- 28 Sep 2023
- 2 Minutes to read
- Print
- PDF
Password Policy for Linux Devices
- Updated on 28 Sep 2023
- 2 Minutes to read
- Print
- PDF
It is very important for companies and IT Admins to make sure that the users are not using a weak passwords on their devices and also change their passwords periodically. Scalefusion offers the option of configuring a password policy and applying it to the device profile, which allows organizations to enforce uniform password compliance across the managed devices.
Follow the steps below to create a password policy and apply it to the managed Linux devices.
Prerequisites
- Create a Device Profile.
Step 1: Create a Password Policy
- Navigate to Device Profiles & Policies, click on Passcode Policy and select Linux
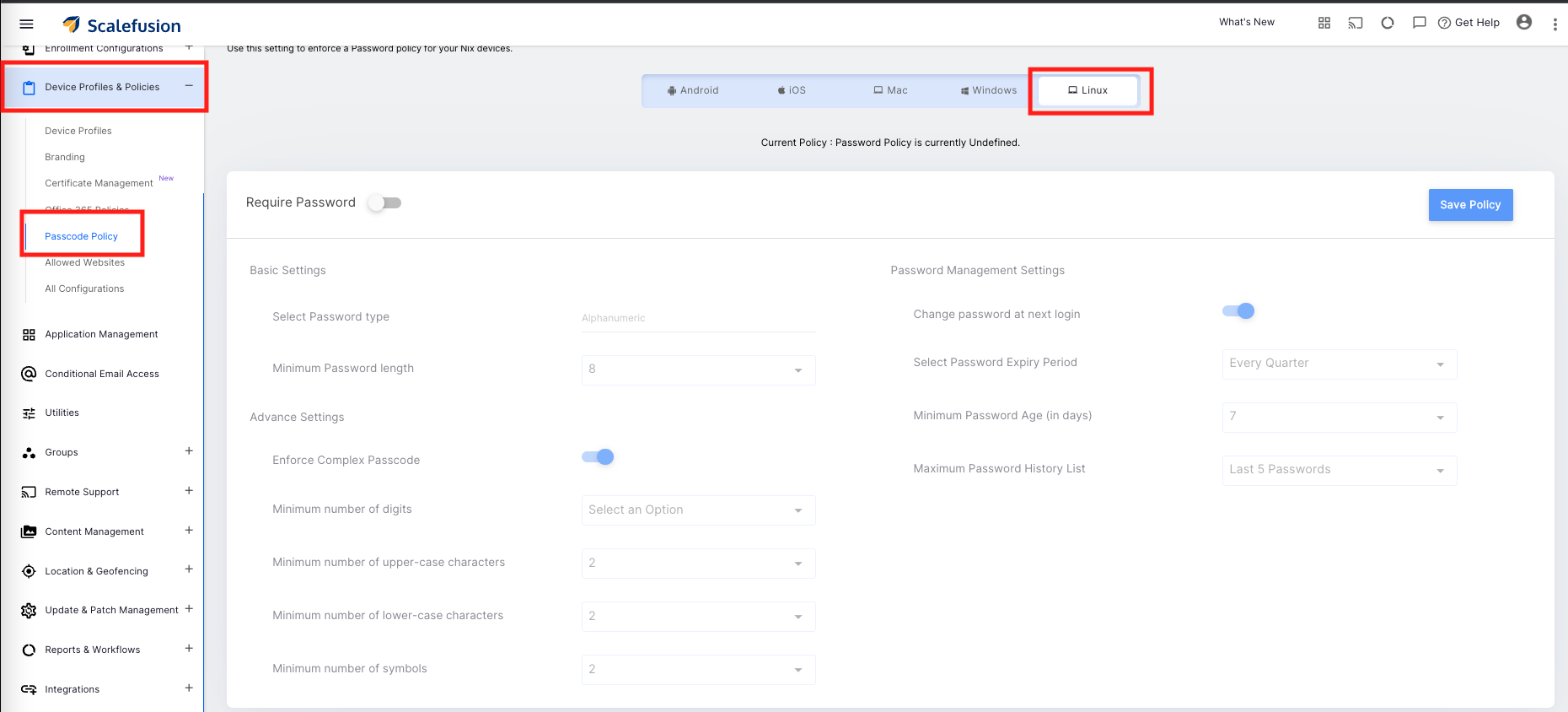
- Click on Require Password to start configuring the password policy using the wizard,
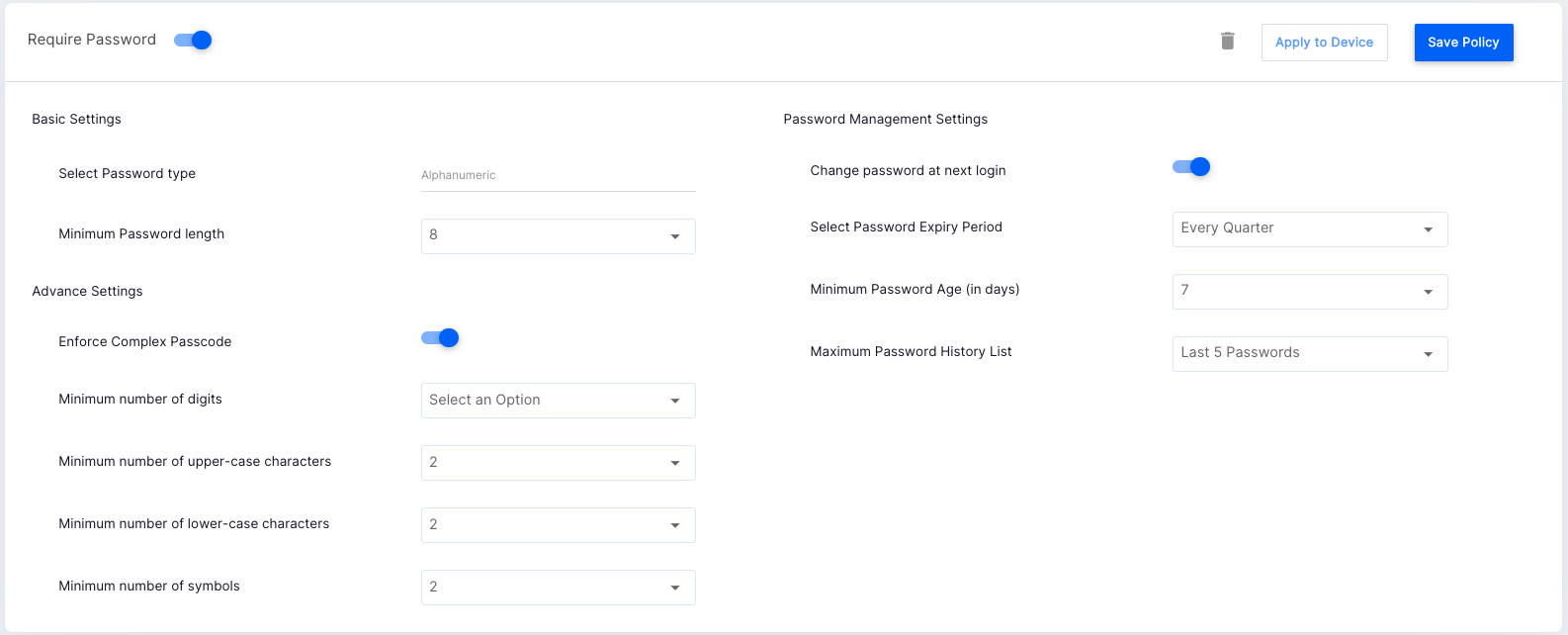
- Basic Settings:
- Password Type: The only option is Alphanumeric, and this cannot be changed.
- Minimum Password Length: Select a minimum password length between 4-16. We recommend choosing a value between 8 to 16.
- Advanced Settings: Use these settings to enforce a complexity on the password of the device.
- Enforce Complex Passcode: Enable this to configure the other options
- Minimum number of digits: Configure the minimum number of digits that should be enforced.
- Minimum number of upper-case characters: Configure the minimum number of upper-case characters that should be enforced.
- Minimum number of lower-case characters: Configure the minimum number of lower-case characters that should be enforced.
- Minimum number of symbols: Configure the minimum number of symbols that should be enforced.
- Password Management Settings: Use these options to set the password management options
- Change password at next login: Enable this option to force the user to change the password at the next login. If this is OFF, then the password change as per the policies will be enforced at login based on the expiry period or if the user uses passwd command at the terminal.
- Select Password Expiry Period: Configure a time after which the current password is expired, and the user is asked to change the password again at login.
- Minimum Password Age (in days): Configure the number of days that the user is not allowed to change the password after a successful change in password. This prevents users from bypassing the history list rules by disallowing instant change in passwords and then reusing it in the next password change cycle.
- Maximum Password History List: Configure this to prevent users from repeating their passwords on password changes. Allows you to configure the rules for password history rules.
- Basic Settings:
- Once you have configured the password policy, click Save to save the policy.
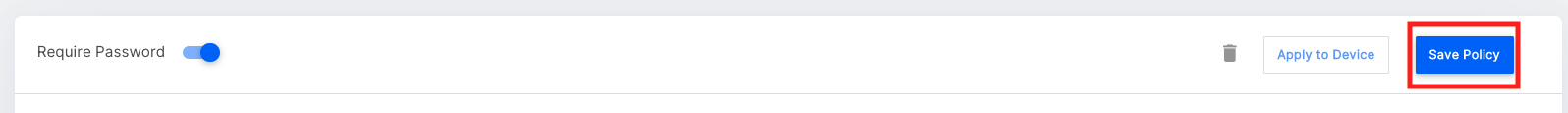
Step 2: Apply a Password Policy
- Once you have created a password policy, you can apply it to one or multiple profiles so that the devices and users that are managed using these profiles are forced to change their passwords based on the policy. Click Apply to Device to apply to devices
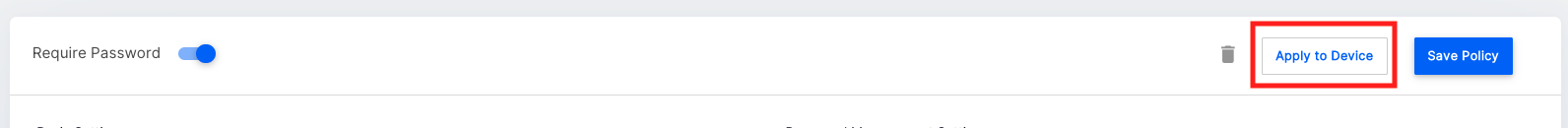
- From the profile selection wizard, select the profiles which you want to apply this policy and click Submit
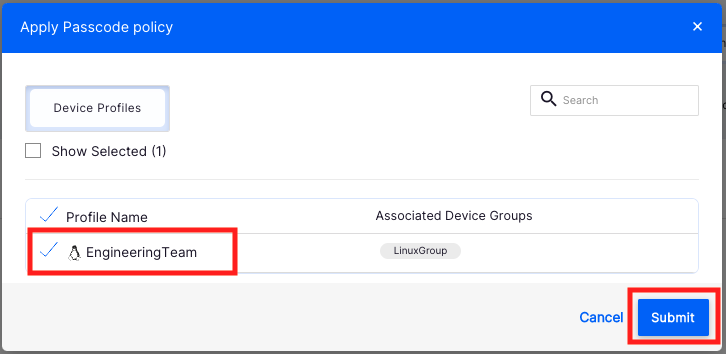
- Post Step 2, the policy will be pushed to all managed devices, and for new devices, it will be applied after enrollment.Once a password policy is applied to the profile, any changes to the password policy are automatically applied to the devices.
Understanding End-user experience
Once you have applied the password, the end users will be asked to change the password either at the next login or after the password expiry period based on your policy. Based on the OS, they would see the following screens,
Please note that the screens may differ based on the flavor of the OS. The following screenshots are from Mint 19.2
- The OS prompts to change the password at the next login,
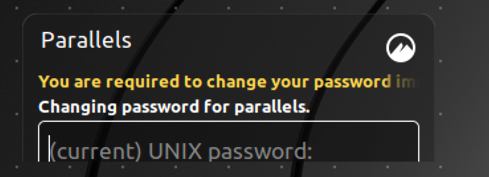
- The OS prompts you to enter the change the current password
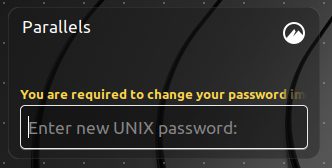
- Finally, the users are prompted to confirm the new password, and then they can log in to the system.