Microsoft Entra Conditional Access
Microsoft Entra Conditional Access (Azure AD previously) is policy-based service that allows organizations to implement conditional access and control access to their applications and resources based on certain conditions.
Microsoft Entra Conditional Access brings signals together, to make decisions, and enforce organizational policies. Conditional Access is Microsoft's Zero Trust policy engine taking signals from various sources into account when enforcing policy decisions.
Conditional Access policies at their simplest are if-then statements; if a user wants to access a resource/apps, then the assigned policy for the user should be matched with respective criteria in the policy.
How does Conditional access policy work?
Once the user logs in using Microsoft Entra (Azure AD previously) credentials to any cloud apps on Entra ID Joined (Azure AD joined previously) device and the device is a compliant as per corporation’s conditional access policies, then the user should be allowed access to use cloud apps without any blockage. On unenrolled devices if a user tries to access any cloud apps, then user access should be blocked, and the user will be asked to enroll the device.
Pre-requisites
Entra ID P1/P2 license for Entra ID is joined.
M365 E3/E5 license for Autopilot devices.
Devices should be joined to Entra ID and the Device compliant status should be shown as compliant.
To know more, please visit:
Steps to make this policy work with Scalefusion
Employing the Entra-based device enrollment provides a strategic avenue to implement Conditional Access (CAS) policies which guarantees that access to Office 365 apps is restricted to compliant devices, establishing a fortified barrier that safeguards sensitive data and promotes a secure digital environment.
Step 1 Integrate ScaleFusion dashboard with Microsoft Entra (Azure AD previously).
Step 2 Create a Conditional Access Policy in Microsoft Entra portal.
Step 3 Setting up Mobility (MDM & WIP) setting in Microsoft Entra portal.
Step 4 Enroll the device as Entra ID joined.
Step 1: Integrate ScaleFusion dashboard with Microsoft Entra (Azure AD previously).
Please refer to our guide here on how to set up Microsoft Entra on the Scalefusion dashboard.
Step 2: Create a Conditional Access Policy in Microsoft Entra portal.
Create a Conditional Access Policy in Microsoft Entra portal to enable access for applications only on enrolled devices by blocking unenrolled devices and to enforce users to enroll devices to get an access.
Navigate to Conditional Access > Policies > click on New Policy in the Microsoft Entra portal.
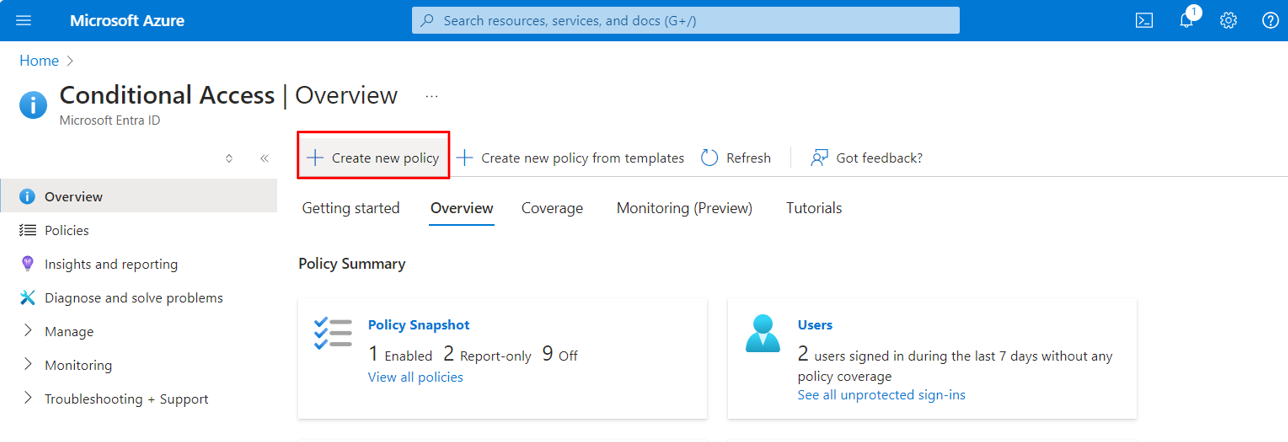
Enter the name of the policy.
Choose the users on whom you want to apply the policy.
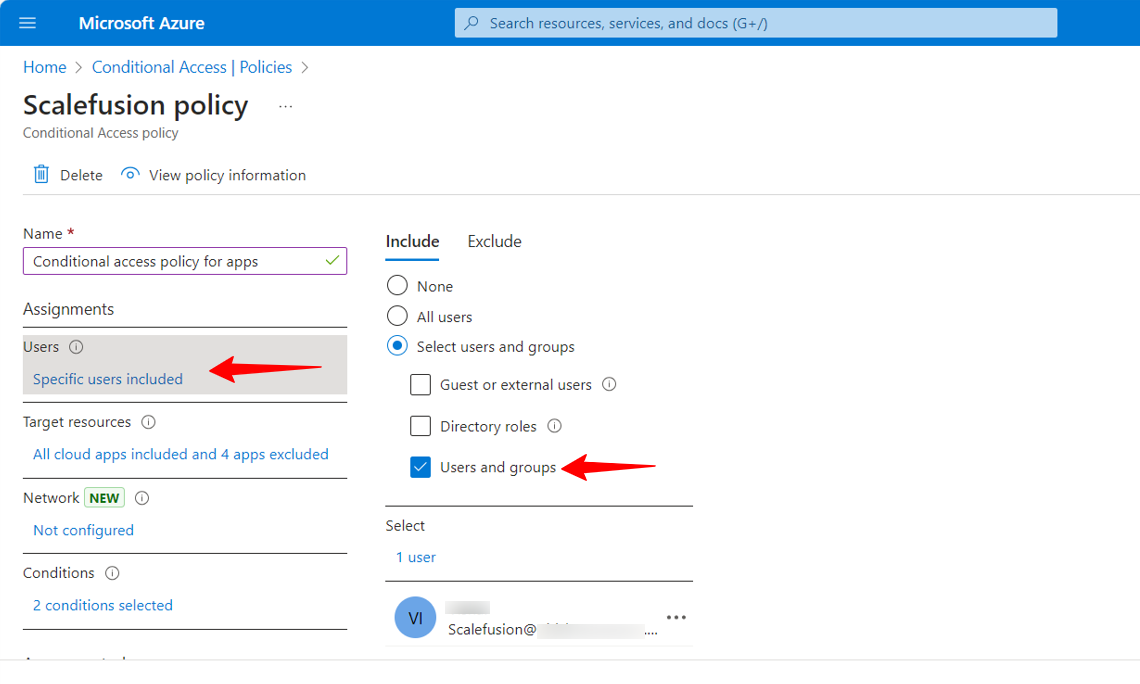
Select Target resources, meaning on which resources and apps you want to apply this policy.
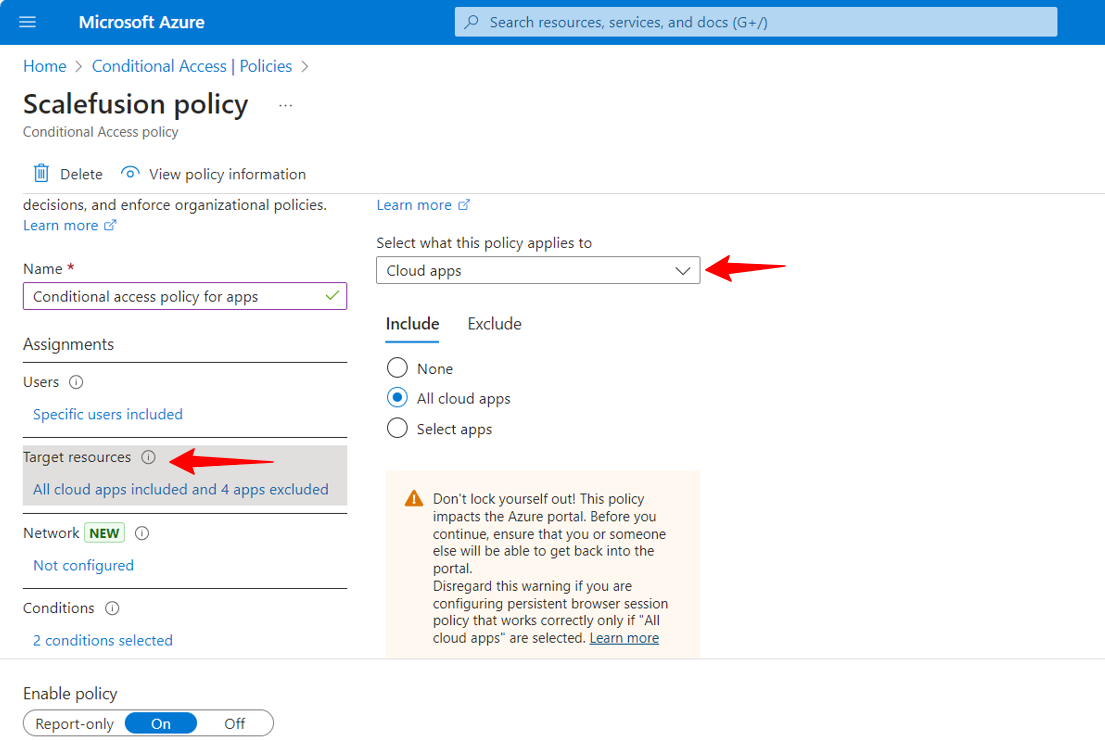
Policy can be applied on selected apps too, except those selected apps users will have access to use apps on both enrolled and unenrolled device.
For example, if you want to apply policy on both Outlook and MS Teams application, however, in the policy if you have selected only Outlook and not MS Teams then user can access MS Teams on any windows device whether it could be enrolled or unenrolled.
Please exclude the applications on which you do not want to apply policy. This is imperative for Scalefusion app.
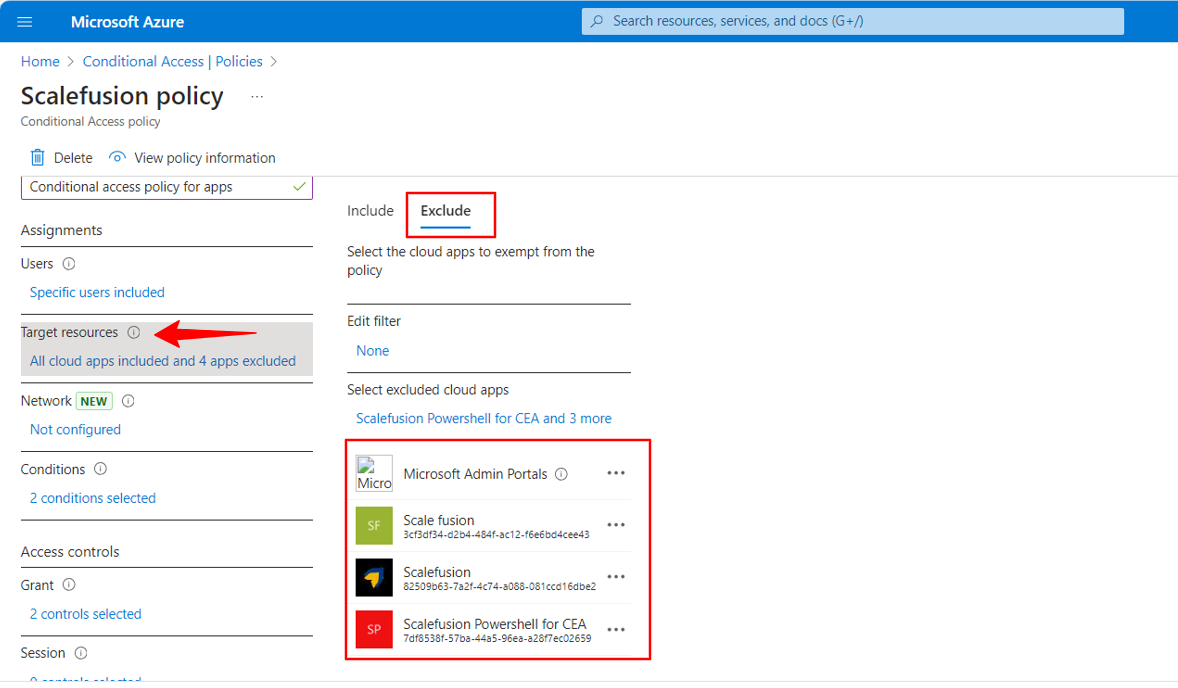
When Scalefusion MDM related apps are selected under the included list the device will face the issues while enrolling in Scalefusion MDM, hence, please exclude the Scalefusion app while creating the policy.
Define Conditions using which you can filter out the access for the users, for example, if users try to login to certain resources using web, client app or any desktop apps then the policy should apply for all these resources to validate and authorize users’ accessibility.
In the Device platform select Windows as the platform so that the policy is applied on Windows devices only.
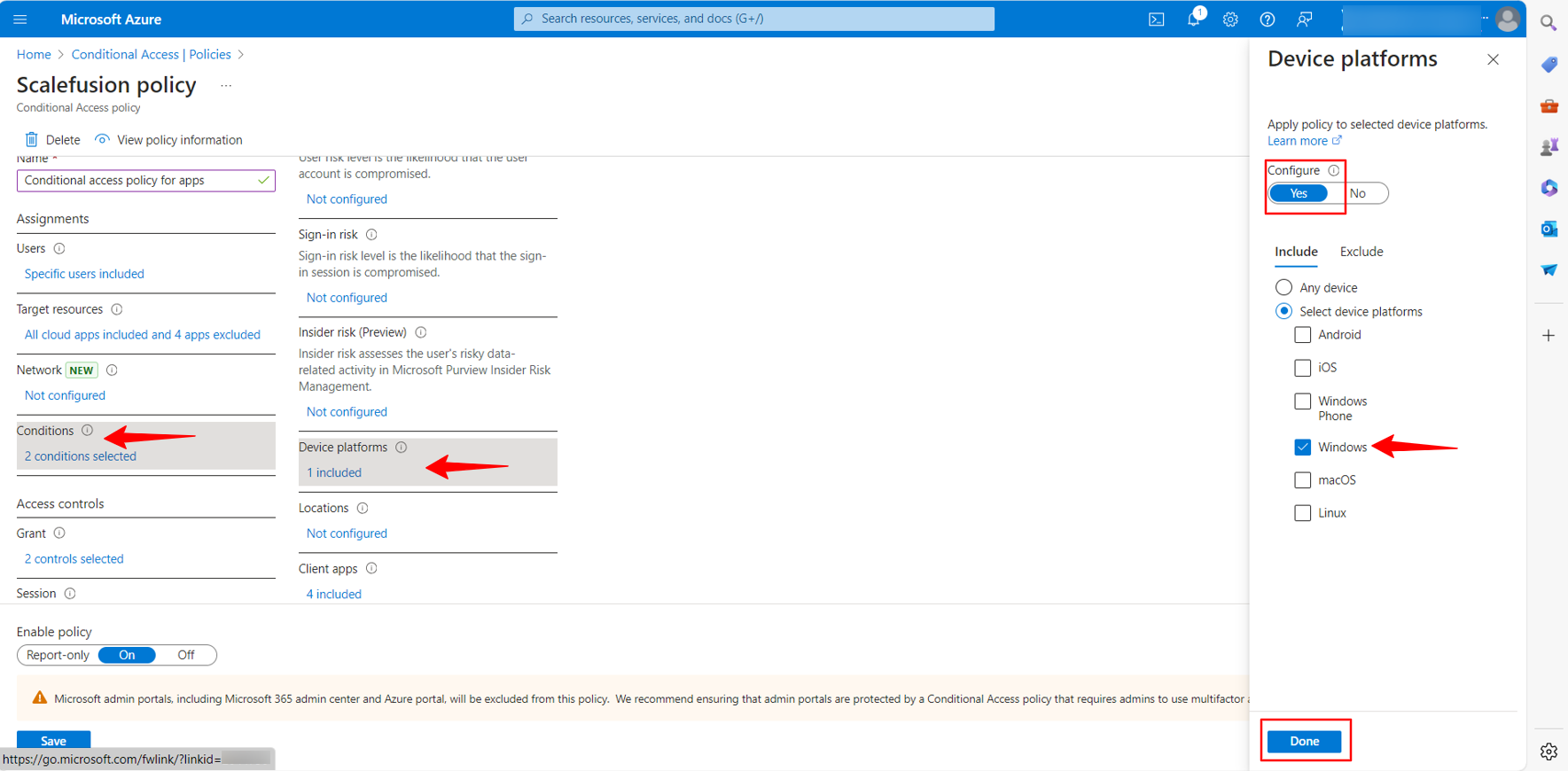
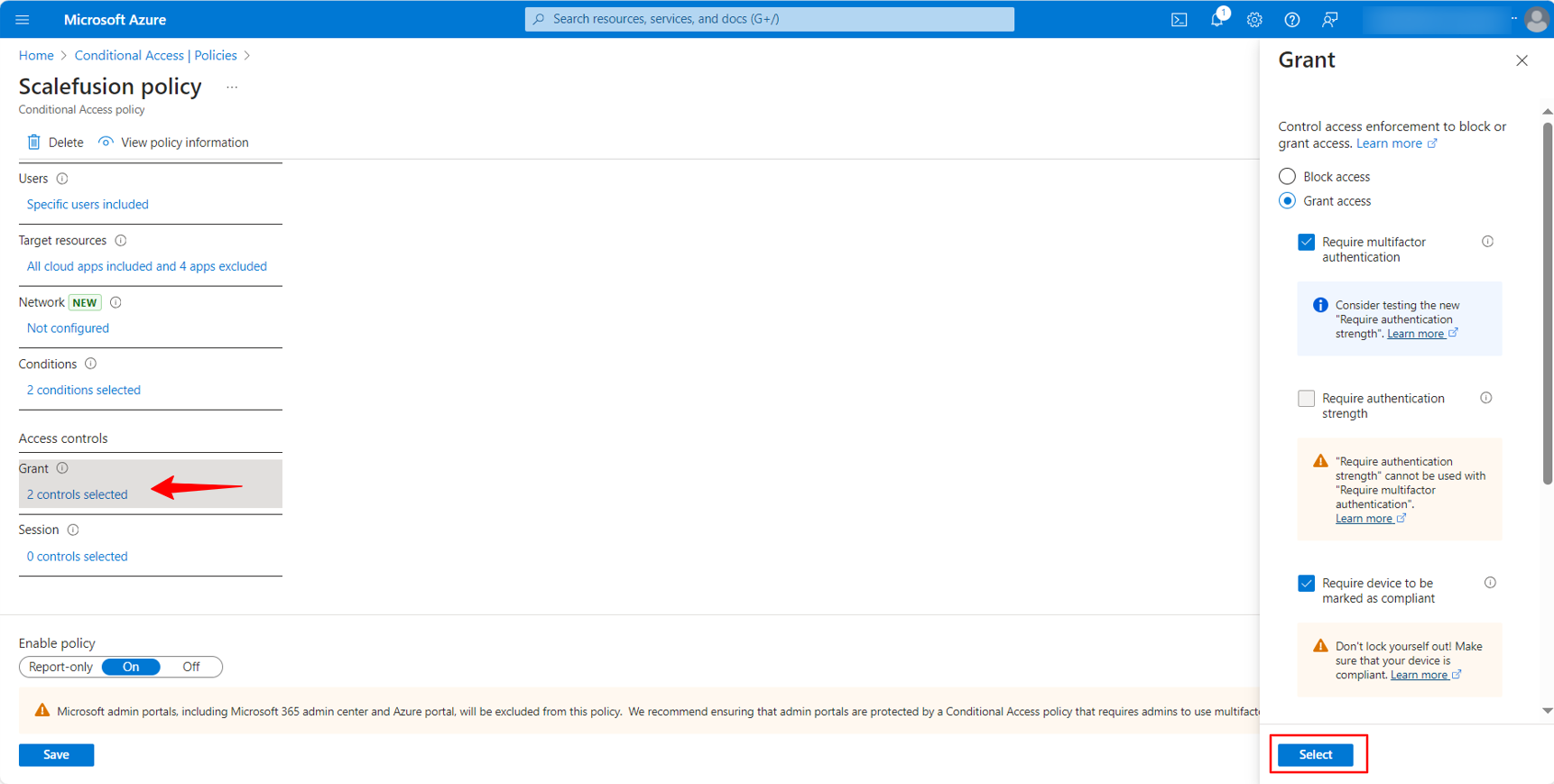
Access control: This setting will help to allow access to users based on the selected criteria.
In this section, select Require device to be marked as compliant, which means users will be able to access resources only when the device is enrolled to Azure as Entra ID joined and only if its device compliance status shows as compliant. If the device is not Joined or if it is not compliant then the policy should restrict the access of the user.
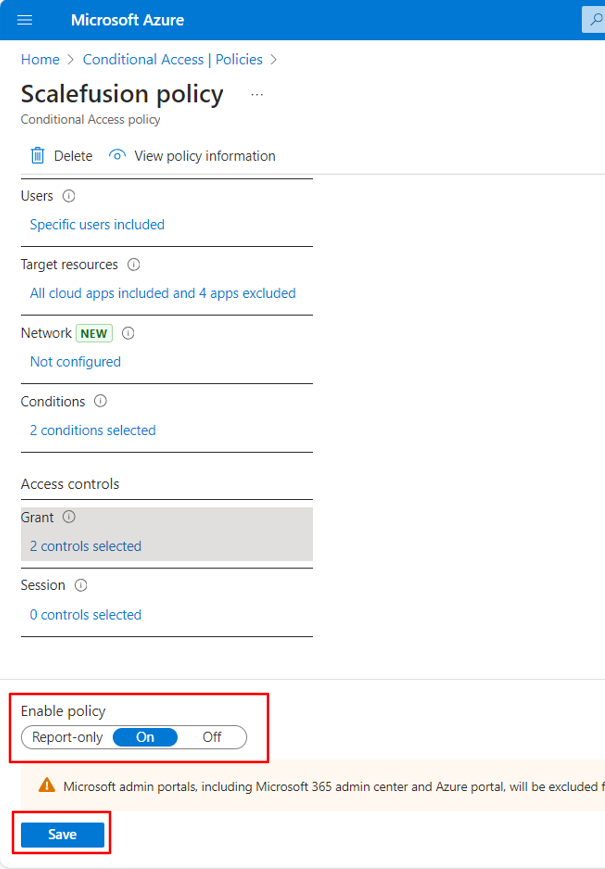
Enable policy should be set to On to make policy apply and save the policy.
Step 3 Setting up Mobility (MDM & WIP) setting in Microsoft Entra portal.
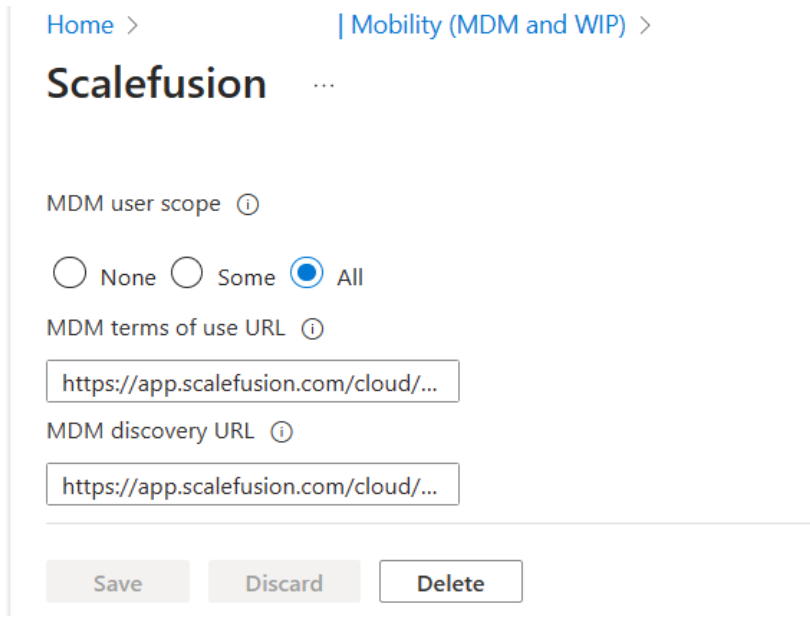
After creating the policy, make sure the Mobility (MDM & Wip) setting is set to All or Some for Scalefusion app.
Navigate to Navigate to Microsoft Entra ID > Mobility MDM & Wip > select Scalefusion.
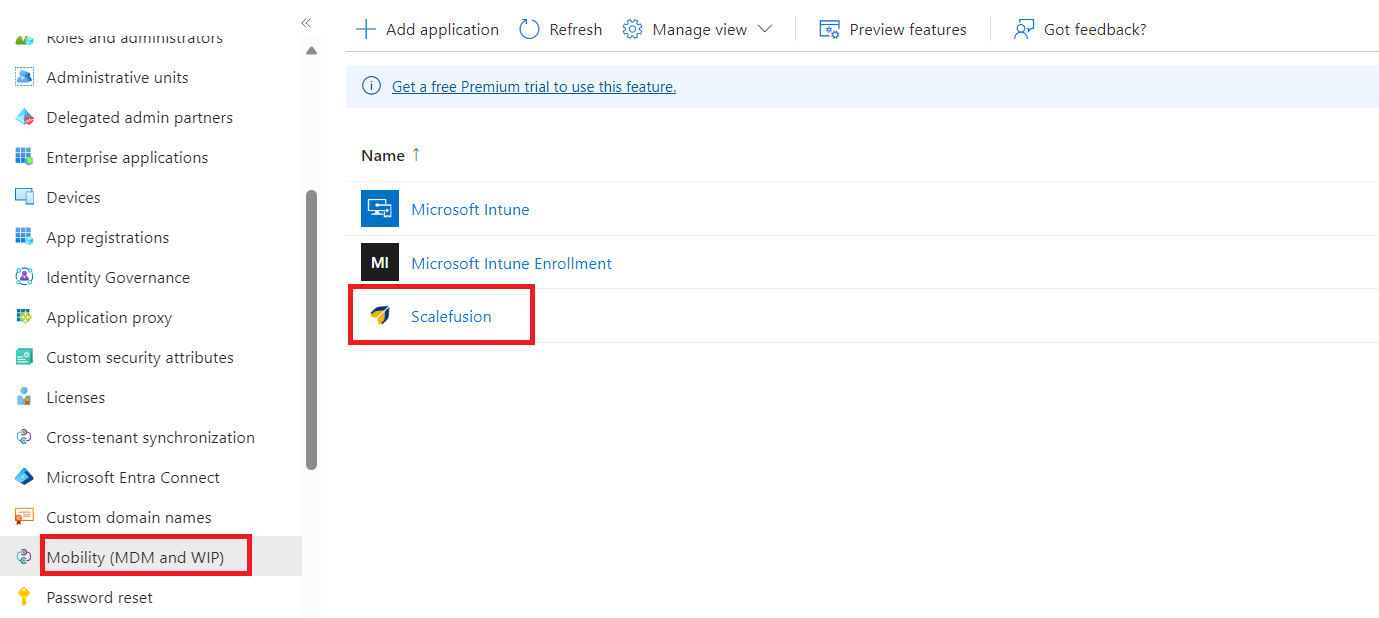
Select Some or All and click on Save.
Step 4 Enroll the device as Entra ID joined.
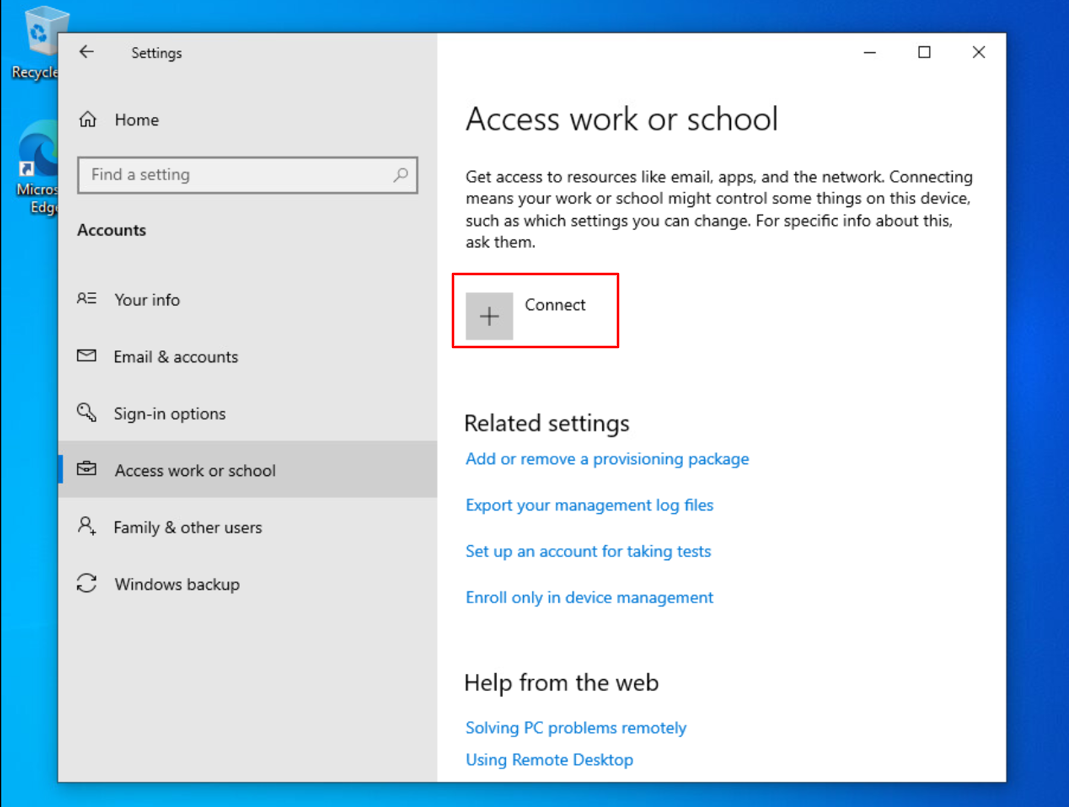
On the target device navigate to Settings > Access work or school account > Connect > Click on Join this device to Entra ID > Sign in > Join.
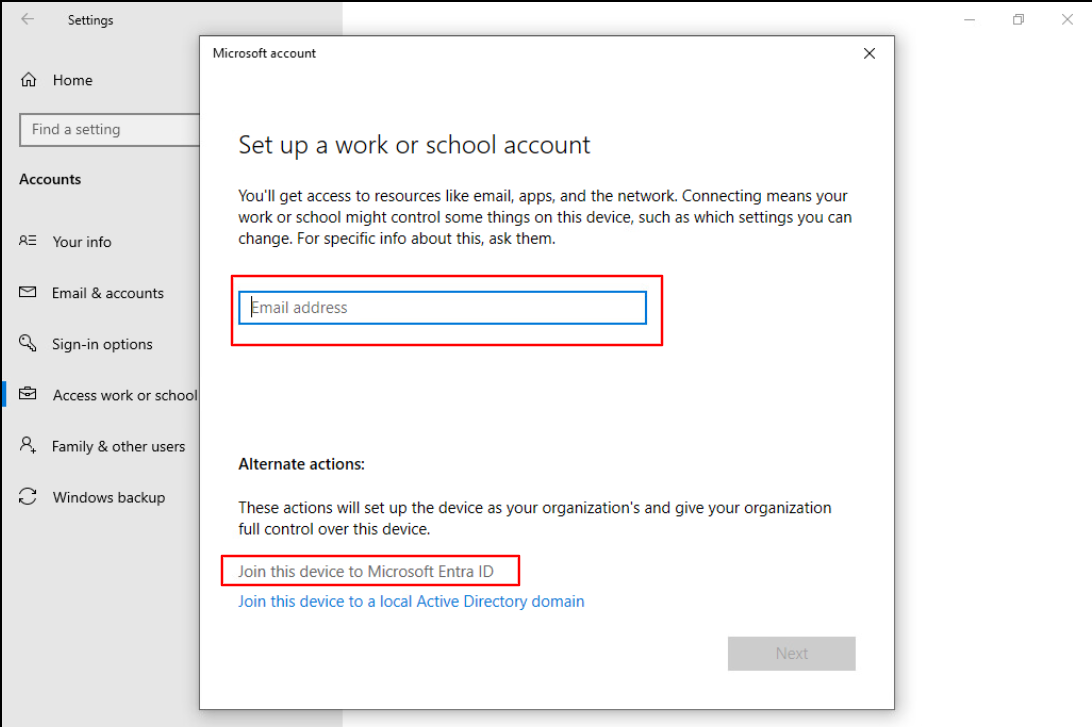
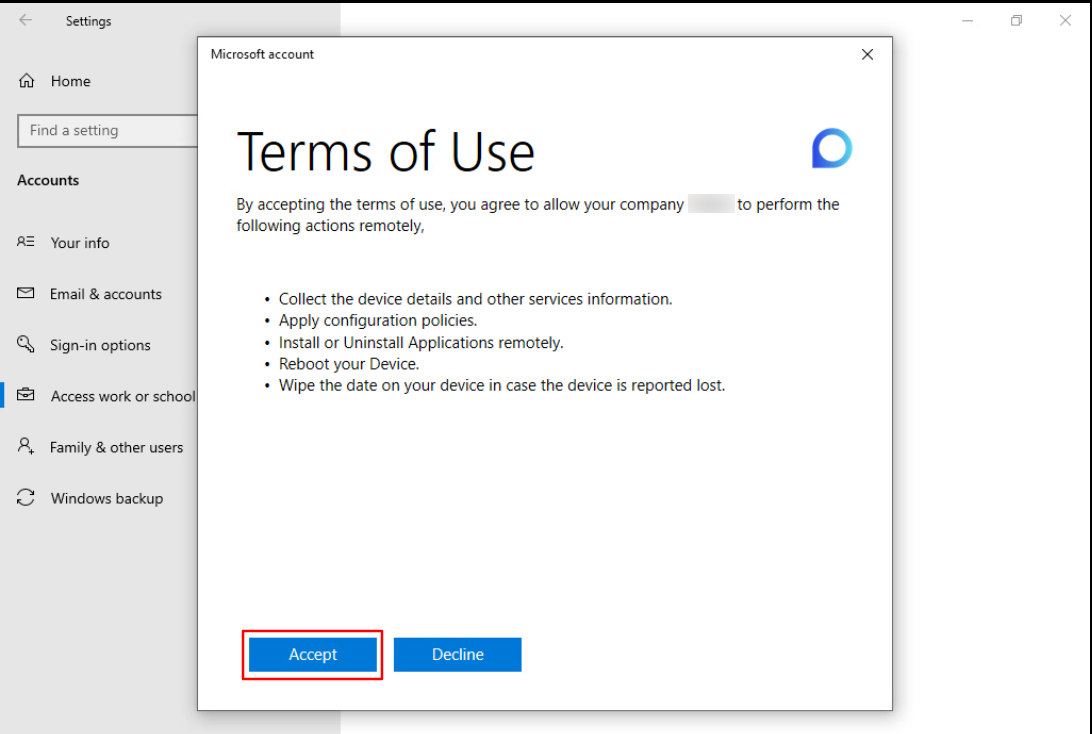
Accept the Terms of Use conditions of Microsoft and Join the device.
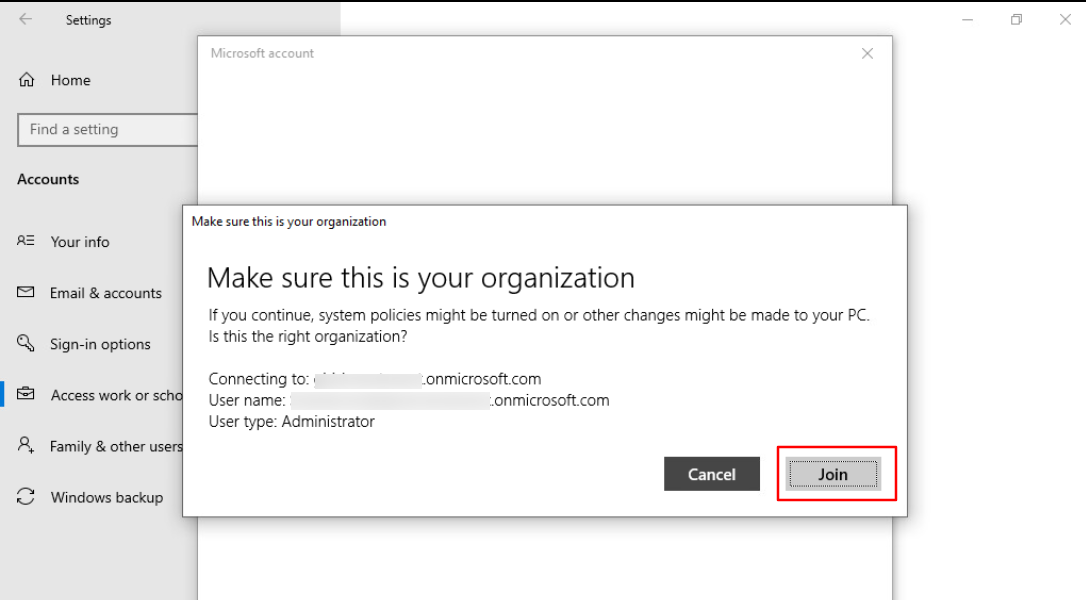
Click on Join to enroll the device.
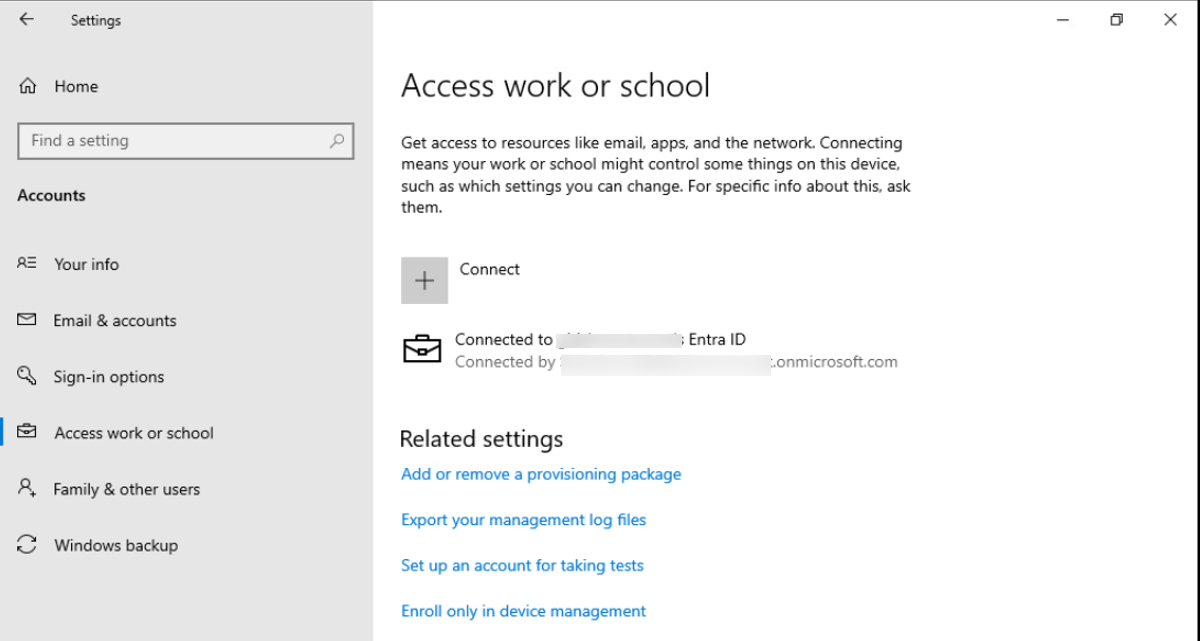
Once you enroll the device successfully, please sign in as Other user on the device.
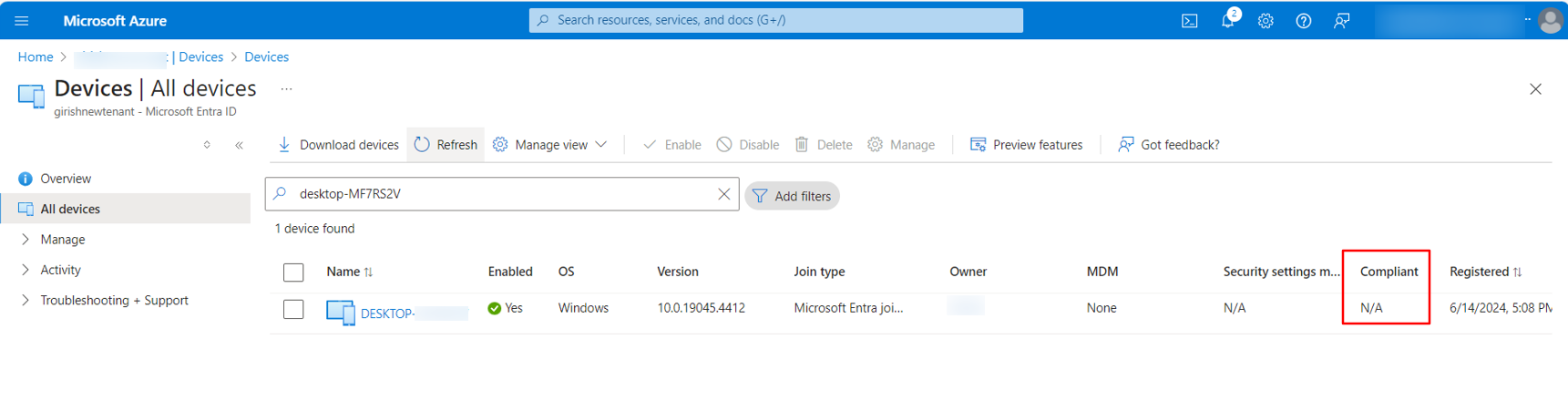
Until the User signs in as Other user the device compliance will be shown as NA on the Microsoft Entra portal.
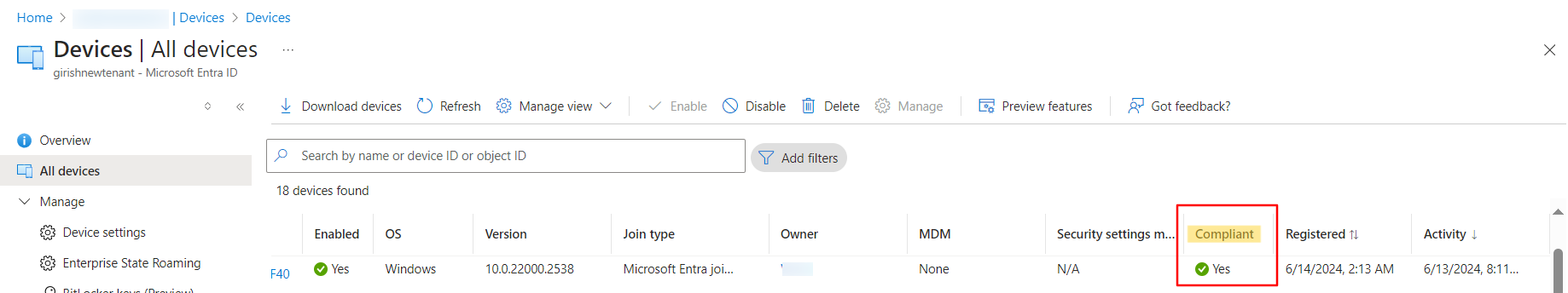
Once user sign in as Other user the device compliance will be shown as compliant and the user will be able to access the policy applied apps.
On the Device
When a user tries to login (on Entra ID joined device) to use teams/outlook, M365 or any cloud apps which is selected under the Included list of the Conditional access policy, it will allow the user access to those apps by Signing in automatically, as the user is trying to access resources on enrolled devices.
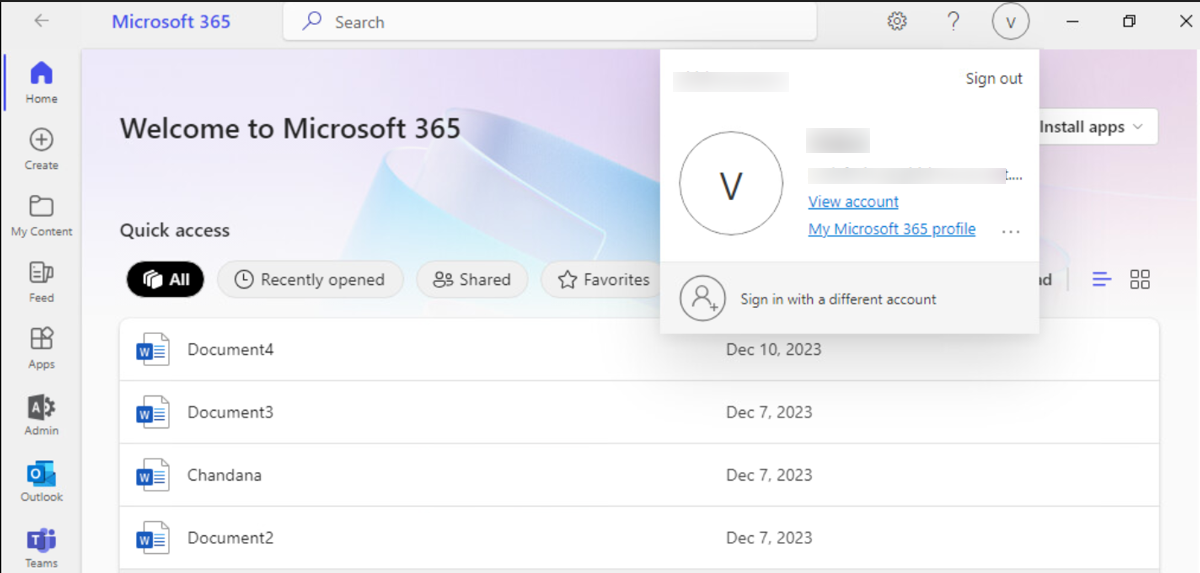
If the same user tries to access the same apps on an unenrolled device it will restrict the access and force the user to enroll the device as Entra Id Joined device.

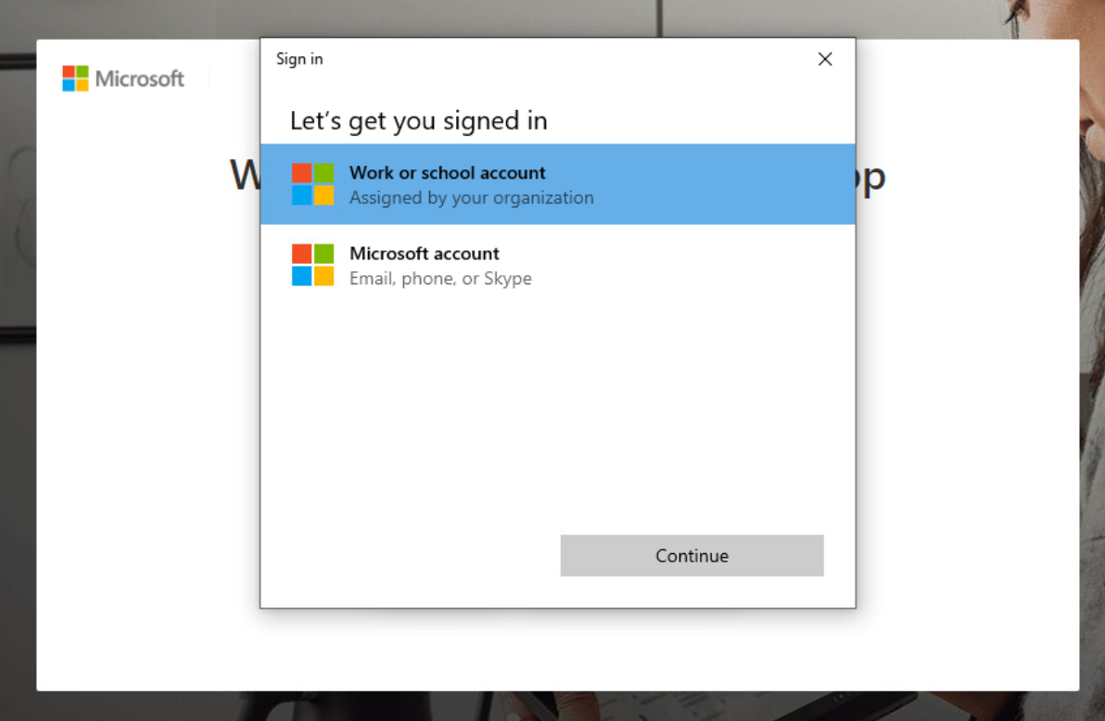
If the same user tries to login to an app using same credentials on non-Entra ID joined device will restrict the access and force the users to enroll the device.
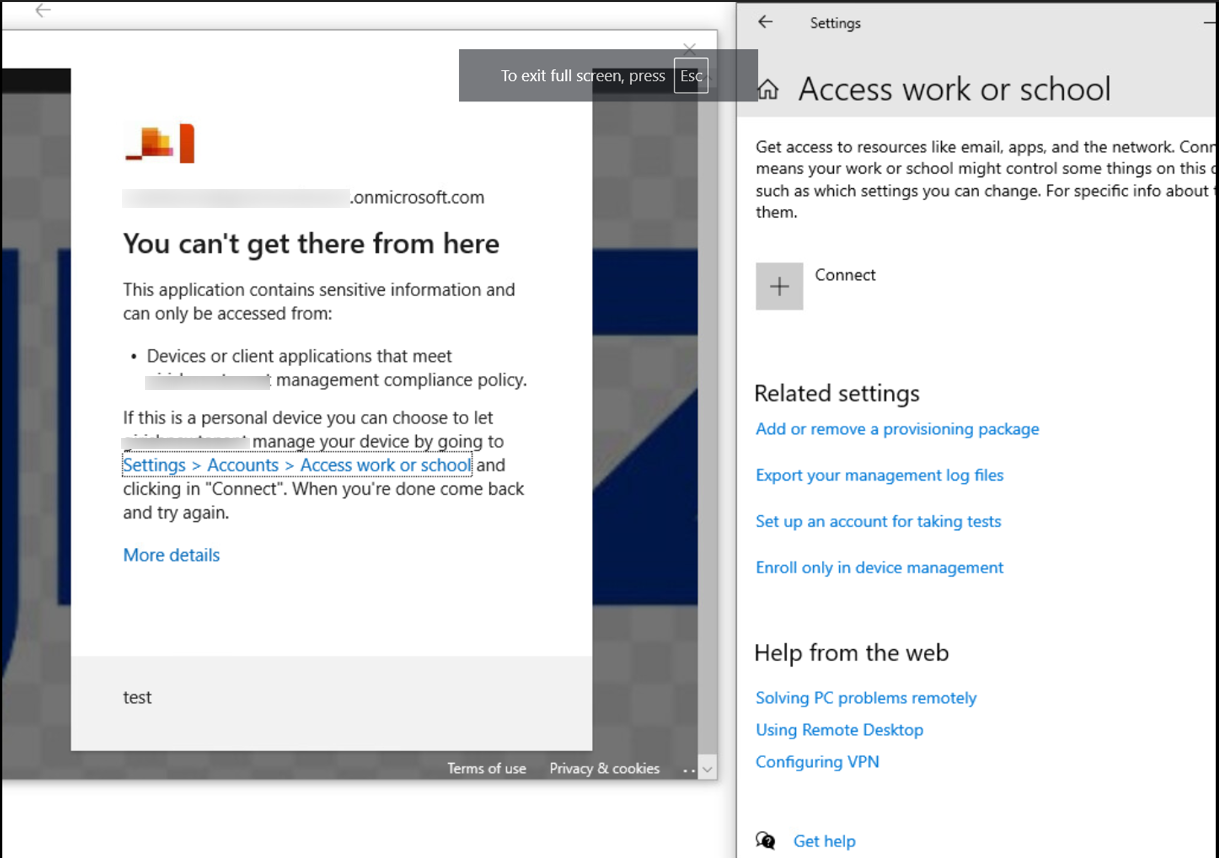
Note:
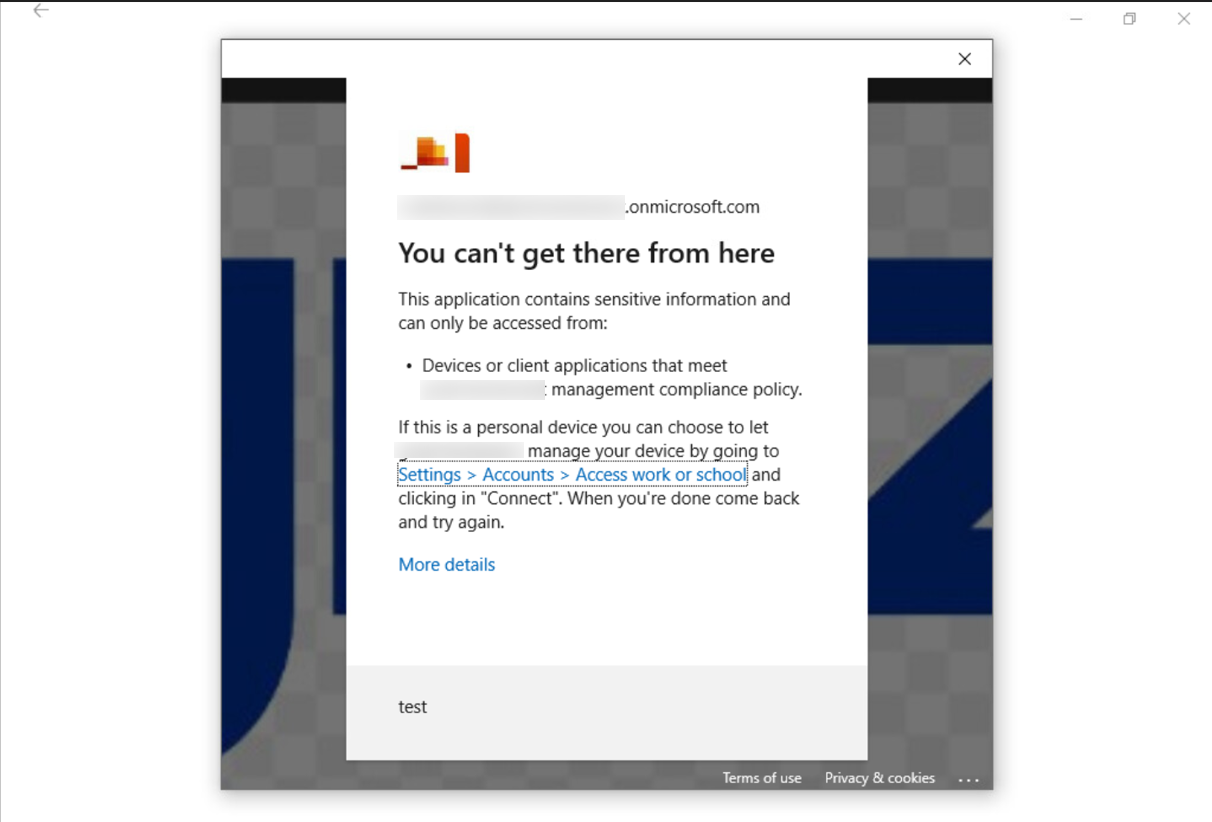
If user/Admin tries to enroll the device just by clicking on Connect instead of clicking on Join this device to Entra ID and then user tries to login into applications, they will see an error message as below and logging using Other User option will be disabled.
By leveraging the Entra device enrollment framework with Scalefusion MDM solution, organizations not only enhance their control over application access but also bolster their overall cybersecurity posture, aligning seamlessly with contemporary standards for secure device management and user authentication within the dynamic landscape of modern workplaces.