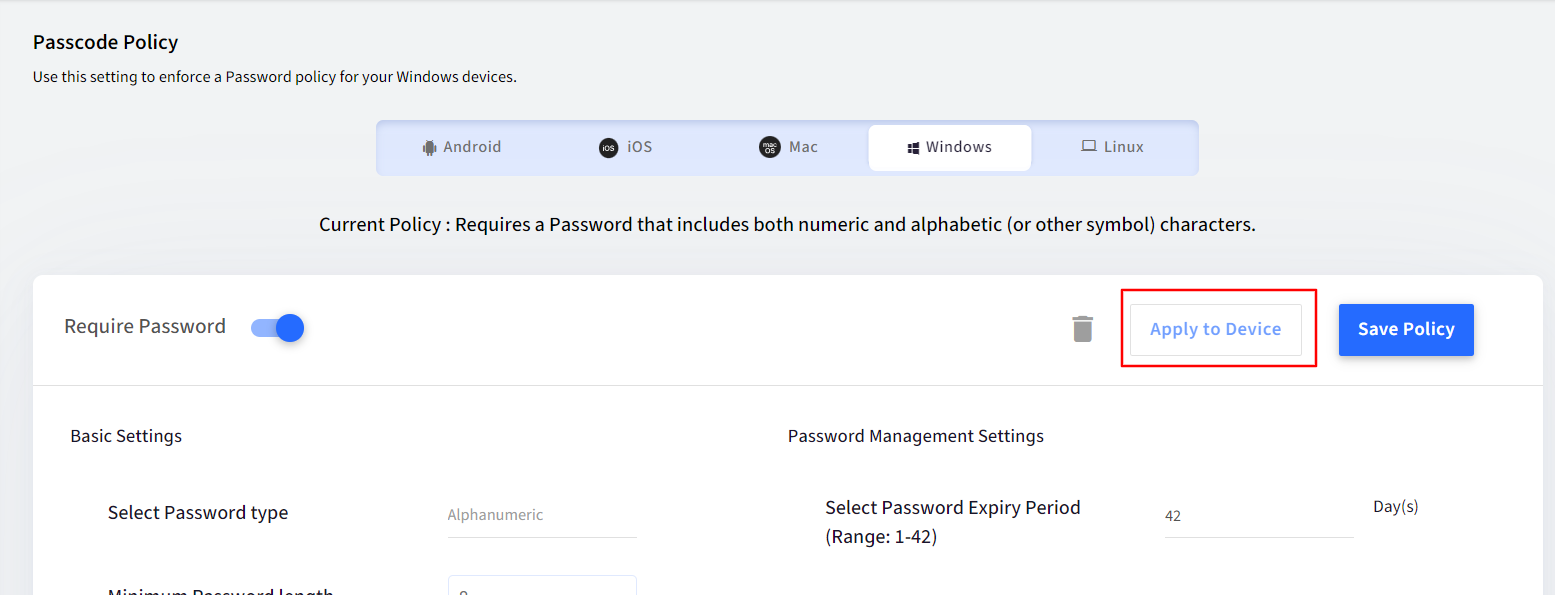
Publishing a Password Policy
- Once you have created a password policy, you can publish it to the Device Profiles. To do so, navigate to Device Profiles & Policies > Passcode Policy. Under Windows tab, click on Apply to Device.
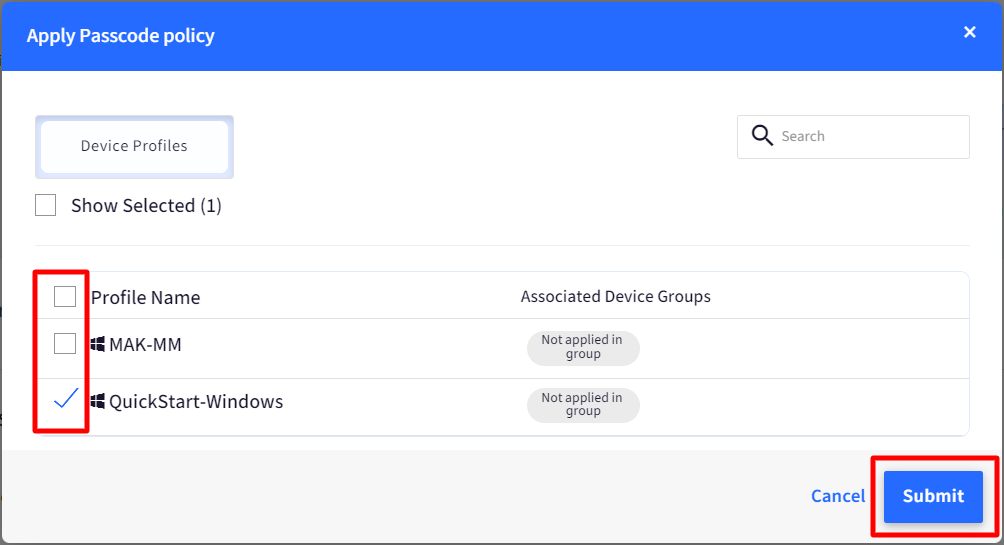
- Select the Device Profile(s) where you want to apply the policy to and click on SUBMIT.
- Once the policy is applied and the devices sync with the Scalefusion dashboard, they will be forced to change the password the next time the device reboots or they Login to their account on device.It is observed that irrespective of the current password on the device, users are forced to create a new password, even if the complexity is less.
Removing a Password Policy
- If you want to relax the password policy and want to remove a password policy from devices, then navigate to Device Profiles & Policies > Passcode Policy and click on Delete icon.
- Select the Device Profile(s) where you want to remove the policy from and click SUBMIT.
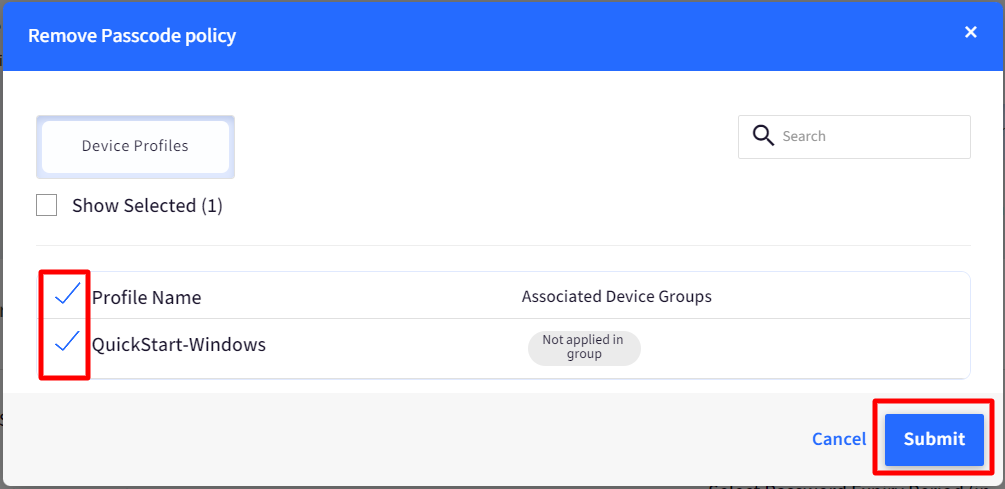
- Once you remove a password policy from a device profile, following are the actions taken,
- All the future devices that enroll into the device profile will not be enforced to create a password.
- For the current devices in the profile, however, the password that is already configured is not removed.







