- 01 Feb 2024
- 2 Minutes to read
- Print
- PDF
Microsoft Platform Single Sign On (SSO) for iOS devices.
- Updated on 01 Feb 2024
- 2 Minutes to read
- Print
- PDF
Introduction
If you utilize Microsoft Entra/Azure and wish to enable your users to experience single sign-on across all apps and websites that use Microsoft Entra ID for authentication, including Microsoft 365. This document provides guidance on how you can leverage this capability.
Microsoft’s Platform SSO offers the Microsoft Enterprise SSO plug-in tailored for Apple devices. Users can now log in using Identity Provider (IdP) credentials, such as Microsoft Entra ID or Azure AD and subsequently, sign in to corporate apps and websites automatically.
To know more about Platform SSO please visit the Microsoft documentation:
https://learn.microsoft.com/en-us/entra/identity-platform/apple-sso-plugin
Prerequisites
iOS/iPadOS 13.0 and newer must be installed on the device.
A Microsoft application that provides the Microsoft Enterprise SSO plug-in for Apple devices must be installed on the device. This app is the Microsoft Authenticator app.
Steps to make this feature work with Scalefusion
Step 1: Install Microsoft Authenticator app on the iOS device(s).
Step 2: Push the Custom Payload to iOS device(s).
Step 1: Install Microsoft Authenticator app on the iOS device(s).
Log into your Scalefusion dashboard and navigate to Application Managment > Apple App Store section.
Click on Add from App Store button.

Search for Microsoft Authenticator app in the search field.
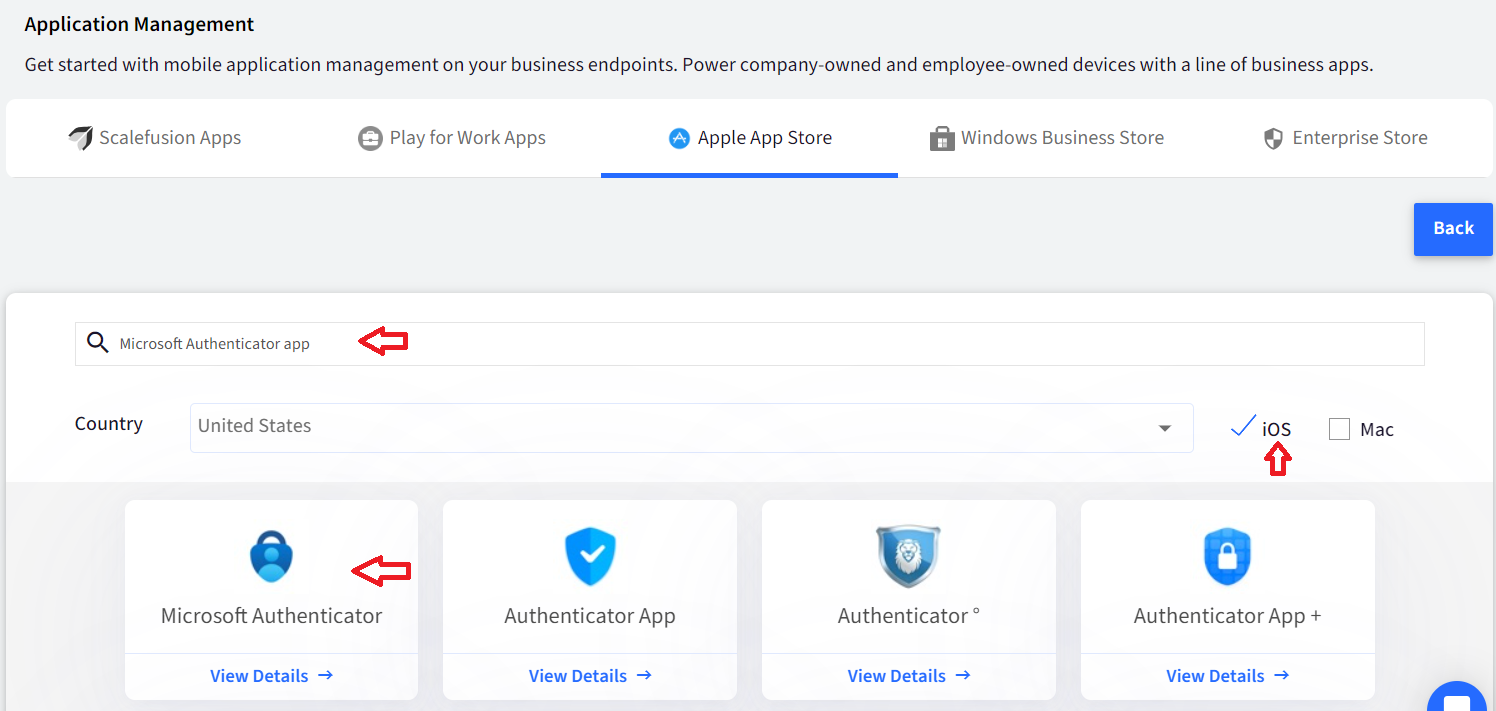
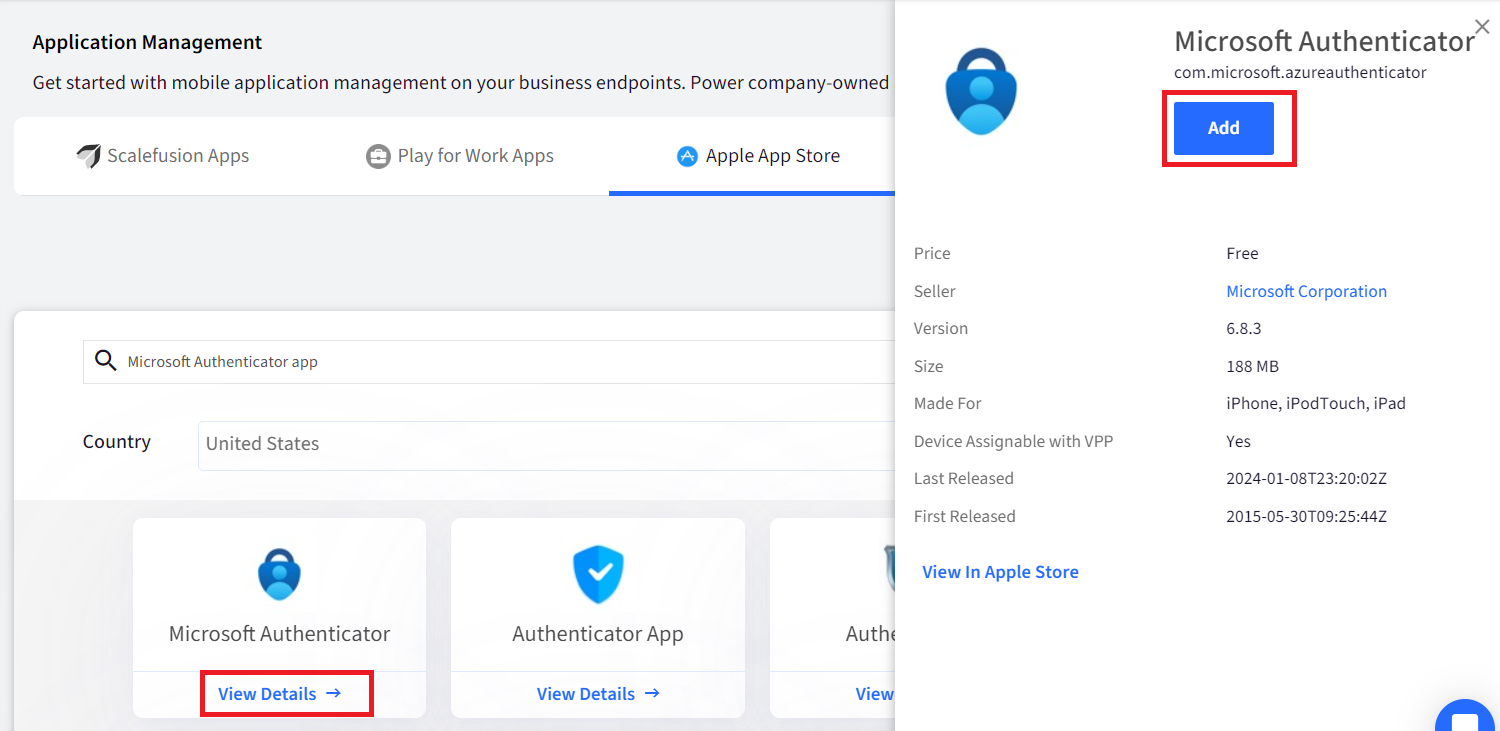
Click on View Details and click on Add button to add the app.
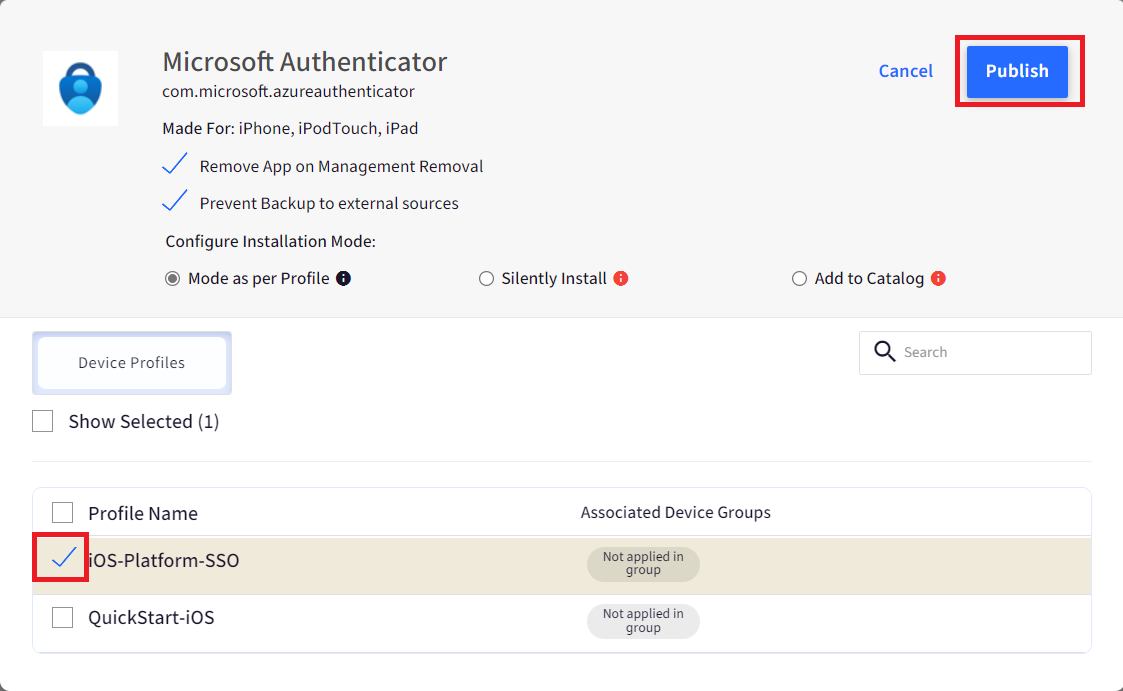
Publish the app on the Device Profile.
You can also push the Microsoft Authenticator app under Volume Purchase Program (VPP app) on the device(s). To know more about VPP apps please refer to our guide here.
Note:
Apps that are added as App Store app will require the end user to sign into their Apple ID on the device(s) to install the app published from the Apple App Store on the dashboard. For silent app installation please push the Microsoft Authenticator app as a VPP app.
Step 2: Push the Custom Payload to iOS device(s).
Copy the contents directly from below and add it in Custom Settings in the Device Profile or click here to download the file and import it in the Device Profile.
<plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>ExtensionData</key> <dict> <key>useSiteAutoDiscovery</key> <true/> </dict> <key>ExtensionIdentifier</key> <string>com.microsoft.azureauthenticator.ssoextension</string> <key>URLs</key> <array> <string>https://login.microsoftonline.com</string> <string>https://login.microsoft.com</string> <string>https://sts.windows.net</string> <string>https://login.partner.microsoftonline.cn</string> <string>https://login.chinacloudapi.cn</string> <string>https://login.microsoftonline.us</string> <string>https://login-us.microsoftonline.com</string> </array> <key>Type</key> <string>Redirect</string> <key>PayloadIdentifier</key> <string>com.example.myessopayload</string> <key>PayloadType</key> <string>com.apple.extensiblesso</string> <key>PayloadUUID</key> <string>dbed949d-39a2-440d-a84b-e0c825cdcb2e</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadDisplayName</key> <string>P1Extensible SSO</string> </dict> </array> <key>PayloadDisplayName</key> <string>Extensible SSO</string> <key>PayloadIdentifier</key> <string>com.example.myprofile</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>da3bbbec-a753-4aa7-aeae-a74b7a65c0b5</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>Follow our guide on how to add the Custom Payload in the Device Profile & deploy it to devices.
Notes:
The Payload and its contents are sourced from various albeit authenticated Apple Developer communities and forums.
Please validate them on a test machine before deploying them on all your managed devices.
Scalefusion has tested these Payloads, however, Scalefusion will not be responsible for any loss of data or system malfunction that may arise due to the incorrect usage of these payloads.
End user experience.
Users don't need to use the Authenticator app; it just needs to be installed on the device.
To initiate the extension, users sign in to any supported app or website, facilitating the bootstrap process, which configures the extension during the initial sign-in.
Upon successful sign-in, the extension seamlessly and automatically authenticates users across all other supported apps or websites.
You can test single sign-on by opening Safari in private mode and opening the https://portal.office.com site. No username and password will be required.
If you encounter any difficulties or have questions, please reach out to our Support team at: support@scalefusion.com





