- 19 Feb 2024
- 9 Minutes to read
- Print
- PDF
Certificate Management for Android Devices
- Updated on 19 Feb 2024
- 9 Minutes to read
- Print
- PDF
Digital Certificates simplify the IT team’s task to authenticate devices and check for security when operating in unknown networks.
Utilizing a Mobile Device Management (MDM) or Enterprise Mobility Management (EMM) platform can further enhance the deployment experience of Digital Certificates on devices, as well as provide enterprises additional features and benefits of implementing security across devices.
Scalefusion, through Certificate Management, helps enterprises streamline the process of deploying Digital Certificates to end users' devices by automatically provisioning digital identities onto devices without end user interaction. You can enable authentication on managed Windows 10, iOS and Android devices using Scalefusion.
The document describes certificate management and how Standalone certificates can be applied on managed devices.
Types of Certificates
- Identity Certificate: These are the certificates that apps/browsers can use to identify the user and used for CBA (Cert Based Authentication). These are of typical .p12, .pfx formats
- CA Certificate: These are the certificates that verify the Trust of the certificate being presented. Can be of .cer, .pem and .der formats.
- Chained Certificates: Both 1 & 2 can contain a chain of certificate leading to a Leaf Node. That is the certificate payload/body can contain leaf certificate and the chain of issuing certificates.
Scalefusion Supported Certificates
Following types of certificates are supported under Scalefusion:
- PKCS12(.p12)
- PKCS1(cer, pem)
Supported Platforms.png)
Configure Certificate Settings
Step 1: Upload a certificate to Dashboard
To configure certificates that can be deployed to devices, follow these steps:
- On Scalefusion Dashboard, navigate to Device Profiles & Policies > Certificate Management and click on UPLOAD CERTIFICATE
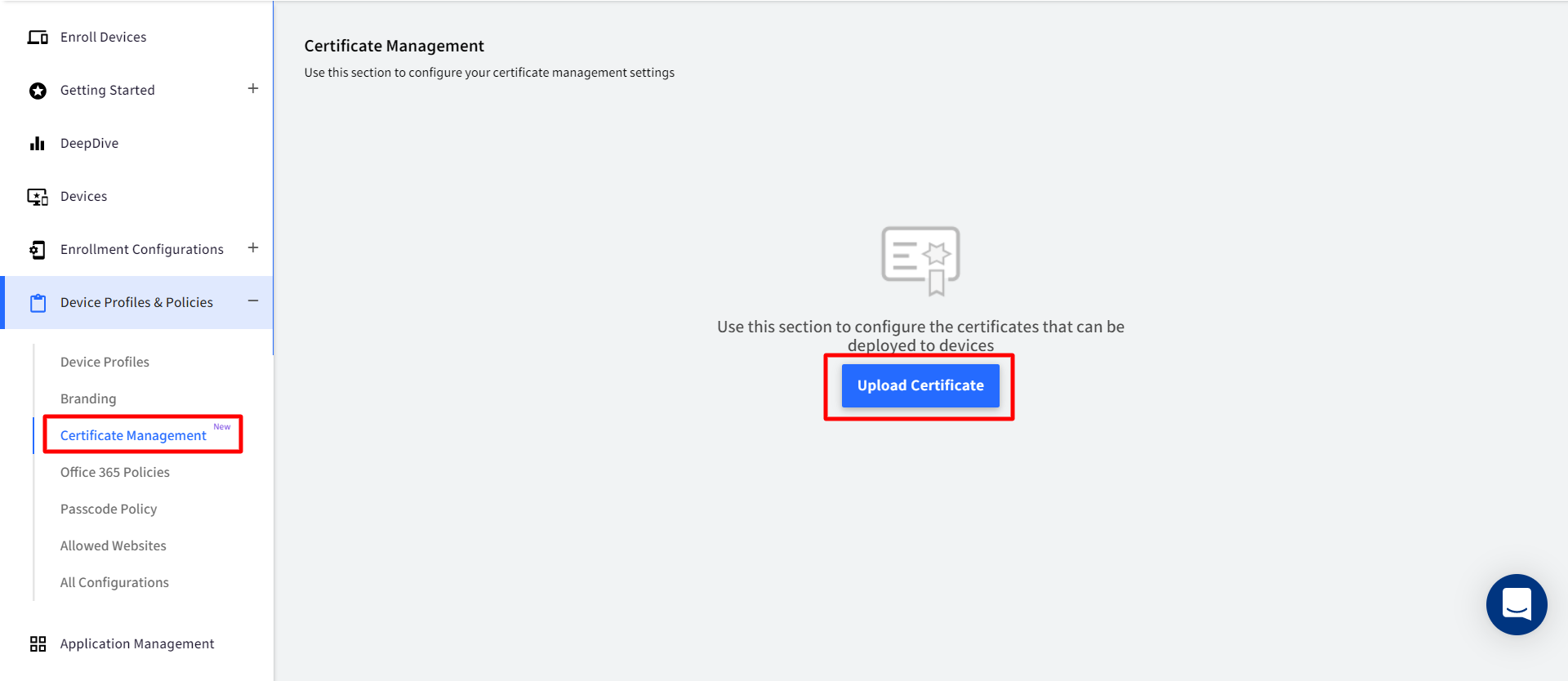
- This opens a new window Upload a Certificate
- Enter a name for the Certificate: Enter a display name for Identification purpose
- Upload Certificate file: Browse for the file and upload. Only .p12, .cer or .pem file formats are supported
- Enter an alias under which to install the certificate: Enter the alias name under which certificate should be installed. The alias cannot be left blank and should not be duplicate.
If the uploaded certificate happens to be .p12 or pfx that is an Identity certificate, following additional details need to be entered:
Enter a Password for the file: A key that encrypts the certificate
- Click SAVE after entering all details.
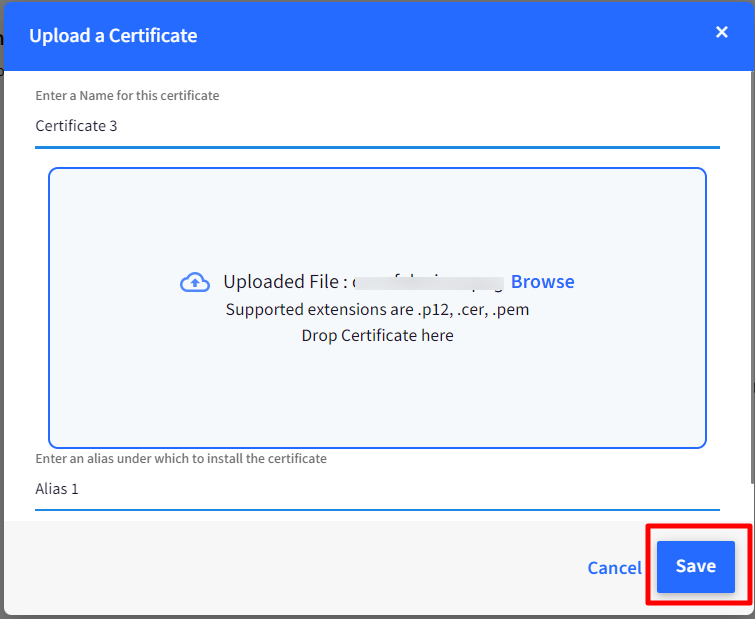
The uploaded certificate with details would be displayed on Certificate Management screen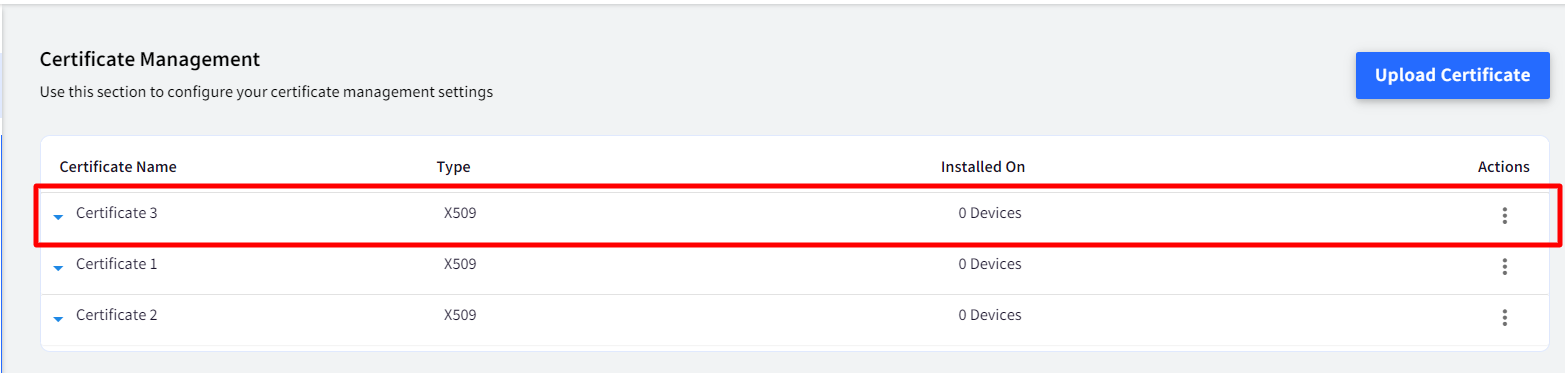
Step 2: Apply Certificates to Device profiles / devices
Once certificates are uploaded, they need to be pushed to device profiles / devices. This is done through Publish under Actions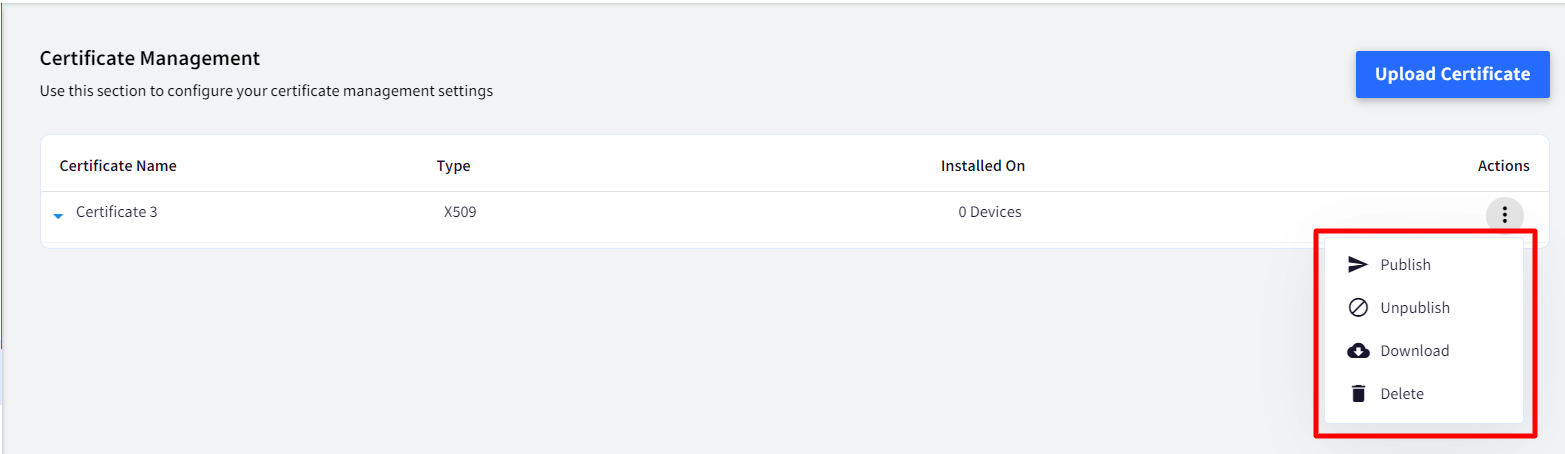
To install certificates on Android devices below OS 9, a password policy needs to be set and applied on the Device Profile(s)/Devices. On devices with OS 10 and above, password policy is not required.
Please navigate to Enterprise > Passcode Policy and apply a password policy before publishing certificates. The password type should only be Numeric, Alphabetic, or Alphanumeric
- Publish: Publishes certificate on selected device profile(s) / device(s). To publish,
- Click on Publish under Actions, in front of the certificate that has to be published. This opens a new window containing list of iOS, Windows and Android device profiles and devices configured on Dashboard.
- Select the device profiles / devices on which the certificate has to be published and click PUBLISH.
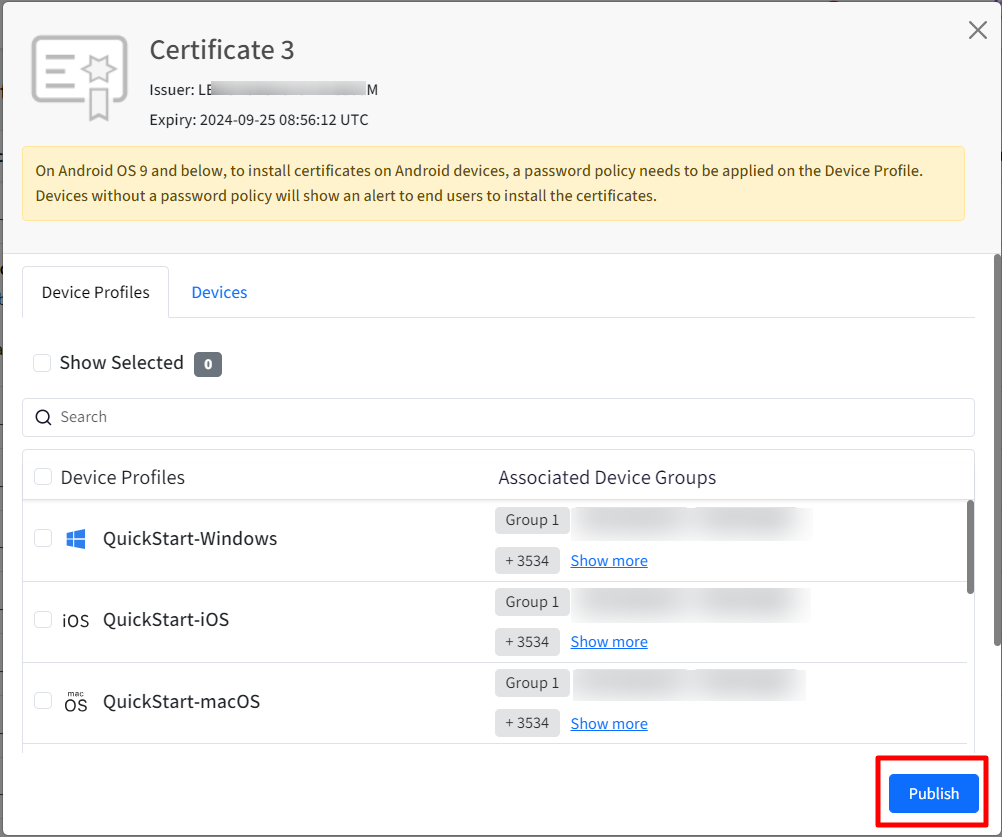
The certificate will get associated with the device profile / device.
Installation of Certificates on Devices (OS9 and below)
- On EMM Managed BYOD or Corporate Owned Devices (below OS 9), if PIN or password is not set on the device, the certificates published from dashboard are visible in Certificate Manager. You need to setup PIN / password on the device first and then the certificates get installed on device.If device PIN or password is already set, the certificates get installed silently on clicking Publish on Scalefusion Dashboard.

- On devices with Legacy Management mode, you need to manually install the certificate on the device. To do so,
- Tap Certificate Manager

- Tap on Install button in front of the certificate
- Tap OK (You can rename the certificate here if required).
- Tap Certificate Manager
The certificates get installed on the device.
When a certificate is installed on device, the count of devices (for the certificate which is published) reflects under Installed On heading on Certificate Management screen on the Scalefusion Dashboard.
Certificates can also be published via Device Profiles section. Navigate to Device Profile > Restrictions > Certificates tab. All the configured certificates are listed here and admin can select the ones that have to be associated with this profile.
Other Actions on Uploaded Certificates
- Unpublish: Unpublishes certificate from the device profiles / devices. To Unpublish,
- Click on Unpublish under Actions, in front of the certificate that has to be unpublished. This opens a window containing list of all the device profiles and devices on which certificate is already published.
- Unselect the profiles and devices and click the button UNPUBLISH. The certificate will get uninstalled from the device(s) / device profiles.If a certificate has been published to Device Profile and Device separately and if it is unpublished from the device profile, then the certificate is still retained on the device as it has been installed on Device also.
- Delete: Deleting a certificate will uninstall the certificate from all devices and delete the stored certificate. Clicking Delete will show a Dialog for Confirmation "This Certificate is currently installed on the XX Device Profiles and used in XX Wifi Configurations? Are you sure you want to delete?"
The confirmation dialog appears only if the certificate is pushed else a simple confirm dialog box appears.
Additional Features
Expanded view of a Certificate
Clicking on down arrow before certificate name shows the expanded view of it. A certificate payload/file can be a single certificate or a chained certificate. Depending upon the same the expanded view shows up:
- Single Certificate: Shows the Issued By, Expiry and Key Usage
.png)
- Chained Certificate: Expanded view displays a List view and selecting each certificate displays its properties. A certificate in the chain can be,
- Root CA Certificate (is usually self-signed and hence no Issued By information is available)
- Intermediate CA Certificate (there can be n number of Intermediate CAs in a Certificate Hierarchy, usually it’s just one. Displays Issued By, as the intermediate CA certificate can be issued by another intermediate CA in the chain above or Root CA)
- Leaf Node Certificate (Displays Issued By which can be an Intermediate CA and extremely rarely the Root CA)
.png)
Where are the Certificates stored after installation
On EMM Managed Android devices,
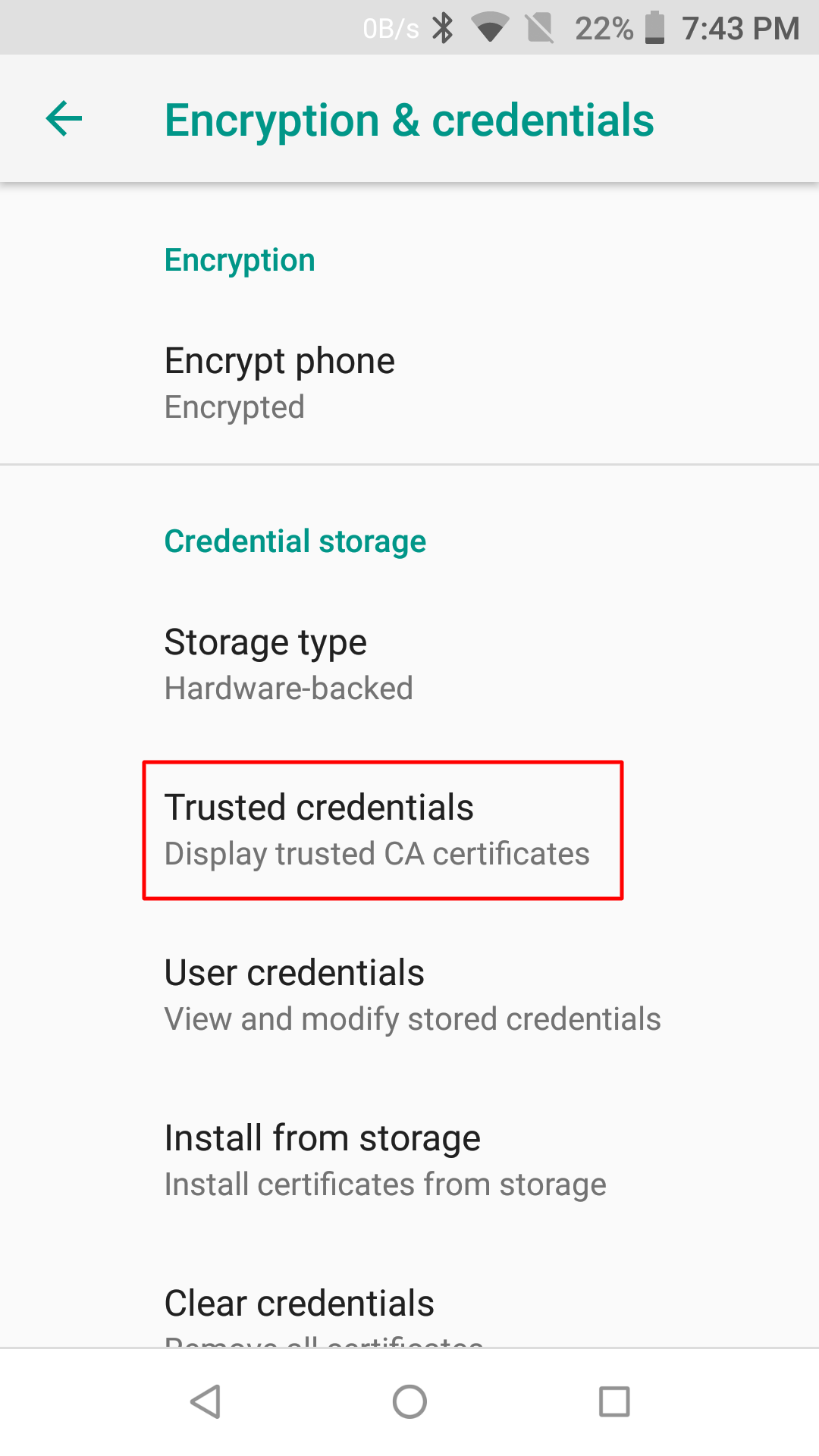
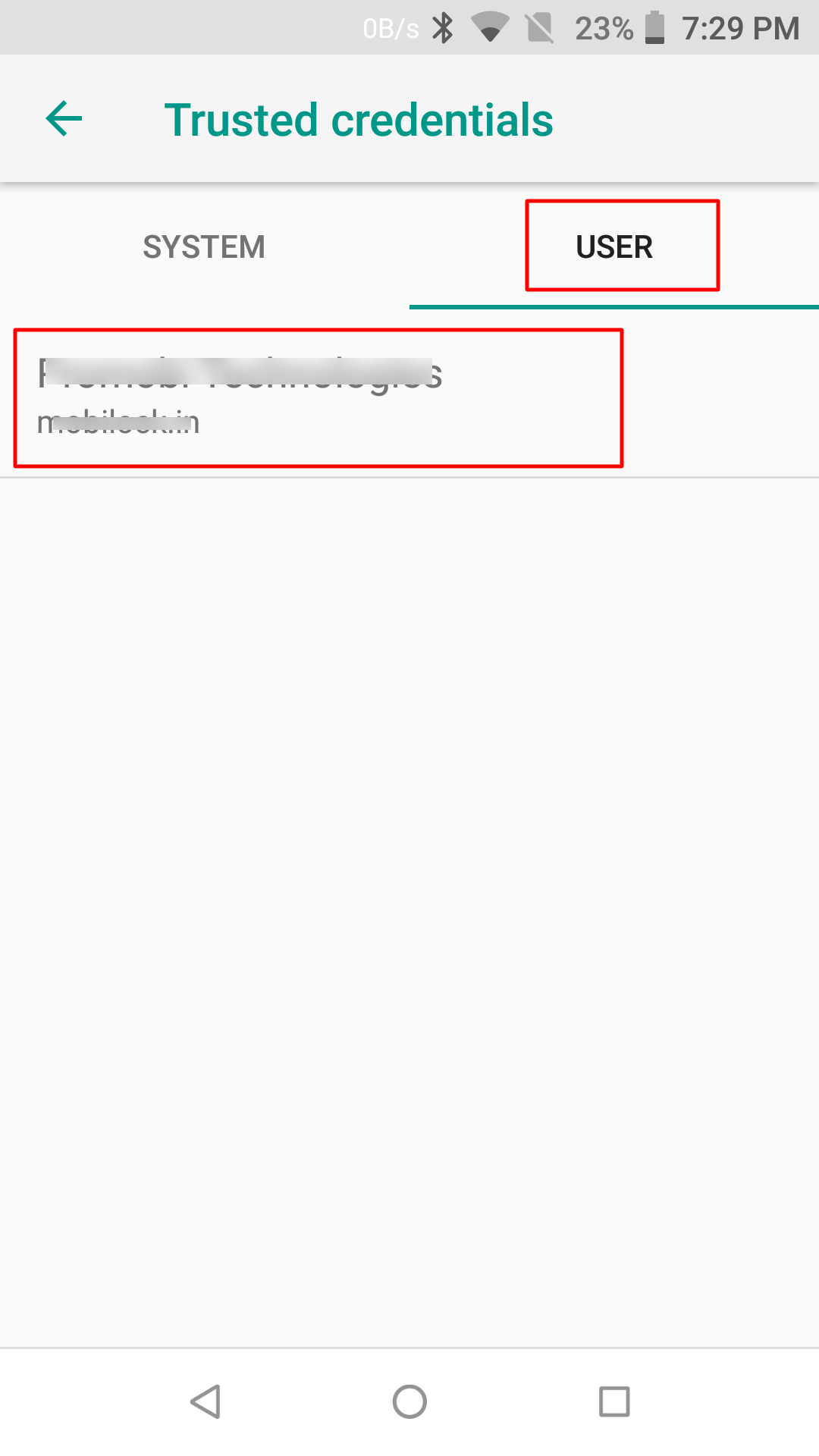
- CA Certificates are stored under Settings > Security & Location > Encryption & Credentials > Trusted Credentials > UserThe path is device specific
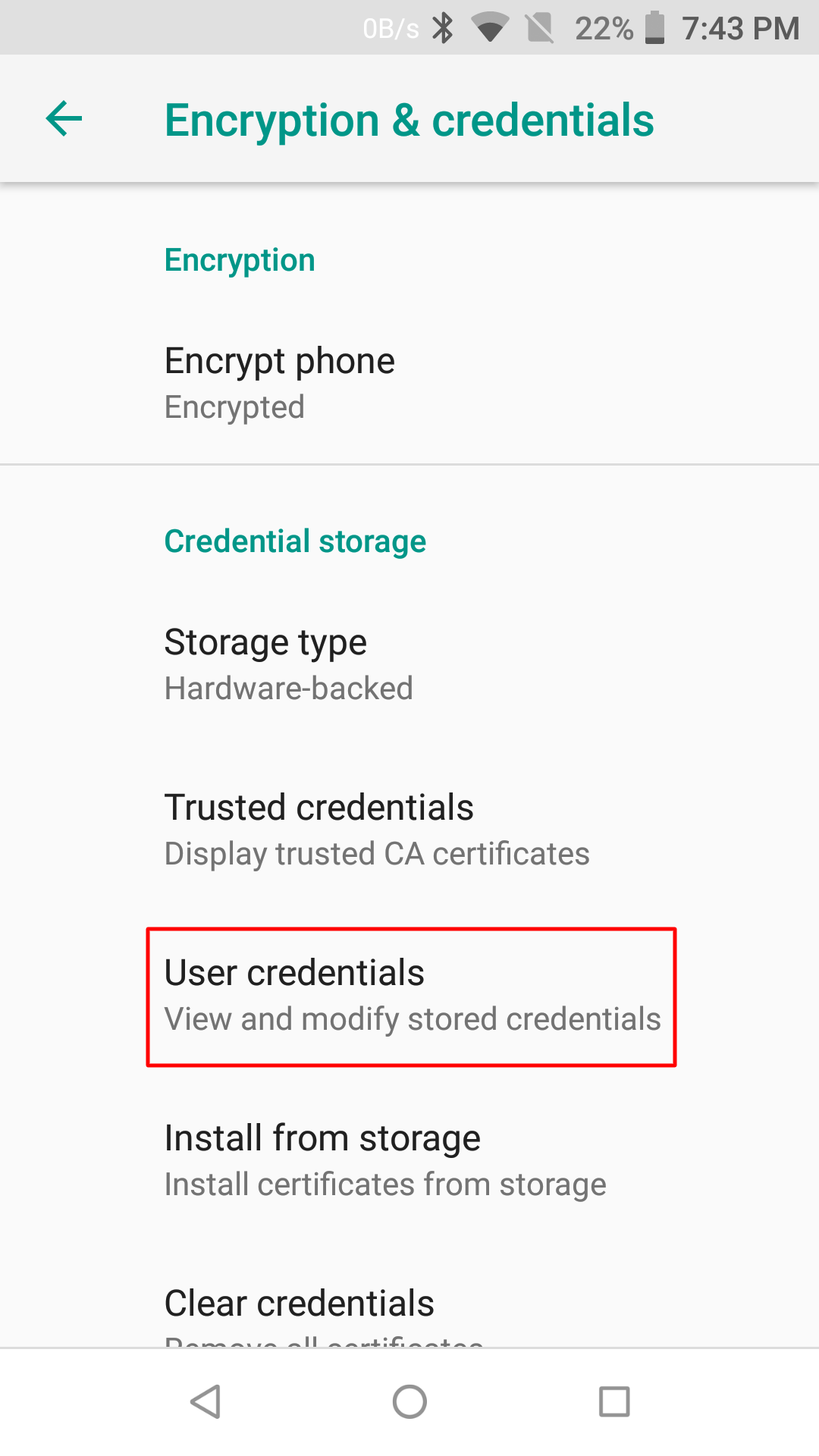
- Identity certificates (.p12) are stored in Settings > Security & Location > Encryption & Credentials > User Credentials
Pre Grant Certificates to Apps and URLs
For the apps that require certificate based authentication, IT admins can grant silent access of certificates to specific apps/URLs. Those apps/URLs can silently access the private key without user intervention to select a certificate. This can be applied on client certificates. PKCS12 with a chain and having a private key are classified as client certificates. The access can be granted from Android Device Profiles. Follow the steps below to do the same:
- Navigate to Device Profiles & Policies > Device Profiles and edit an existing Android Device Profile.
- Navigate to Restrictions > Device Management > Certificates
- On the client certificate which you want to grant access, enable the Install toggle. On enabling, the row will become expandable downwards for a client certificate.
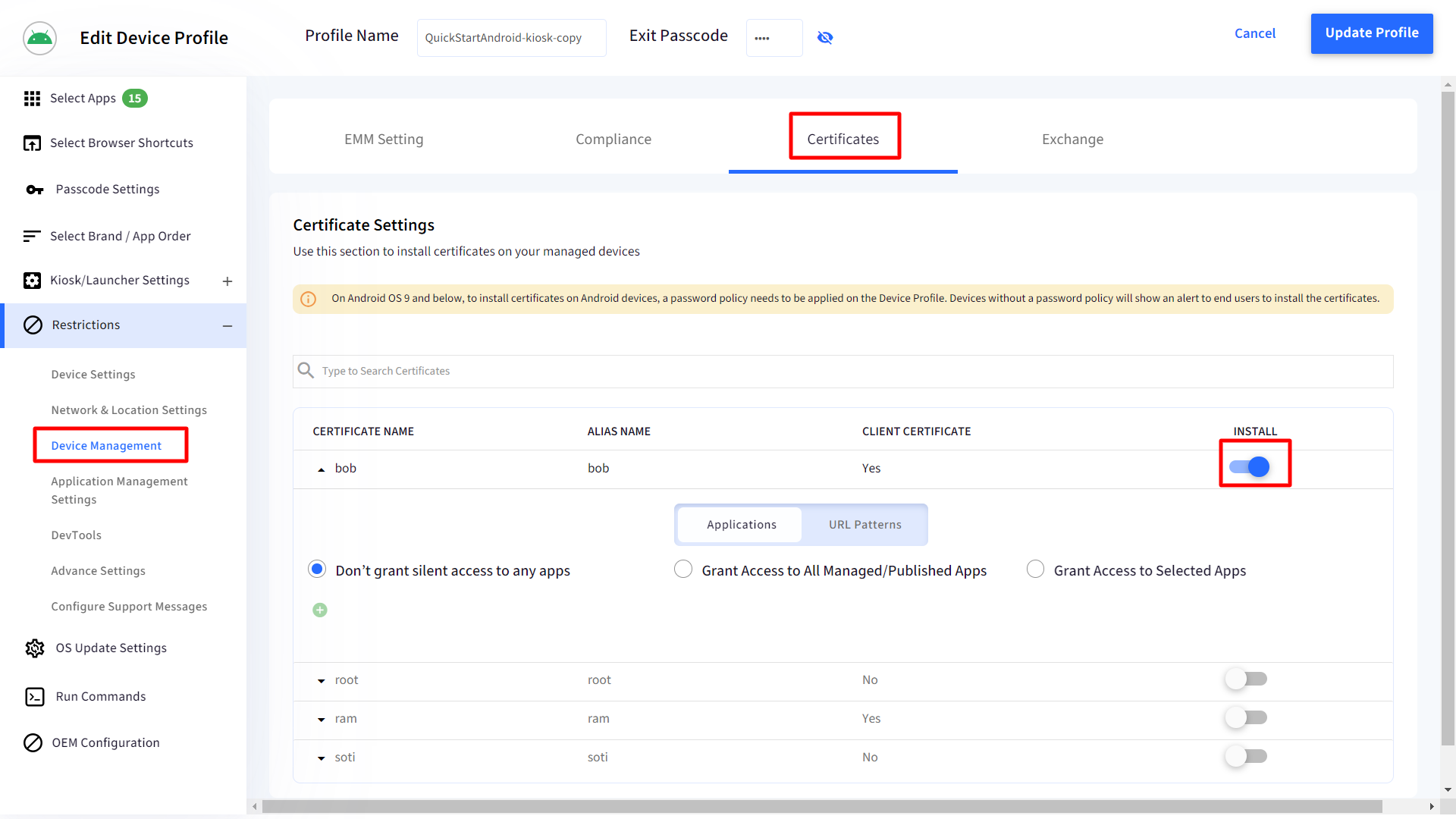
- There will be two tabs, viz
- Applications: This section allows admins to select which all apps have access to certificates. Choose one from the following three options:
- Don’t grant silent access to any apps (default): Silent access to certificates is not granted
- Grant Access to All Managed/Published Apps: Access is granted to all the apps published (apps published from Play for Work or Enterprise Store) published on the profile.
- Grant Access to Selected Apps: Select the apps to which you want to grant access of certificates. On choosing this option, a drop-down will be enabled from which you can select the app. Click on + icon to add more than one app. A maximum of 12 apps can be selected. The drop-down lists all the apps allowed on the profile.
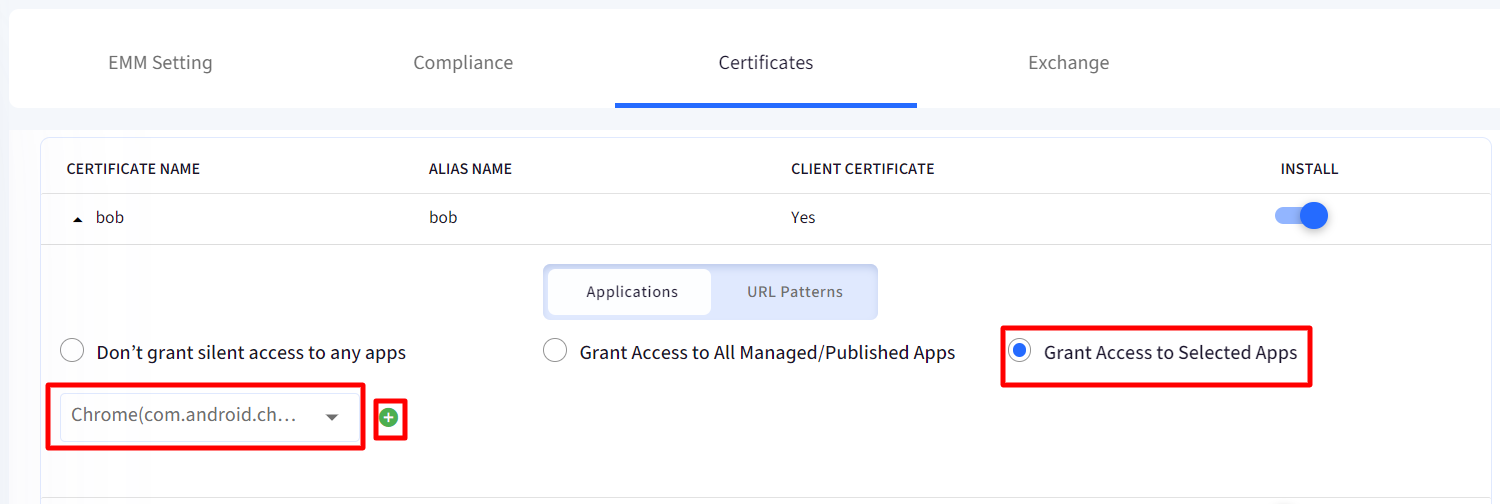
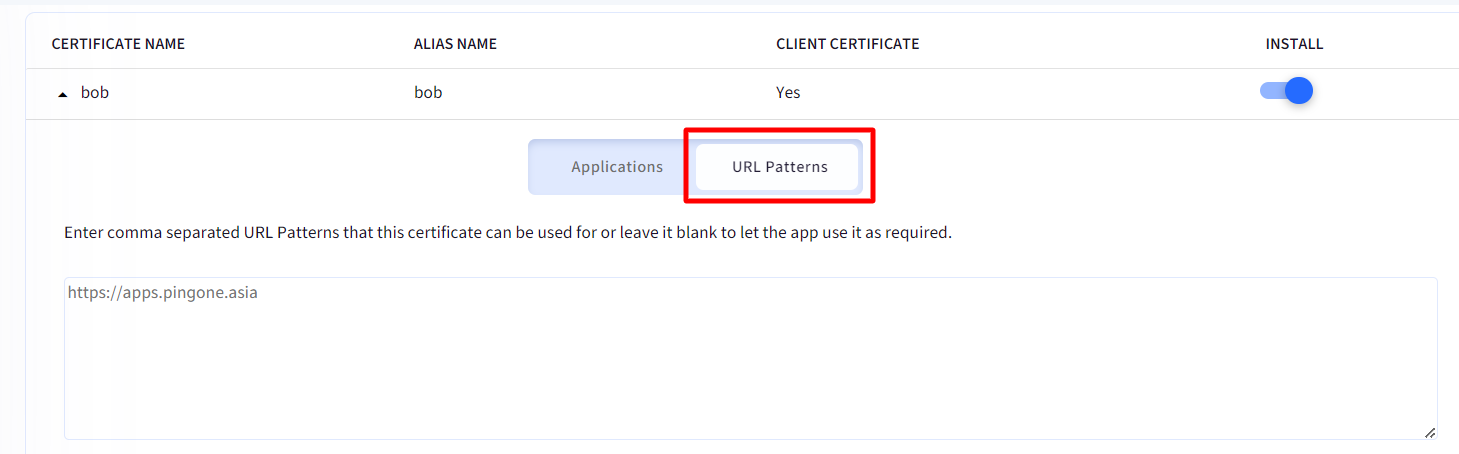
- URL patterns: If you have granted access of certificate to one or more apps, you can also specify URLs in those apps with which certificate can be associated silently. Enter comma separated URL Patterns that this certificate can be used for. It is optional for you to provide a URL pattern.
- Applications: This section allows admins to select which all apps have access to certificates. Choose one from the following three options:
- Once you have provided necessary grants, click on Update Profile
- On the devices associated with the profile, the apps will now be granted certificate access without the dialog.
Certificate based Enterprise Wifi Profile
On Android devices, certificates can be associated with Enterprise Wifi configurations. As a result, all the devices where this Wifi has been published as well as Wifi being pushed on new Profiles, it will be sent with the Certificate payload.
- On the Dashboard, Navigate to Device Profiles & Policies > All Configurations > Global Settings > Wifi Settings
- Click on Create New > Enterprise for Android or Edit an existing Wifi configuration created for Android
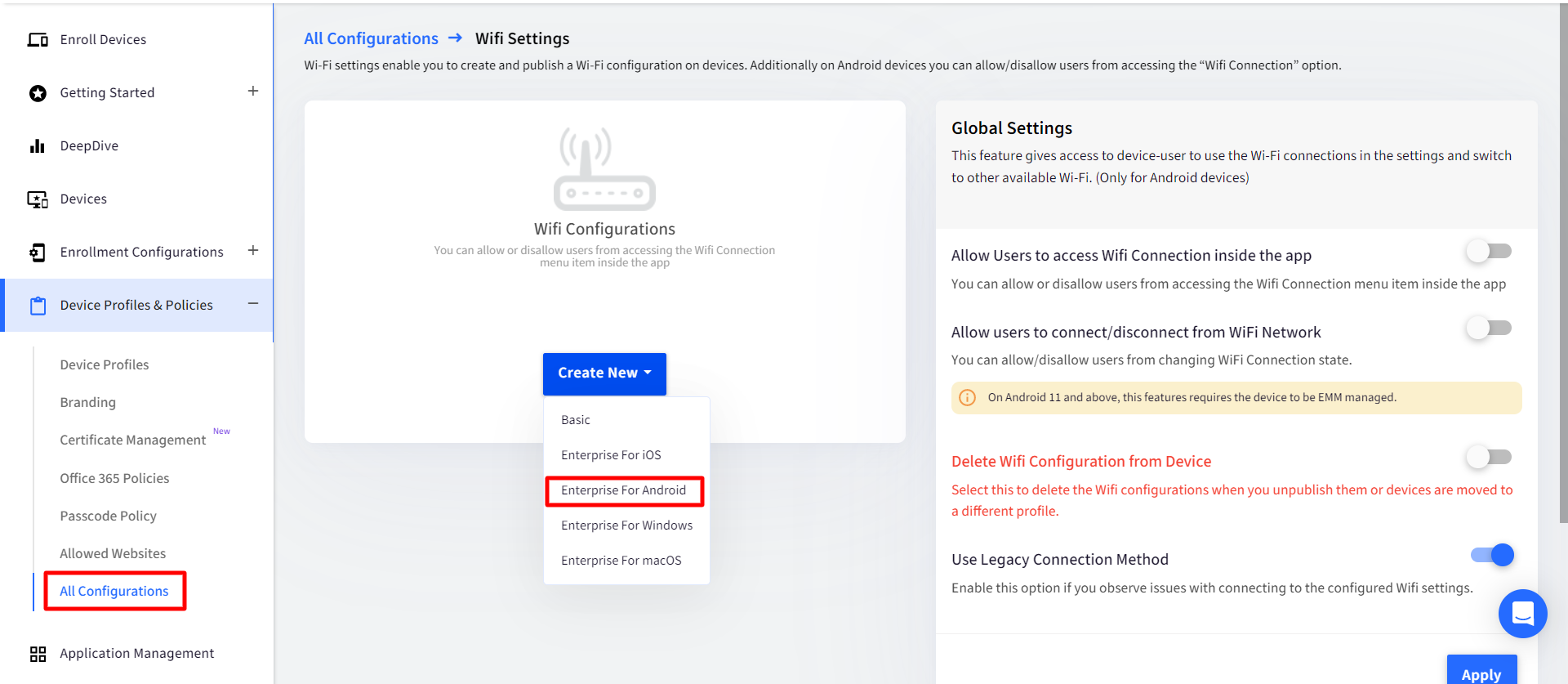
- In the Wifi Configuration window, when you scroll down there would be an option (drop-down) to select certificate (Identity and Trusted) that are previously uploaded
.png)
- Select certificates that need to be associated with the Wifi configuration, and click Submit
The certificate will get associated with the Wifi Configuration.
If a Certificate is deleted from Certificate screen:
- The association between the Wifi and Certificate will be removed and a new payload of Wifi would be sent.
- The Certificate will get uninstalled from devices.
Known Behaviors
- Legacy Managed devices:
- When certificates are Unpublished from Scalefusion dashboard, they do not get uninstalled from the device.
- After installation of p12 certificates on the device, the Install button in Certificate Manager on the device remains there.
- p12 certificates being installed on the device, but the 'Installed On' count on Certificate Management screen on the Scalefusion dashboard doesn't reflect it.
- After installation of Trust certificates, the Install button in front of Trust certificates goes away only after you refresh the managed device.
- If CA certificates have been removed from the device (Device Settings > User credentials) by user, the Install button for such certificates does not appear again in Certificate Manager on the device.
- On a Wifi Configuration if there are two certificates (a trust and an identity) associated, they are all displayed as one, under User credentials on the device.
- On BYOD devices, Identity Certificates get installed but are not visible on device.
- On Legacy Managed devices, if a Wifi configuration is unpublished or deleted from Scalefusion dashboard, the Wifi and certificates do not get uninstalled from the device.
- Passcode policy - In the passcode policy applied on the device profiles on which certificates are to be published, the password type should not be Unspecified, Something, or Weak Biometric.


