BitLocker is Microsoft’s built-in full-volume encryption feature designed to protect data by providing encryption for the drives. It integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker works best on computers with Trusted Platform Module (TPM) version 1.2 or later. TPM is a hardware component installed in many newer computers by computer manufacturers. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system is offline.
On computers that do not have TPM version 1.2 or later, you can still use BitLocker to encrypt the Windows operating system drive.
Scalefusion lets IT Admins configure BitLocker settings and apply these settings to manage Windows 10 and above devices. Further on Azure AD joined devices the BitLocker encryption can be enforced and automated.
Prerequisites
BitLocker requires Windows 10 v1809+ and above to work on Windows Pro, Enterprise, Education, and Server (if Bitlocker Settings are installed on Server) Editions.
The latest Scalefusion MDM Agent should be published for the device(s).
Not Supported on Windows Home (10 & 11).
The following document guides you through setting up BitLocker and pushing the configuration to devices. We also cover the user experience once the BitLocker policy is pushed to devices.
Note:
When Agent based BitLocker settings is applied then both OS Drives and Fixed Drives will be encrypted.
Setting up BitLocker in Windows Profile
The first step is to configure a BitLocker policy that can be pushed to devices. Follow the steps below to configure a BitLocker policy:
Sign In to your Scalefusion Dashboard.
Navigate to Device Profiles & Polices > Device Profiles. Click on a Windows Device profile to Edit it. Or click on the Create New Profile button if you are creating a Windows Profile for the first time.
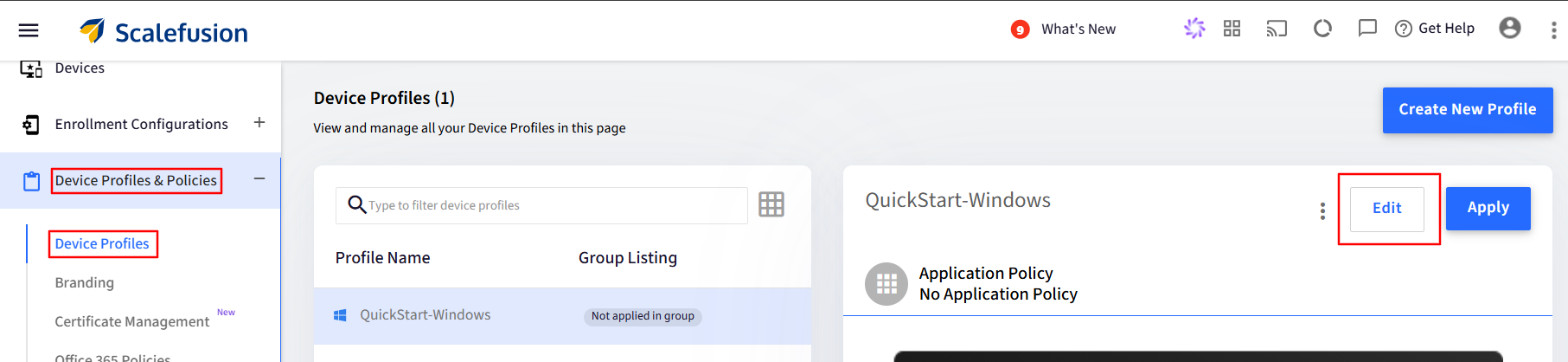
Once in the Device Profile wizard, navigate to Settings > Security Settings. Go to the BitLocker section to configure BitLocker settings.
Toggle On the Prompt for Device Encryption button. This will make the BitLocker settings under it accessible.
BitLocker Settings
The following are the BitLocker settings that you can configure to encrypt the Windows Operating system drives.
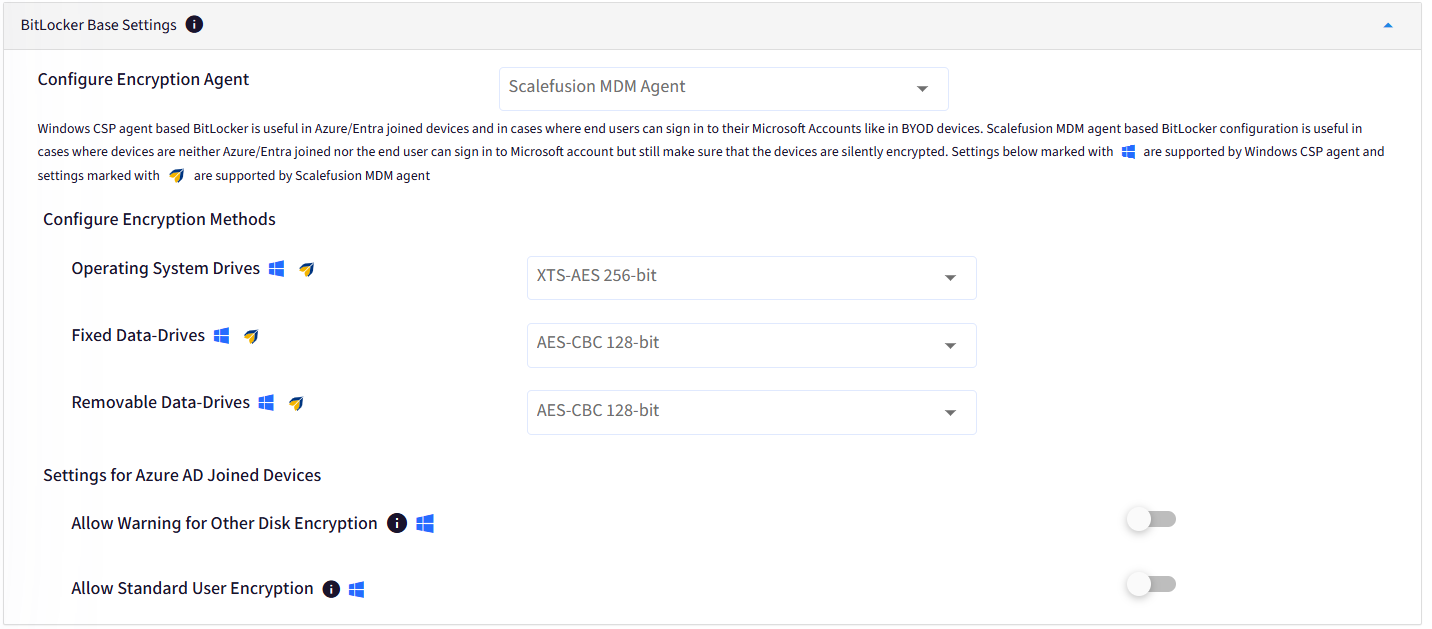
A. BitLocker Base Settings
The first section controls the basic encryption settings.
Configure Encryption Agent: To apply BitLocker encryption via Scalefusion MDM Agent please select Scalefusion MDM Agent from the drop-down menu list.
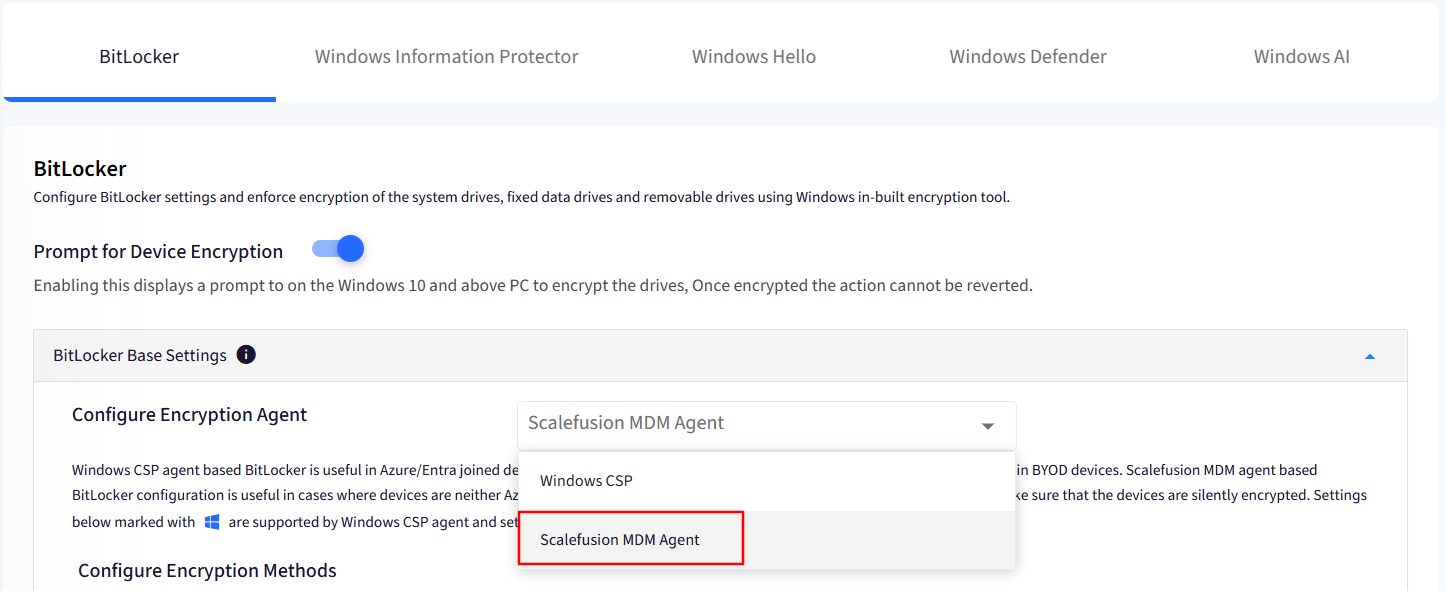
Scalefusion MDM agent-based BitLocker configuration is useful in cases where devices are neither Azure/Entra joined nor the end user can sign in to a Microsoft account, however, BitLocker encryption via Scalefusion MDM Agent makes sure that the devices are silently encrypted.
Note:
Settings marked with
 are supported by Windows CSP and settings marked with
are supported by Windows CSP and settings marked with  are supported by Scalefusion MDM agent
are supported by Scalefusion MDM agent
Configure Encryption Methods: Choose an encryption algorithm for the various disk drives.
Operating System Drives: Defaults to XTS-AES 256-bit
Fixed Data Drives: Defaults to AES-CBC 128-bit
Removable Data Drives: Defaults to AES-CBC 128-bit
Settings for Azure AD joined Devices: These settings are applicable only for devices enrolled using the AD join method. Please note these settings are only supported on Windows CSP.
Allow Warning for Other Disk Encryption: Enable this to show a warning for AD-joined devices. Disabling this silently applies the BitLocker settings.
Allow Standard User Encryption: Enable this to encrypt all the disk drives for a standard user account.
B. Configure Startup Authentication for System Drives
Use this section to configure additional authentication methods when the computer starts and configure settings for computers with/without a TPM chip.
Enforce Additional Authentication at Startup: Enable this setting to configure additional authentication mechanisms.
Allow BitLocker on PCs without a Trusted Platform Module(TPM): Configure BitLocker for computers without a TPM chip.
Select Authentication method for PCs with a Trusted Platform Module: Select the authentication method. You will see 4 options that you can choose from.
Use System Defaults: The user will get a prompt to set Pin and Password on the device. On reboot and fresh start there is no requirement to enter Pin or Password.
Use Password: The user will get a prompt to set Pin and Password on the device. On reboot and a fresh start, users will need to enter the password that they have set during the encryption process.
Use TPM & Startup Pin: The user will get a prompt to set Pin and Password on the device. On reboot and fresh start, the user will need to enter the Pin that they have set during the encryption process.
For unlocking the Fixed Drives user will need to enter the password.
Use TPM during Startup: This option is helpful when the admin might want to encrypt the drives without any user interaction. In this case, the password will be auto-generated. On reboot and fresh start, there is no need to enter Pin or Password to unlock the device.
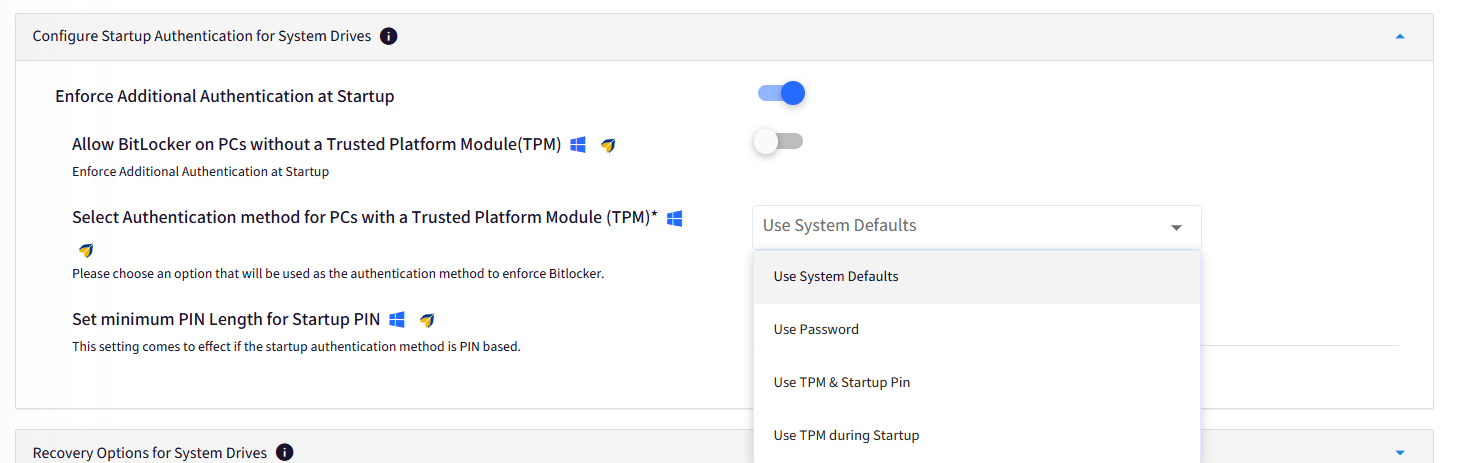
Set Minimum Length for Startup PIN: Enforce a minimum PIN length that needs to be configured.
This setting works only if the authentication method includes a PIN.
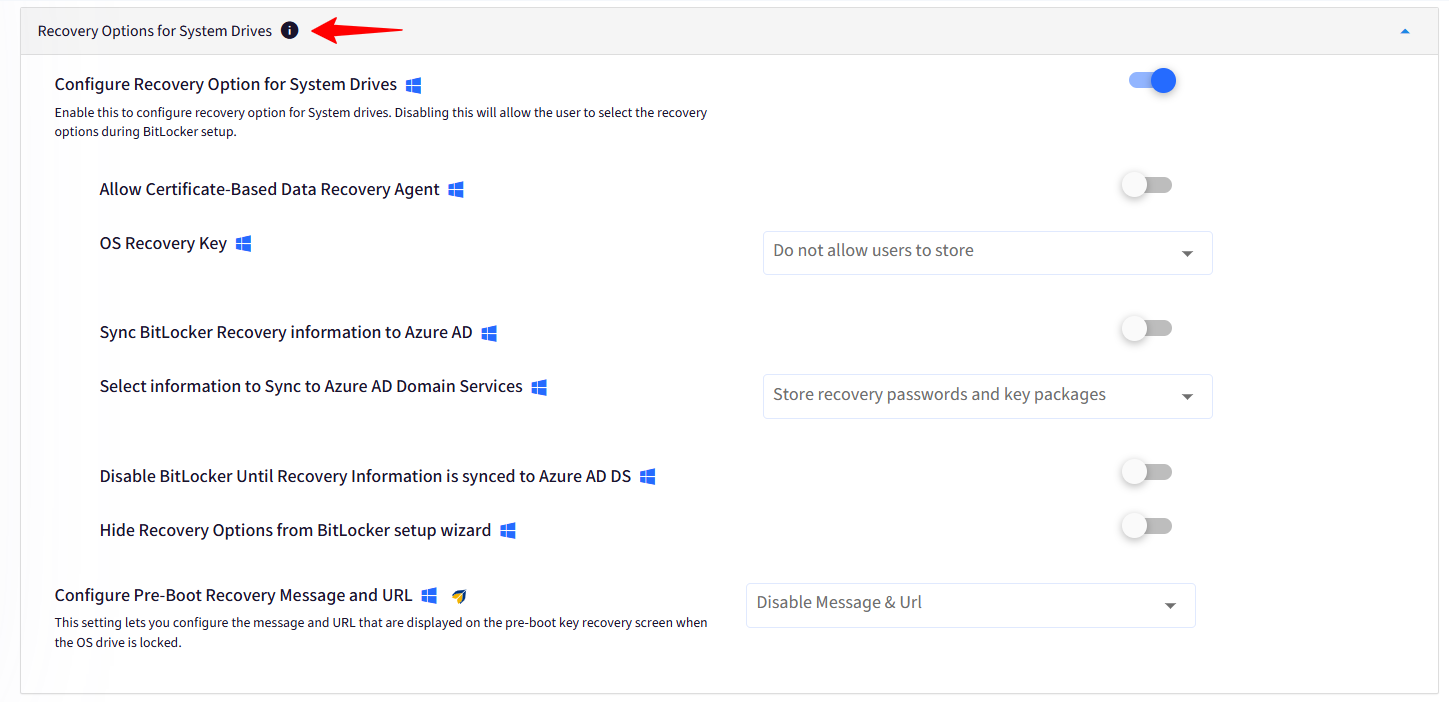
C. Recovery Options for System Drives
If you have configured the startup authentication, then this method allows you to configure the recovery mechanisms for System drives (the drive that hosts the OS).
Note:
The settings in this section will only apply if the Windows CSP is chosen in the "Configure Encryption Agent" section of the BitLocker Base Settings. Except for option “Configure Pre-boot Recovery Message and URL” which is applicable for Scalefusion Agent based settings also.
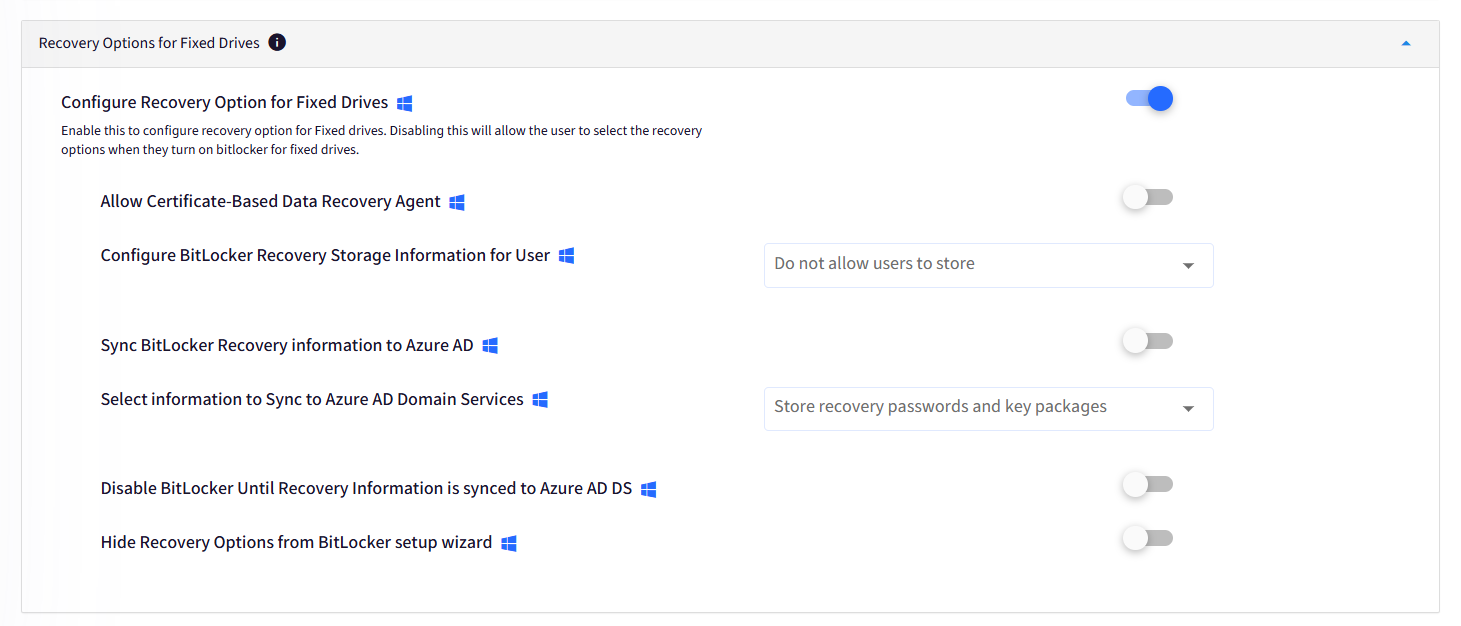
Configure Recovery Option for System Drives: Enable this to configure the recovery options.
Allow Certificate-Based Data Recovery Agent: Specify whether a data recovery agent can be used with BitLocker-protected operating system drives. Before a data recovery agent can be used it must be added from the Public Key Policies item in either the Group Policy Management Console or the Local Group Policy Editor.
OS Recovery Key: Configure if users are allowed, required, or not allowed to generate a 48-digit recovery password or a 256-bit recovery key.
Sync BitLocker Recovery Information to Azure AD: Enable this to Sync the BitLocker recovery/escrow keys to Azure AD. This setting works only if the device is Azure AD joined.
Select information to Sync to Azure AD Domain Services: Choose what information related to BitLocker recovery should be used to sync with Azure AD.
Disable BitLocker Until Recovery Information is synced to Azure AD DS: Prevent users from configuring BitLocker until they join their devices to Azure AD.
Hide Recovery Options from BitLocker setup wizard: Prevent users from specifying recovery options when they turn on BitLocker on a drive. This means that you will not be able to specify which recovery option to use when you turn on BitLocker, instead, BitLocker recovery options for the drive are determined by the policy setting.
Configure Pre-boot Recovery Message and URL: Override the default pre-boot recovery message and URL that is displayed when the computer starts.
D. Recovery Option for Fixed Drives
Configure recovery options for your fixed drives. These options are similar to the Recovery Options for System Drives, as seen previously in Point C; except that these are set for the non-System or other fixed drive partitions.
Note
The settings in this section will only apply if the Windows CSP is chosen in the "Configure Encryption Agent" section of the BitLocker Base Settings.
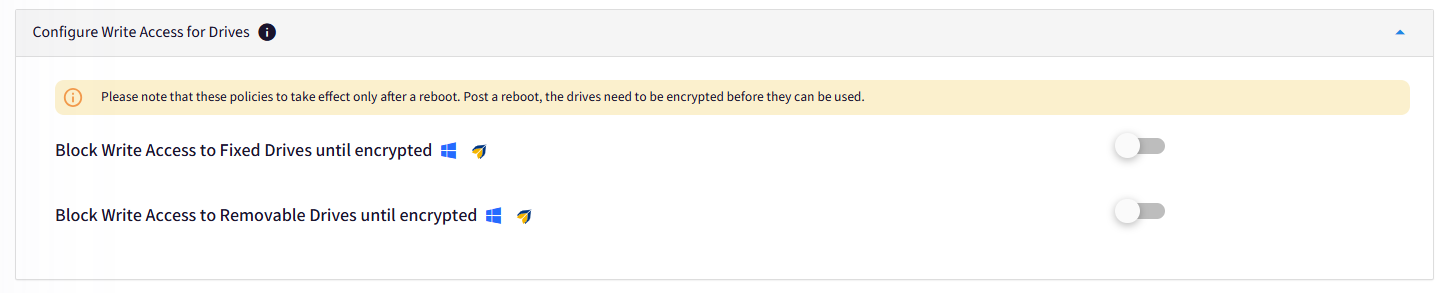
E. Configure Write Access for Drives
Block Write Access to Fixed Device until encrypted: If enabled blocks write access to fixed drives until they are encrypted.
Block Write Access to Removable Devices until encrypted: If enabled blocks write access to removable drives until they are encrypted.
Note:
The existing data stored on these drives can be read always.
F. Configure Scalefusion MDM Agent based Settings
The settings in this section are exclusive to the Scalefusion MDM agent and will apply only if the Scalefusion MDM agent is chosen in the "Configure Encryption Agent" section of the BitLocker Base Settings.
Note:
These settings come in handy in cases where the device(s) might already be encrypted prior to enrollment in Scalefusion or in case you want to apply BitLocker policies from Scalefusion.
Decrypt and Re-Encrypt once using Scalefusion MDM Agent if the device is already encrypted: This setting will decrypt drives if they are already encrypted and then re-encrypt them. There are 3 options to choose from:
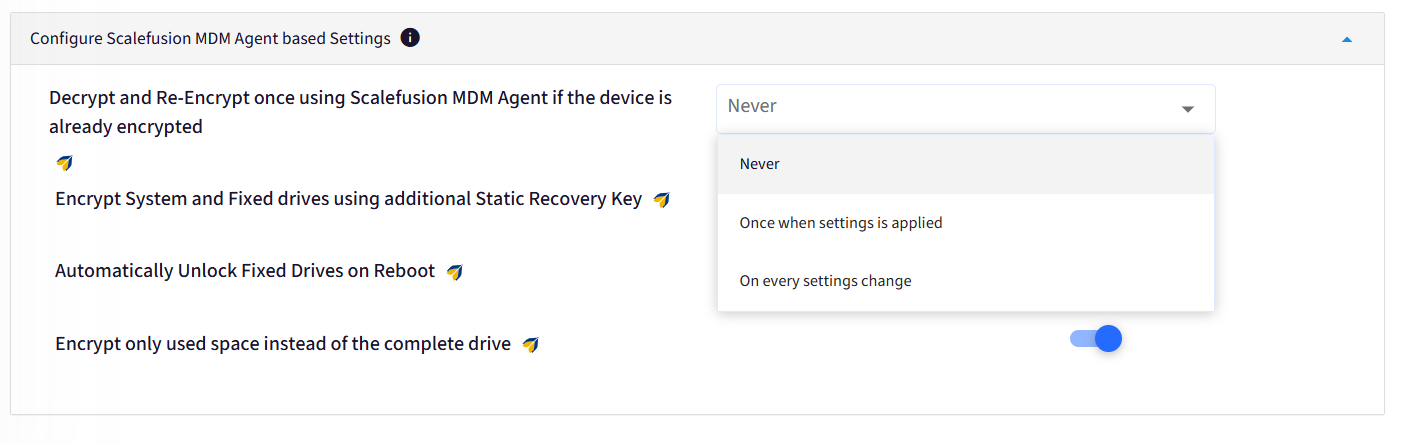
Never: This is selected by default.
If the device is already encrypted through any third-party BitLocker encryption method, and this option is selected, then the Agent-based Bitlocker settings will not apply to the device, that is, the device will not decrypt & re-encrypt. So if the device was previously encrypted via CSP it will remain so.
If the device is being encrypted for the first time, the Agent-based BitLocker settings will be applied on the device, meaning all the settings where the Scalefusion Agent logo is shown those settings will apply.
Once when settings is applied: If the device is already encrypted through any third-party BitLocker encryption method, and if this option is selected, then the device will decrypt and re-encrypt once.
On every settings change: If the device is already encrypted through any third-party BitLocker encryption method, and if this option is selected, then the device will decrypt and re-encrypt.
The device will decrypt and re-encrypt also when the “Encrypt only used space instead of the complete drive” option is enabled or disabled. Or, if there are changes in the “Configure Encryption methods” in the “BitLocker Base settings”.
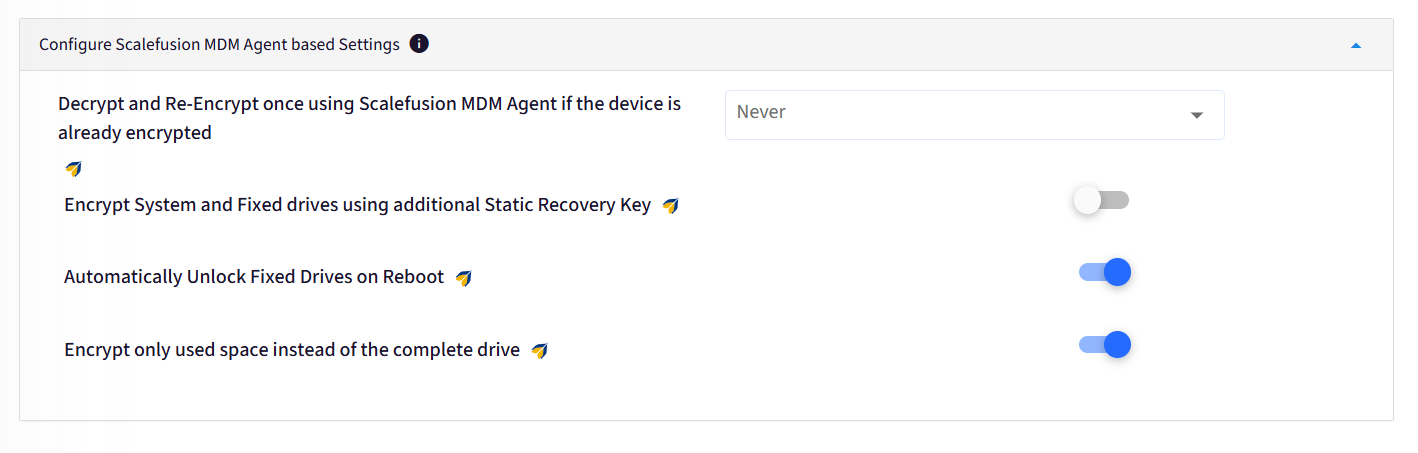
Encrypt System and Fixed drives using additional Static Recovery Key:
If this is toggled On then the Static Key will be forcefully applied to all the Drives.
If this is toggled Off then a different Recovery Key will be generated for each Drive and can be used to unlock the respective Drives.
Note:
Scalefusion generates a Static Key at Profile Level and it is stored in Full device information. This key will be constant through out the lifetime of a device while it is managed by Scalefusion and can be generated at any ONE of the triggers:
On Enrollment & Migration.
Or when BitLocker configuration is applied for the first time.
Automatically Unlock Fixed Drives on Reboot:
If this option is enabled then the fixed drives remain unlocked post reboot.
If it is disabled, then fixed drives will be locked post-reboot and to open them the user will have to use the BitLocker pin/password that they would have set during the encryption. This password and pin are also available on the dashboard > Devices > Full device information > Storage info > BitLocker Details for the concerned device.
Encrypt only used space instead of the complete drive: If this is turned On, only the used space on the drive will be encrypted. If it is turned Off then the whole drive will be encrypted.
Note:
If Fixed Drives are in Locked state then Agent based BitLocker Settings will not be applied on the particluar Drive. Hence it is recommend that you keep the Automatically Unlock Fixed Drives on Reboot turned On.
Once you have configured your BitLocker settings, click on Update Profile to save these settings. The changes will be automatically pushed to the devices where this profile is applied.
User Experience for BitLocker Setup on Device
On the device, users will see a pop-up dialog box asking them to set up a Pin and a Password.
If the user clicks on Later, the prompt reappears within 1 or 2 minutes. So unless the user enters the pin and password to encrypt the drives they will keep on getting the prompt.
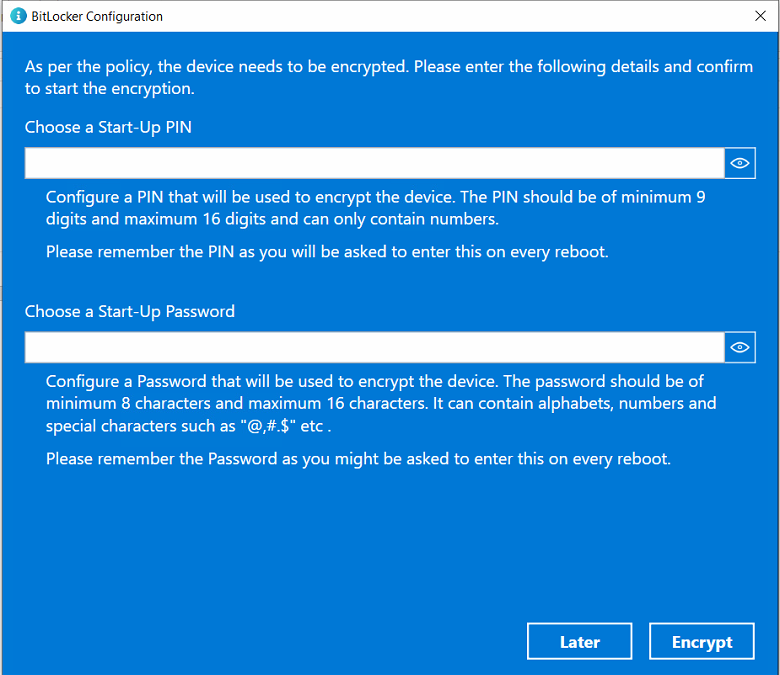
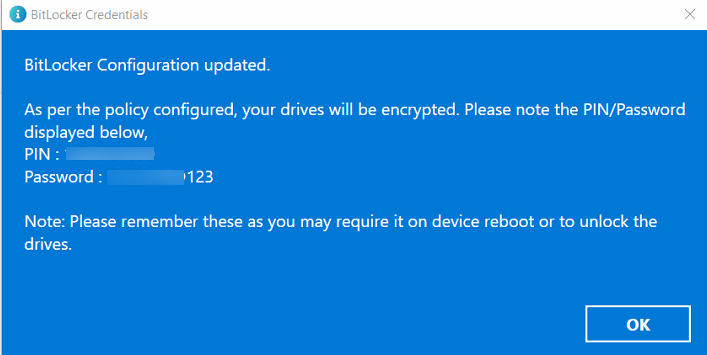
After setting Pin and Password click on the Encrypt button. The user(s) will see the BitLocker credentials as shown in the image below. They will need to save these as these will be required when a device is rebooted or to unlock the drives.
Behavior of Agent-Based BitLocker in Kiosk Modes (Single App Mode-Agent/Modern Managed (SAM-A/SAM-MM) & Multi App Kiosk Mode-Agent/Modern Managed (MAK-A/MAK-MM))
In this section, we have added a few known cases and the expected behavior of Agent-Based BitLocker in Kiosk modes.
Case 1: When SAM-A mode the behavior of the Agent-based BitLocker prompt is dependent on the application that is running in SAM-A mode.
Case 2: When SAM-MM mode is applied on the device the Prompt for Pin & Password set will not be displayed.
Case 3: When MAK-A mode is applied on the device, the Prompt for the Pin and password set displays correctly, but in some cases, it displays behind the apps and in other cases over the apps.
Case 4: When MAK-MM mode is applied then the notification icon of Prompt for Pin & Password set is displayed in the Task Bar (when Taskbar is allowed in MAK-MM).
In conclusion:
When MAK-A is applied on the device then BitLocker will work and a prompt will be shown to users. However, in the case of SAM-A, the behavior of the prompt depends on the application that is running in SAM-A mode.
In the case of MAK-MM, it depends on the setting of the Taskbar. In the case of SAM-MM, it will not work as the notification icon of Prompt will not be shown.
Other Points to Note:
There may be a case where the user is passwordless that is no password is set for the user login on the machine. In such cases, after the device has been encrypted, the BitLocker PIN/Password is available to users in the Scalefusion MDM Agent on the device.
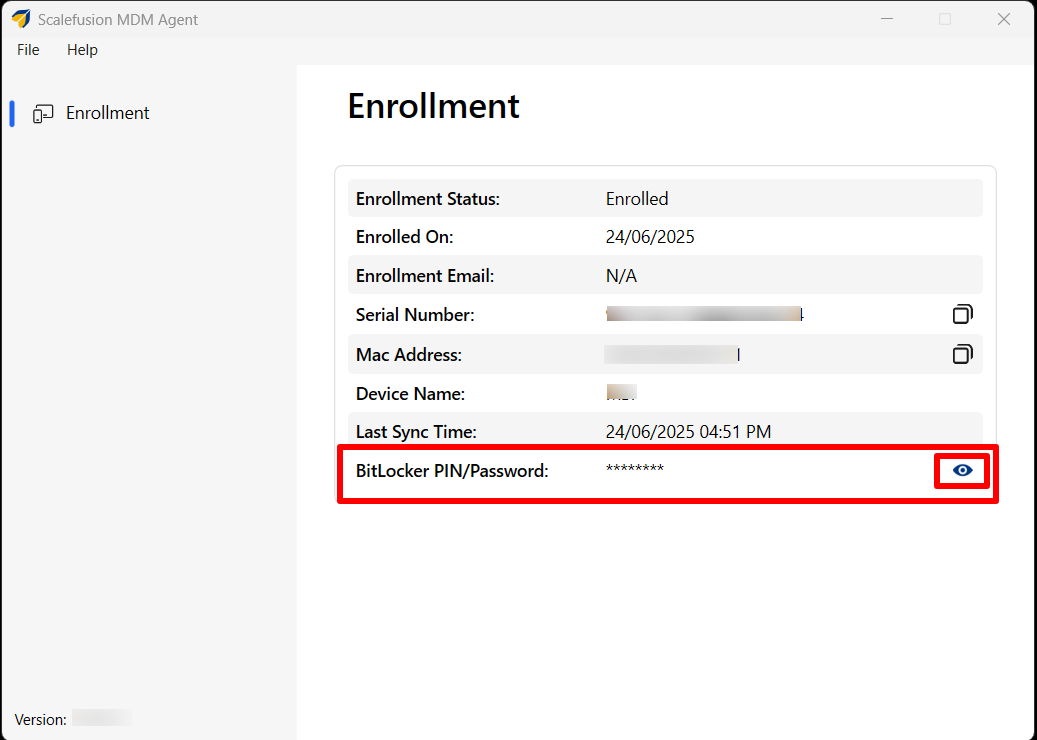
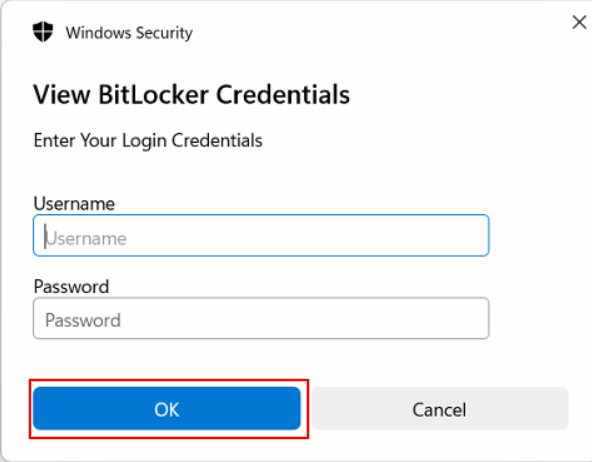
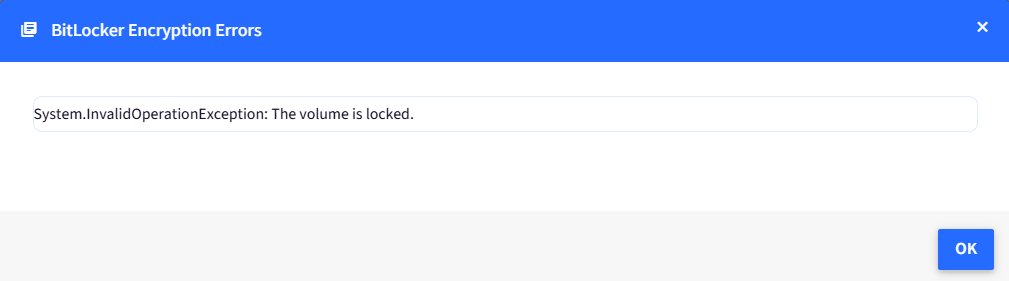
However, on clicking the "Eye" icon, the user will get the following user interaction dialog box where they will have to enter their machine’s login name and password.
As there is no password set, the user will click on Ok which will show the following error message.
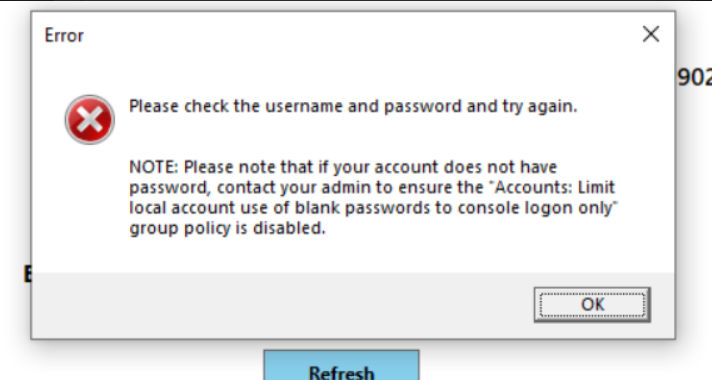
To avoid such kind of situation, we need to go to the Registry Editor > Local Security Policy > Security Settings > Local Policies > Security Options > Accounts: Limit local use account use of blank passwords to console logon only
and set the value for "Accounts: Limit local use account use of blank passwords to console logon only" to Disable.
Checking BitLocker status on the dashboard
You will find the details of the BitLocker status in the Full Device Information in the Devices section on the dashboard.
Navigate to the Devices section and click on the device name for which you want to see the status.
Click on the gear icon and then click on Full Device Information.
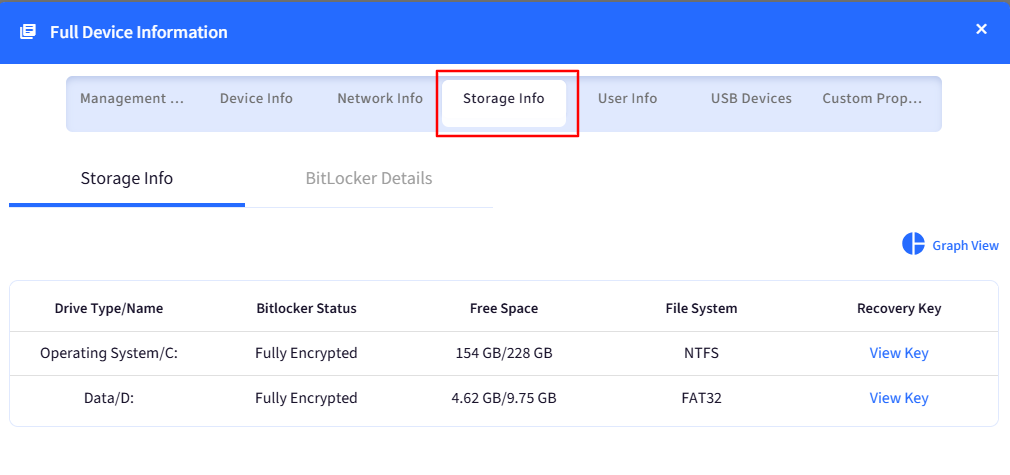
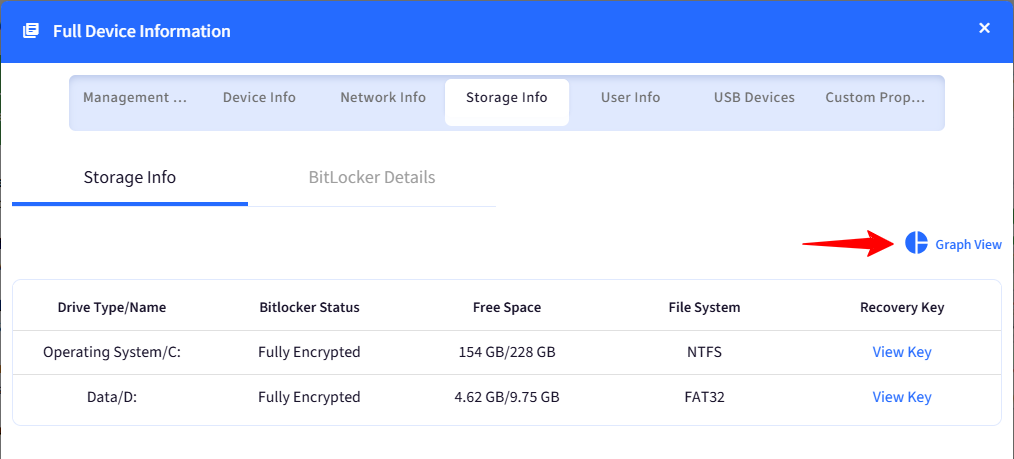
Go to the Storage Info tab. There are 2 tabs:
Storage info: It will show the Drive Type, BitLocker Status, Free Space, File System, and Recovery Key details.
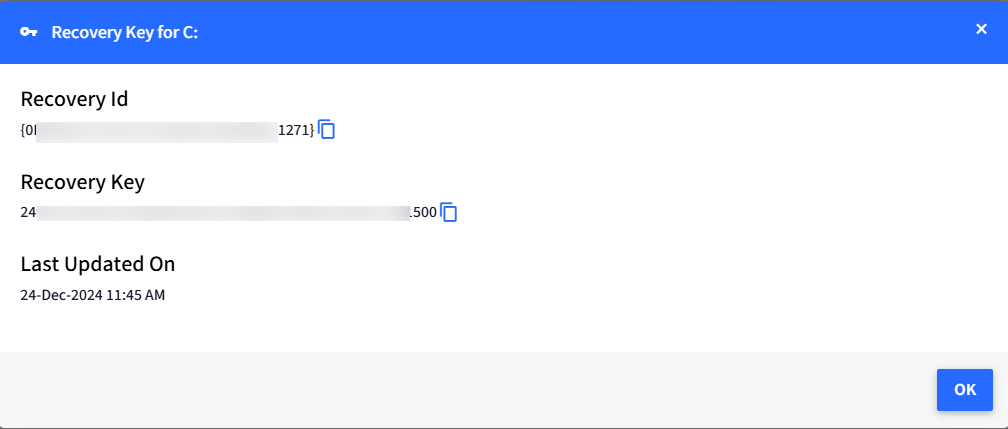
When you click on View Key under the Recovery Key, you will get a password dialog box to enter your Scalefusion dashboard password and click on the Submit button. This will show a pop-up dialog box with Recovery ID, Recovery Key, and Last Updated On details of the concerned Drive.
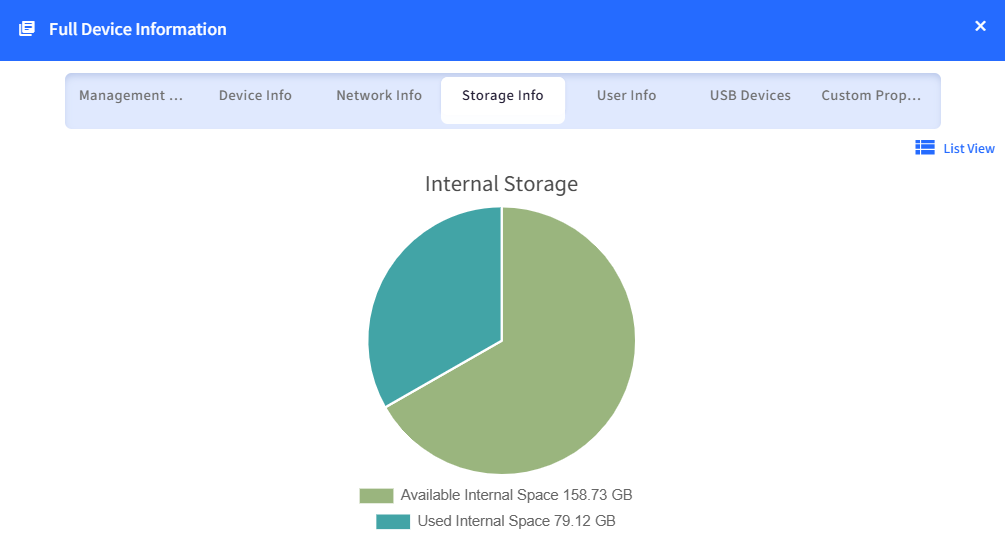
Graph view: This will show the available and used Internal space of the OS drive.
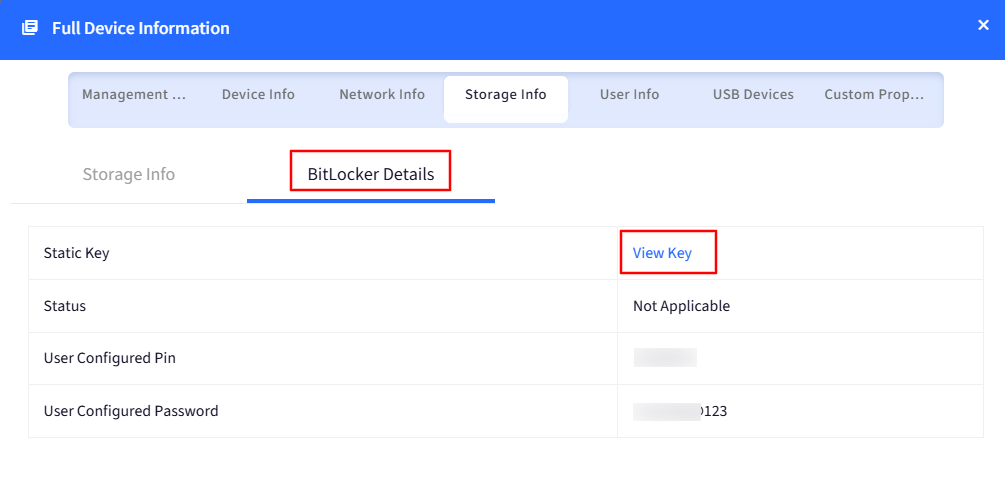
BitLocker Details: This section will show the following information:
Static Key: To view the key you will have to click on View Key. You will see a password dialog box to enter your Scalefusion dashboard password. Once done, it will show the Static key for that device.
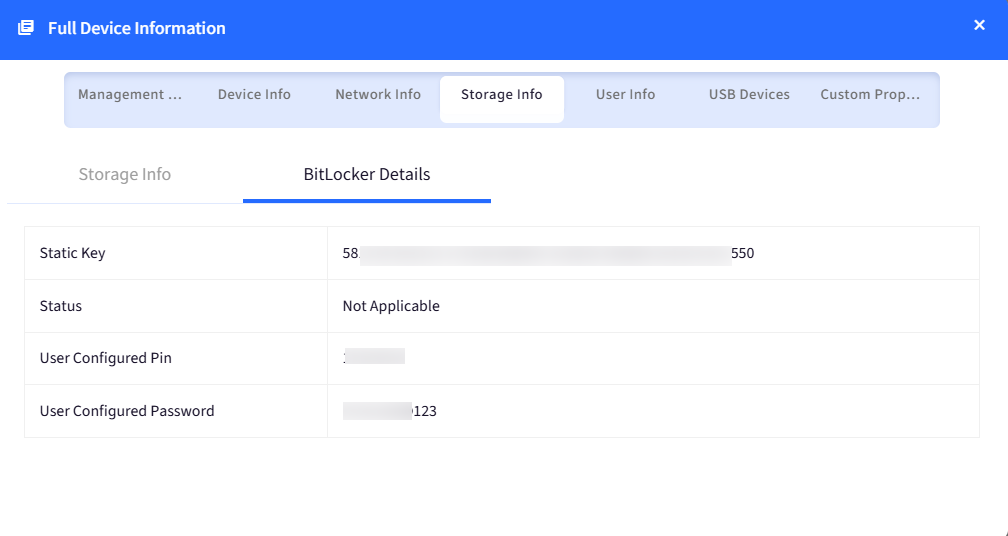
Status: It will show the status of the static key.
If it shows Not Applicable it means that the option “Encrypt System and Fixed drives using additional Static Recovery Key“ is disabled and the static key will not be applicable to unlock the drives.
If it shows as Enforced it means that the option “Encrypt System and Fixed drives using additional Static Recovery Key“ is enabled and the static key will be applicable to unlock the drives.
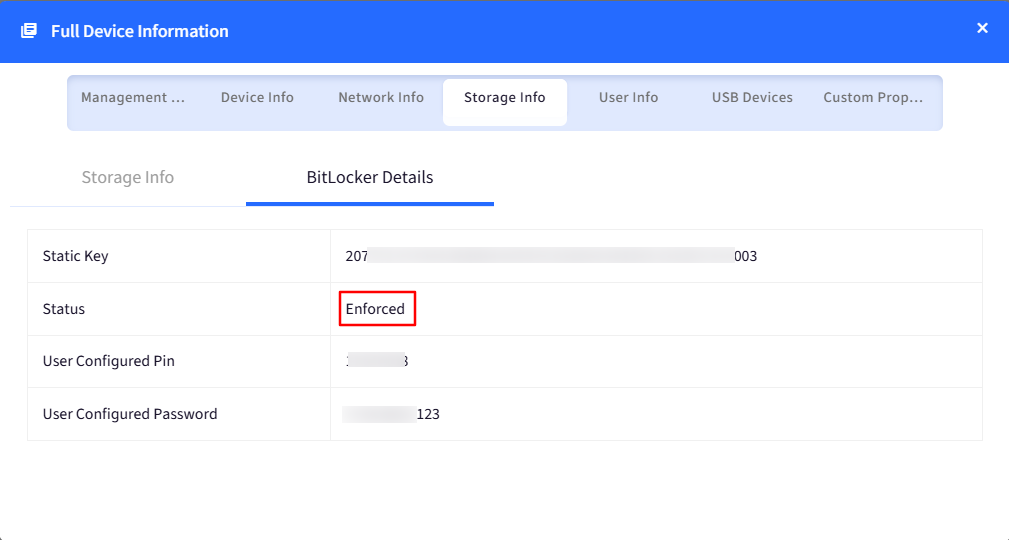
If it shows as Failed, it means that the option “Encrypt System and Fixed drives using additional Static Recovery Key” was turned On, however the drives that are there on the device are in Locked state. Click on the eye icon to see the reason for failure.
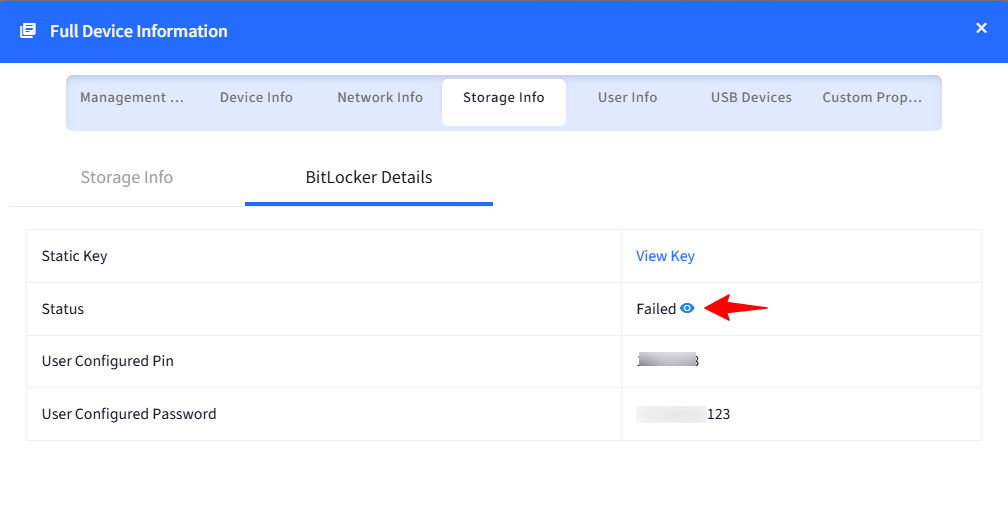
User Configured Pin: This will be the pin that user would have configured while encrypting the device via Agent-based Bitlocker settings.
User configured Password: This will be the password that the user would have configured while encrypting the device via Agent-based Bitlocker settings.
Note:
Please be aware that if you've configured a Passcode Policy on the dashboard under Device Profiles & Policies > Passcode Policy > Windows, and set the number of attempts in the "Configure max attempts to enforce Bitlocker recovery mode / Restart" option, the device will reboot into Bitlocker recovery mode once the user exceeds the allowed number of incorrect password attempts.
If you perform this action multiple times then there is a chance that OS can crash. Hence, it is recommended to set the "Configure max attempts to enforce Bitlocker recovery mode / Restart" option as Never in Passcode Policy if the BitLocker policy is also applied.
Limitations
A. LTSB
It is mandatory that the option Encrypt only used space instead of the complete drive must be enabled. This is basic BitLocker behavior.
B. Windows 8
The following 2 encryption methods are applicable for Windows 8 devices :
AES-CBC-128 bit
AES-CBC-256 bit
It is mandatory that Encrypt only used space instead of the complete drive must be enabled.