Keycard plugin provides capability to configure settings with which you can control users' access to devices where users can be Identity Providers or otherwise. This article explains the settings.
- In Keycard configuration window, navigate to Keycard Settings on the left panel.
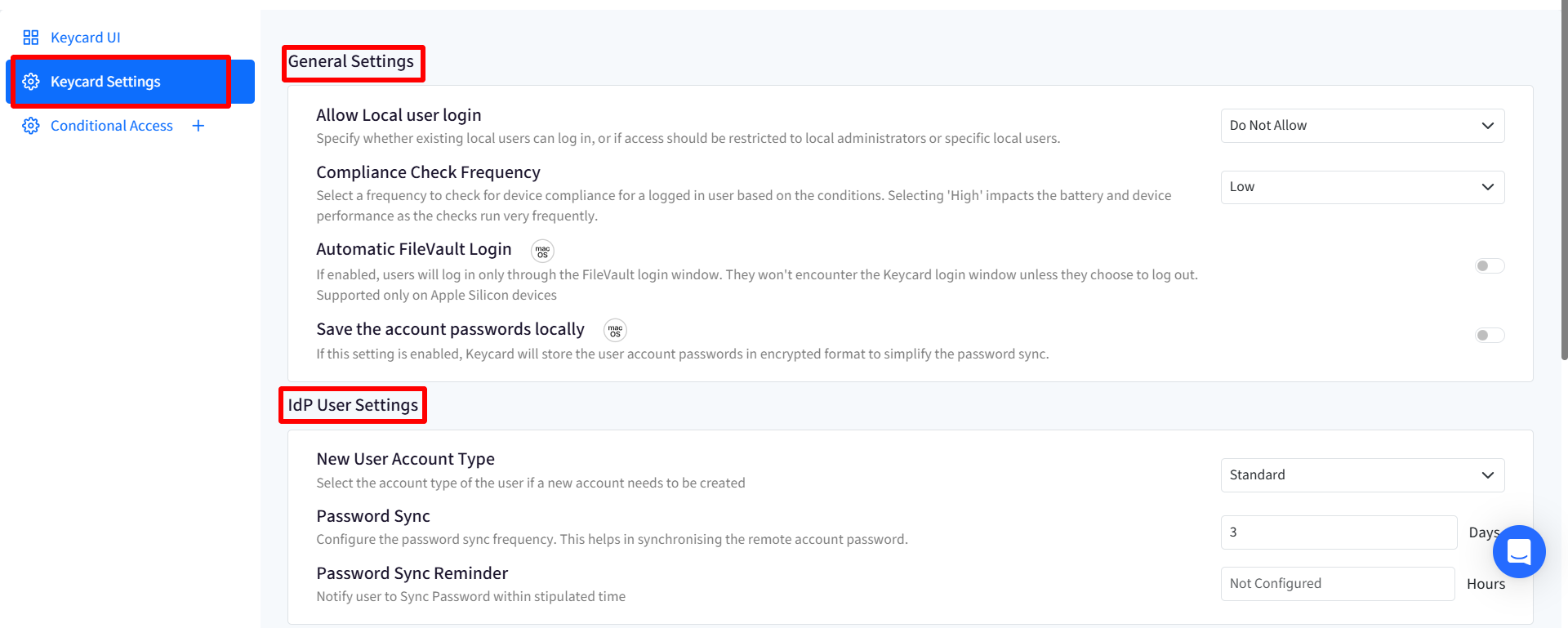
General Settings
- Allow Local User Login: Select an option to specify which Local users will display on the lock screen whether existing local users can log in, or if access should be restricted to local administrators or specific local users. Choose one from the following options in drop-down:

- Do not allow: No local users will be displayed on lock screen. This option will be visible if you are an IdP user.
- Enrolled User: Only the enrolled user will be displayed on the lock screen.
- All Accounts (default): All the user accounts will be displayed on the lock screen.
- Administrator Accounts: The Administrator type of users will be displayed on lock screen.
- Specify User Accounts: Specify the user accounts which will be displayed on lock screen. On selecting this option, a grid will be displayed where you need to enter Local user short names which have been previously configured, from the Device details > User Accounts section on Scalefusion Dashboard. You can search for a particular user which will populate list of users created. To add more than one user, click on New User link. If users are not configured (do not exist in UAM section), they can be configured from this section. Custom properties are also supported for configuring local users.

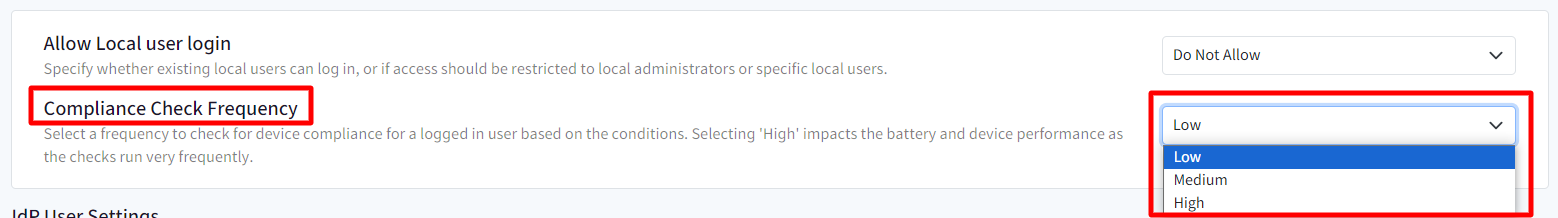
- Compliance Check Frequency: Select a frequency to check whether the device is compliant with the conditions specified under Conditional Accessfor logged in user accounts. The frequency can be selected from one of the following:
- High: The compliance check is performed every 5 minutes. Selecting 'High' impacts the battery and device performance as the checks run very frequently.
- Medium: The compliance check is performed every 30 minutes.
- Low: The compliance check is performed every 60 minutes.
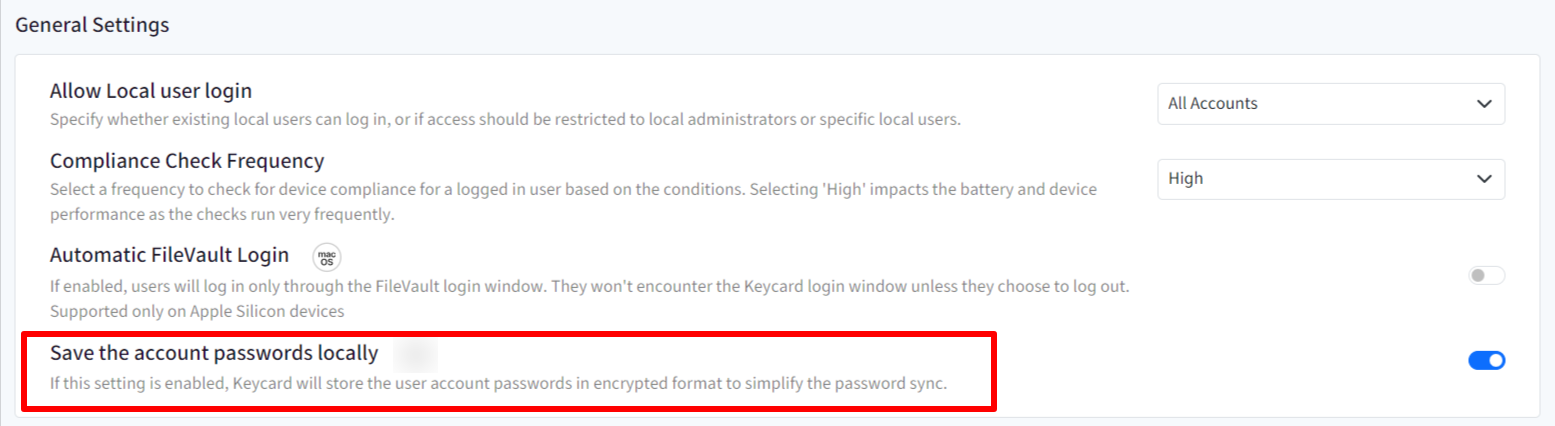
- Save the account passwords locally: If this is enabled, the keycard will securely store the user's account password. As a result, during subsequent password sync operations, the system will validate whether the stored password matches the remote account password. If a password mismatch is detected, it will automatically get updated.
How User settings work on device
Taking an example, if you have allowed local user login for All accounts, and pushed the configuration, then on the device you will get a list of all the users existing on Scalefusion Dashboard. Select one and enter password to login to the machine.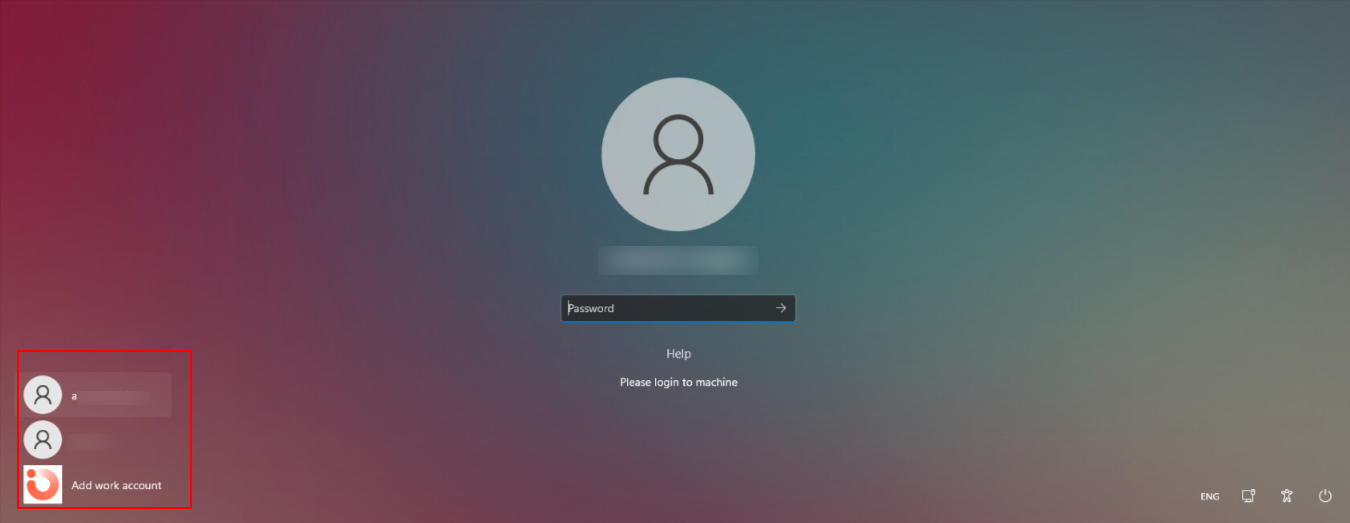
IdP User Settings
These settings are configurable if one of the following conditions are met:
- The account with which you have logged in on Scalefusion Dashboard, is an IdP account (Google Workspace / Microsoft Entra/ OneIdP / Okta / PingOne / OnPrem AD) For OnPrem AD, the OPC setup should be done on Scalefusion Dashboard
- You have created a Directory in OneIdP (with custom and/or default domain)
- Also, the users should be existing under User Enrollment section on Scalefusion Dashboard.
- For identity providers other than oneidp, following settings should be enabled on Scalefusion Dashboard:
- Under User Enrollment > Enrollment & sync settings, the setting Enforce users to sign in using <Identity Provider name> should be enabled
- If User group settings are configured and admin wants to override global enrollment settings, the setting Override Global settings should be enabled with Enforce users to sign in using <Identity Provider name> selected.
Here are the settings:
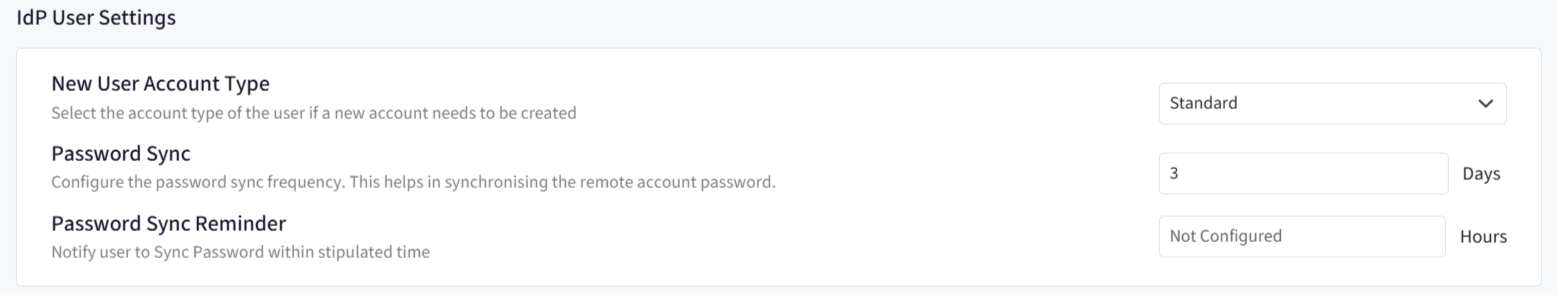
- New User Account Type: For a new user account created on the device, you can select the new user's account type whether it will be Standard or Administrator. The user should be existing in the User Enrollment section on Scalefusion Dashboard.
- Password Sync: Configure the frequency for synchronizing remote account password. It may happen that IT admin sets/resets the password for an IdP user account, remotely. This password has to be synced with the device and you can select the frequency (in days) at which synchronizing with the device takes place. By default frequency is set to 3 days. It can be selected anywhere between 1 to 30 days.
- Password Sync Reminder: This will notify user to complete sync password activity. Specify a time limit (in hours) and user will be notified to sync password within that timeframe. Reminder time can be set anywhere from 0 to 72 hours. Also, the users will not get logged off to perform the online login, the reminder window is shown to them to complete login.
 If Password policy is set by admin, the remote account password should adhere to the Password policy rules.If the IdP password does not match the password policies configured then the user is alerted to change their IdP password.
If Password policy is set by admin, the remote account password should adhere to the Password policy rules.If the IdP password does not match the password policies configured then the user is alerted to change their IdP password.
How IdP user settings work on the device
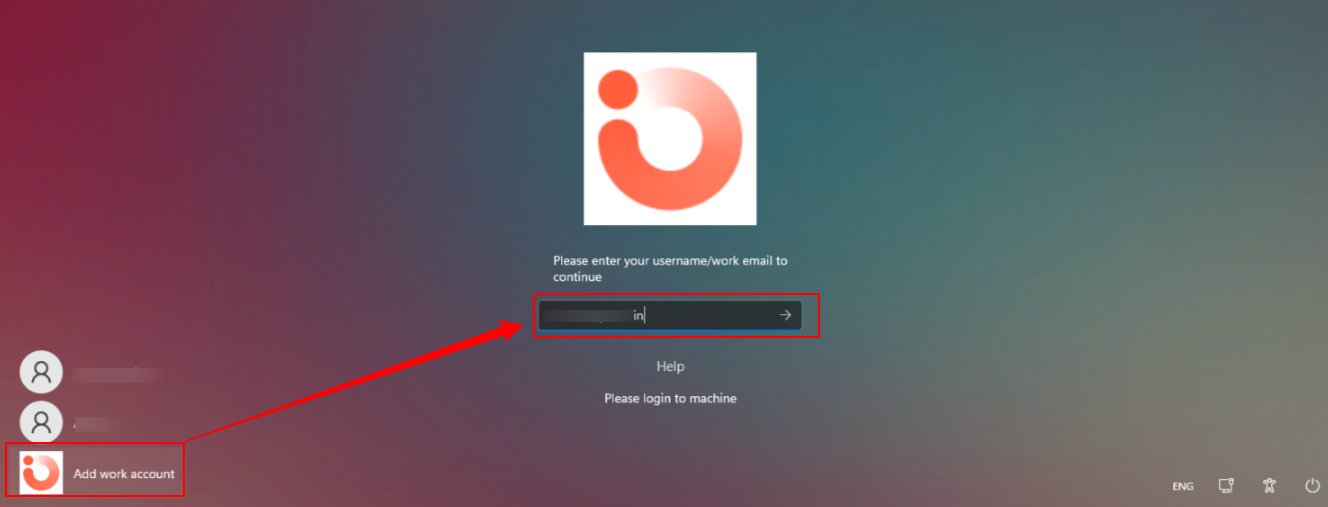
When you push Keycard configuration on the device with IdP user settings configured, an additional link Add work account is created on the device, on the login screen. Click on it and enter your account credentials to authenticate.
- Taking an example of a domain configured in O365 account, click on Add work account and enter your email address on the login screen.
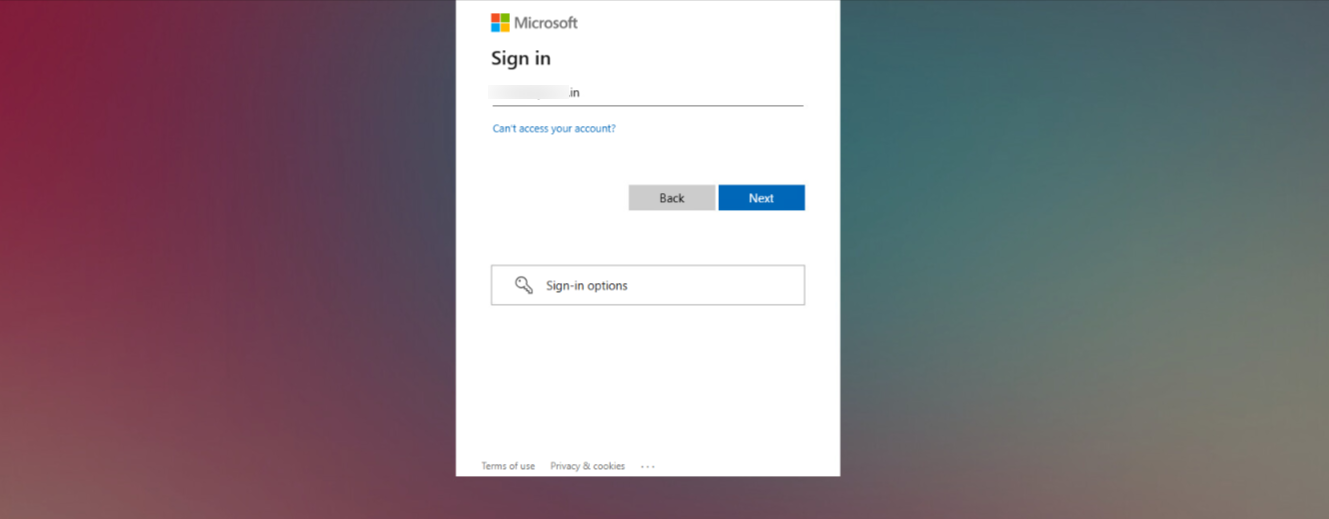
- The domain being configured in O365 account, the next screen will be from Microsoft. Enter your credentials (email address and password) and follow the steps to authenticate.
- Once authenticated, a new user account will be created on the device with the user type (Standard or Administrator), as selected in the New User Account type in IdP User Settings, with which you can login on the device next time. The user will also be added in Device details > User accounts section on Dashboard.
- If a local user with the same username already exists on the device, then it will get linked to the existing user present on the device. Hence, it is up to the discretion of IT admins whether to have a new user created on the device or not. If they want a new user to be created then the username in User Enrollment section should be different from the users already existing on the device.
- Username can be of maximum 20 characters. If it is longer, then it will be truncated till the 20th character. Also, if there are similar usernames then for the user who signs in next, after 18th character the username will automatically trim with 00, 01, 02 and so on appended to it. The full username will be used as the display name on the login screen.
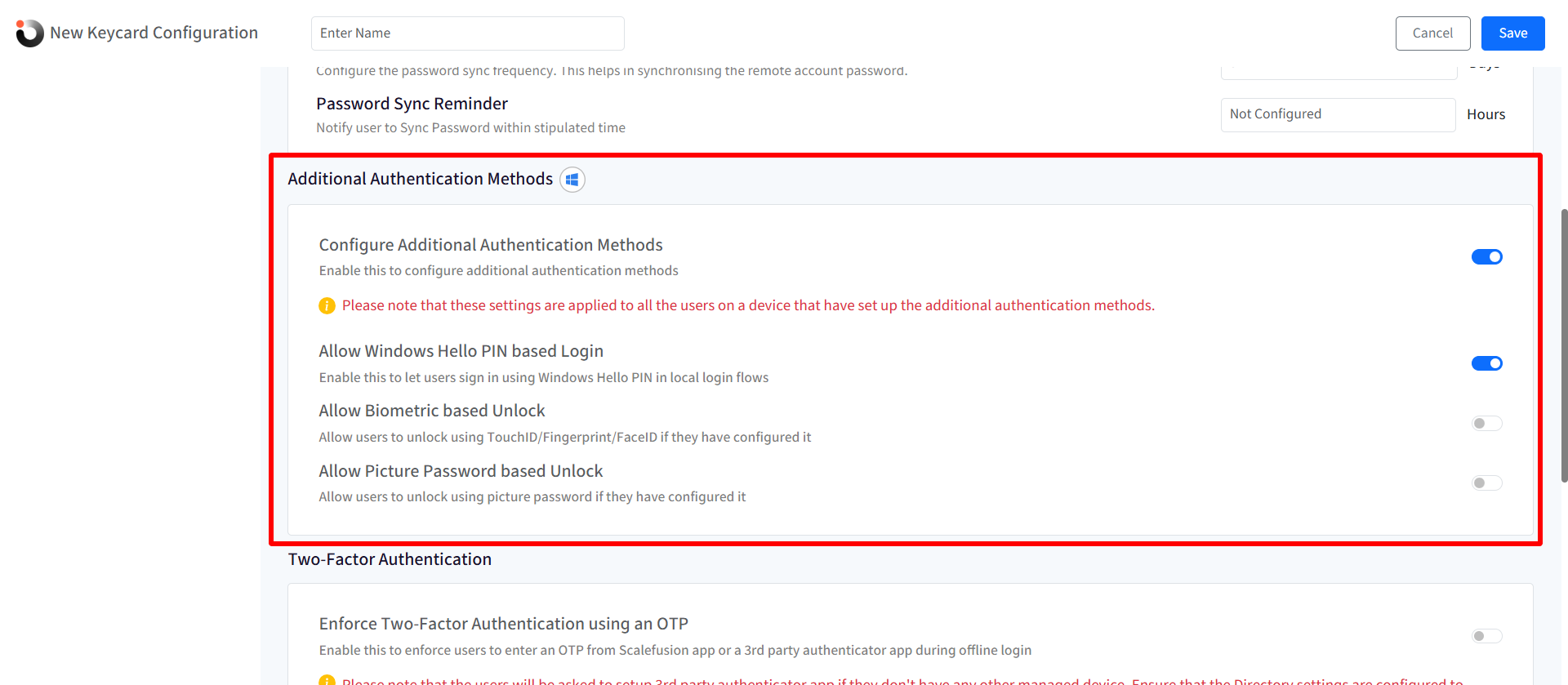
Additional Authentication Methods
Windows devices support a range of authentication methods that enhance user experience and security during offline (local) logins—that is, when the device is not connected to a network. These methods, such as Windows Hello PIN and TouchID/Fingerprint, allow users to access their devices quickly and securely without relying solely on traditional passwords.
With these methods you can enforce users to authenticate when they login through Keycard login screen. Let us learn how to enable and configure these additional authentication options. These settings are applied globally across the device, affecting all users who have set up the respective authentication mechanisms.
Pre-requisites
- Users should have these authentication methods configured on the devices
Enabling Additional Authentication Methods
- Navigate to Keycard Configuration > Keycard Settings
- Go to Additional Authentication Methods and configure the following:
- Configure Additional Authentication Methods: Enable this to allow additional authentication options for offline login. This serves as the parent control for all additional authentication methods on the device. When enabled, it allows users to log in using alternative methods such as PIN or biometric data.
- Allow Windows Hello PIN-Based Login: Allows users to sign in to the device using a personal identification number (PIN)
- Allow Biometric Based Unlock: Allows users to authenticate via biometric methods, such as fingerprint scanning (e.g., TouchID), faceID for offline login, provided the hardware supports it and the user has previously configured this option.
- Allow Picture Password based Unlock: Allows users to sign in to the device using a Picture password that allows users to sign in to their device using a combination of gestures on a picture.
- Configure Additional Authentication Methods: Enable this to allow additional authentication options for offline login. This serves as the parent control for all additional authentication methods on the device. When enabled, it allows users to log in using alternative methods such as PIN or biometric data.
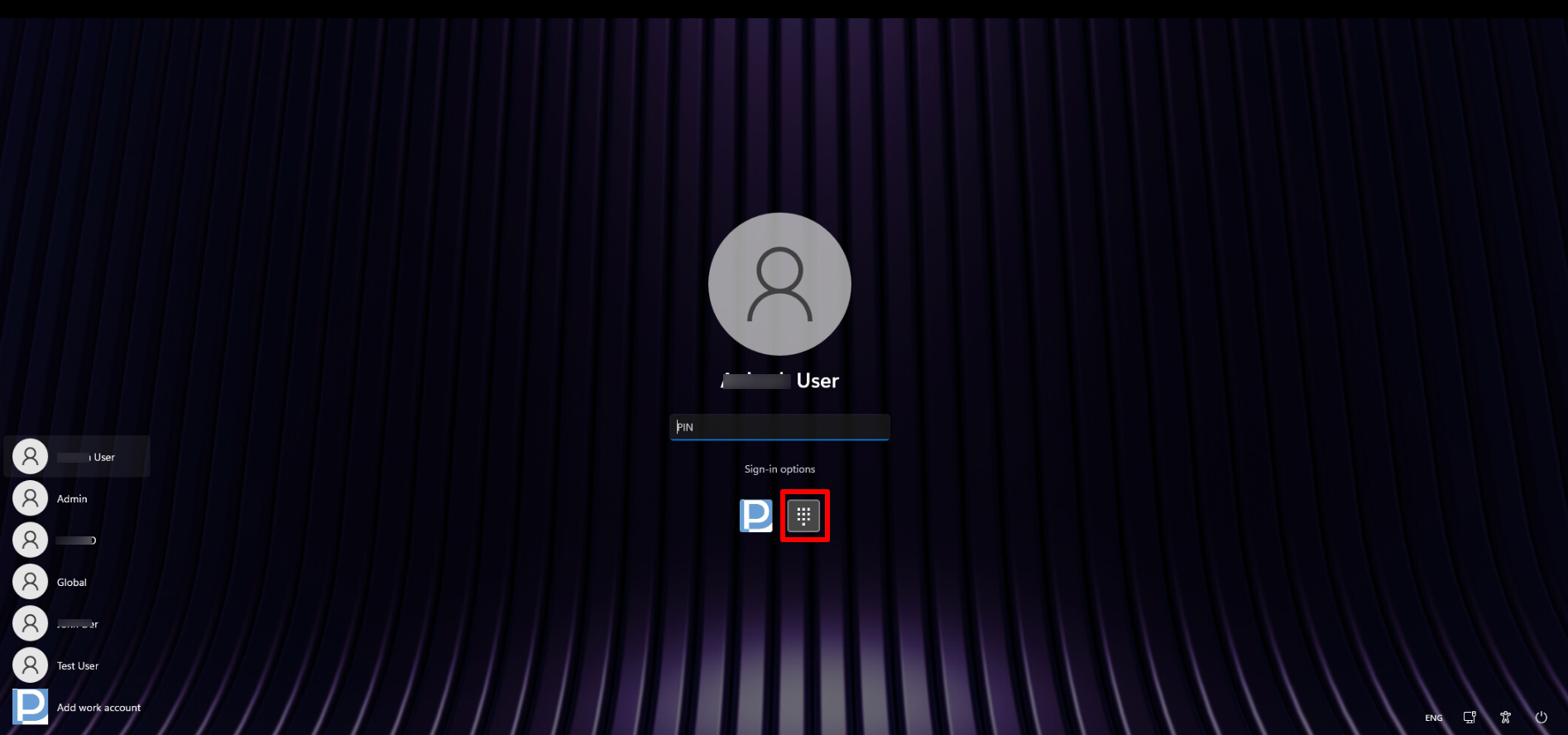
How Authentication methods work on device
If any of the above authentication methods are enabled and set by the user, the authenticator will display at the login screen with which you can login.
Two Factor Authentication
Traditional offline login methods often rely solely on stored credentials, such as passwords or cached tokens, which can be vulnerable to misuse if a device is lost or compromised. To enhance user authentication and reduce the risk of unauthorized access, implementing a one-time password (OTP) requirement for offline login provides an added layer of verification. This approach not only strengthens security by requiring users to verify their identity through an additional factor but also ensures that only the legitimate user can access the system, even without an active internet connection.
With the Enforce Two-Factor Authentication using an OTP option, you can now enforce users to enter an OTP from the Scalefusion Authenticator app from a managed mobile device (Android or iOS) or a 3rd party authenticator app during offline login in the Keycard login screen.
Pre-requisites
- The user must have at least one managed device with the Scalefusion Authenticator app installed or access to a third-party authenticator app that can generate the required OTP.
- The user(s) must be migrated to OneIdP.
Enabling Two-Factor Authentication
- Navigate to OneIdP > Keycard > click on Edit.
- Go to Keycard settings > scroll down to the Two-Factor Authentication section.
- Toggle on the Enforce Two-Factor Authentication using an OTP option.
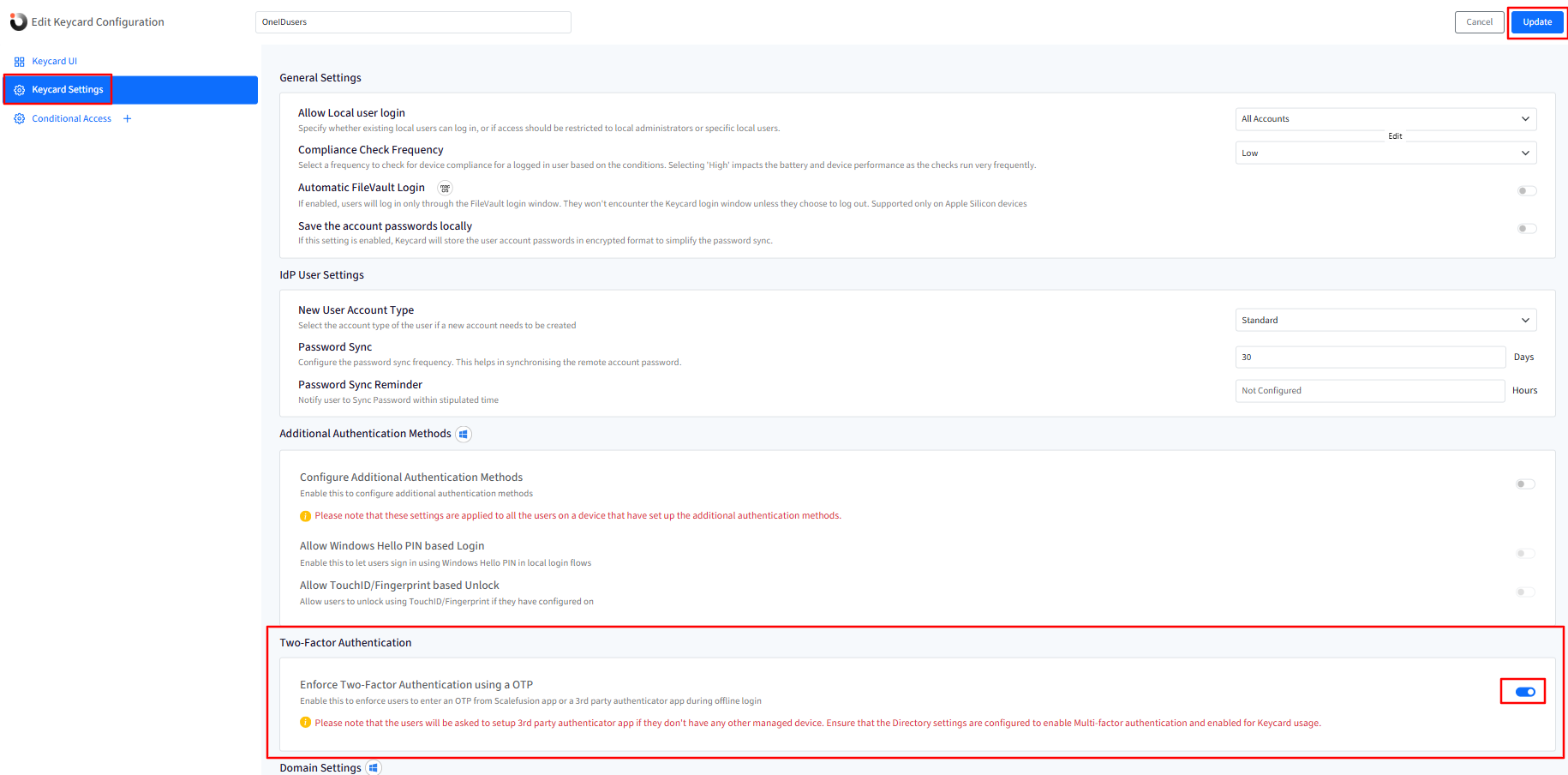
- Click on Update.
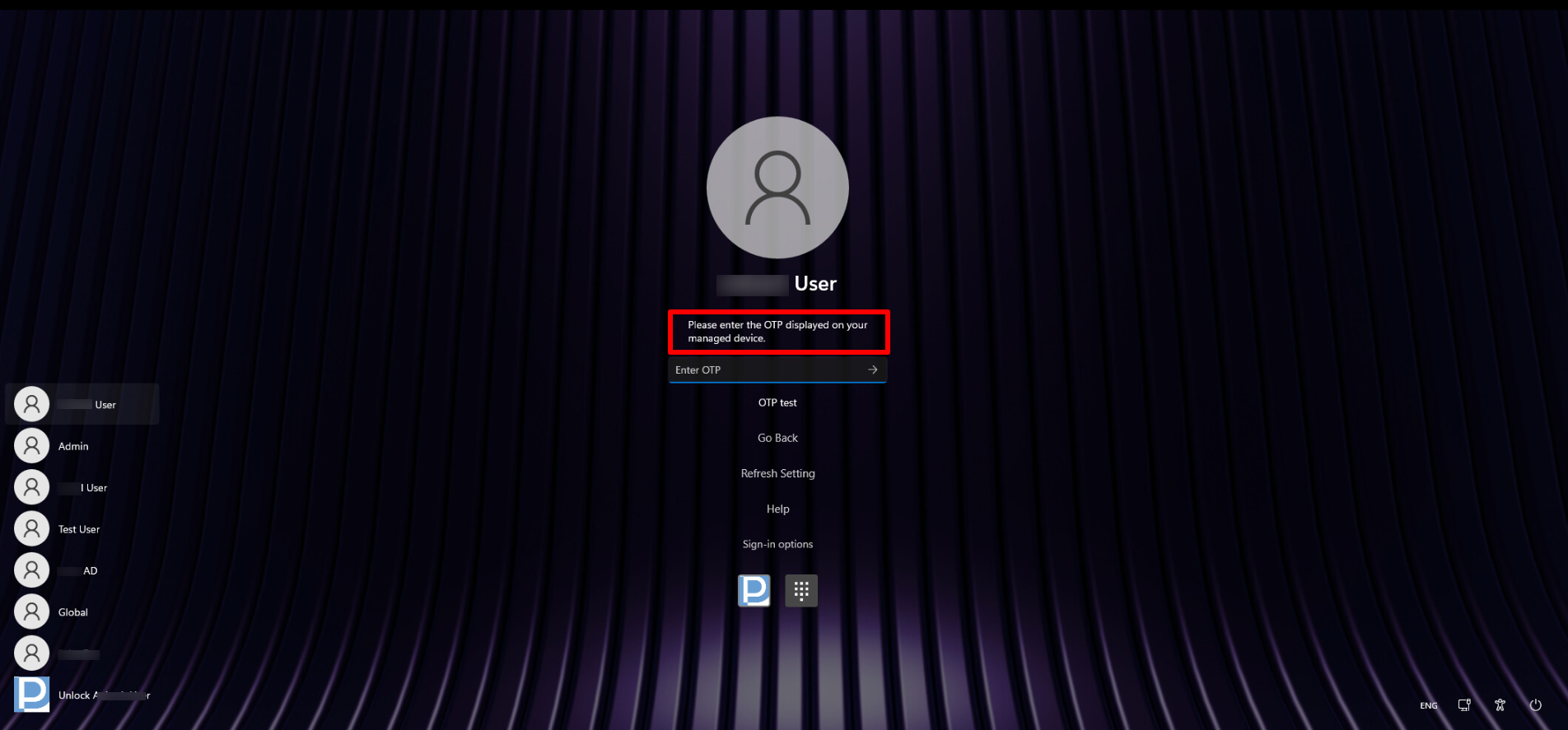
A. User(s) have a managed mobile device with the Scalefusion Authenticator app installed
- Once the setting is successfully applied to the device, the user(s) may see the following message when they try to log in locally on the device.
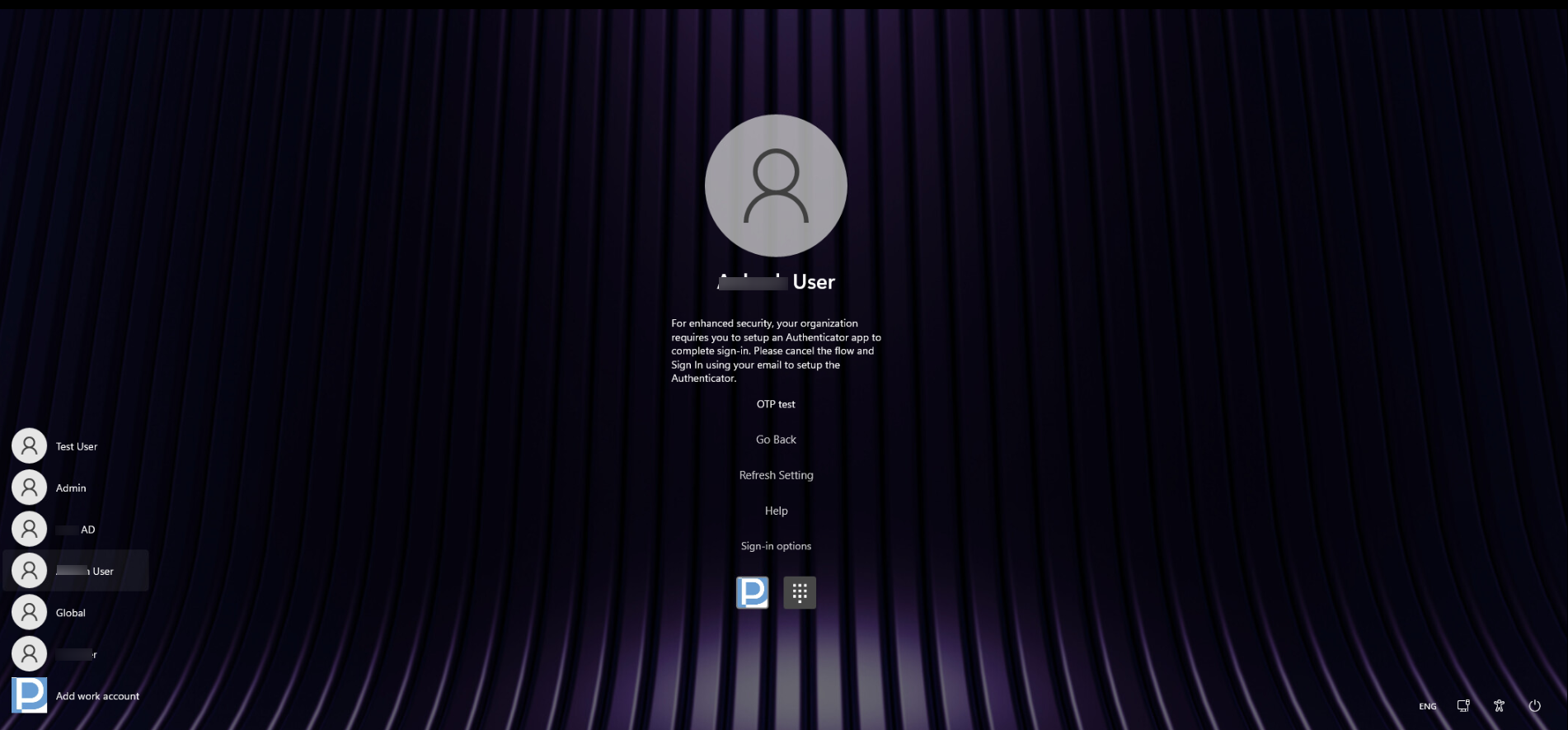
- They will be asked to complete an online login to synchronize the settings with the device.
- If the user(s) already have a managed mobile device (Android or iOS) with the Scalefusion Authenticator app installed, they can use the OTP from that device for their next local login.
B. User(s) do not have a managed mobile device with the Scalefusion Authenticator app installed
- Once the setting is successfully applied to the device, the user(s) may see the message (as shown above in point 1) when they try to log in locally on the device.
- They will be asked to complete an online login to synchronize the settings with the device.
- In this case, where the user(s) don't have a managed device, they can set up a 3rd party authenticator app on their device.
- However, for this to work, you will have to enable the option Enable MFA using third-party authenticator app in Directory Settings.
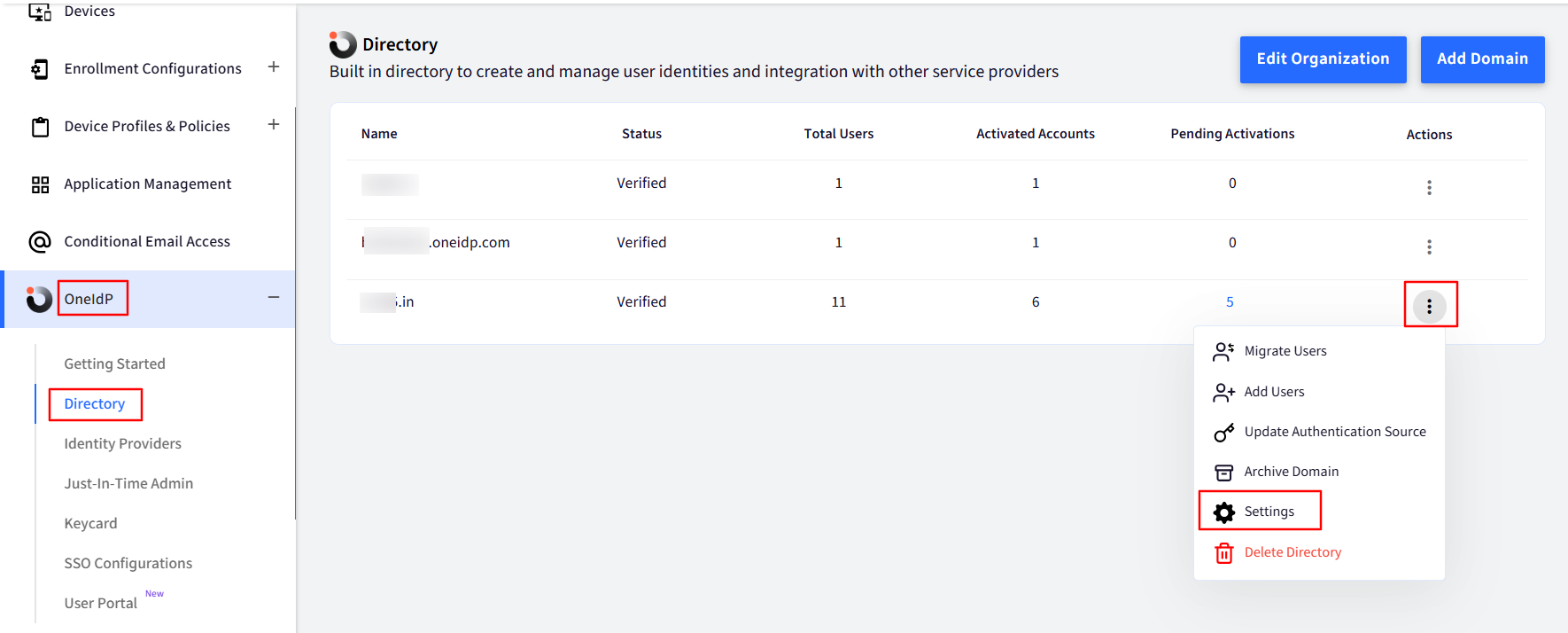
- Navigate to OneIdP > Directory.
- Click on the 3-dots for the concerned domain > Settings.
- Go to the Multi-factor Authentication tab and select the Enable MFA using third-party authenticator app option.
- Next, select the Use MFA for Keycard-based logins option.
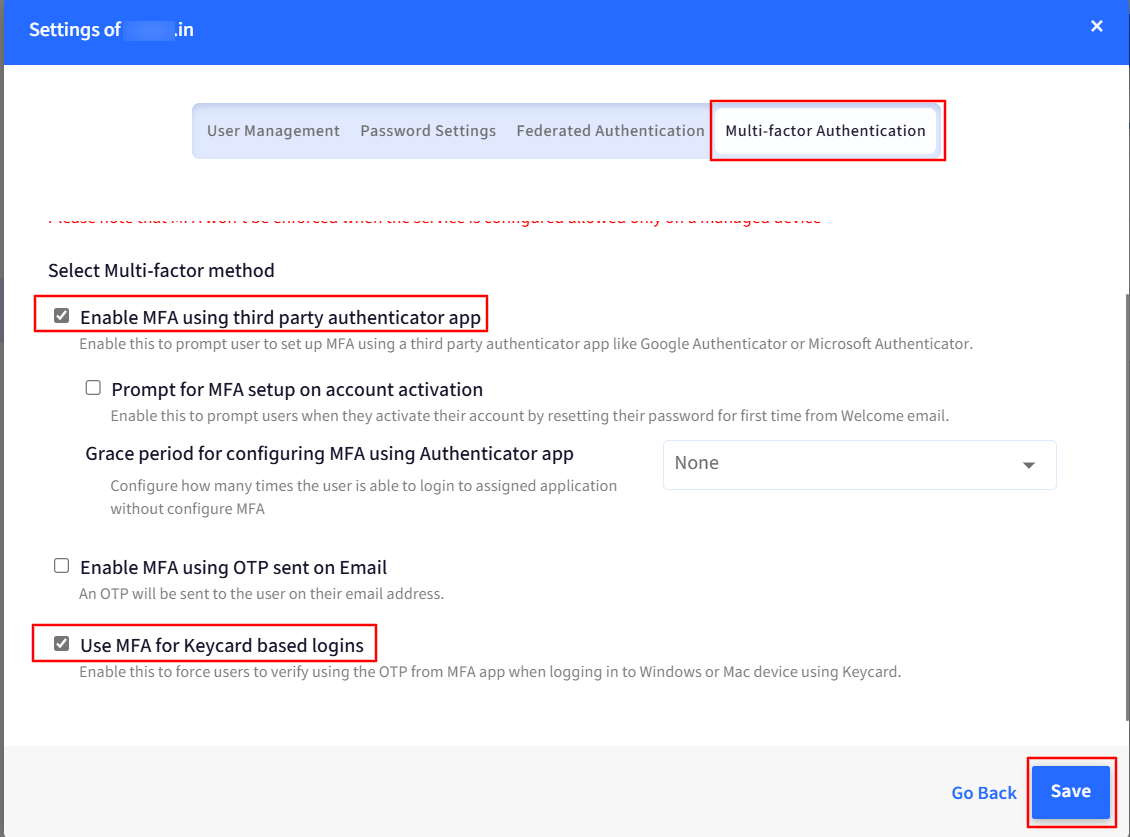
- Click on Save.
- Please note that the user must complete the online login using an OTP generated by a third-party authenticator app.
- Once this is done, on the next local login, they can use the OTP from a 3rd-party authenticator app.
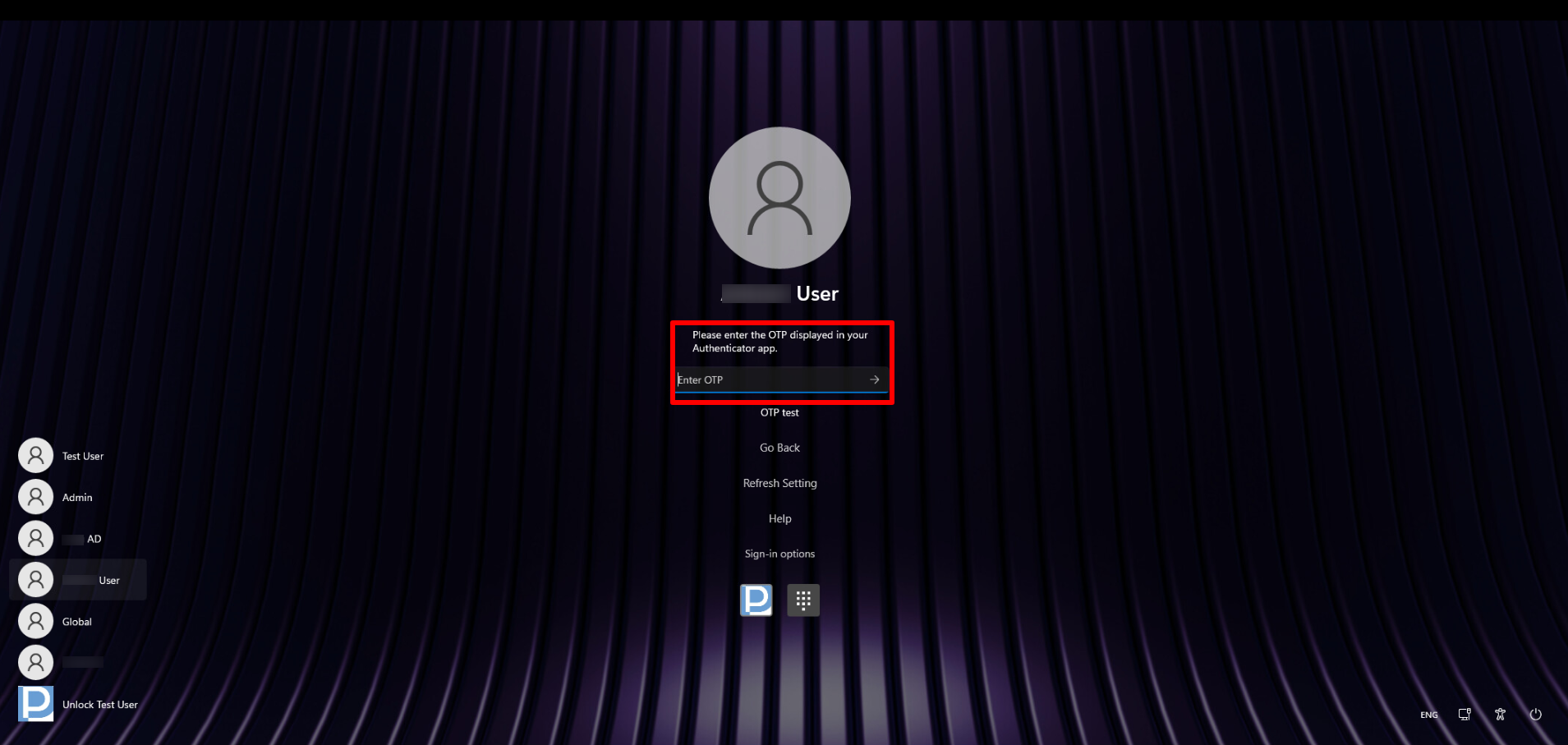
- The Two-Factor Authentication will not be applied to the native lock screen.
- If the user(s) have both (managed device as well as 3rd-party authenticator app), they can use OTP from either source.
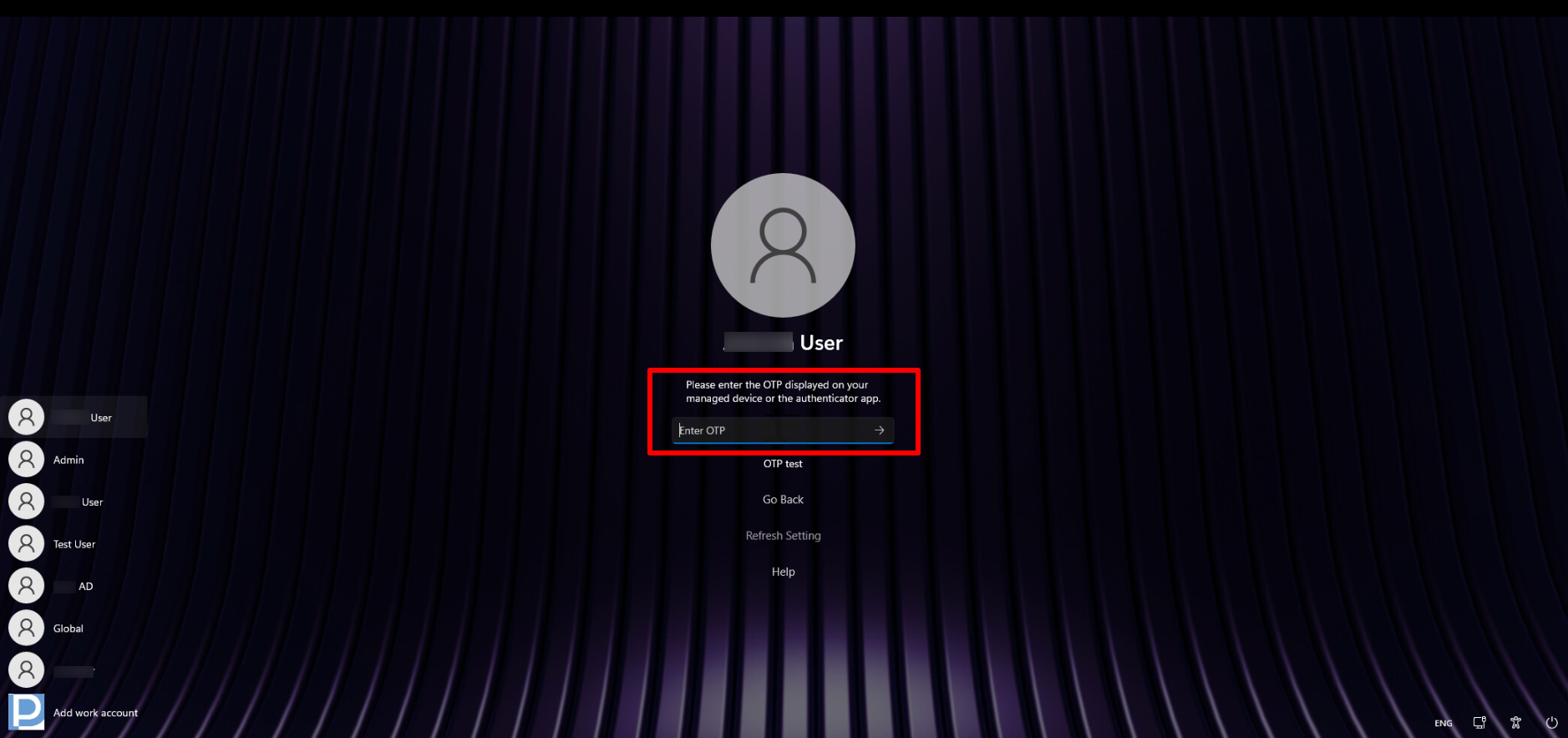
- If there are any updates about the concerned user that haven't synced with the device, the user can tap the Refresh Settings button, which will appear on the OTP screen, to retrieve the latest changes.
- If the Enforce 2FA option is enabled, the user might be required to log in to their account at least once, either online or offline.
- If the device is a managed mobile device, the user must be assigned to the SSO configuration in order to receive the OTP from the Scalefusion Authenticator app.
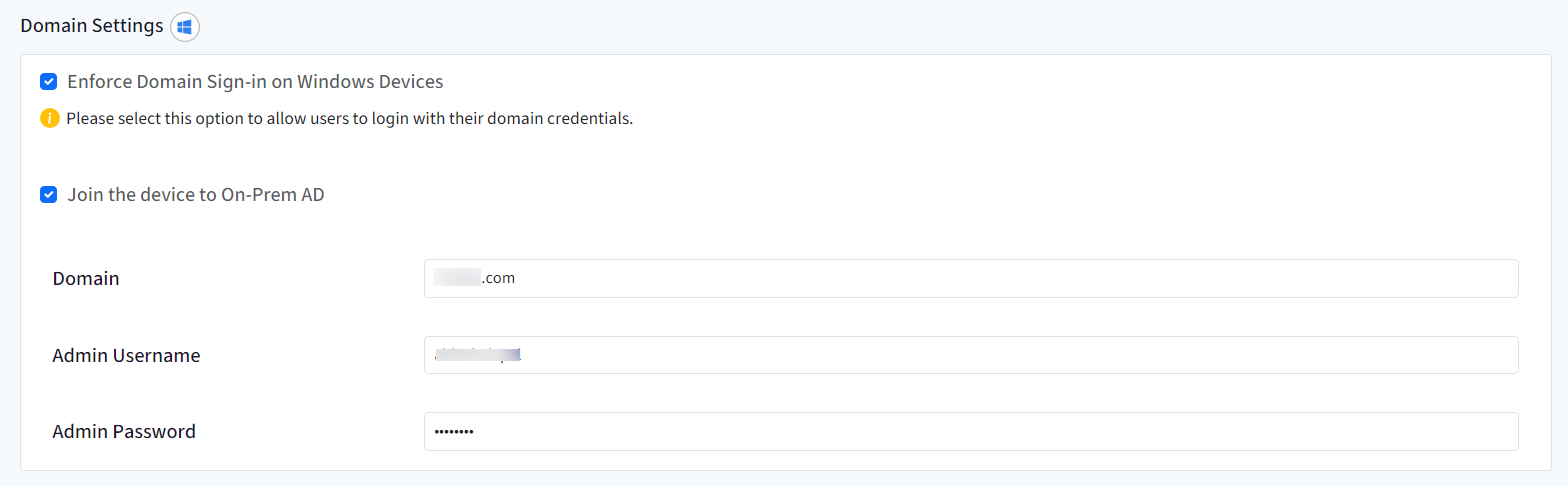
Domain Settings
- Enforce Domain Sign-in on Windows Devices: Allows users to sign in to the windows machine directly with their domain credentials. In this case, a new user account will not get created in User Account Management section or in User Management on the dashboard. Please note that once domain sign in has been enforced, only domain users or local users can sign in to the machine.
- To sign in with local users, end users will have to use the special convention of .\localaccountname
- Other users like Directory users cannot sign in to the machine if they DON’T exist (matching username) in the domain
- Join the device to On-Prem AD: Enabling this setting joins the windows device with a local domain once Keycard configuration is pushed, giving access to their Active Directory. As a result, the users belonging to the domain, can directly login to the device with their domain credentials. Enter the Active Directory domain name, admin username and password with which you want to join the Windows device.