- 26 Apr 2024
- 1 Minute to read
- Print
- PDF
Block access to Erase all Content and Settings on Mac devices.
- Updated on 26 Apr 2024
- 1 Minute to read
- Print
- PDF
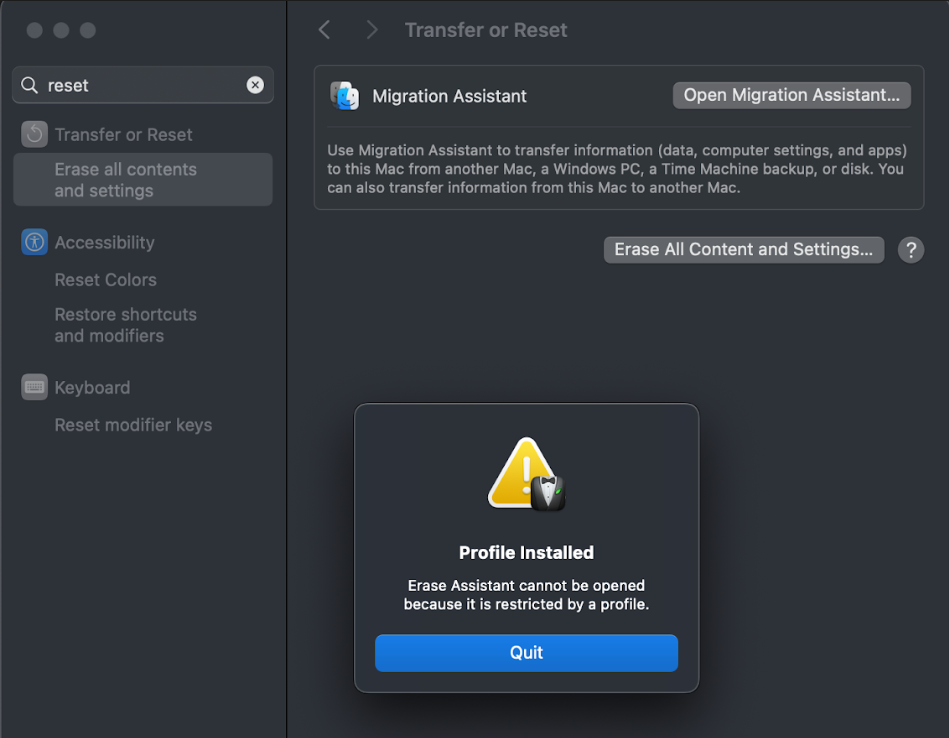
The following Payload helps the IT Admins to block access to Erase all Content and Settings option on their managed Mac devices. This is supported from macOS 12+ and above.
Copy the contents directly from below and add it in Custom Settings in the Device Profile or click here to download the file and import it in the Device Profile.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadDisplayName</key> <string>Restrictions</string> <key>PayloadIdentifier</key> <string>com.apple.applicationaccess.9AE3B033-B4F8-46A4-93D8-1E3FA442E669</string> <key>PayloadType</key> <string>com.apple.applicationaccess</string> <key>PayloadUUID</key> <string>9AE3B033-B4F8-46A4-93D8-1E3FA442E669</string> <key>PayloadVersion</key> <integer>1</integer> <key>allowEraseContentAndSettings</key> <false/> </dict> </array> <key>PayloadDescription</key> <string>Disables Factory Reset option</string> <key>PayloadDisplayName</key> <string>Disable Factory Reset</string> <key>PayloadIdentifier</key> <string>com.promobitech.scalefusion.81B87610-313F-475A-90CF-F97C0CB323D8</string> <key>PayloadOrganization</key> <string>Scalefusion</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>81B87610-313F-475A-90CF-F97C0CB323D8</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>Follow our guide on how to add the Custom Payload in the Device Profile & deploy it to devices.
On the device, the "Erase all Content and Settings" option will be inaccessible to users.
Notes:
The Payload and its contents are sourced from various albeit authenticated Apple Developer communities and forums.
Please validate them on a test machine before deploying them on all your managed devices.
Scalefusion has tested these Payloads, however, Scalefusion will not be responsible for any loss of data or system malfunction that may arise due to the incorrect usage of these payloads.


