In today’s security-conscious digital environment, controlling access to enterprise applications requires more than just a username and password. Extended Access Policies (XAP) provide a robust layer of conditional access control for Single Sign-On (SSO) configurations, enabling organizations to enforce Zero Trust principles. With a wide range of device and contextual signals such as compliance status, location, IP address, application presence, and security posture, XAP empowers administrators to dynamically allow or deny access in real time.
This document walks you through the setup, configuration, and management of Extended Access Policies using Scalefusion’s OneIdP.
How Extended Access Policies (XAP) Work
Here's an overall view of how the process works:
Policy Definition
An administrator defines access conditions within the Scalefusion portal using the XAP configuration wizard. These conditions may include compliance status, OS Updates & Patches, IP address, device location, installed applications, and other contextual signals.Real-Time Evaluation
Scalefusion evaluates these conditions in real time using its built-in Rules Engine, continuously monitoring device posture and user context against the defined policies.Signal Transmission to OneIdP
Based on the evaluation, Scalefusion passes a compliance signal to OneIdP, indicating whether the device and user meet the defined access criteria.Access Enforcement by OneIdP
OneIdP uses this compliance signal to:Allow or block access to SSO-integrated services.
Automatically log out users from devices that no longer meet compliance requirements.
Store logs and audit data for future analysis and compliance reporting.
Pre-Requisites
User Groups should be created on Scalefusion Dashboard
SSO should be configured for the required application(s)
Veltar > Compliance should be configured on Scalefusion Dashboard
OS Updates & Patch Management should be configured on Scalefusion Dashboard
Step 1: Create Configuration
To create or edit an Extended Access Policy (XAP) configuration,
On Scalefusion Dashboard, navigate to OneIdP > Extended Access Policies > Access Policies
Click on Create Configuration.
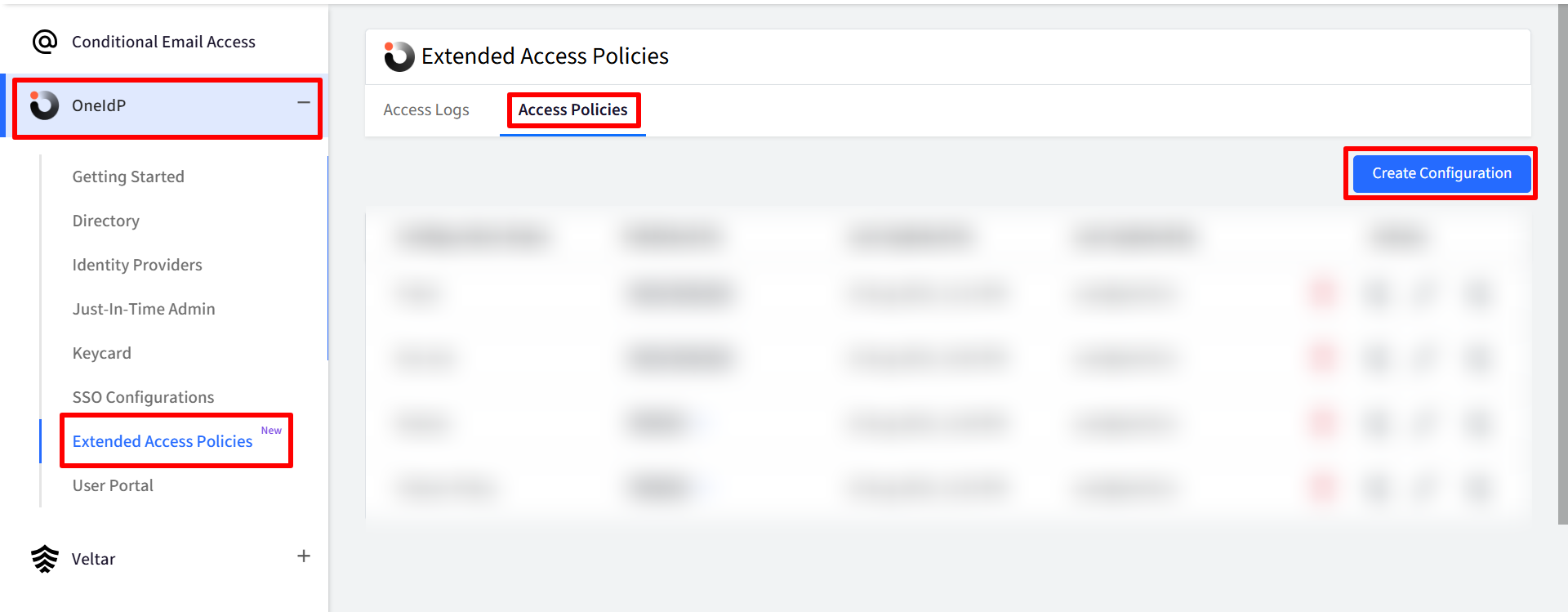
This will open the XAP Wizard, where you can set up or modify your access policies.
Name: Enter a name for your configuration.
The configuration wizard has following tabs to organize settings:
Configure the above and click on Save Configuration
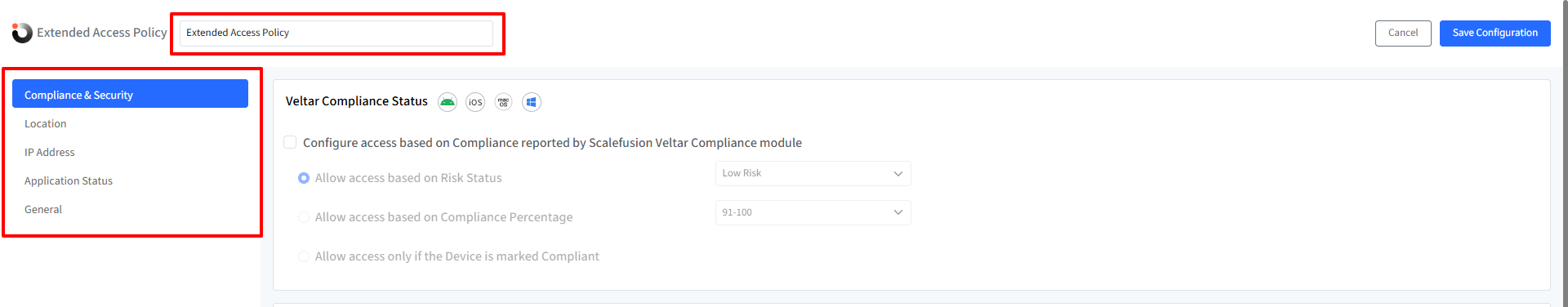
Compliance & Security Settings
Click on the Compliance & Security tab to configure access rules based on device compliance and security status.
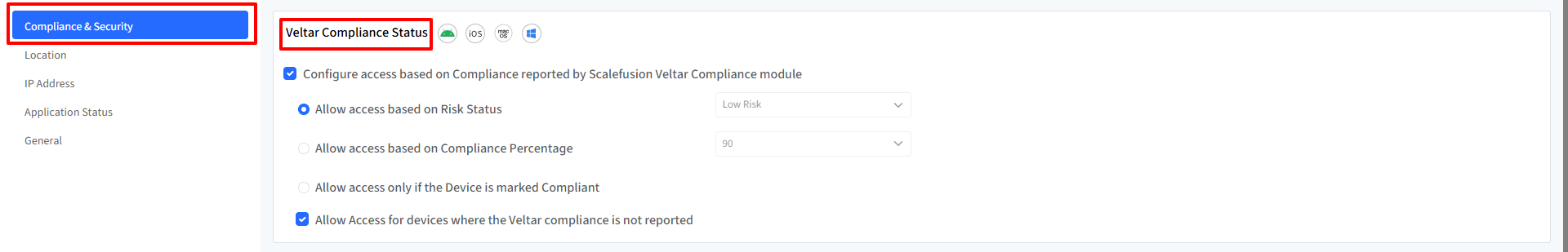
Veltar Compliance Status
Configure access based on Compliance reported by Scalefusion Veltar Compliance module
Turns on access control based on compliance reports from the compliance module. Choose one of the following:
Allow Access Based on Risk Status
Choose risk levels that allow access (e.g., Low, Medium).
Default: Low risk only.
Allow Access Based on Compliance Percentage
Select the minimum compliance percentage required to allow access:
100
90
80
70
60
50
Allow Access Only if Device is Marked Compliant
This option requires the device to be marked compliant.
Allow Access for Devices Where Veltar Compliance Is Not Reported
Grants access to devices that haven’t reported their compliance status yet. This option is helpful when devices are in a transitional state (e.g., first-time setup or offline), and compliance data is not immediately available.
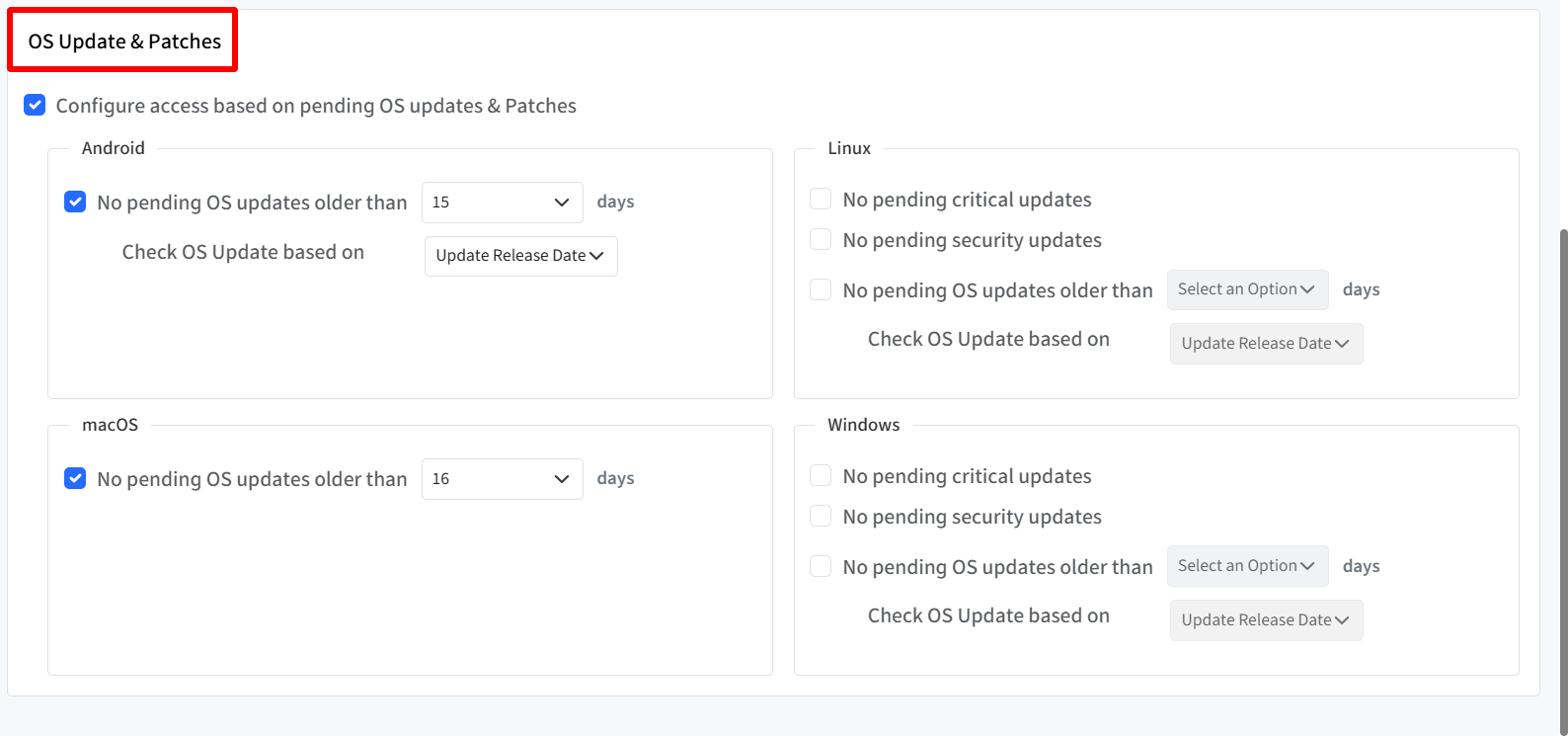
OS Updates & Patches Access Control
Configure access based on pending OS updates & Patches
Turns on access control based on OS update status. Choose the settings as per platform
Platform
Conditions
Android
No pending OS updates older than [15-30] days
Check OS Update based on:
Update Release Date
Reported On
Linux
No pending critical or security updates;
No OS updates older than [15-30] days
Check OS Update based on:
Update Release Date
Reported On
macOS
No pending OS updates older than [15-30] days
Windows
No pending critical or security updates;
No OS updates older than [15-30] days
Check OS Update based on:
Update Release Date
Reported On
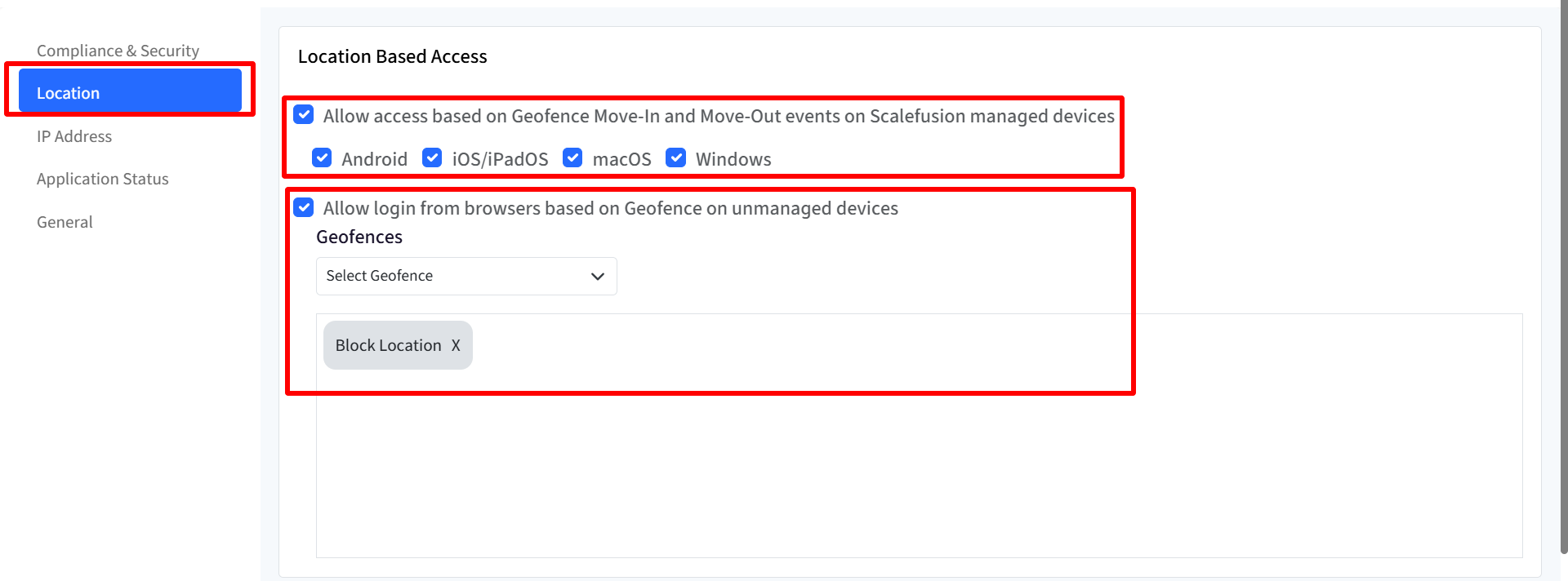
Location Settings
To configure location-based access controls, click on the Location tab. This opens the Location settings where you can manage access based on device location using geofences
Geofence must be published on managed devices to apply XAP policy
a. Allow Access Based on Geofence Move-In and Move-Out Events on Scalefusion Managed Devices
Enable this to control access to managed devices using geofences. You can apply geofence access rules to specific platforms:
Android
iOS/iPadOS
macOS
Windows
b. Allow Login from Browsers Based on Geofence on Unmanaged Devices
Enable this to restrict browser logins on unmanaged devices using geofence rules. Here, select the geofence(s) (as created on dashboard) from the drop-down, on which you want to apply location-based access.
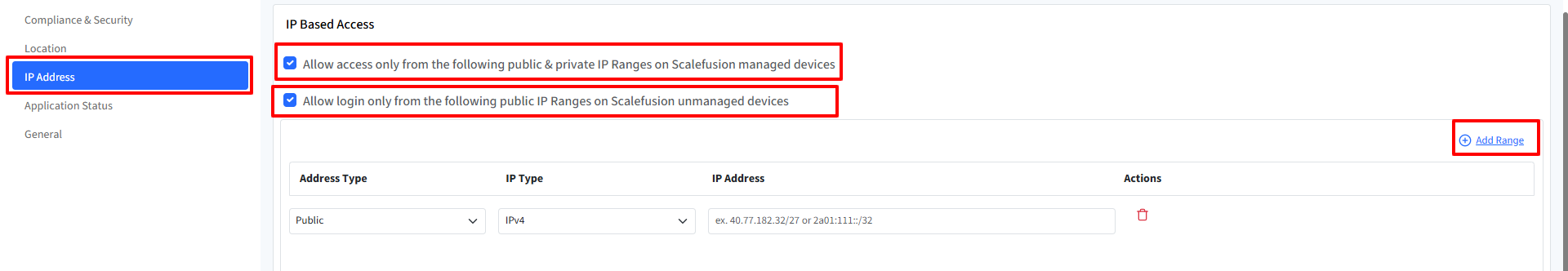
IP Address Settings
To configure access control based on IP addresses, click on the IP Address tab in the Extended Access Policy wizard. This section allows you to restrict logins based on specified IP ranges.
1. Restrict Access for Managed Devices
Allow access only from the following public & private IP ranges on Scalefusion managed devices: When enabled, access will only be allowed from the specified IP ranges for devices managed by Scalefusion.
Restrict Browser Logins for Unmanaged Devices
Allow login only from the following public IP ranges on unmanaged devices: When enabled, users can only log in via browsers on unmanaged devices from the listed public IP addresses.
Use the IP Address table to define the allowed IP ranges.
Field | Description |
|---|---|
Address Type | Select Public or Private IP addresses |
IP Type | Choose IPv4 or IPv6 |
IP Address | Enter valid IP addresses or ranges in CIDR format (e.g., |
Actions | - Add Range: Adds a new row for IP input |
By clicking on Add Range, you can add multiple IP ranges as needed to cover different network segments.
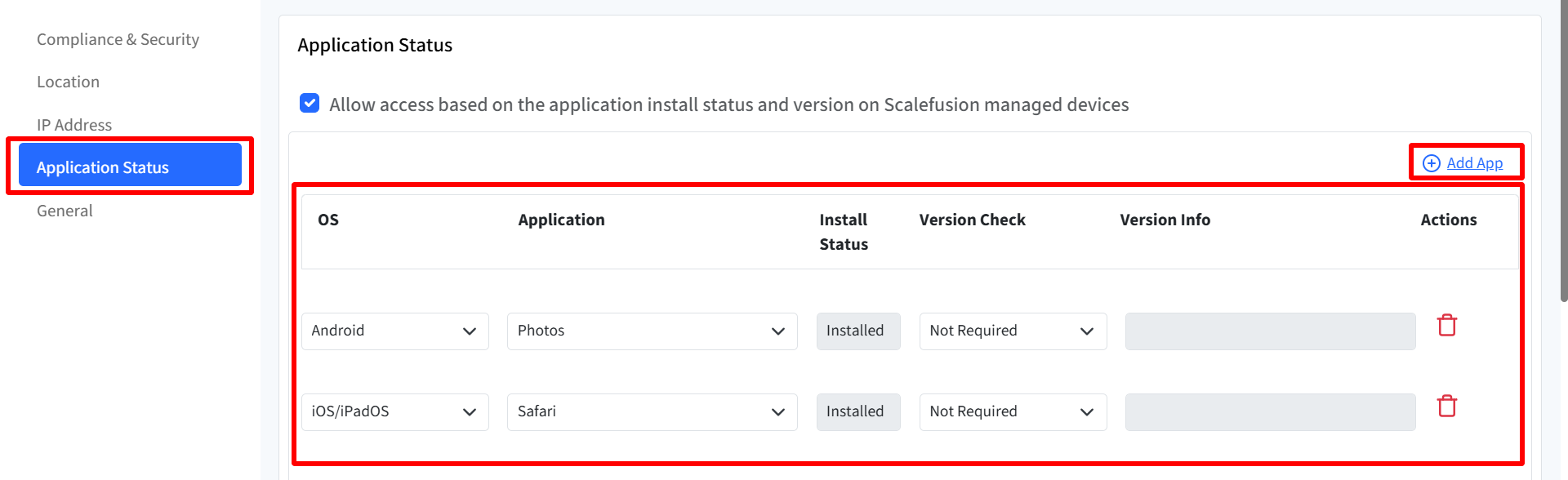
Application Status Settings
To configure access rules based on the presence and version of installed applications, click on the Application Status tab in the Extended Access Policy wizard.
Allow access based on the application install status and version: Enabling this option allows you to define access conditions based on whether specific applications are installed on a device—and optionally, their version. Use this feature to restrict access to devices that must have specific business-critical apps installed. You can enforce minimum app versions for added security or compatibility.
Use this table to add application-based access rules for different operating systems.
Field | Description |
|---|---|
OS | Select the platform:
|
Application | Search for the application (searches apps from your account based on the selected OS). Lists all applications installed on the device including Enterprise Apps and Scalefusion Managed Apps. |
Install Status | Installed |
Version Check | Choose if and how to validate the app version:
|
Version Info | Enter the version value (enabled only if Version Check is set to Name or Code) |
Actions | - Delete: Removes a row from the table |
Likewise, click on Add App on the top right to add multiple apps for different OS.
Platform-Specific Behavior
Windows: Version Code is disabled (only Version Name is available).
macOS and iOS/iPadOS: Version Name is disabled (only Version Code is available).
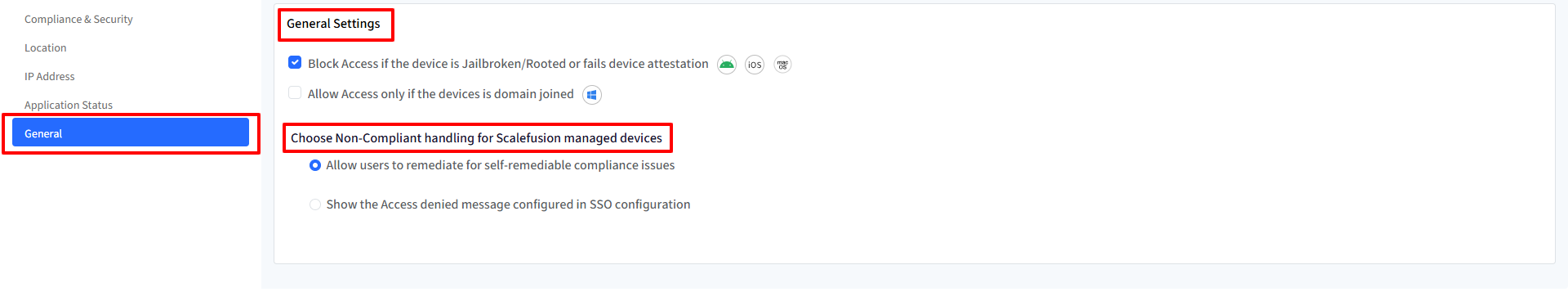
General Settings
To manage additional access control rules and fallback options, click on the General tab in the Extended Access Policy wizard.
General Settings
Block Access if Device is Jailbroken, Rooted, or Fails Attestation
Prevents access from devices that are jailbroken (iOS), rooted (Android), or fail device attestation checks.
Applies to Platforms: Android, iOS, macOS
Allow Access only if the devices are domain joined
Grants access to those devices which are domain joined
Applies to Platforms: Windows
Choose Non-Compliant Handling for Scalefusion Managed Devices
Choose one of the following options to handle access for devices that are marked non-compliant.
Allow users to remediate for self-remediable compliance issues
Users will be prompted to fix issues themselves if they are resolvable (e.g., install updates). In this case, following will be the kind of prompt users will see on the device: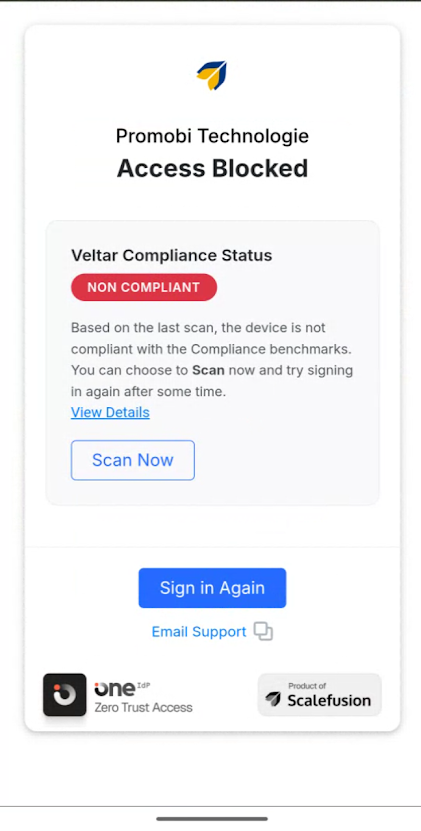
Here,
View Details: This will show the all Failed Rule summary.
Scan Now: This will immediately initiate a compliance scan on your desktop devices
Update: This will start to install the pending updates.
In case OS Updates & Patches are pending, following will be the prompt: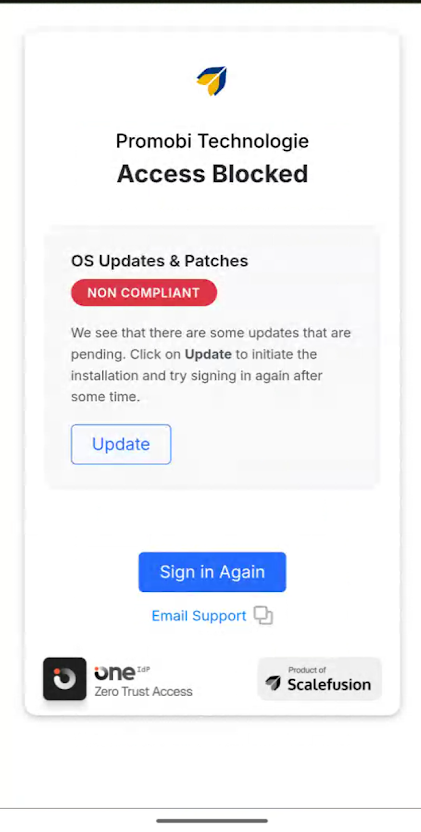
Show the Access Denied message configured in SSO configuration
Blocks access and displays a message as defined in your SSO configuration.
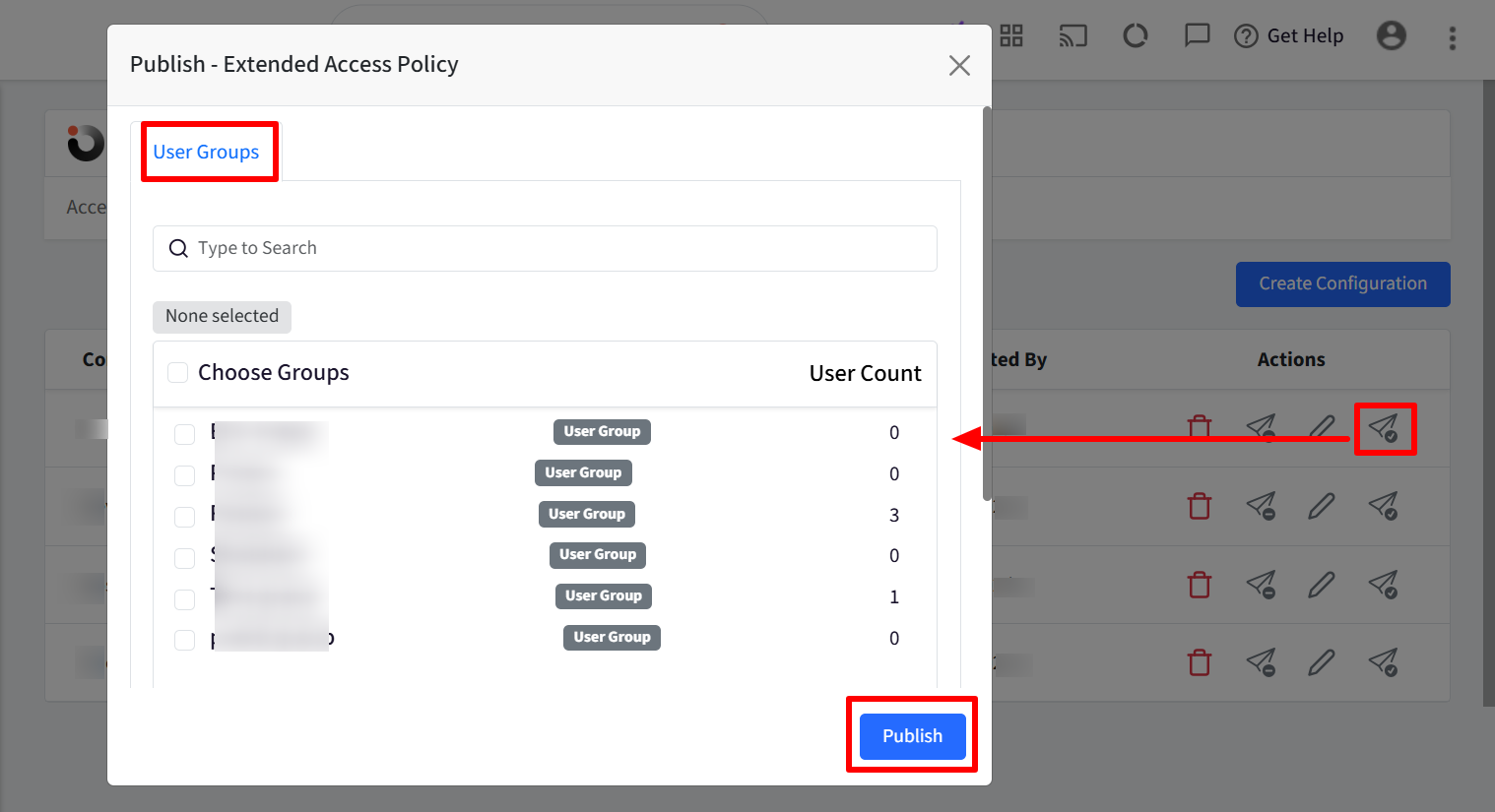
Step 2: Publish Configuration
Once the configuration is created it will be displayed under Access Policies tab with other related details. To Publish,
Click on publish icon in front of the configuration
In the new window, select the user group(s) on which you want to publish the configuration.
Click Publish
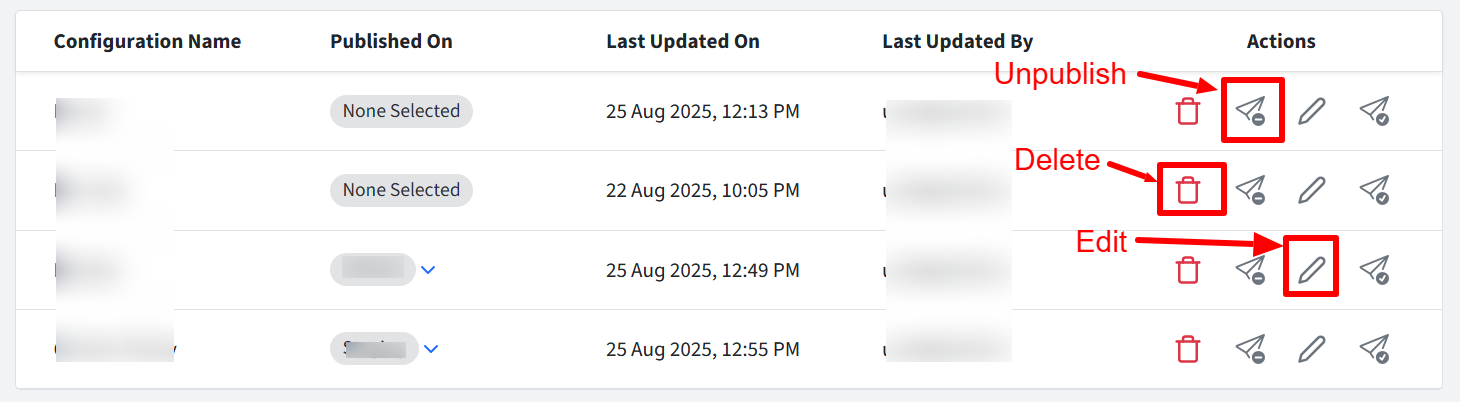
Additional Actions
You can also take additional actions on a configuration:
Unpublish: Unpublishes the extended access policy from the user groups on which it is already published.
Edit
Delete: Deletes the configuration and clears the compliance records from all devices currently using this configuration.
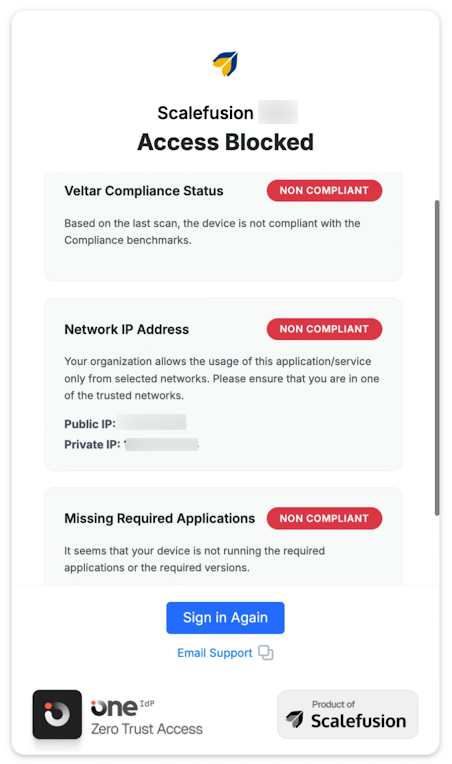
End User Experience
When signing in on a device with an Extended Access Policy (XAP) applied, users will encounter a compliance check screen as part of the login process.
Note: The example shown reflects a scenario where policies for Veltar Compliance, IP address restrictions, and application requirements are in effect.