CrowdStrike is widely adopted by enterprises and organizations globally as a critical component of their cybersecurity strategy, offering a modern and effective approach to protecting endpoints from an ever-evolving threat landscape.
Recognizing the importance of seamless integration, Scalefusion provides comprehensive guidance for IT Admins in configuring Crowdstrike Falcon on their managed Mac devices. This article offers step-by-step instructions to configure Crowdstrike within their Mac environments.
Step 1: Publishing the Custom Payload.
Step 2: Installing the software using the script.
Step 1: Publishing the custom Payload.
The following Payload is designed to enforce specific security and system settings related to CrowdStrike Falcon on managed macOS devices. It includes configurations for web content filtering, system extension control, privacy preferences, system extensions, and the installation of the CrowdStrike license.
Please publish the custom payload before publishing the script.
Copy the contents below directly and add them to Apple Configurations > Custom Configurations for Mac, or click here to download the file and import it.
Follow our guide on how to add the Custom Payload in the Apple Configurations & deploy it to devices.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>FilterBrowsers</key> <false/> <key>FilterDataProviderBundleIdentifier</key> <string>com.crowdstrike.falcon.Agent</string> <key>FilterDataProviderDesignatedRequirement</key> <string>identifier "com.crowdstrike.falcon.Agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] and certificate leaf[field.1.2.840.113635.100.6.1.13] and certificate leaf[subject.OU] = "X9E956P446"</string> <key>FilterGrade</key> <string>inspector</string> <key>FilterPacketProviderBundleIdentifier</key> <string>com.crowdstrike.falcon.Agent</string> <key>FilterPacketProviderDesignatedRequirement</key> <string>identifier "com.crowdstrike.falcon.Agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] and certificate leaf[field.1.2.840.113635.100.6.1.13] and certificate leaf[subject.OU] = "X9E956P446"</string> <key>FilterPackets</key> <false/> <key>FilterSockets</key> <true/> <key>FilterType</key> <string>Plugin</string> <key>Organization</key> <string>CrowdStrike Inc.</string> <key>PayloadDisplayName</key> <string>Web Content Filter</string> <key>PayloadIdentifier</key> <string>com.apple.webcontent-filter.2C5CBFD0-7CFE-41CB-95BC-A681F4D293B8</string> <key>PayloadType</key> <string>com.apple.webcontent-filter</string> <key>PayloadUUID</key> <string>2C5CBFD0-7CFE-41CB-95BC-A681F4D293B8</string> <key>PayloadVersion</key> <integer>1</integer> <key>PluginBundleID</key> <string>com.crowdstrike.falcon.App</string> <key>UserDefinedName</key> <string>Falcon</string> </dict> <dict> <key>AllowedTeamIdentifiers</key> <array> <string>X9E956P446</string> </array> <key>PayloadDescription</key> <string>Controls the system extension loading/unloading</string> <key>PayloadDisplayName</key> <string>App System Extension Control</string> <key>PayloadIdentifier</key> <string>com.apple.system-extensions.admin.E45B5986-74A6-4B6A-A4CA-E179516A7F52</string> <key>PayloadOrganization</key> <string>CrowdStrike Inc.</string> <key>PayloadType</key> <string>com.apple.system-extensions.admin</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>E45B5986-74A6-4B6A-A4CA-E179516A7F52</string> </dict> <dict> <key>PayloadDescription</key> <string>Configures Privacy Preferences Policy Control settings</string> <key>PayloadDisplayName</key> <string>Privacy Preferences</string> <key>PayloadIdentifier</key> <string>com.apple.TCC.configuration-profile-policy.9A10BE5D-5E46-4C22-89C9-20597A04B616</string> <key>PayloadOrganization</key> <string>CrowdStrike Inc.</string> <key>PayloadType</key> <string>com.apple.TCC.configuration-profile-policy</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>9A10BE5D-5E46-4C22-89C9-20597A04B616</string> <key>Services</key> <dict> <key>SystemPolicyAllFiles</key> <array> <dict> <key>Allowed</key> <true/> <key>CodeRequirement</key> <string>identifier "com.crowdstrike.falcon.Agent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string> <key>Comment</key> <string></string> <key>Identifier</key> <string>com.crowdstrike.falcon.Agent</string> <key>IdentifierType</key> <string>bundleID</string> <key>StaticCode</key> <false/> </dict> <dict> <key>Allowed</key> <true/> <key>CodeRequirement</key> <string>identifier "com.crowdstrike.falcon.App" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = X9E956P446</string> <key>Comment</key> <string></string> <key>Identifier</key> <string>com.crowdstrike.falcon.App</string> <key>IdentifierType</key> <string>bundleID</string> <key>StaticCode</key> <false/> </dict> </array> </dict> </dict> <dict> <key>AllowUserOverrides</key> <true/> <key>AllowedSystemExtensionTypes</key> <dict> <key>X9E956P446</key> <array> <string>EndpointSecurityExtension</string> <string>NetworkExtension</string> </array> </dict> <key>AllowedSystemExtensions</key> <dict> <key>X9E956P446</key> <array> <string>com.crowdstrike.falcon.Agent</string> </array> </dict> <key>PayloadDescription</key> <string>Configures System Extensions Policy settings</string> <key>PayloadDisplayName</key> <string>System Extensions</string> <key>PayloadIdentifier</key> <string>com.apple.system-extension-policy.20258B06-5866-4424-8893-A3AF1AFAAEDC</string> <key>PayloadOrganization</key> <string>CrowdStrike Inc.</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadType</key> <string>com.apple.system-extension-policy</string> <key>PayloadUUID</key> <string>20258B06-5866-4424-8893-A3AF1AFAAEDC</string> </dict> <dict> <key>PayloadDisplayName</key> <string>CrowdStrike License</string> <key>PayloadIdentifier</key> <string>com.crowdstrike.falcon.F7004E33-A620-4741-BF0D-50DB5F39F4B7</string> <key>PayloadType</key> <string>com.crowdstrike.falcon</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>F7004E33-A620-4741-BF0D-50DB5F39F4B7</string> <key>PayloadVersion</key> <integer>1</integer> <key>ccid</key> <string>PUT YOUR LICENSE HERE</string> </dict> </array> <key>PayloadDescription</key> <string>System Extensions, and Privacy Preferences</string> <key>PayloadDisplayName</key> <string>Falcon Profile</string> <key>PayloadEnabled</key> <true/> <key>PayloadIdentifier</key> <string>C1A6E28A-21EF-49C6-B85F-84E845731E22</string> <key>PayloadOrganization</key> <string>CrowdStrike Inc.</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadScope</key> <string>System</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>183F63FC-A94F-44F6-AF62-D3D68FDAE755</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>In this Payload, please search and replace “PUT YOUR LICENSE HERE” with the License key from your Crowdstrike portal.
On the device, you should see the following custom payload in the Profiles section in System Preferences.
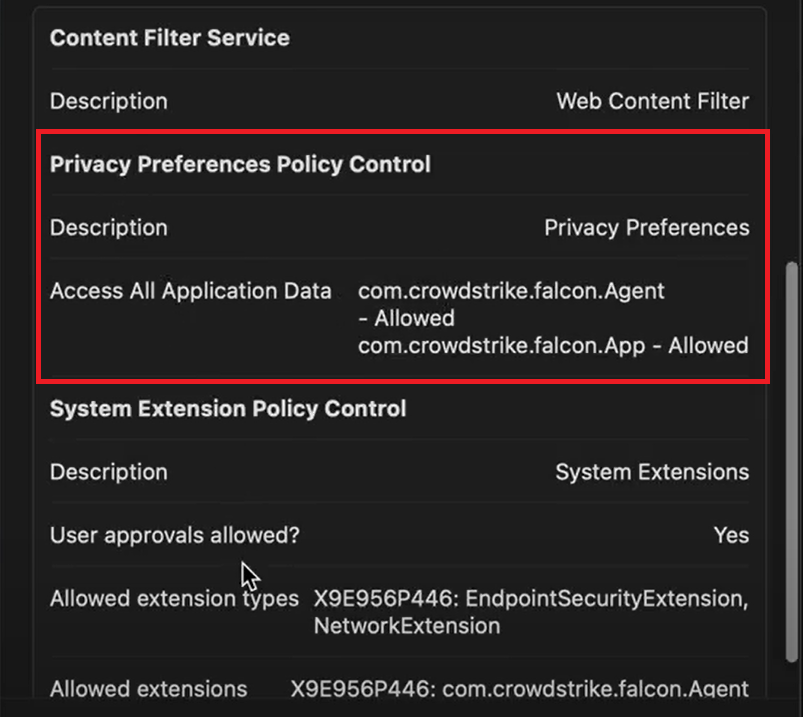
Notes:
The Payload and its contents are sourced from various albeit authenticated Apple Developer communities and forums.
Please validate them on a test machine before deploying them on all your managed devices.
Scalefusion has tested these Payloads, however, Scalefusion will not be responsible for any loss of data or system malfunction that may arise due to the incorrect usage of these payloads.
Step 2: Installing the software using the script.
Create a file on your desktop, for example, DownloadAndInstallCrowdStrike.sh, and open it in a text editor like Notepad++
Copy the contents below to the file or click here to download the file.
#!/bin/bash #Create variable with download url of the installer DownloadUrl="ENTER_DOWNLOAD_URL" #Create variable with app name AppName='Falcon' #License Key LicenseKey="ENTER_LICENSE_KEY" #Write content of variable to console output echo "App Name: $AppName" echo "Testing to ensure App is not already installed" #Create variable with results of search in Application folder for $AppName ExistingSearch=$(find "/Applications/" -name "$AppName") #If variable is not null (If search found the app in the application folder) if [[ -n "$ExistingSearch" ]] then echo "$AppName already present in /Applications folder, exiting." exit 1 else # Runs if app name wasn't found in application folder echo "$AppName not present in /Applications folder, installing" # Check if the CrowdStrike profile is present echo "checking to see if the CrowdStrike profile is present" # variable containing the installed profiles on the device ProfileSearch=$(profiles list -output stdout-xml) # Team identifier of CrowdStrike ProfileCompare="X9E956P446" # If statement that checks whether or not the CrowdStrike profile is installed if [[ $ProfileSearch = *"$ProfileCompare"* ]] then echo "The CrowdStrike profile is present, installing CrowdStrike Falcon" # Install CrowdStrike #download installer from S3 bucket and output it to /tmp folder curl "$DownloadUrl" --output /private/tmp/FalconSensorMacOS.pkg #Run the installer installer -verboseR -package /private/tmp/FalconSensorMacOS.pkg -target / # Activate Falcon with our license echo "Licensing app..." /Applications/Falcon.app/Contents/Resources/falconctl license "$LicenseKey" echo "Install finished, deleting install files..." #delete left over installation files no longer needed rm /private/tmp/FalconSensorMacOS.pkg echo "The following files were deleted: /private/tmp/FalconSensorMacOS.pkg" echo "displaying agents stats: (if blank agent isn't running)" /Applications/Falcon.app/Contents/Resources/falconctl stats agent_info else echo "The CrowdStrike profile is NOT present, CrowdStrike Falcon will NOT be installed." fi fiIn the script, set the values for the following properties:
DownloadUrl: You can upload the Crowdstrike Falcon app to the Scalefusion dashboard and copy the download URL from there.
You will find the Crowdstrike Falcon app on your Crowdstrike portal.
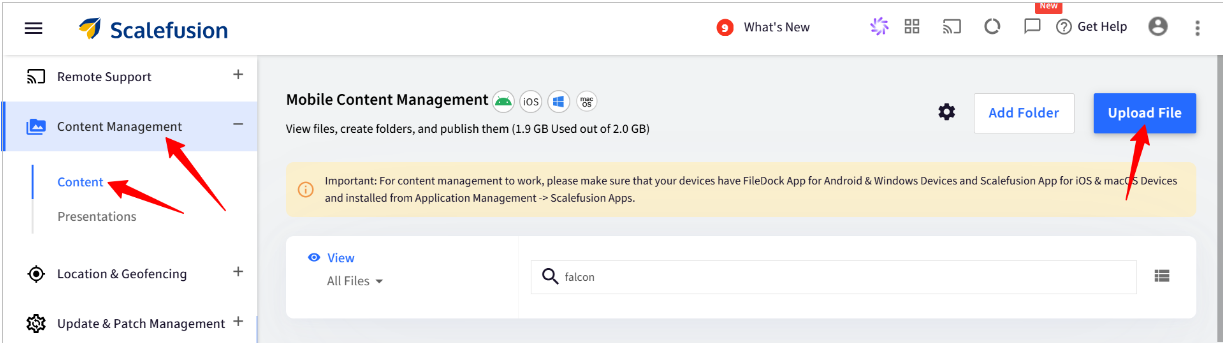
Once you have the app, Navigate to the Content Management section on the Scalefusion dashboard > Content > Upload a File > Upload the Falcon app file.
Once uploaded, select the file > Click on the 3 dots option > Click on the copy Download link.
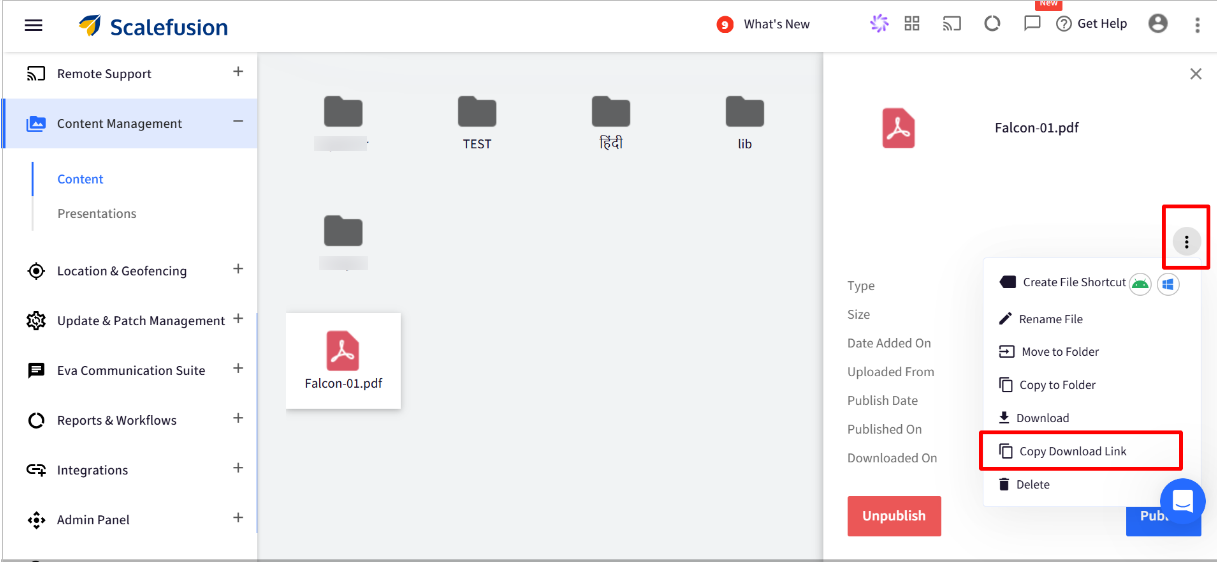
Paste this link in the script above.
AppName: Will be Falcon.
LicenseKey: You will get the license key from your Crowdstrike portal.
Once the above values are added, upload the script into the Enterprise store and set “Run Script as signed-in user” to NO.
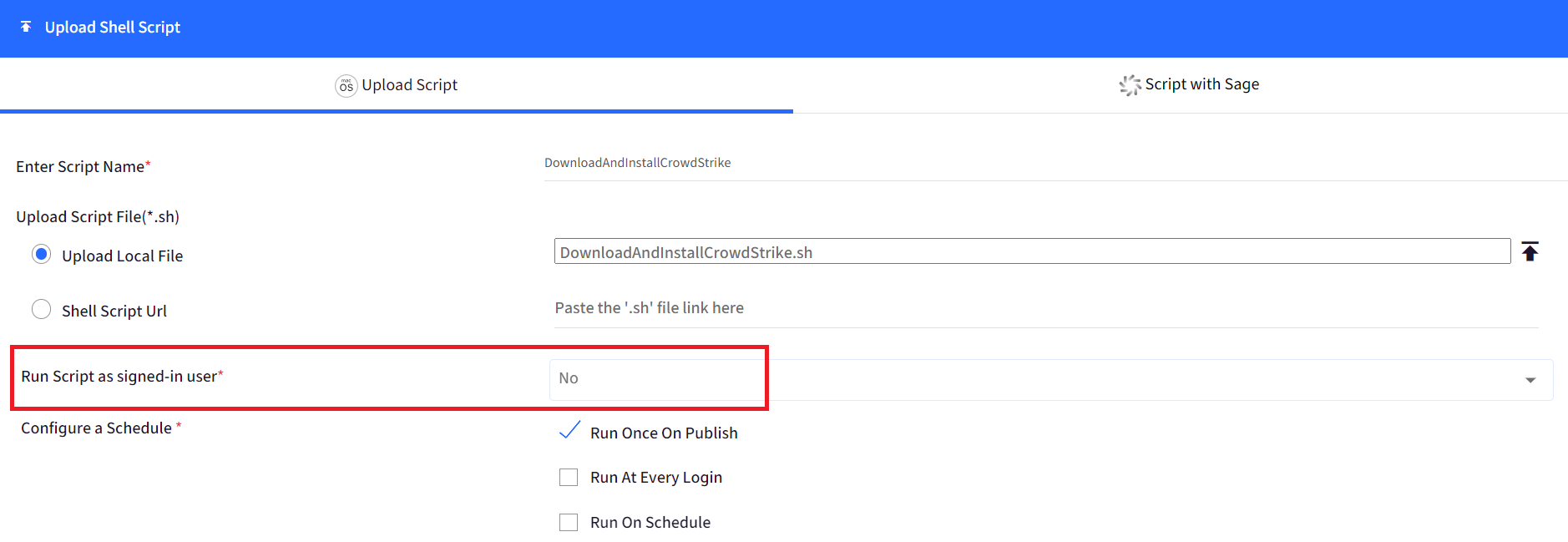
Follow our guide to upload & publish the Shell script using Scalefusion Dashboard.
Please note that to use the Shell scripts, the Scalefusion MDM Client Application must be installed on the device(s). Please follow our guide to publish and install the Scalefusion MDM Agent Application.
Notes:
The scripts and their contents are sourced from various albeit authenticated Apple Developer communities and forums.
Please validate the scripts on a test machine before deploying them on all your managed devices.
Scalefusion has tested these scripts, however, Scalefusion will not be responsible for any loss of data or system malfunction that may arise due to the incorrect usage of these scripts.