Microsoft's Windows Defender, now known as Microsoft Defender Antivirus provides real-time protection of Windows devices against software threats like viruses, malware, and spyware across email, apps, cloud, and the web.
With Scalefusion MDM, administrators can now configure and push various Windows Defender policies on their managed Windows devices. With Windows Defender feature, admins can configure policies ranging from scanning, real-time monitoring, signature updates to certain advanced ones like cloud protection and more, thereby protecting the systems from malware threats.
The document below describes all Windows Defender policies and how they can be configured.
Before You Begin
- Defender policies work on Windows 10 version 1809 and above, and on Windows Pro, Business, Enterprise, Education editions.
- The devices should be enrolled.
Configuring Defender Policies
- Sign In to Scalefusion Dashboard
- Navigate to Device Profiles & Policies > Device Profiles. Click on a Windows Device profile and edit, or create a new Windows Device profile.
- Once in the Device Profile wizard, click on the Settings > Security Settings > Windows Defender section to configure Defender policies.

- To configure Defender policies, toggle ON Configure Defender Policies. This allows you to start configuring various settings and also prompt the end users that they need to configure policies.

- There are four baselines provided here, viz Basic, Medium, Advanced and Custom which get enabled after toggling on Configure Defender Policies.

- Select Custom, to finetune the policies as per your enterprise requirements. Once you select Custom, the various policies categorized into sections get enabled. Below is a description of the policies and the options available.Note:To learn more about Windows Defender policies, please visit Policy CSP - Defender
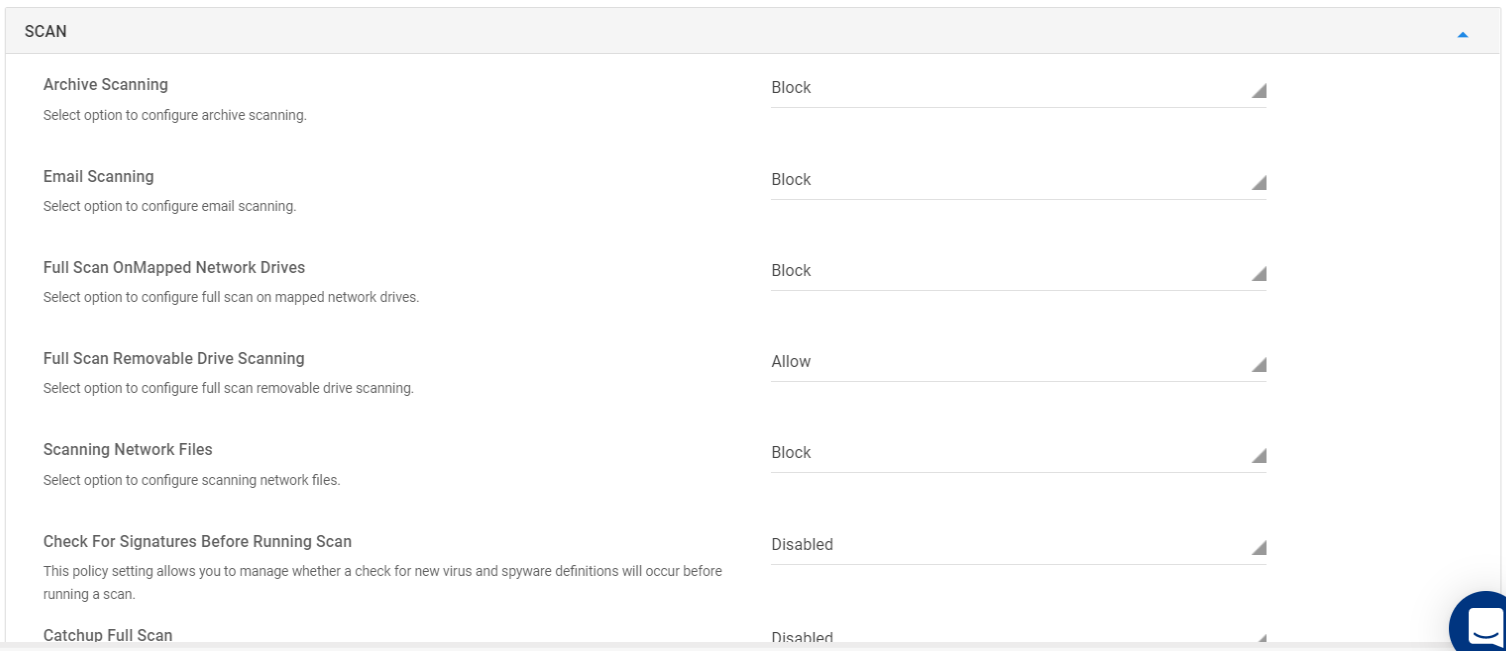
- Scan: This section lets you configure policies which apply at the time of scanning the device.
Setting
Description
Archive Scanning
Configure scanning of archives with the following options:
- Block (default) - Blocks scanning of archived files
- Allow - Scans archived files
- User Control - User controls scanning of archives
Email Scanning
Configure scanning of emails with the following options:
- Block (default) - Blocks scanning of emails
- Allow - Scans emails
- User Control - User controls scanning of emails
Full Scan OnMapped Network Drives
Configure full scan of mapped network drives with the following options:
- Block (default) - Blocks scanning of mapped network drives
- Allow - Scans mapped network drives
- User Control - User controls scanning of mapped network drives
Full Scan Removable Drive Scanning
Configure full scan of removable drives with the following options:
- Block - Blocks scanning of removable drives
- Allow (default) - Scans removable drives
- User Control - User controls scanning of removable drives
Scanning Network Files
Configure scanning of network files with the following options:
- Block (default) - Blocks scanning of network files
- Allow - Scans network files
- User Control - User controls scanning of network files
Check For Signatures Before Running Scan
Use this policy to manage whether a check for new virus and spyware definitions have to be done before running a scan. Following options are available:
- Disabled (default) - The scan will start using the existing definitions
- Enabled - A check for new definitions will occur before running a scan
- User Control - User controls whether a check for new definitions has to be performed or not.
Catchup Full Scan
Use this policy to configure catch-up scans (for scheduled full scans) which is initiated because a regularly scheduled scan was missed if a computer is offline for two consecutive scheduled scans.
Following options are available:
- Disabled (default) - Catchup scans for scheduled full scan do not take place.
- Enabled - Catch-up scans for scheduled full scans will be turned on
- User Control - User controls whether to perform catch-up scans for scheduled full scans.
Catchup Quick Scan
Use this policy to configure catch-up scans (for scheduled quick scans) which is initiated because a regularly scheduled scan was missed.
Following options are available:
- Disabled (default) - Catchup scans for scheduled quick scan do not take place.
- Enabled - Catch-up scans for scheduled quick scans will be turned on
- User Control - User controls whether to perform catch-up scans for scheduled quick scans.
Scan Parameter
Configure a scan type with the following options:
- Quick Scan (default) - Performs quick scan
- Full Scan - Performs full scan
- User control - User controls quick scan or full scan
Schedule QuickScan Time
Specify the time of day when the Windows Defender quick scan should run. Time has to be entered in the form of values like 0, 60, 120 etc. By default it is 120.
A value of 0=12:00AM, a value of 60=1:00AM, a value of 120=2:00, and so on, up to a value of 1380=11:00PMSchedule Scan Day
Select a day when the Windows Defender quick scan should run, with the following options:
- EveryDay (default)
- Sunday
- Monday
- Tuesday
- Wednesday
- Thursday
- Friday
- Saturday
- No Scheduled - No scheduled scan
For scheduled scans (quick scan or otherwise), the operating system can override the scan time. The scan usually runs when the CPU usage is low on the system.Average CPU Load Factor
This value represents the average CPU load factor for the Windows Defender scan (in percent). By default it is 50.
Low CPU Priority
Configure low CPU priority for scheduled scans, with the following options;
- Enabled - Low CPU priority is used during scheduled scans
- Disabled (default) - No changes are made to CPU priority for scheduled scans
- User Control - User controls the low CPU priority for scheduled scans
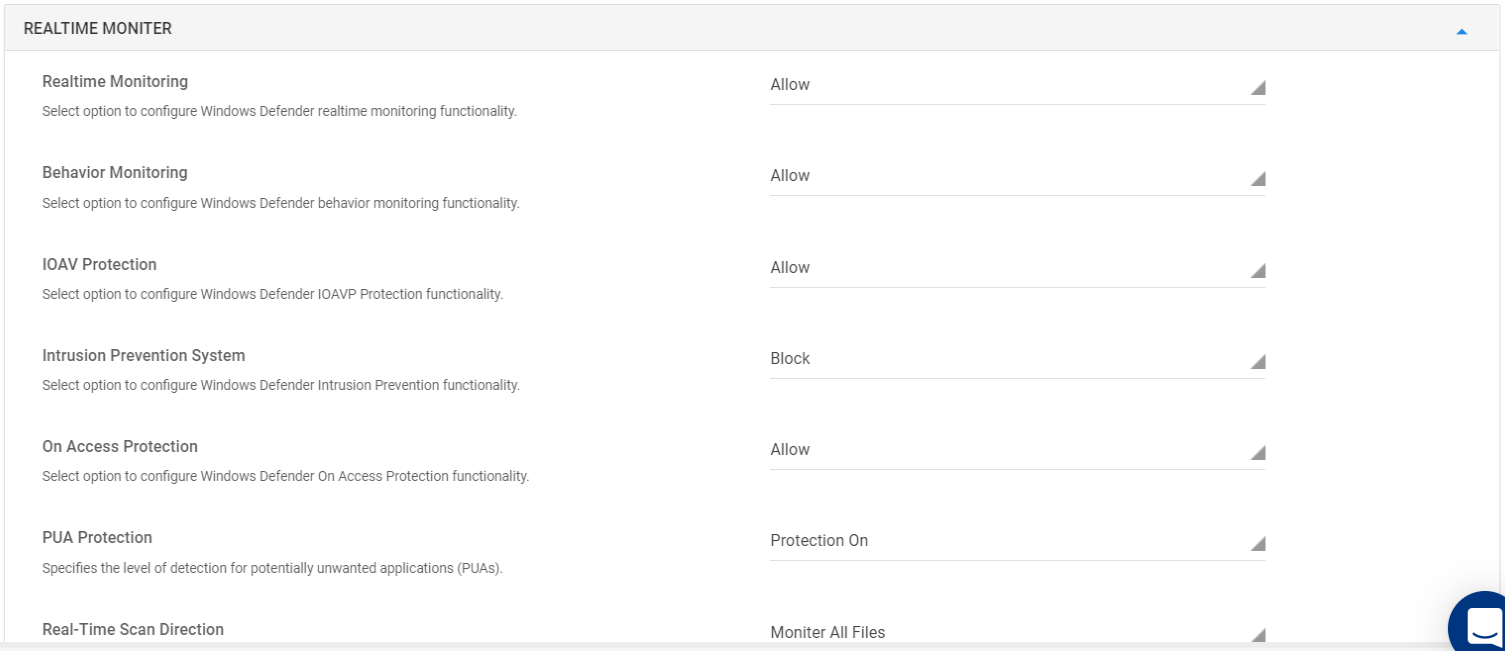
- Realtime Monitor: Configure policies for real time monitoring.
Setting
Description
Realtime Monitoring
Use this setting to configure Windows Defender Realtime Monitoring functionality. Following options are available:
- Allow (default) - Runs the real-time monitoring service
- Block - Turns off the real-time monitoring service
- User Control - User controls whether to run realtime monitoring service or not
Behavior Monitoring
Use this setting to configure Windows Defender Behavior Monitoring functionality. Following options are available:
- Allow (default) - Turns on the real-time Behavior monitoring service
- Block - Turns off the Behavior monitoring service
- User Control - User controls whether to run Behavior monitoring service or not
IOAV Protection
Use this setting to configure Windows Defender IOAV Protection functionality. Following options are available:
- Allow (default) - Allows IOAV Protection
- Block - Disallows IOAV Protection
- User Control - User controls whether to allow or block IOAV Protection
Intrusion Prevention System
Use this setting to configure Windows Defender Intrusion Prevention functionality. Following options are available:
- Allow - Allows Intrusion Prevention
- Block (default) - Disallows Intrusion Prevention
- User Control - User controls whether to allow or block Intrusion Prevention
On Access Protection
Use this setting to configure Windows Defender On Access Protection functionality. Following options are available:
- Allow (default) - Allows On Access Protection
- Block - Disallows On Access Protection
- User Control - User controls whether to allow or block On Access Protection
PUA Protection
With this you can configure and specify the level of detection for potentially unwanted applications (PUAs), with the following options:
- Protection On (default) - Windows Defender protects against potentially unwanted applications by blocking detected items. They will show in history along with other threats.
- Protection Off - Windows Defender does not protect against potentially unwanted applications
- Audit Mode - Windows Defender will detect potentially unwanted applications, but take no action.
- User Control - User controls whether to protect against potentially unwanted applications or not.
Real-Time Scan Direction
Specify the configuration that can be used to monitor specific files, with the following options:
- Monitor All Files (default) - Monitors all files
- Monitor Incoming Files - Monitors only incoming files
- User Control - User controls which files are to be monitored
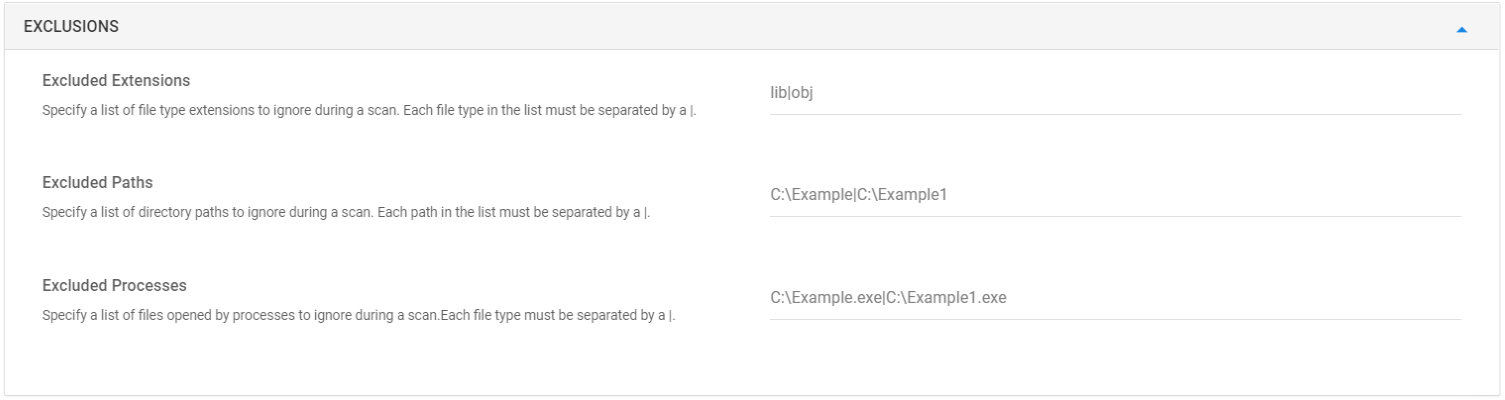
- Exclusions: Use this section to configure policies for excluding extensions, paths, processes etc. at the time of scan.
Setting
Description
Excluded Extensions
Use this setting to specify a list of file type extensions to ignore during a scan. Each file type in the list must be separated by a |. For example, "lib|obj".
Excluded Paths
Use this setting to specify a list of directory paths to ignore during a scan. Each path in the list must be separated by a |. For example, "C:\Example|C:\Example1".
Excluded Processes
Use this setting to specify a list of files opened by processes to ignore during a scan. Each file type must be separated by a |. For example, "C:\Example.exe|C:\Example1.exe".
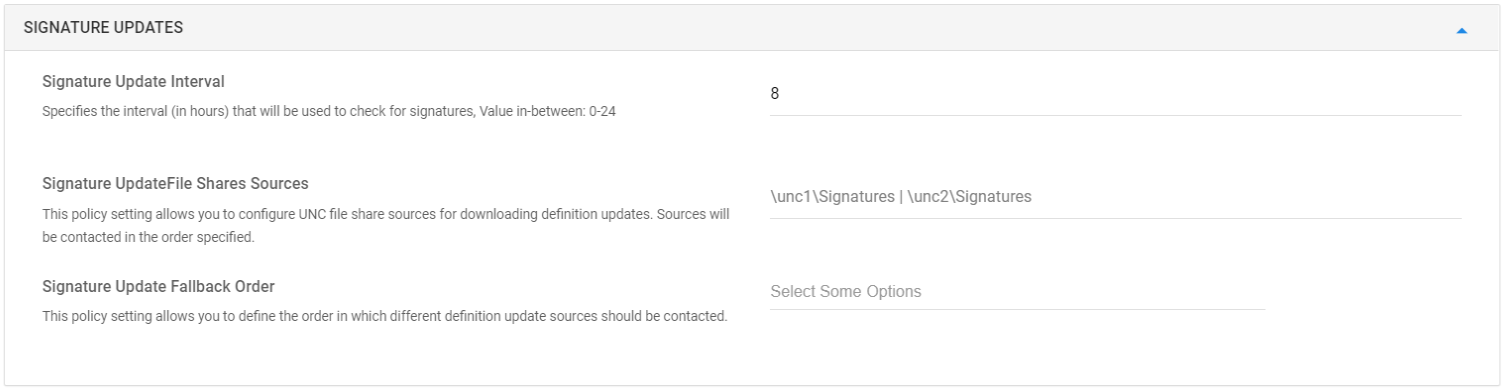
- Signature Updates: In this section you can set configurations related to signature updates.
Setting
Description
Signature Update Interval
Use this setting to specify the interval (in hours) that will be used to check for signatures. The value can be between 0-24 where 0 means no check for new signatures, a value of 1 means to check every hour and so on.
By default, value is 8.
Signature UpdateFile Shares Sources
This allows you to configure UNC file share sources for downloading definition updates. Sources will be contacted in the order specified. The value of this setting should be entered as a pipe-separated string enumerating the definition update sources.
For example: \unc1\Signatures | \unc2\Signatures
Signature Update Fallback Order
This allows you to define the order in which different definition update sources should be contacted.
Following are the values:
- Internal Definition Update Server
- Microsoft Update Server
- MMPC
- File Shares
Multiple values can be selected - Windows Defender Exploit: In this section you can configure policies on Attack Surface reduction rules, folder access, network protection and more.

Setting
Description
Attack Surface Reduction Rules
This policy enables setting the state (Block/Audit/Off) for each Attack surface reduction (ASR) rule. Each ASR rule listed can be set to one of the following states (Block/Audit/Off). Each entry must be listed as a name value pair. The name defines a valid ASR rule ID, while the value contains the status ID indicating the status of the rule.
For more information on Attack Surface Reduction Rules, visit here
Attack Surface Reduction Only Exclusions
This policy setting allows you to prevent Attack Surface reduction rules from matching on files under the paths specified or for the fully qualified resources specified. Paths should be added under the Options for this setting.
As an example, a path might be defined as: "c:\Windows" to exclude all files in this directory. A fully qualified resource name might be defined as: "C:\Allowed.exe"..
Controlled Folder Access
Use this setting to configure the state (On/Off/Audit) for the controlled folder access feature.
- Enabled - If enabled, this feature removes modify and delete permissions from untrusted applications to certain folders such as My Documents.
- Disabled (default) - Does not remove modify and delete permissions from untrusted applications
- Audit Mode - Identifies untrusted applications but no action is taken
- User Control - User controls whether controlled folder access features.
Controlled FolderAccess Protected Folders
Use this setting to allow user-specified folder locations to the controlled folder access feature. These folders will complement the system defined folders such as My Documents and My Pictures.
Controlled Folder Access Allowed Applications
This allows user-specified applications to the controlled folder access feature. Adding an allowed application means the controlled folder access feature will allow the application to modify or delete content in certain folders such as My Documents.
Network Protection
Use this setting to configure turning network protection on (block/audit) or off.
- Enabled (default) - Protects users using any app from accessing phishing scams, exploit-hosting sites, and malicious content on the Internet.
- Disabled - Users/apps will not be blocked from connecting to dangerous domains.
- Audit Mode - Users/apps will not be blocked from connecting to dangerous domains. However, you will still see this activity in Windows Defender Security Center.
- User Control - User controls network protection behavior
- Advanced: This section contains advanced policies on cloud protection etc. that you can configure.

Setting
Description
Cloud Protection
Use this setting to control if Windows Defender should send information to Microsoft about any problems it finds. Following options are available:
- Allow (default) - Turns on the Microsoft Active Protection Service
- Block - Turns off the Microsoft Active Protection Service
- User Control - User controls if the service has to be allowed or not
Submit Samples Consent
This setting checks for the user consent level in Windows Defender to send data, with following options:
- Send Safe Sample Automatically (default)
- Never Send
- Send All Sample Automatically
- Always Prompt
- User Control
Cloud Block Level
This allows you to set a blocking level regarding how aggressive Microsoft Defender Antivirus will be in blocking and scanning suspicious files. Following options are available:
- High (default) - aggressively blocks unknowns while optimizing client performance
- Aggressively - aggressively blocks unknowns and apply additional protection measures
- Zero Tolerance - blocks all unknown executables
- Default - Default windows defender blocking level
- User Control - User controls in setting the blocking level
Cloud Extended Timeout
Specify the time (in seconds) limit up to which Microsoft Defender Antivirus can block a suspicious file, and scan it in the cloud to make sure it's safe. By default time is set to 10. It can be set up to 60.
Script Scanning
Configure Windows Defender Script Scanning functionality with the following options:
- Allow (default) - Allows script scanning
- Block - Disallows script scanning
- User Control - User controls script scanning
User UI Access
Use this setting to control user access to the Windows Defender UI. If disallowed, all Windows Defender notifications will also be suppressed. Following options are available:
- Allow (default) - Allows users to access UI
- Block - Prevents users from accessing UI
- User Control - User controls access to UI
Threat Severity Default Action
With this you can specify any valid threat severity levels and the corresponding default action ID to take.
This value is a list of threat severity level IDs and corresponding actions, separated by a |
By default the level is set to 2-2
Days To Retain Cleaned Malware
Specify the time period (in days) for which quarantine items will be stored on the system. The default value is 0, which keeps items in quarantine, and does not automatically remove them. It can be between 0-90.
- Scan: This section lets you configure policies which apply at the time of scanning the device.
- Once you have configured Windows Defender policies, click on Update Profile to save these settings. The changes will be automatically pushed to the devices where this profile is applied.